Malware
Raccoon Stealer’s Abuse of Google Cloud Services
Raccoon emerged as Malware as a Service (MaaS) last April 2019. Despite its simplicity, Raccoon became popular among cybercriminals and was mentioned as a notable emerging malware in underground forums in a malware popularity report.
Raccoon emerged as Malware as a Service (MaaS) last April 2019. Despite its simplicity, Raccoon became popular among cybercriminals and was mentioned as a notable emerging malware in underground forums in a malware popularity report.
The malware is capable of stealing login credentials, credit card information, cryptocurrency wallets, and browser information. Raccoon has basic infostealer functions but an aggressive marketing campaign and overall good user experience proved enough to make up for its lack of additional features. The service is also relatively cheap, with a price that ranged from US$75 per week to $200 per month.
It can arrive on a system through different delivery techniques such as exploit kits, phishing, and bundled with other malware. In this blog entry we investigate campaigns that used the exploit kits Fallout and Rig, where we also observed its use of Google Drive as part of its evasion tactics.
Exploit kits
We have recorded the Rig exploit kit and two cases that used the Fallout exploit kits being used to drop the Raccoon stealer in July and October 2019. The infection chain of these three cases are summarized in the table below.
| Fallout October 31, 2019 |
Fallout October 10, 2019 |
Rig July 15, 2019 |
|
| Arrival | Malvertisement maximili[.]com (173.254.98.143) |
Malvertisement hxxps://biome.es/php.php (31.31.198.19) |
Ad Network hxxp://p201298[.]mybetterdl[.]com/adServe/domainClick?{redacted} hxxp://mybetterdl[.]com/aS/feedclick?{redacted} |
| Redirector | hxxps://coliqiou[.]com/gzJrZZ?&se_referrer= (5.188.60.95) | hxxp://makemoneyeazywith[.]me/?utm_trc=ASIA{redacted} | |
| EK URL | hxxp://getyourfree[.]cloud/3966/rerelease-8383/24-07-1920[.]aspx (134.209.185.112) | hxxps://germanrights4u[.]com/2010-03-08/ypiNv/unengaged?PdohQ=UEmE (104.248.32.22) | hxxp://185[.]246[.]65[.]115/?MzkxMTg3&pbcHJYg&Cb{redacted} |
| Racoon malware dropped (SHA256) | c0127722274b1b821443ee5d6a8f59e7d01e75eb32c41b8a74a11e950d6bbf80 | 697706505adf5b5d051eddb1047cd158f6488c54a113a71c0a38942c7d29d91e | 1f2f7f34743b5869f37398d0427875bc34b4244d6094298aa828a6af63730b72 |
| C&C Server | hxxp://35[.]189[.]105[.]242/file_handler/file[.]php?{redacted} | hxxp://34[.]89[.]185[.]248/file_handler/file[.]php?{redacted} | hxxp://34[.]65[.]241[.]219/file_handler2/file[.]php?{redacted} |
Once the Raccoon malware infects a machine, it connects to a Google Drive URL to decrypt the actual C&C server. The format of the URL is hxxp://{IP}/gate/log.php, which logs the computer configuration information. Then, it will receive a JSON-formatted file containing the location dependencies. Next, it will connect to URL hxxp://{IP}/file_handler/file.php for data exfiltration. Finally, it downloads FoxMail-like components from /gate/libs.zip and a SQLite library for parsing the browser database from hxxp://{IP}/gate/sqlite3.dll.
We identified 67 IP addresses that act as its C&C sever. Based on the organization ID of the IP addresses we could see that the attackers used Google Cloud Services to host many of their C&Cs. This technique allows the attackers to evade detection as it pretends to be legitimate traffic coming from Google.
It is important to note that not all the IP addresses used by the malware were related to Google. For example, an IP from Lithuania (176[.]223[.]143[.]5) resolved a domain named raccoon-gate[.]site[.]. Other Raccoon samples were also found connected to this C&C server, which drops another malware, the infostealer Predator the Thief.
Spam campaign
We also recently detected a spike in MalSpam activity. Included in this detection are spam with attachments that drop the Raccoon malware (detected as TrojanSpy.Win32.RACEALER.M). The emails claimed that the recipient’s friend had their email hacked, either by the sender themselves or by some other group. The emails demand money in exchange for the stolen sensitive information they claim to have accessed.
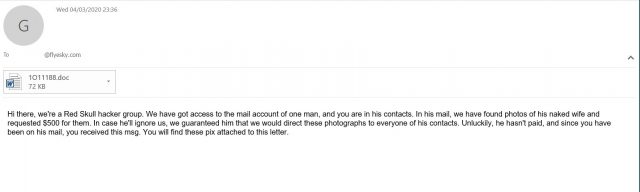
A sample from this campaign downloads the typical libraries required for its infostealing routines from the C&C server. Aside from downloading the libraries, the raccoon sample also downloads an executable binary from hxxp://hrcorp1[.]site/signed.exe. This component would then drop and extract an archive, help.zip, which contains the appropriately named evil.ps1 PowerShell script.

Impact and Activity
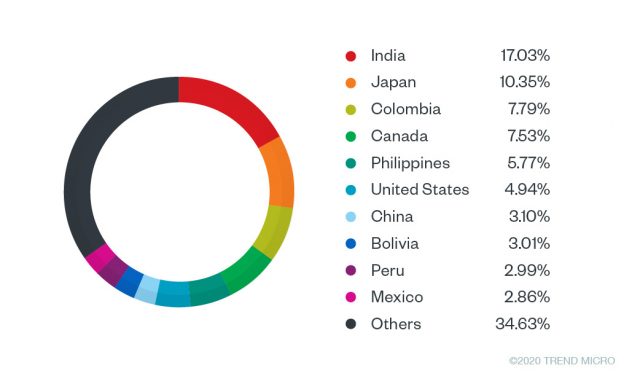
Since April 2019, we have detected more than 100,000 raccoon related events. We observed a peak in detections in July 2019 that could be reflective of the number of buyers who were then using the service. The most affected countries were India and Japan. India seems to be growing into a popular target for such schemes, as recently stolen cards had shown up for sale in the Jokerstash underground market. Other countries in the Americas were also affected, specifically Colombia, Canada, United States, Mexico, Bolivia, and Peru.
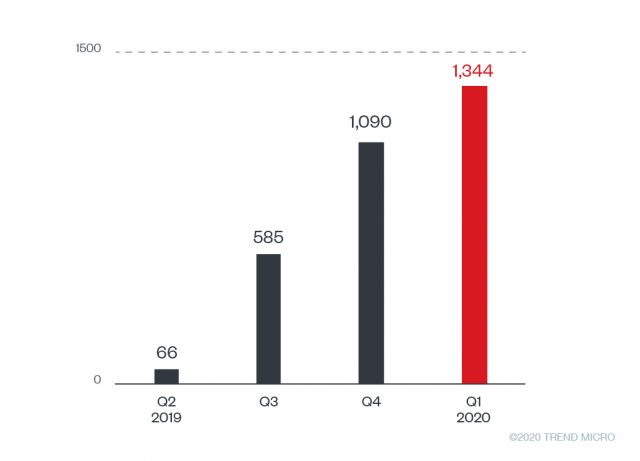
We have also identified over 3,000 unique binary samples of the Raccoon “Racestealer” stealer since the second quarter of 2019. There were several samples of the malware created, with the author continuing to release newer versions on underground forums since the first one came out.
Conclusion
Part of what makes the Raccoon MaaS popular among cybercriminals is the purported active “customer support” behind the service that makes up for the simple features. According the report by Cybereason, the MaaS received generally favorable reviews from those who have had the chance to use it. A number have described it as a suitable replacement to the discontinued AZORult stealer, which was popular during its heyday.
The current activity of the Raccoon malware seems to indicate that its development and use by threat actors will continue. The next best move for its creators would likely be to improve and fix some of its bugs, and then add new techniques to its relatively basic repertoire.
As creators work on developing Raccoon further, threat actors who have bought its services could be planning or deploying attacks using the version currently available in the underground market. Organizations should remain wary of the Raccoon malware and prepare defenses that take cues from the multiple deployment methods Raccoon has been known to employ.
Trend Micro Solutions
Organizations can take advantage of Trend Micro Apex One™ which provides actionable insights, expanded investigative capabilities, and centralized visibility across the network through a variety of threat detection capabilities such as behavioral analysis, which protect against malicious scripts, injection, ransomware, memory and browser attacks.
Trend Micro™ Deep Discovery Inspector™ protects customers from this attack via this DDI rule:
- Rule 4364: “RACCOON – HTTP (REQUEST)”
Indicators of Compromise (IOCs)
| SHA256 | Detection Name |
|---|---|
| 3787e7d0d8fd8496bf1425a05dddf8f6f0fee7d8782a2e6bd46a91239986171f | TrojanSpy.Win32.RACEALER.E |
| 48957252e011d2763e6f9ec5499e011d38c9f06b1c3fb6084c0255422d01dafe | Trojan.Win32.RACEALER.AB |
| 6e2bcde33b15acb157a38a857b5391d497a3f647ee02cb7da76cb82cb9b434f2 | TrojanSpy.MSIL.RACOONSTIL.A |
| b4fbcced40a53bf818d6d13d0dde9147ddd17e423fe4d3d2a80401035b571112 | TrojanSpy.Win32.RACEALER.M |
| URLs |
|---|
| hxxp://drive[.]google[.]com/uc?export=download&id=1QQXAXArU8BU4kJZ6IBsSCCyLtmLftiOV – contains encrypted C&C server URL |
| hxxp://35[.]228[.]215[.]155/gate/log[.]php |
| hxxp://35[.]228[.]215[.]155/gate/sqlite3[.]dll |
| hxxp://35[.]228[.]215[.]155/gate/libs[.]zip |
| hxxp://35[.]228[.]215[.]155/file_handler/file[.]php?hash={redacted} |
| hxxp://34[.]77[.]125[.]60/gate/sqlite3[.]dll |
| hxxp://34[.]77[.]125[.]60/gate/libs[.]zip |
| hxxp://hrcorp1[.]site/signed[.]exe |

