Mobile
Toast Overlay Weaponized to Install Android Malware
A new Android malware can install other malware on affected devices via the Toast Overlay attack: TOASTAMIGO. The malicious apps abuse Android’s Accessibility features, enabling them to have ad-clicking, app-installing and other capabilities.
Updated as of November 16, 2017, 6:30PM PDT to clarify the number of installs in one of the malicious apps.
We uncovered new Android malware that can surreptitiously install other malware on the affected device via the Toast Overlay attack: TOASTAMIGO, detected by Trend Micro as ANDROIDOS_TOASTAMIGO. The malicious apps, one of which had installs between 100,000 and 500,000 as of November 6, 2017, abuses Android’s Accessibility features, enabling them—at least for now—to have ad-clicking, app-installing and self-protecting/persistence capabilities.
Overlay attacks entail drawing and superimposing Android View (i.e., images, buttons) atop other running apps, windows or processes. A typical scenario for a Toast Overlay attack is to employ it to trick the user into clicking a window or button specified by the attacker instead of the legitimate one. The technique, which was demonstrated earlier this year, leverages a vulnerability in Toast (CVE-2017-0752, patched last September), a feature in Android used to display notifications over other applications.
TOASTAMIGO is the first we’ve seen to weaponize this proof of concept, and like many before it, we’re bound to see this threat (and the other malware that it downloads/installs) being fine-tuned—given the malware’s relatively low-key functionalities as of this time—or mimicked by other cybercriminals. All versions of Android OS except the latest (8.0/Oreo) are affected, so users with earlier versions are urged to update and patch their device.
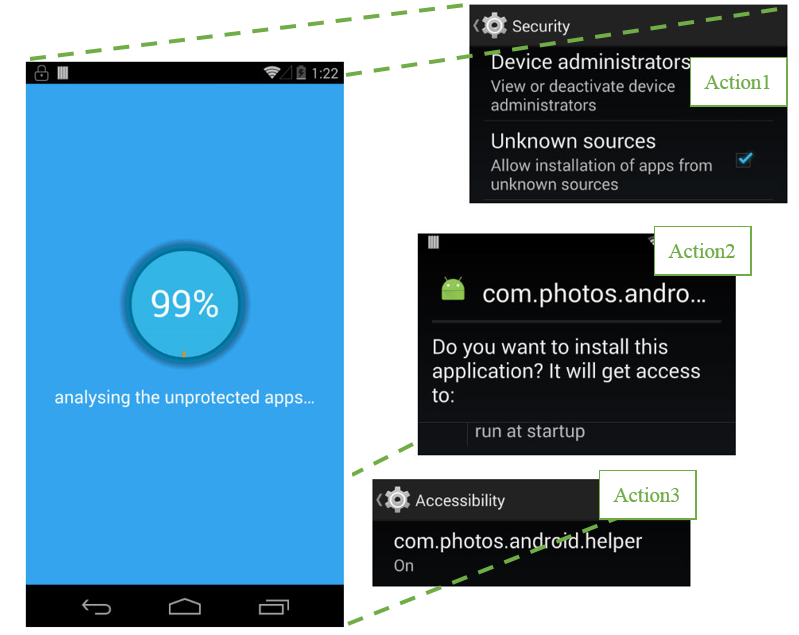 Figure 1: An illustration of how the Toast overlay attack works: an apparently benign image (left) is superimposed over actual actions the malware triggers, such as requesting for Accessibility permissions
Figure 1: An illustration of how the Toast overlay attack works: an apparently benign image (left) is superimposed over actual actions the malware triggers, such as requesting for Accessibility permissions
 Figure 2: The malicious apps on Google Play
Figure 2: The malicious apps on Google Play
Infection ChainThe malware ironically poses as legitimate app lockers that supposedly secure the device’s applications with a PIN code. Upon installation, these apps will notify the user that they need to be granted Accessibility permissions for it to work. It's all a ruse to sidestep Android’s countermeasure that requires apps to have explicit user permission. After granting permissions, the apps will launch a window to purportedly "analyze" the apps. Behind the scenes, however, the apps carry out actions or commands, including the installation of a second malware (since it already has the permissions).
 Figure 3: Screenshots of the malware’s “running time”
Figure 3: Screenshots of the malware’s “running time”
Technical AnalysisThe malicious apps were already packed before they were published in Google Play, as shown below. Note the strings from the package structure: “amigo” and “goami”, which are all under “com”, indicating that both apps were made by the same developer.

Figure 4: Package structure of the malware
The Toast Overlay attack is carried out when the apps purportedly note that it’s “analyzing the unprotected apps.” The screenshot below shows the code snippet for this function. It's actually a TOAST-type window, set as full screen in the malware:
- v2.type value 2005 is TYPE_TOAST
- v2.SystemUiVisibility value 1280 means SYSTEM_UI_FLAG_LAYOUT_FULLSCREEN and SYSTEM_UI_FLAG_LAYOUT_STABLE
- v2.flags’ value means FLAG_FULLSCREEN and FLAG_NOT_FOCUSABLE
 Figure 5: Code snippets showing how the apps employ Toast Overlay
Figure 5: Code snippets showing how the apps employ Toast Overlay
To launch an overlay attack, malicious apps will typically request the “draw on top” permission; this has been the case with Android versions up to 6.0 (Marshmallow), and if installed from Google Play, they are exempted. We found, however, that this affects all versions of Android except 8.0 (Oreo), since Toast overlays (and in turn the malware that employs this technique) don’t require specific permissions or conditions.
Executing Malicious TasksWe renamed some key functions when we analyzed the apps’ codes for readability. The function doBackgroudTask.getInstance((Context)this).doTask facilitates the execution of certain tasks in the background, and is designed to bypass various warning dialogs for different Android versions.
Figure 6: Code snippet of the malware’s background task code (highlighted)
The malware also has several functions executed behind the Toast window, including actions to keep itself from being removed in the device:
- com.photos.android.helper: Download a specified Android application package (APK)
- force_stop_MC: Forcibly stop mobile security apps
- bgAsprotectDialog: Prepare actions for dialog prompts, such as “Unknown sources”
- bgAutoInstallPage_4: Install an APK via Accessibility
- Accessibility: Open the Accessibility permission for the other APK
These functions maintain the malware’s core services:
- bgGpAutoProtect: Keep itself from being uninstalled
- bgAsprotectDialog and bgAsprotectPage_4: Keep its Accessibility permissions
The downloaded and installed app is named com.photos.android.helper, with the package name, com.vpn.free.migovpn. We renamed this into AMIGOCLICKER (ANDROIDOS_AMIGOCLICKER): TOASTAMIGO’s offshoot with ad-clicking routines. AMIGOCLICKER hides from the launcher and is instead found in the system’s Accessibility App list.
Figure 7: AMIGOCLICKER in the infected device’s Accessibility App list
AMIGOCLICKER can be automatically started by registered broadcast receivers. It can also be run by TOASTAMIGO invoking AMIGOCLICKER’s exported services, as shown below.
 Figure 8: AMIGOCLICKER’s exported services
Figure 8: AMIGOCLICKER’s exported services
Figure 9: Code snapshots where AMIGOCLICKER’s services are invoked
AMIGOCLICKER was also packed, and our analysis delved into its exported core services. It will first get the latest control information by accessing a remote server. It will then provide a proxy depending on the device’s current network connection, which helps some regions access networks like Admob and Facebook if they are initially not able to. Here are AMIGOCLICKER’s main behaviours, which share some similarities with TOASTAMIGO:
- force_stop: Forcibly stop mobile security apps
- open_device_manager: Open device administrator to prevent it from being uninstalled
- bgDeviceDeactivate: Prevent the device administrator from being disabled
- bgGpAutoProtect: Prevent the app from being uninstalled
- autoUninstall_setting: Uninstall specific packages
- bgAsprotectDialog: Keep its Accessibility permissions
- bgAsprotectPage_4: Keep its Accessibility permissions
- bgAutoCancelDialog: Click the cancel button on the system’s alert dialog
- bgAutoUninstallOnDesktop: Click the uninstall button from system’s alert dialog
- bgAutoSureDialog: Click a button when receiving a specified system dialog
- collect_gp_account: Collect victim’s Google account
- bg_auto_click_fb: Click a loaded Facebook ad
- gp_search_input_aso action1: Input and search in Google Play
- gp_search_input_aso action2: Give itself a five-star rating on Google Play
MitigationThe miscellany of the malware’s malicious functionalities, combined with a relatively unique attack vector, makes them credible threats. In fact, the aforementioned functionalities can actually be modified for further cyberattacks. Since TOASTAMIGO and AMIGOCLICKER can misuse Android’s Accessibility feature to virtually do anything, this malware can update itself when getting the remote server’s commands.
Google already patched the initial entry point—Toast Overlay—in their September Android security bulletin. Users are urged to patch their OS, and more significantly, practice good mobile security habits, especially if the device is under the workplace’s Bring Your Own Device programs. Updates on other Android devices apart from Nexus and Pixel are still fragmented, however, so users should contact their device’s original equipment manufacturer (OEM) for their availability.
We have notified Google of our findings, which promptly removed the malicious apps in Google Play. The appendix lists the indicators of compromise (IoCs).
Trend Micro SolutionsTrend Micro™ Mobile Security for Android™ (also available on Google Play) blocks malicious apps that may exploit this vulnerability. End users and enterprises can also benefit from its multilayered security capabilities that secure the device’s data and privacy, and safeguard them from ransomware, fraudulent websites, and identity theft.
For organizations, Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.
Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies. It can protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.




