Cyber Threats
Examining CONFICKER/DOWNAD's Impact on Legacy Systems
Despite being nearly a decade old, DOWNAD (also known as CONFICKER) has not gone away. Nine years after its first discovery, we take a look at where DOWNAD is today, and why it is still one of the world’s most prevalent malware.
The banking trojan known as DOWNAD (Detected by Trend Micro as DOWNAD family) first appeared back in 2008, where it managed to be one of the most destructive malware at the time, infecting up to 9 million computers and gaining worldwide notoriety. Despite being nearly a decade old, and years past its peak, DOWNAD, also known as CONFICKER, has not gone away. 9 years after its first discovery, we take a look at the numbers to see where DOWNAD is today, and why it is still one of the world’s most prevalent malware.
Taking a look at the numbersAt its peak, DOWNAD had massive infection rates, with total global estimates reaching up to 9 million. Taking a look at the number four years later, DOWNAD was still the top malware for the year, with 2,564,618 detections across the globe. The malware slipped in 2013, with WORM_DOWNAD registering a considerable drop in detections from 741,000 in the first quarter, to 229,000 in the 4th quarter – which we attributed to more people migrating from older Windows operating systems to newer ones, thus less chance for vulnerability exploitation. Still, WORM_DOWNAD emerged as the top malware of 2013, with 1,824,000 detections. The trend continued in 2014 and 2015, where DOWNAD still proved to be among the top 2 malware infectors for the year for both enterprise and SMBs, with 288,374 and 298,000 infections, respectively.
Figure 1: Tracking the detections for DOWNAD from 2012 to 2016
Although DOWNAD has calmed down considerably since its peak, the Trend Micro™ Smart Protection Network™ data for DOWNAD from 2016 and 2017, shows a consistency over time --- the malware has stayed above 20,000 monthly detections for both years, which means that in terms of detections, it is still highly active.
This rate has stayed consistent year on year. From the past two years alone, we see that infection rates for the WORM_DOWNAD.AD detection stays consistent with relatively shallow spikes and dips:
Figure 2: Monthly WORM_DOWNAD.AD detections for 2016 and 2017
There there are three major industries where DOWNAD’s presence can be felt: government, manufacturing and healthcare, which make up 34% of all WORM_DOWNAD.AD detections in 2016, and 41% of all detections in 2017. These industries are typically made of organizations that focus more on their own specific operational expertise, and spend less resources on technological upgrades than companies involved in “tech heavy” industries such as software or outsourcing. In addition, the size and complexity of the organizations in these industries mean that upgrading their systems will require a large amount of time and resources. These are all important points that will help show why DOWNAD thrives in these industries.
Figure 3: WORM_DOWNAD.AD detections across different industries in 2016
Figure 4: WORM_DOWNAD.AD detections across different industries in 2017
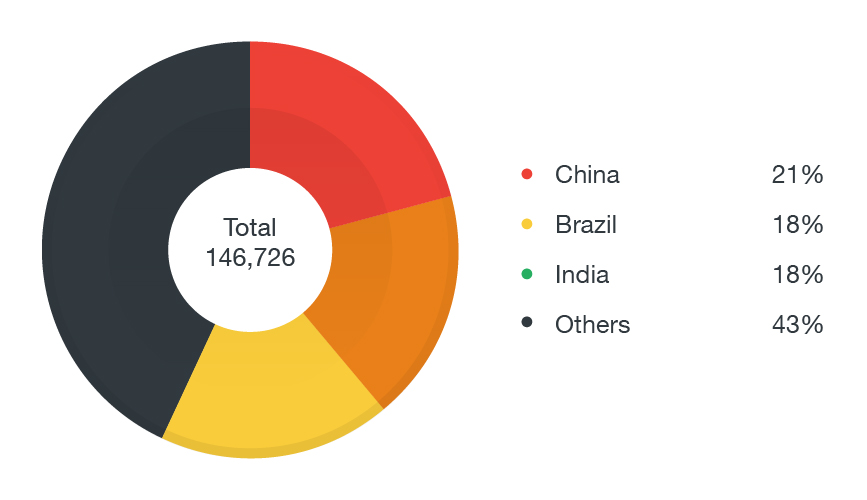
Delving further into the specific regions, we again take a look at our top detection, WORM_DOWNAD.AD, and where it was most prevalent. We are also able to see a consistent pattern: the top countries affected for both 2016 and 2017 are developing countries, notably in the BRICS bloc -- India, China, Brazil, which are well known for their tremendous growth as well as their robust manufacturing sectors.
Figure 5: Top 3 Countries affected by WORM_DOWNAD.AD in 2016
Figure 6: Top 3 Countries affected by WORM_DOWNAD.AD in 2017
According to our Smart Protection Network data, the most prevalent detection of DOWNAD is the older variant known as WORM_DOWNAD.AD, which up to now is still among our most detected malware threats. Among the first variants to be detected in the wild, WORM_DOWNAD.AD propagates dropping copies of itself into physical and removable drives as well as by sending exploit code to randomly selected targets over the Internet.
Figure 7: WORM_DOWNAD.AD Infection Chain
Once it arrives on a target system, WORM_DOWNAD.AD will drop a copy of itself into the Recycle Bins of all drives in the systems connected to the infected machine’s removable and network drives. It then creates an obfuscated AUTORUN.INF file on the drives that allows it to execute whenever a user browses an infected network folder or removable drive (take note that this behavior is no longer possible in current versions of Windows). It will then retrieve user account data from the connected systems by enumerating the available servers on a network. As a final step, it will perform a dictionary attack using a predefined password list on these accounts. To prevent users from removing it from their system, WORM_DOWNAD.AD will modify the computer’s DNS settings to prevent users from visiting antivirus-related websites that contain specific strings.
If successful, WORM_DOWNAD.AD exploits the CVE-2008-4250 vulnerability (patched in October 2008) that will allow attackers to remotely execute code on the target’s system. Given WORM_DOWNAD.AD’s ability to propagate via multiple avenues, it’s not surprising that the malware manages to still be relevant, 9 years after its peak.
Given that we know which detection of DOWNAD is the most prevalent, let’s delve deeper into where exactly the worm can be found.
Why is DOWNAD still prevalent after all these years?Despite being nearly a decade old, DOWNAD is still rather prevalent. But why is an old malware, with years of security solutions created to combat it, still highly effective? In addition to its propagation technique, we are also able to see clues in the data itself.
In a report involving DOWNAD infecting IoT devices, the malware was able to slip through the cracks unnoticed by exploiting systems using older, unpatched versions of Windows, which many modern security systems are unable to adequately protect. This shows that one of the areas in which DOWNAD thrives are systems which rely on legacy software – notable ones that are not updated regularly. In addition, DOWNAD exploits an older vulnerability, one that has been patched since 2008. Again, common sense dictates that given the time in which this has been addressed, only a small number of systems can still be exploited using this vulnerability. However, our data paints a different picture-- in fact, CVE-2008-4250 dominates our detections for vulnerabilities, with over 60,000 for the month of October 2017 alone.
All these clues paint a picture of the typical DOWNAD victim: organizations in key industries, typically from developing countries, that use outdated, unpatched legacy systems as an integral part of their network.
The key takeaway here is that 9 years after its peak, DOWNAD has settled down into a comfortable niche of being a highly effective “background” malware that has its greatest impact on legacy systems. Although it is not as exciting to the public eye as more modern malware such as WannaCry and Petya, it remains a persistent threat – and will continue to be as long as unsupported, unpatched legacy systems are still a regular part of an organization’s network.
How can organizations prevent malware like DOWNAD?Tried and true security measures go a long way towards protecting both users and organizations from a malware like DOWNAD.
- Even organizations that don’t place heavy emphasis on security can protect themselves from DOWNAD. By properly scanning removable drives and ensuring they are not infected, companies can greatly minimize its impact.
- Organizations should refrain from using outdated operating systems. Especially those that are no longer supported such as Windows XP. The recent WannaCry attacks, which exploited vulnerabilities in older operating systems, were a perfect example of why using unsupported systems can result in a security disaster.
- We cannot stress enough the importance of updating computer systems. The fact that an old malware exploiting an old vulnerability is still one of the top detections in 2017 is proof that not enough is being done in this regard.
Updating long-time entrenched computer systems can be a drain on both manpower and resources. Ideally, an organization will move on from an operating system or software when they are no longer supported by its manufacturer. However, as seen in the large number of users who are still using the 16-year old Windows XP, it’s not really something that can be realistically expected from everyone. Key challenges emerge when trying to migrate from legacy systems:
- It will entail a large amount of time, resources and effort
- Legacy applications may not properly run on newer operating systems
- An organization’s IT professionals may not have the skills, knowledge or expertise to perform migration
- Rewriting applications – especially when major changes need to made-- may not be cost-effective or efficient
Fortunately, there is a way for organizations that are unable, or unwilling to upgrade their legacy systems to protect them from malware like DOWNAD: virtual patching.
In essence, virtual patching is ideal for mitigating the impact older malware like DOWNAD which exploit vulnerabilities. It protects legacy systems by providing convenient and automatic updates, allowing organizations to maintain protection while minimizing their patch management costs. It can protect a wide variety of devices and systems, making it a versatile method of protecting the entire network.
Trend Micro™ Deep Security™ and Vulnerability Protection provide virtual patching that protects endpoints from threats like DOWNAD that abuses vulnerabilities. OfficeScan’s Vulnerability Protection shield endpoints from identified and unknown vulnerability exploits even before patches are deployed.
TippingPoint helps organizations manage their legacy systems and control their patch management life cycle by providing added protection for legacy, out-of-support software, delivered weekly or when critical vulnerabilities emerge. This process is automated, as Digital Vaccine filters can be deployed automatically without user interaction.