Banks are offering more features and upgrades for their banking apps, and thanks to their convenience more users are adopting mobile banking services around the world. But as new financial technology proliferates and users start to look for apps and other services from their particular bank, opportunities for scammers also increase. One recent example of this is the app Movil Secure. We found this malicious app on Google Play on October 22, as part of a SMiShing scheme targeting Spanish-speaking users.
Movil Secure is a fake banking app pretending to be a mobile token service. Its developers evidently put in the effort to trick users into thinking it is legitimate, with professional-looking branding and a sophisticated user interface. We also found three other similar fake apps under the same developer. Google has already confirmed that these apps have been removed from Google Play.
Movil Secure was published on October 19, and there were over 100 downloads in a six-day period. The number of downloads is likely because the app claims to be connected to Banco Bilbao Vizcaya Argentaria (BBVA), a popular Spanish banking group with multinational ties. This bank is actually known for being pro-technology, and its real mobile banking app is considered one of the industry’s best.
The fake app (seen in Figure 1 below) capitalized on BVVA’s prominence and posed as the bank’s service for mobile banking tokens — used in identity management and transaction authorization — but a closer review reveals that it doesn’t have any of the functionality it claims to have.
Figure 1. The app claimed that it is digital token
The app is for Spanish-speaking users and claims that it is used to identify and then authorize transactions for customers of the BBVA bank. However, after analyzing its capabilities and behavior we can classify it as spyware. It is still very simple, which may indicate that it is a pilot app published on Google Play.
What the app does and how it affects victims
When the app first launches, it gathers device identifiers: device ID, OS version, and Country Code. Then it sends all the information to its command and control (C&C) server. It also hides itself from the user’s view — there is no icon on the mobile phone screen.
Figure 2. The snapshot of device identifier collection
We saw a simple sign-in portal when we accessed the C&C server, indicating that attackers developed a complete management system to analyze and organize the collected data. It is also a sign that they might be organizing all that data to initiate a campaign.
Figure 3. Sign-in page for command and control server
The data it collects isn't limited to device identifiers. The app also collects SMS messages and phone numbers; analyzing the code of this app shows that this is the main goal of this spyware. As seen below (in Figure 4), when a device with the app installed receives a new SMS, it sends the SMS sender and message content to the C&C server and a specific phone number. This type of information is quite valuable—SMS is often used by mobile banking apps to confirm or authorize banking transactions.
Figure 4. The snapshot of SMS collection
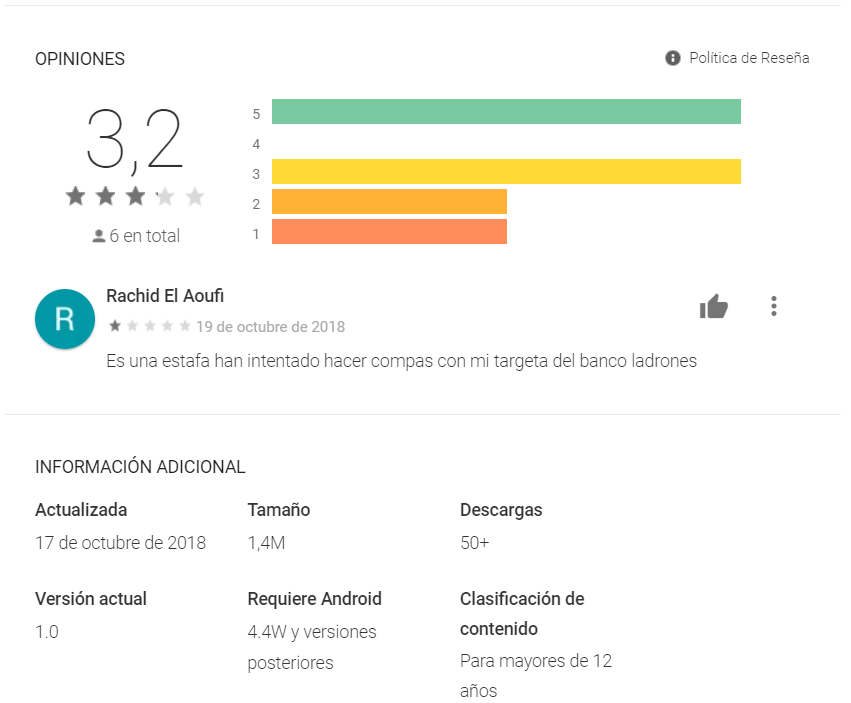
The actors behind the app have already started using the data they’ve collected for SMiShing attempts. In a post in the app's reviews section, one commenter said it was a scam that targeted his bank card.
Figure 5. Review claiming the app is a scam
A look into the developer's details reveals three similar fake apps (as seen in Figure 6) under their name. Evo and Bankia are popular Spanish banks, while Compte de Credit isn’t connected to any large financial institution. These three apps were published on October 19, the same time as Movil Secure. Analysis revealed that the apps have the same routine as Movil Secure — collect identifiers and SMS data, then send to the C&C server.
Figure 6. Other fake apps with the same developer
Trend Micro SolutionsWe suspect that the data taken from these apps may be used for further SMiShing attacks, or in other attempts to collect banking credentials from customers of these Spanish banks. So far, we have uncovered the capabilities of this version of the spyware, but we will continue to monitor and track its evolution. Users should be wary of downloading apps that are linked to bank accounts, and should always check if they are legitimately connected to the bank. Devices should also be equipped with comprehensive mobile security that can mitigate mobile malware. Trend Micro Mobile Security detects all related threats in this attack. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies, protecting users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
Indicators of Compromise
Detected as AndroidOS_FlokiSpy.HRX:
- b168e64a02c3aed52b0c6f77a380420dd2495c3440c85a3b7ed99b8ac871d46a
- d8018d869254abd6e0b2fb33631fcc56c9f2e355c5d6f40701f71c1a73331cb3
- 299e1eb8a1f13e1eb77a1c38e5cf7bbdc588db89d4eaad91e7fc95d156d986e5
- 24e7a8ed726efa463edec2e19ad4796cf4b97755b8fdf06dea4950c175c01f77
C&C:
- hxxps://backup.spykey-floki.org/add.php