The usage of exploits in current threats underlines the critical need for users to keep programs updated at all times. Considering the great amount of time people spend on their computers connected to the Internet, web browsers are prime targets for cybercriminals.
This is a technical analysis of a recently discovered vulnerability in one of the most-used web browser: Mozilla Firefox.
This Mozilla Firefox vulnerability was discussed by Charis Rohlf and Yan Lvnitskiy during their presentation, Attacking Clientside JIT Compilers at the Black Hat Conference in Las Vegas earlier this year.
This vulnerability, identified as CVE-2011-2371, lies in the Js3250.dll library and Js3250!array_reduceRight function in Mozilla Firefox, and affects versions earlier than 3.6.18, as well as versions 4.0 through 4.0.1. Two proofs-of-concept for this vulnerability were already disclosed publicly earlier this month by Matteo Memelli and metasploit.
We performed some analysis through reverse engineering and tested with the published proof of concept. Through this, we were successfully able to execute arbitrary remote code on Firefox 3.6.16.
Vulnerability Analysis The following is a sample exploit code:

This code sets the array object length to a long value that will be handled as an unsigned integer. This will call reduceRight function on new Array. If the JavaScript shown above is loaded through the JIT engine by Firefox, the js3250!array_reduceRight function will be executed. It will call the js3250!array_extra function after setting ArrayExtraMode as 2.
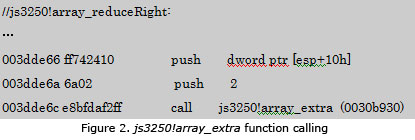
The array object length set as unsigned is then passed to js_GetLenghProperty function for getting the new created array length property.

When js_GetLenghProperty has been called from array_extra function, it will return an address of a new created array object length as a type of unsigned integer.

After getting Array length(0x83000006) as a signed value, it will be passed to the js3250!GetArrayElement function.

The GetArrayElement function will then return a value of (obj->dslots[index]).This value will be calculated as the following: (base address(ecx)+index(edx)*4). The address of (obj->dslots[index]) shows a heap sprayed address.

After setting returned data for js_invoke, it will call the js3250!js_Invoke function.
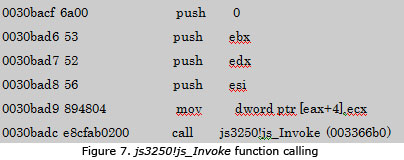
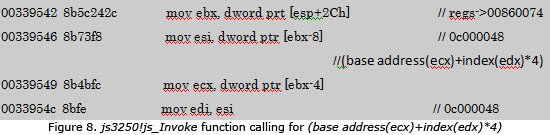
At this point, a user-defined script file will be executed. It will get the regs ofJSFrameRegs type and get a address of (base address(ecx)+index(edx)*4).

Mitigation and Solution Whenever any vulnerability is found, the first thing that always comes to mind is what we can do to protect users from threats that will make use of that vulnerability. For users, to default call for action during such circumstances is to check if they are affected by the vulnerability, and to patch their system.
However, security updates are not always available immediately. Also, for network administrators, patch management is at times difficult since it requires testing processes to make sure it won’t affect the network in an unfavorable way.
Using a security product that shields networks and systems from threats that leverage on vulnerabilities can help the networks and systems protected before the vulnerabilities are patched. For example, if a network administrator uses Trend Micro Deep Security, then he or she does not need to hurry to apply patch and save times until patch test has been finished.
For this specific vulnerability, users are advised to upgrade their Mozilla Firefox browser to the latest version, and to refrain from accessing untrusted links or opening emails from untrusted senders. Network administrators are also advised to maintain minimal system privilege for users.
Enterprises already using the Trend Micro Deep Security and IDF are already protected from exploits leveraging on this vulnerability, provided that they’ve applied virtual patch that includes the rule 1004722-Mozilla Firefox 'Array.reduceRight()' Remote Code Execution, which was released in July 2011.

