Malware
Zoomed In: A Look into a Coinminer Bundled with Zoom Installer
We found a coinminer bundled with the legitimate installer of video conferencing app Zoom. Users who attempt to download the installer get more than what they bargain for as they instead download the AutoIt compiled malware Trojan.Win32.MOOZ.THCCABO.
Many companies around the world have transitioned to work-from-home arrangements because of growing concerns over the COVID-19 global health crisis. This new setup has highlighted the usefulness of video conferencing apps. These platforms have been utilized by companies and remote workforces to hold meetings and for other communication needs even long before the virus outbreak occurred. Unfortunately, cybercriminals are taking advantage of these tools’ recent time in the spotlight to spread malware.
We found a Coinminer bundled with the legitimate installer of video conferencing app Zoom, luring users who want to install the software but end up unwittingly downloading a malicious file. The compromised files are not from Zoom’s official download center, and are assumed to come from fraudulent websites. We have been working with Zoom to ensure that they are able to communicate this to their users appropriately.
Figure 1. Code snippets of 64.exe (a coinminer) bundled with a Zoom installer
Analysis of the malicious file
Users who attempt to download the installer get more than what they bargain for as they instead download the AutoIt compiled malware Trojan.Win32.MOOZ.THCCABO. The files it drops include the following:
| File | Description |
|---|---|
| 64.exe | Detected as Coinminer.Win64.MOOZ.THCCABO |
| asacpiex.dll (first 5 bytes are NULL) | Archive file containing Coinminer.Win64.MOOZ.THCCABO |
| CR_Debug_Log.txt (asacpiex.dll with the first 5 bytes replaced) | Archive file containing Coinminer.Win64.MOOZ.THCCABO |
| CL_Debug_Log.txt | 7-zip Archiver |
| SystemCheck.xml | Used for scheduling tasks |
| ZoomInstaller.exe | Legitimate Zoom installer version 4.4.0.0 |
Figure 2. The contents of the malicious file
Figure 3. A detailed breakdown of the file’s contents
For the archive file asascpiex.dll, the first 5 bytes NULL, and then were replaced by 0x00 in an attempt to make it difficult to determine its original file signature, 0x37 0x7A 0xBC 0xAF 0x27, which would identify it as a 7-Zip archive file. This file will soon be copied as CR_Debug_log.txt. 7-Zip archiver CL_Debug_log.txt is used to decompress this password-protected archive.
Figure 4. Screen showing the asacpiex.dll file format signature
The file determines the architecture of the infected system by using the cpuinfo flags bits. It will drop 64.exe for 64-bit systems. The package does not contain a 32.exe for 32-bit systems, meaning the malware only runs in a 64-bit environment for now.
Figure 5. Screens showing 64.exe code snippet
The file gathers information such as Graphics Processing Unit (GPU) information using Windows Management Instrumentation (WMI queries), which is useful information for mining activities. It also collects details on CPU, system, operating system version, video controllers, and processors.
Figure 6. Code that checks the processor details
Figure 7. Code that checks the video controller details
It also checks whether the Microsoft SmartScreen and Windows Defender are enabled and if the antivirus solutions listed below are running in the system:
| Process Name | Antivirus solution |
|---|---|
| AvastUI.exe / AvastSvc.exe | Avast |
| avguix.exe / AVGUI.exe | AVG |
| avp.exe / avpui.exe | Kaspersky |
| dwengine.exe | Dr. Web |
| egui.exe / ekrn.exe | ESET NOD32 |
| MBAMService.exe | Malwarebytes |
Figure 8. Code that checks for running antivirus products
The gathered info will be sent to hxxps://2no.co/1IRnc using HTTP GET request.
Figure 9. Information sent to a URL using HTTP GET request
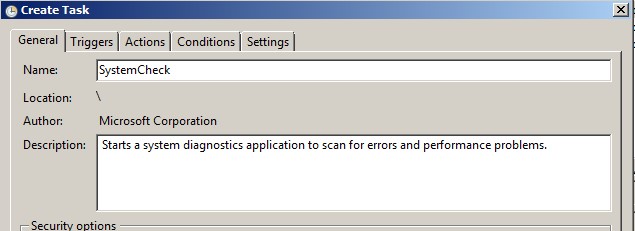
The CR_Debug_log.txt is a file, compressed using 7-Zip archiver, that contains the payload 64.exe coinminer. It will soon be copied as helper.exe coinminer into the %appdata%\Roaming\Microsoft\Windows\ folder. This is an AutoIt compiled malware that contains 7-Zip archiver and a compressed Tor binaries that are password protected. To maintain persistence, it schedules tasks with the -SystemCheck argument.
Figure 10. -SystemCheck scheduled task description
Figure 11. -SystemCheck scheduled task – actions
Once helper.exe is launched using the scheduled task, it will spawn itself with the -SystemCheck91137 argument.
Figure 12. -SystemCheck91137 in the Command Line of helper.exe properties
To evade detection, helper.exe checks whether the following processes are running. Aside from security tools, this list also includes other monitoring tools that can help detect mining activity:
- aida64.exe
- AnVir.exe
- anvir64.exe
- GPU-Z.exe
- HWiNFO32.exe
- HWiNFO64.exe
- i7RealTempGT.exe
- OpenHardwareMonitor.exe
- pchunter64.exe
- perfmon.exe
- ProcessHacker.exe
- ProcessLasso.exe
- procexp.exe
- procexp64.exe
- RealTemp.exe
- RealTempGT.exe
- speedfan.exe
- SystemExplorer.exe
- taskmgr.exe
- VirusTotalUpload2.exe
It will then spawn the Tor binaries to start with coinmining.
 Figure 13. helper.exe spawning tor binaries
Figure 13. helper.exe spawning tor binaries
Recommendations
The sudden need to transition to a work-from-home setup left enterprises with little time to ramp up security measures to ensure that it fits the requirements demanded by remote work. It also exposes businesses to possible compromise due to threat actors abusing tools like video conferencing apps to propagate malware.
Users are advised to only download installers from applications’ official websites to avoid such compromise. Users should also follow best practices for securing work-from-home setups. A multilayered protection approach is also recommended to effectively detect and block threats regardless of where they are in the system.
Indicators of Compromise
URL
- 2no(.)co/1IRnc
- hxxps://2no(.)co/1O5aW
Hashes
| SHA-256 | Trend Micro Pattern Detection | Trend Micro Predictive Machine Learning Detection |
|---|---|---|
| d65e8a784c2ba0d9f7a029e1817b78b31324fb8c988e0467fd693b0efd890756 (Installer) | Trojan.Win32.MOOZ.THCCABO
|
Troj.Win32.TRX.XXPE50FFF034 |
| 04b560d234e8706d5e43532e9e674ee54ed6f63d62795fb0e5776e23da7eb4d8 (64.exe payload) | Coinminer.Win64.MOOZ.THCCABO | N/A |