It seems like every time you blink there’s a new shiny acronym to describe the latest cybersecurity approaches: cloud access security broker (CASB), cloud workload protection platform (CWPP), cloud security posture management (CSPM), and now cloud-native application protection platform (CNAPP). What does it all mean, and more importantly, what does this new term mean for devs?
What is CNAPP?
CNAPP, Gartner, is an emerging category of security solutions designed to help identify, assess, prioritize, and adapt to risk in cloud-native applications1.
Before we get into the features of CNAPP, let’s review how it differentiates from CASB, CWPP, and CSPM.
CASB
To put it simply, CASB is a security gateway to cloud services. It’s like TSA the at the airport checking baggage for illegal items; CASB enforces security policies to ensure users’ actions are compliant and authorized.
CWPP
As the name suggests, CWPP is focused on protecting all types of workloads like servers on-premises, virtual machines (VMs), containers, and serverless workloads. According to Gartner Peer Insights™2 , “ CWPPs are workload-centric security products that protect server workloads in hybrid, multicloud data center environments (see Note 1). CWPPs provide consistent visibility and control for physical machines, virtual machines (VMs), containers and serverless workloads, regardless of location. CWPP offerings protect workloads using a combination of system integrity protection, application control, behavioral monitoring, intrusion prevention and optional anti-malware protection at runtime. CWPP offerings should also include scanning for workload risk proactively in the development pipeline.”
CSPM
This category is focused on configurations. More specifically, CSMP continuously monitors for misconfigured cloud infrastructure. A CSPM offering integrates with DevOps processes, and incorporates incident response, risk assessment and visualization to help identify unknown or increased risk in your cloud tools and processes. Furthermore, if your security posture has drifted from expectations, CSPM can push tickets and other items into DevOps workflows to quickly return the posture back within policy.
CNAPP consolidates many of the most important features from siloed point-products into one streamlined platform. These capabilities are categorized as Artifact Scanning, Runtime Protection, and Cloud Configuration, which includes:
- Misconfiguration checks for open Amazon S3 buckets, databases, and network ports
- Runtime monitoring and protection of your cloud workloads
- Automated detection of vulnerabilities within containers, virtual machines (VMs), or serverless functions
- Exposure scanning for CVEs, secrets, sensitive data, and malware
- Infrastructure as code (IaC) scanning
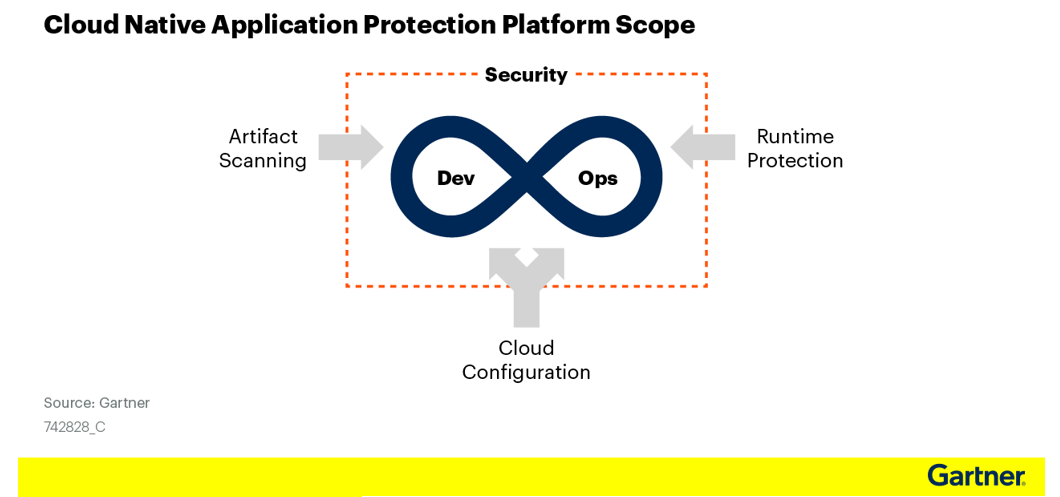
According to Gartner1, “Securing cloud-native applications offers enterprises the opportunity to redesign security approaches. Rather than treat development and runtime as separate problems — secured and scanned with a collection of separate tools — enterprises should treat security and compliance as a continuum across development and operations, and seek to consolidate tools where possible.” Ok, good for them, you may be thinking, but how does this help me?
DevOps and CNAPP
Think of it this way: the alignment between security and development teams (also known as DevOps) results in more secure apps and less build/deployment headaches. An important element of establishing a strong DevOps culture is using security tools that help security teams see all the bad stuff as quickly as possible, enabling devs to build resilient apps faster.
Ok, so how do you choose the right tool? With DevOps, this isn’t just a single-person decision; security, operations, and development teams need to weigh in on how the product(s) will help everyone do their jobs quickly and effectively to meet the overarching business goals.
Therefore, devs need to be aware of the best security architectures like CNAPP to choose the right products, ensuring apps are secure without slowing down build times.
Why CNAPP?
Security professionals aren’t developers and developers aren’t security professionals. In a recent Gartner survey, the highest rated challenge when securing cloud-native applications in a DevSecOps pipeline was a lack of internal knowledge about security.
Roadblock #1: Knowledge gap
Security professionals aren’t developers and developers aren’t security professionals. In a recent Gartner survey, the lack of internal knowledge about security was rated the biggest challenge for securing cloud-native apps in a DevOps pipeline.
This knowledge gap can lead to security teams trying to “cover all their bases” by deploying many different point products to address specific needs. In theory, this man-to-man coverage may seem effective, but in reality, it creates more mental work for already stretched teams; they’re now responsible for stitching together data from separate products.
For devs, this time-consuming manual correlation leads to delays in development workflows. Even worse, security blind spots can lead to undetected risks throughout the lifecycle until it’s too late. Research from NIST shows the later a bug is discovered, the more expensive it is to remediate.
CNAPP act as a super brain. One console with the power to correlate threat data and quickly determine risks across endpoints, containers, serverless functions, etc. This allows devs to build with confidence that their apps are as secure as possible.
Roadblock #2: Time management
Agility is the name of the cloud app game. Security testing needs to be swift and effective, allowing devs to continue on their merry way. Building off roadblock #1, we know that doing things the old-fashioned way by hand isn’t going to cut it.
To get the full benefits of a CNAPP approach, make sure your platform of choice has robust automation capabilities that can automate as many tasks, scans, and checks as possible. When organizations automate as much as possible, not only is detection much quicker, but the number of false-positive alerts are reduced.
Less false positives ensure devs are spending their valuable time investigating and remediating the highest severity and risk vulnerabilities, instead of being sent on a wild goose chase. Now that they’re spending less time on security tasks, they have more time to focus on doing what they do best—build great cloud apps.
Roadblock #3: Collaboration
To have a successful DevOps culture, security and development teams must be collaborating. There’s no longer a “you vs. me” mentality; secure cloud app development depends on establishing a two-way flow of communication between the application owners (devs) and security operations teams. This is especially important as organizations shift to more complex multi- and hybrid-cloud environments and the amount of data continues to increase.
In a recent survey, Gartner found that 44% of participants had “stitched together” a DevOps pipeline with 10 or more security tools, each with siloed responsibility and application view. This type of approach only hinders the collaboration between teams. Think of it like two people sewing a blanket, but neither discussing the pattern or dimensions or material beforehand… The result would be ugly to say the least.
To enhance collaboration between teams, a CNAPP with turnkey, customizable API integrations that fit into the development toolchain is a must. This will provide comprehensive visibility across the entire development lifecycle, allowing security teams to investigate and remediate risks like misconfigurations, overly permissive containers and buckets, and more.
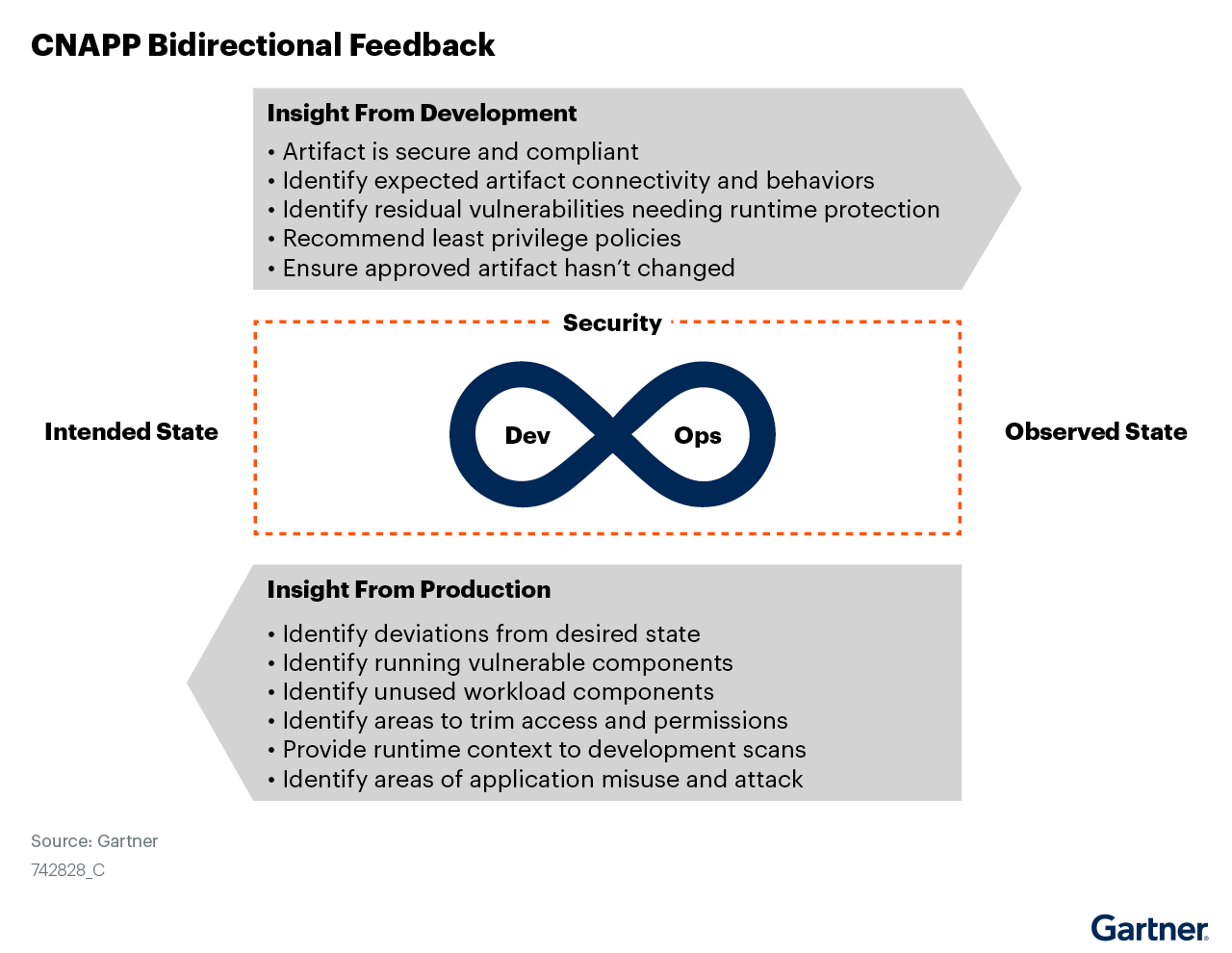
For example, integrating the right platform can shift security to the very start of the build process by running automated vulnerability scans on open source code as soon as it is committed to the repository. Now, security teams are able to remediate any open source risks and ensure that workloads are essentially born secure, in turn reducing friction throughout the lifecycle.
Next steps
Now that we’ve covered the basics of the CNAPP architecture and why it matters for devs, what’s next? As we mentioned earlier, in DevOps, choosing a security product shouldn’t be decided by one person. Devs need to be equally involved in the process—security needs to support the build process, not hinder it.
It may seem complex to differentiate which platforms align with the CNAPP architecture. A good place to start is checking out industry analyst reports. The 2021 Gartner, Emerging Technologies: Future of Cloud-Native Operations, mentioned Trend Micro as an example of a CNAPP vendor. If you’re interested in learning how Trend Micro Cloud One™, our security services platform for cloud builders, can fit into your CNAPP architecture, check out our documentation.
- Disclaimer: Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
1 Gartner, Innovation Insight for Cloud-Native Application Protection Platforms (Neil MacDonald, Charlie Winckless, August 2021)
2 Gartner Peer Insights, Cloud Workload Protection Platforms Reviews and Ratings, as on March 1, 2022


