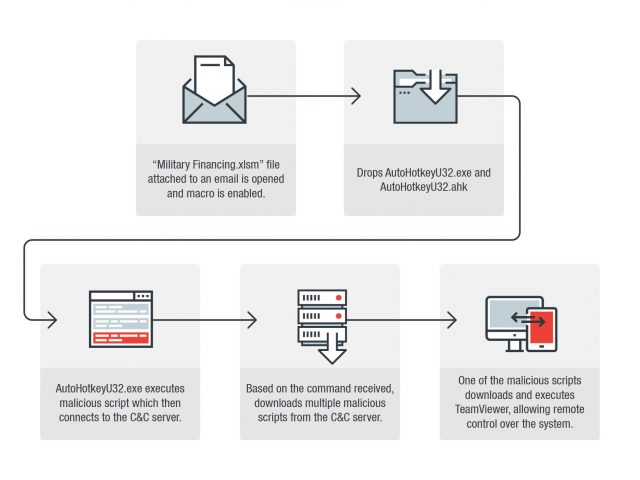
We discovered a potential targeted attack that makes use of legitimate script engine AutoHotkey, in combination with malicious script files. This file is distributed as an email attachment and disguised as a legitimate document with the filename “Military Financing.xlsm.” The user would need to enable macro for it to open fully, which would use AutoHotkey in loading the malicious script file to avoid detection. It will then enable the threat actors to steal certain information and even download TeamViewer to gain remote access to the system.
If the user enables macro to open the xlsm file, it will then drop the legitimate script engine AutoHotkey along with a malicious script file. Once the AutoHotkey loads the malicious script file, it connects to its C&C server to download and execute additional script files in response to commands from the server. In our observation, it lastly downloaded and executed TeamViewer to gain remote control over the system. However, it can download and execute other script files depending on the command it receives from the C&C server.
Figure 1. Attack chain starting with the arrival of the email with the malicious attachment
The Excel File
The attached excel file is titled “Foreign Military Financing (FMF),” named after a program of the U.S. Defense Security Cooperation Agency. This cover was likely used to further push users to enable content so that they can access confidential information.
Figure 2. Content of the Excel file
At first glance, the excel file seems to only have one filled sheet. However, as can be seen in figure 2, it has another sheet inconspicuously named with a “ ” or a blank space.
Figure 3. HEX strings in the second sheet originally “hidden” using white font
Once the user enables macro for this file, it drops two files through the HEX strings written as binary text in two columns of the blank space sheet. These HEX strings are originally written in white font, to make it appear as if the columns were blank. These dropped files are:
- Content of column X: 「C:\ProgramData\AutoHotkeyU32.exe」(legitimate AutoHotkey executable file)
- Content of column Y: 「C:\ProgramData\AutoHotkeyU32.ahk」(malicious script for AutoHotkey created by the attacker)
The malicious string and abuse of AutoHotkey
Depending on the script files, the AutoHotkey application can assign a hotkey or execute any process written in the script file. In this case, the script file AutoHotkeyU32.ahk does not assign a hotkey but it does execute the following commands:
- Create a link file in the startup folder for AutoHotkeyU32.exe, allowing the attack to persist even after a system restart.
- Connect to the C&C server every 10 seconds to download, save, and execute script files containing the commands.
- Send the volume serial number of the C drive, which allows the attacker to identify the victim.
Figure 4. A partial code snippet of AutoHotkeyu32.ahk
Figure 5. A sample C&C response
When the attacker sends a response similar to that shown in the figure 5 sample via the C&C, the script file converts the HEX strings into plain text, which translates to the URL “001::hxxp://185.70.186.145/7773/plug/hscreen.ahk.” Then it downloads the ahk file (hscreen.ahk) from this URL, saves the file in “%temp%” folder using a random filename, and finally executes it by loading it through AutoHotkeyU32.exe. The URL was no longer available at the time of writing.
Further research uncovered other dropped files involved in this attack. These files allow the attackers to get the computer name and take screen captures. More importantly, one of these files also enables the download of TeamViewer, a remote access tool that gives threat actors remote control over the system.
We have yet to conclude this attack's exact purpose. For now, we can surmise that it has the makings of a potential targeted attack because of its cyber espionage capabilities, as well as the potential for delivering ransomware and coinminer.
Security recommendations
As we continue to monitor this attack users can re-asses their security measures against similar cases. Against most attacks, users should implement a multilayer defense and have mitigation protocols in place to detect and address intrusions. Users should also take full advantage of their network defense solutions by enhancing settings, especially for macro malware attached emails.
Such attacks highlight the need for caution before downloading files from unknown sources and enabling macro for files from unknown sources. Microsoft provides several security notifications about enabling content.
Other best practices:
- Consistently check the sender, title, and body for any suspicious details before downloading and opening an attached file.
- Always check the extension of any attached file to see if it is consistent with the received email.
- Before enabling content to open a file, check for red flags such as content that urges the user to enable macro, or content that appears blank.
Indicators of Compromise (IoCs)
| SHA256 | Filename | Detection name | Description |
| EFE51C2453821310C7A34DCA3054021D0F6D453B7133C381D75E3140901EFD12 | Military Financing.xlsm | W2KM_HTV.ZKGD-A | Carries the malicious script and AutoHotkeyU32.ahk |
| 43FBDA74A65668333727C6512562DB4F9E712CF1D5AD9DCA8F06AE51BB937BA2 | hscreen.ahk | TSPY_HTV.ZJGD-A | Takes screen captures |
| ACB3181D0408C908B2A434FC004BF24FB766D4CF68BF2978BC5653022F9F20BE | AutoHotkeyU32.ahk | BKDR_HTV.ZKGD-A | Loads the malicious script |
| BE6C6B0942AD441953B0ED0C4327B9DED8A94E836EACA070ACA3988BADB31858 | hinfo.ahk | TSPY_HTV.ZLGD-A | Gets the computer name |
| F64792324839F660B9BDFDA95501A568C076641CF08CE63C1DDBE29B45623AC0 | htv.ahk | TROJ_HTV.ZJGD-A | Downloads and executes TeamViewer |
C&C
185[.]70[.]186[.]145