The fraudulent redemption of freebies, discounts, and rebates in the form of coupons is reportedly costing U.S. businesses $300–600 million every year. And where there’s money to be made, there are cybercriminals rustling up schemes to take advantage of it. Unsurprisingly, that was the case when it comes to coupon fraud, which we found to be rife and thriving in the underground.
What does coupon fraud mean for businesses? In 2012, major manufacturers were victimized by counterfeit coupons, with one consumer goods corporation pegging its losses to around $1.28 million. Another coupon fraud scheme almost a decade in the making stole at least $250 million from companies.
The real-life costs are beyond claiming unlimited coffee, free car rides and hotel stays, or gadgets at bargain prices. Coupon fraud in the underground has the scalability that results to business process compromise, where the components underpinning business operations are undermined, which in turn significantly affect the bottom line.
Coupon Fraud and Business Process CompromiseThe coupon fraud schemes we saw in the underground were diverse. There are, however, ties that bind them—especially when business processes are concerned. Here’s a visualization:
 Figure 1: How the combination of cybercriminal underground services and coupon fraud work in compromising the business processes of a typical coupon transaction
Figure 1: How the combination of cybercriminal underground services and coupon fraud work in compromising the business processes of a typical coupon transaction 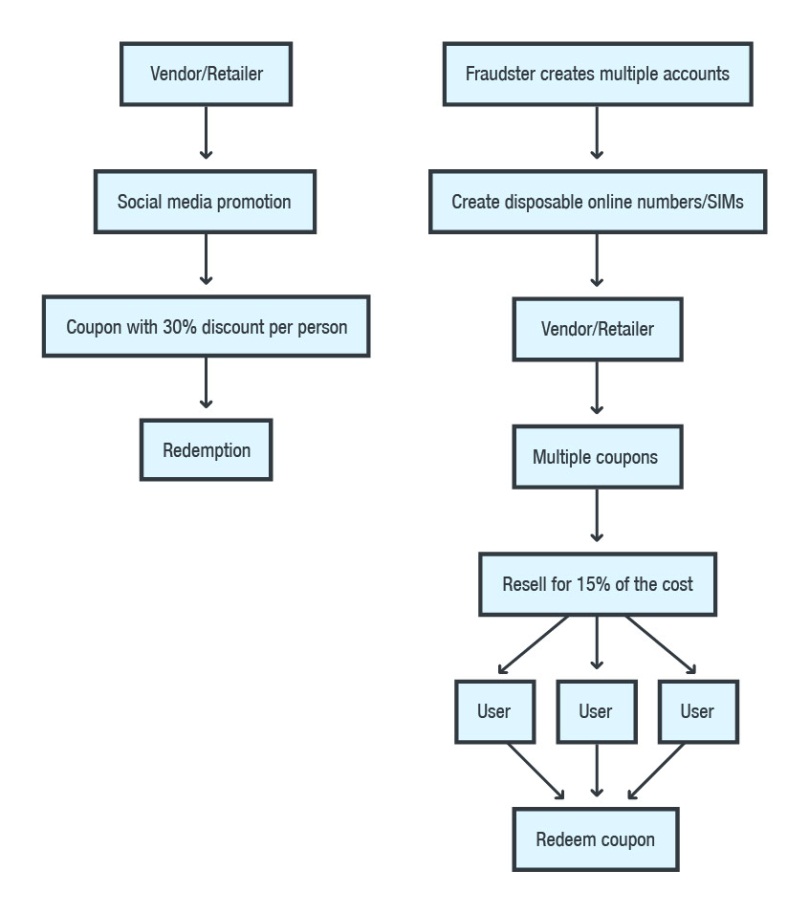 Figure 2: A graphical representation of how a normal coupon transaction works for a certain consumer goods vendor (left) and how the processes behind it are abused (right)
Figure 2: A graphical representation of how a normal coupon transaction works for a certain consumer goods vendor (left) and how the processes behind it are abused (right)
Coupon transactions typically entail data changing hands between the consumer, retailer/coupon provider, and a clearing house/agent that sorts and audits the coupons. Intermediaries are also often brought into the equation—an online coupon distributor, for instance, or a media service provider that promotes the coupons on the retailer’s behalf.
Indeed, there are many channels through which data travels—and it only takes one vulnerable layer to affect the whole supply chain. The underground has products and services specifically created to do that: brute-forcing coupon and promo codes by stealing or cracking their algorithms and exploiting vulnerabilities in code verification. Case in point: a researcher was able to exploit a “race condition” (where software relies on the sequence/timing of processes) in the web application that processes Starbucks gift cards. The result? Unlimited coffee.
Region or market-specific coupon/voucher codes were also abused. A purveyor in one of the forums we saw sold promo codes purportedly from a telecommunications company that gave its employees discounts on mobile voice, SMS, and internet data tariffs. Another attack chain involved misusing corporate rates hotels give to their client’s employees in the form of codes keyed in during the booking’s verification process.
That’s just the tip of the iceberg. Many of the products and services we saw in the underground involve the automation of fraud—scalable enough to drive an economy of fake or misused coupons/promo codes. It’s also worth noting that the prices we saw in underground marketplaces are often 3-10 times cheaper than their legitimate/original counterparts. Here are some of the notable schemes we saw peddled in the underground:
Brute-forcing codes and exploiting vulnerabilities.Software for checking and brute-forcing coupon codes are sold in the underground. There are even video manuals (uploaded to social media channels), including how to crack the promo codes of a certain ride-sharing service. Coupons come with secret codes “randomly” computed by the business/retailer. If an attacker can figure out how to pre-compute or brute-force these codes, the vendor loses control of these coupons. In theory, a properly generated random code is hard to predetermine. It’s a different matter in practice. Vulnerabilities in the web application that generates or verifies the codes, for instance, can have a hand in enabling a hacker to know the codes.
 Figure 3: Russian underground forum offering tools for brute-forcing/checking the validity of coupon codes
Figure 3: Russian underground forum offering tools for brute-forcing/checking the validity of coupon codes
Coupons as a service. Coupons—counterfeit or not—are further monetized by selling them to fellow fraudsters. There are also coupon generators, which also misuse online check digit calculators, enabling scammers to create purportedly valid coupon codes. Of note is a coupon generator for a vendor that uses crowdsourcing to promote content to social media.
 Figure 4: Coupon generators, including one for a vendor that provides social media promotion services (right)
Figure 4: Coupon generators, including one for a vendor that provides social media promotion services (right)
Abusing “new customer” or registration promos. We also found “new accounts” peddled in the underground, which can be sold by bulk. These accounts take advantage of the perks or other free offers given by retailers upon account registration. There’s also a forum post we saw providing instructions on how to misuse a newly registered Google Cloud Platform account, and make it part of a cryptocurrency-mining pool.

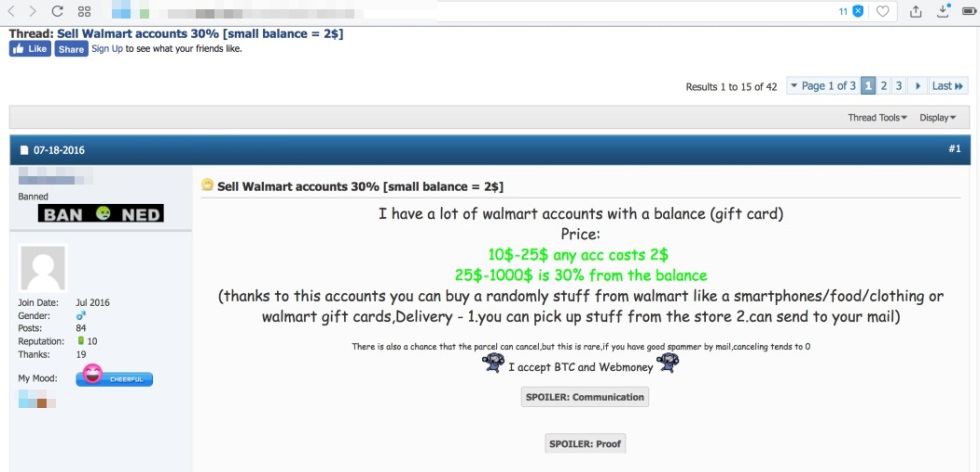 Figure 5: A dark web advertisement selling Amazon gift card codes (top) and Walmart accounts with gift card balance (bottom)
Figure 5: A dark web advertisement selling Amazon gift card codes (top) and Walmart accounts with gift card balance (bottom)
Reselling coupons or serving as an affiliate. Coupons serve as an alternative currency to fellow fraudsters, and are resold to proxify/anonymize the service itself. Some also sell the physical goods redeemed through coupons. Others resort to pyramid schemes and affiliate marketing, where scammers use social engineering to entice and incentivize would-be fraudsters.
 Figure 6: A buy and sell forum for AliExpress coupons
Figure 6: A buy and sell forum for AliExpress coupons  Figure 7: Dark web advertisements for 25% discount on items in M.video (an electronic retail chain), as well as QIWI e-wallets, and prepaid cash cards with balances
Figure 7: Dark web advertisements for 25% discount on items in M.video (an electronic retail chain), as well as QIWI e-wallets, and prepaid cash cards with balances
Lessons LearnedCoupons help companies bring in more business while maintaining the visibility of their products and services. But while getting new customers is a good thing, businesses should be more prudent—especially against those who don’t play by the rules to score freebies and discounts. In March, for instance, an American household item manufacturer and distributor fell to coupon fraud when the barcodes in their coupons, while having a “Do Not Double” disclaimer, weren’t set to expire. It let abusers repeatedly cash in the coupon. What can businesses do? Put safeguards in place. Limit the reuse, distribution, and timeframe of coupon codes. Personalize coupons: anti-counterfeit techniques like using more complex data codes, microprinting, watermarking, and code authentication and verification help deter scammers from duplicating codes. Set the codes to expire after use at the point of sale, for instance. Work proactively with distributors, stakeholders, and law enforcement in reviewing, fine-tuning, and enforcing stronger fraud resistance/risk management policies in coupon programs. The non-profit Coupon Information Corporation, for instance, helps retailers and manufacturers combat coupon fraud. But more importantly, ensure the privacy, security, and integrity of the gateways, endpoints, networks, servers, and other infrastructures that manage the company’s business processes.

