While monitoring our Smart Protection Network™ data, we noticed a suspicious file from the website http://{BLOCKED}bookhacking.com/FacebookHackerPro_Install.exe. From the looks of the domain name, it suggests that it hosts a hacking tool for the social networking site Facebook.
When I checked, the file is supposedly capable of obtaining Facebook passwords. Based on our analysis of the setup file, it behaves like an ordinary installer that displays an end-user license agreement (EULA) and gives users the option to save the program in their preferred folder. Installing the setup file drops the malicious file "Toolbar.exe" in the users’ temporary folder without their knowledge.
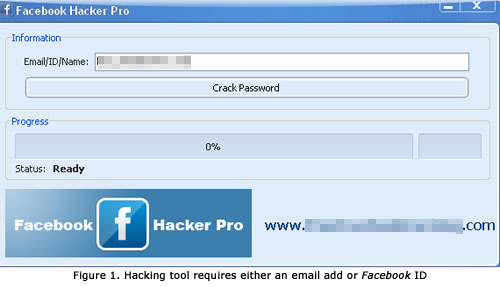
Once installed, it displays a window that requires users to encode the email address or Facebook ID of their target Facebook account:
To appear legitimate, the program even shows a window to indicate that the request is in progress. After 2-5 minutes, it informs users that the desired password has been found:
Now for the interesting part: to acquire password, users must purchase a product key, which costs US $29.99. If users opt to buy a product key, they are reverted to the site http://{BLOCKED}bookhacking.com/p/unlock.
Once purchased, users are again required to encode the email address or Facebook ID. Since the key was already provided, the program now shows the following:
But how did the program obtain these? Simple: the program downloaded and used a free third party application, designed to recover and display saved passwords in the users' local browser cache. Thus, the retrieval of the credentials will only work for users who have passwords stored in their systems. The said third party app is a legitimate password recovery, but was used maliciously in this attack.
If the hacking tool failed to download the third party app, the program would instead display the following error prompt:
Trend Micro detects the rogue program as SPYW_FAKEHACK, while the dropped file "Toolbar.exe" as ADW_PLUGIN. My colleague Sarah Calaunan also uncovered another hacking tool for Facebook being peddled on the site below:
Once users download and run this tool (detected as TROJ_DROPPER.ZGD), it drops the malicious file (detected as TROJ_VBINJECT.XG). The dropped file is a keylogger that hooks certain APIs, steals information from the infected system, and sends stolen information to a specific URL.
Some Internet users may be lured into downloading these tools, as they promise access to someone's Facebook password without the their consent. Luckily, instead of the actual password, users who download these hacking tools acquire a different password and ends up paying for a bogus service.
Survey Scam on Facebook Takes Advantage of SOPA
We also noted several suspicious wall posts on Facebook that leverage the controversial Stop Online Piracy Act (SOPA) bill. Users who click the links contained on these wall posts are directed to another site:
Users who follow the instructions are redirected to several pages, which eventually leads to a survey scam page. This attack is your average clickjacking attack that leads users to survey scams, with affected users spamming the same malicious wall posts to their Facebook contacts. To know more about clickjacking attacks, you may refer to our Threat Encyclopedia post "Think Before You Click: Truth Behind Clickjacking on Facebook."
Trend Micro protects users from this threat via Smart Network Protection™, which prevents access to the sites hosting these hacking tools and the survey scams. It also detects and deletes the related malware from the system. Because of its 901 million users, Facebook is a natural target of cybercrime activities. To know more on how to protect yourself from these threats, you may read our comprehensive digital life e-guide “A Guide to Threats in Social Media”. With additional analysis by Sabrina Sioting.