Updated as of May 7, 2019, 6:30PM PDT to inlcude an updated TippingPoint MainlineDV filter/rule as well as clarify descriptions on opening a new duplicate tab and how the vulnerability is triggered manually.
A zero-day extensible markup language (XML) external entity (XXE) injection vulnerability in Microsoft Internet Explorer (IE) was recently disclosed by security researcher John Page. An attacker can reportedly exploit this vulnerability to steal confidential information or exfiltrate local files from the victim’s machine. Page tested the vulnerability in the latest version of IE (11) with current patches on Windows 7 and 10, and Windows Server 2012 R2 operating systems. We looked at its attack chain to better understand how the security flaw works and how it can be mitigated. XXE injection works by exploiting an XML parser with an improperly restricted XML external entity reference (CWE-611), which is used to access unauthorized content.
XXE injection also exploits misconfigured document type definition (CWE-827) used to define document types for markup languages like XML. For example, an attacker can use a malicious XML file with external entity reference that abuses the ‘file://’ protocol to access local files, or ‘http://’ to access files on web servers.
In the case of the vulnerability reported by Page, the security flaw is triggered when a specially crafted MIME HTML web archive (.mht) file is opened and the user interacts with the browser, with actions such as opening a new duplicate tab in IE (Ctrl+K) or printing a file (Ctrl+P). However, the user interaction can be simulated by JavaScript functions like window.print(). Once the user opens the malicious .mht file, the attacker would be able to exfiltrate files from the user’s system. Note that successfully exploiting this flaw relies heavily on social engineering. For instance, attackers have to lure the user into downloading a malicious .mht file and manually triggering the vulnerability (i.e., opening the file).
Page disclosed the vulnerability, and we shared our analysis to Microsoft, which released this official statement: “Internet Explorer alone does not permit this type of malicious behavior. An attacker must trick or convince a user into downloading a malicious document through a socially engineered scheme, for example a spam email attachment or phishing campaign that triggers a download. The file must then be opened with the browser. To guard against this scheme, practice safe computing habits online, such as avoid downloading and opening untrusted files from the Internet.”
Vulnerability impact
An attacker who successfully exploits this vulnerability could gain access to sensitive files on the user’s system. Successful exploitation could also provide reconnaissance information that can be used to execute more attacks or launch more payloads. For instance, it can divulge the client’s installed applications, network configuration, privileges, and details of antivirus protection to an attacker. The attacker could then use the obtained information to gain a foothold into the affected system's network.
While XXE injections/attacks aren’t new, they could pose significant security risks. In fact, XXE attacks are listed among Open Web Application Security Project’s (OWASP) top security risks to applications and features in popular software or tools. The abuse of .mht files as an attack vector is also notable, as it’s also known to be abused by exploit kits and threats like information stealers.
Attack chain analysis
In order for the security flaw to be exploited, a malicious XML file has to be placed in the attacker’s hypertext transfer protocol (HTTP) server. This XML file should mention the specific files that need to be exfiltrated from the user’s system in the ENTITY tag, which represents a request or response in HTTP messages. In turn, the corresponding file needs to be referred as an external entity in the malicious MHTML file, which the users could manually execute on their machines.
Figure 1. A malicious XML file that specifies the files to extract from the user’s system
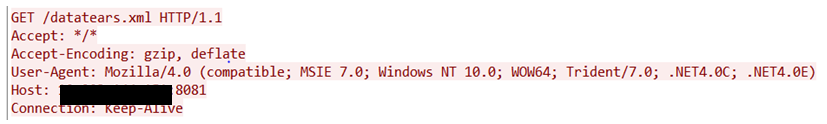
The attacker must convince the user to download the malicious MHTML file through external attack vectors, such as socially engineered spam email attachment or phishing. The email client must then open the malicious file with IE. Note that IE is the default application used to open MHTML files on all versions of Windows and so the user does not need to specify the application. As shown in Figure 3, the vulnerable IE client will send a GET request to the attacker’s server to retrieve the malicious XML file once the malicious MHTML file is opened.
Figure 2. Sample MHTML file that uses the XXE vulnerability in IE to download a malicious XML file from the attacker’s machine
Figure 3. Packet capture of first request sent from the client to the attacker’s server to get the malicious XML file
As can be seen from Figure 1, the malicious XML file contains details of files specified for exfiltration, along with the uniform resource identifier (URI) of the attacker-controlled server. The contents of the files that the attacker referenced in the malicious XML are sent back to the attacker’s server as per the URI path mentioned in the same XML file. This will then be displayed on the attacker’s end.
 Figure 4: Packet capture of the second request sent from the client to the attacker’s server that sends the contents of the attacker’s target file
Figure 4: Packet capture of the second request sent from the client to the attacker’s server that sends the contents of the attacker’s target file
Trend Micro solutions
As of this writing, Microsoft has not released a fix for this vulnerability. Users should exercise caution when opening any file from an unknown sources. Successfully exploiting the vulnerability entails enticing users to open malicious files. Avoid clicking links or downloading and opening files from unsolicited sources. Ensure that the operating system and applications have the latest security updates (or use virtual patching for legacy systems). System administrators, developers, and programmers should also adopt best practices. OWASP, for instance, has a list of recommendations for preventing XXE issues.
The Trend Micro™ Deep Security™ and Vulnerability Protection solutions protect user systems from threats that may exploit this vulnerability via the following DPI rule:
- 1005676 – Identified Download Of XML File With External Entity Reference
Trend Micro™ TippingPoint™ customers are protected from this vulnerability via this MainlineDV filter:
- 35016: HTTP: Internet Explorer MHT XXE Information Disclosure Vulnerability