Updated on August 9, 2023, 9:30 a.m. EDT: We updated the entry to include an analysis of current Rhysida ransomware samples’ encryption routine.
Updated on August 14, 2023, 6:00 a.m. EDT: We updated the entry to include Trend XDR workbench alerts for Rhysida and its components.
Introduction
On August 4, 2023, the HHS’ Health Sector Cybersecurity Coordination Centre (HC3) released a security alert about a relatively new ransomware called Rhysida (detected as Ransom.PS1.RHYSIDA.SM), which has been active since May 2023. In this blog entry, we will provide details on Rhysida, including its targets and what we know about its infection chain.
Who is behind the Rhysida ransomware?
Not much is currently known about the threat actors behind Rhysida in terms of origin or affiliations. According to the HC3 alert, Rhysida poses itself as a “cybersecurity team” that offers to assist victims in finding security weaknesses within their networks and system. In fact, the group’s first appearance involved the use of a victim chat support portal.
Who are Rhysida’s targets?
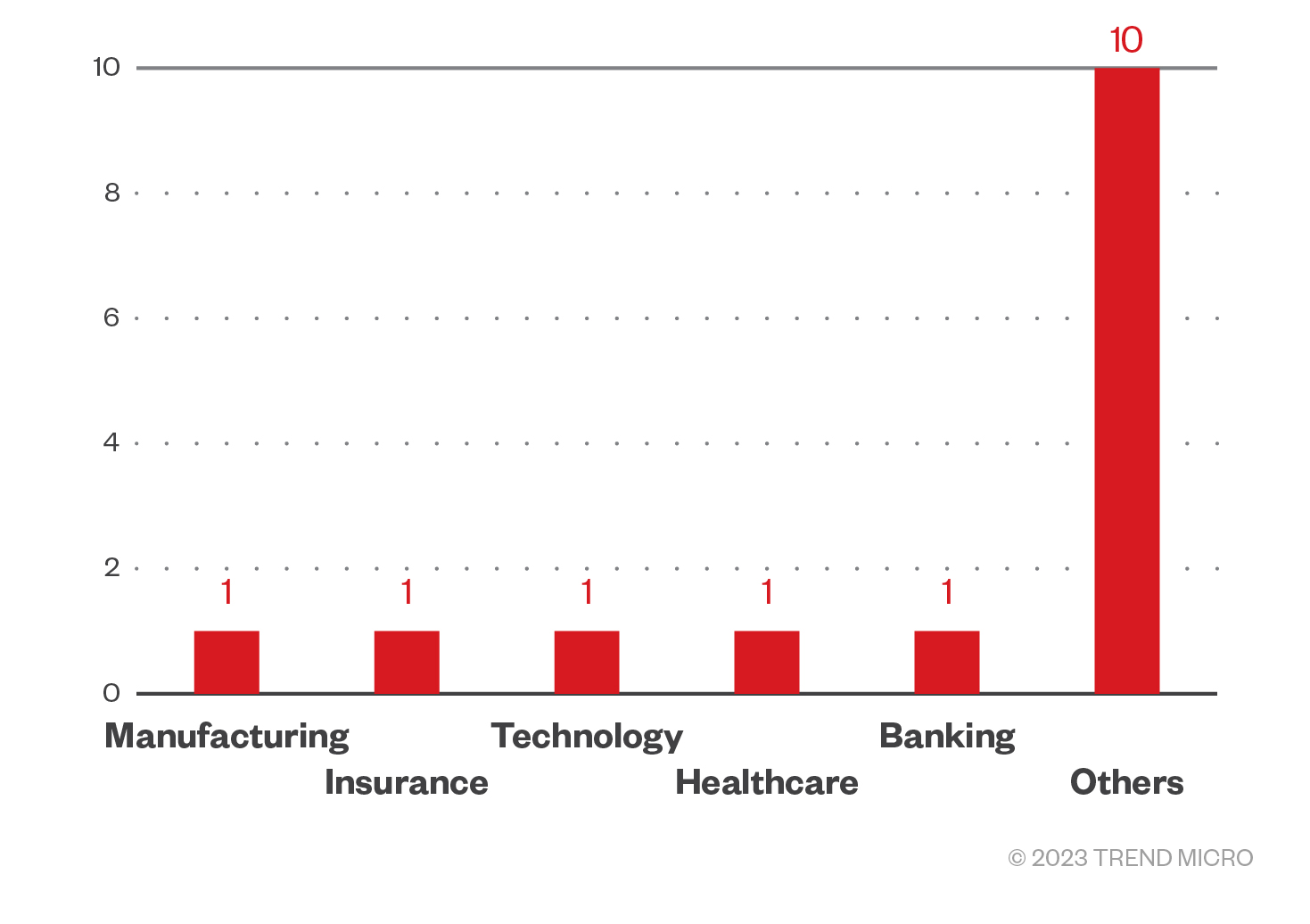
As mentioned earlier, Rhysida, which was previously known for targeting the education, government, manufacturing, and tech industries, amongst others — has begun conducting attacks on healthcare and public health organisations. The healthcare industry has seen an increasing number of ransomware attacks over the past five years. This includes a recent incident involving Prospect Medical Holdings, a California-based healthcare system, that occurred in early August (although the group behind the attack has yet to be named as of writing).
Data from Trend Micro™ Smart Protection Network™ (SPN) shows a similar trend, where detections from May to August 2023 show that its operators are targeting multiple industries rather than focusing on just a single sector.
The threat actor also targets organisations around the world, with SPN data showing several countries where Rhysida binaries were detected, including Indonesia, Germany, and the United States.

How does a Rhysida attack proceed?
Rhysida ransomware usually arrives on a victim’s machine via phishing lures, after which Cobalt Strike is used for lateral movement within the system.
Additionally, our telemetry shows that the threat actors execute PsExec to deploy PowerShell scripts and the Rhysida ransomware payload itself. The PowerShell script (g.ps1), detected as Trojan.PS1.SILENTKILL.A, is used by the threat actors to terminate antivirus-related processes and services, delete shadow copies, modify remote desktop protocol (RDP) configurations, and change the active directory (AD) password.
Interestingly, it appears that the script (g.ps1) was updated by the threat actors during execution, eventually leading us to a PowerShell version of the Rhysida ransomware.
Rhysida ransomware employs a 4096-bit RSA key and AES-CTR for file encryption, which we discuss in detail in a succeeding section. After successful encryption, it appends the.rhysida extension and drops the ransom note CriticalBreachDetected.pdf.
This ransom note is fairly unusual — instead of an outright ransom demand as seen in most ransom notes from other ransomware families, the Rhysida ransom note is presented as an alert from the Rhysida “cybersecurity team” notifying victims that their system has been compromised and their files encrypted. The ransom demand comes in the form of a “unique key” designed to restore encrypted files, which must be paid for by the victim.
Summary of malware and tools used by Rhysida
- Malware: RHYSIDA, SILENTKILL, Cobalt Strike
- Tools: PsExec
| Initial Access | Phishing | Based on external reports, Rhysida uses phishing lures for initial access |
| Lateral Movement | PsExec | Microsoft tool used for remote execution |
|---|---|---|
| Cobalt Strike | 3rd party tool abused for lateral movement | |
| Defence Evasion | SILENTKILL | Malware deployed to terminate security-related processes and services, delete shadow copies, modify RDP configurations, and change the AD password |
| Impact | Rhysida ransomware | Ransomware encryption |
Table 1. A summary of the malware, tools, and exploits used by Rhysida
A closer look at Rhysida’s encryption routine
After analysing current Rhysida samples, we observed that the ransomware uses LibTomCrypt, an open-source cryptographic library, to implement its encryption routine. Figure 3 shows the procedures Rhysida follows when initialising its encryption parameters.

Rhysida uses LibTomCrypt’s pseudorandom number generator (PRNG) functionalities for key and initialisation vector (IV) generation. The init_prng function is used to initialise PRNG functionalities as shown in Figure 4. The same screenshot also shows how the ransomware uses the library’s ChaCha20 PRNG functionality.

After the PRNG is initialised, Rhysida then proceeds to import the embedded RSA key and declares the encryption algorithm it will use for file encryption:
- It will use the register_cypher function to “register” the algorithm (in this case, aes), to its table of usable cyphers.
- It will use the find_cypher function to store the algorithm to be used (still aes), in the variable CIPHER.
Afterward, it will proceed to also register and declare aes for its Cypher Hash Construction (CHC) functionalities.
Based on our analysis, Rhysida’s encryption routine follows these steps:
- After it reads file contents for encryption, it will use the initialised PRNG’s function, chacha20_prng_read, to generate both a key and an IV that are unique for each file.
- It will use the ctr_start function to initialise the cypher that will be used, which is aes (from the variable CYPHER), in counter or CTR mode.
- The generated key and IV are then encrypted with the rsa_encrypt_key_ex function.
- Once the key and IV are encrypted, Rhysida will proceed to encrypt the file using LibTomCrypt’s ctr_encrypt function.

How can organisations protect themselves from Rhysida and other ransomware families?
Although we are still in the process of fully analysing Rhysida ransomware and its tools, tactics, and procedures (TTPs), the best practises for defending against ransomware attacks still holds true for Rhysida and other ransomware families.
Here are several recommended measures that organisations implement to safeguard their systems from ransomware attacks:
- Create an inventory of assets and data
- Review event and incident logs
- Manage hardware and software configurations.
- Grant administrative privileges and access only when relevant to an employee's role and responsibilities.
- Enforce security configurations on network infrastructure devices like firewalls and routers.
- Establish a software whitelist permitting only legitimate applications
- Perform routine vulnerability assessments
- Apply patches or virtual patches for operating systems and applications
- Keep software and applications up to date using their latest versions
- Integrate data protection, backup, and recovery protocols
- Enable multifactor authentication (MFA) mechanisms
- Utilise sandbox analysis to intercept malicious emails
- Regularly educate and evaluate employees' security aptitude
- Deploy security tools (such as XDR) which are capable of detecting abuse of legitimate applications
Indicators of compromise
The indicators of compromise for this entry can be found here.
MITRE ATT&CK Matrix
| Initial Access | T1566 Phishing | Based on external reports, Rhysida uses phishing lures for initial access. |
| Execution | T1059.003 Command and Scripting Interpreter: Windows Command Shell | It uses cmd.exe to execute commands for execution. |
| T1059.001 Command and Scripting Interpreter: PowerShell | It uses PowerShell to create scheduled task named Rhsd pointing to the ransomware. | |
| Persistence | T1053.005 Scheduled Task/Job: Scheduled Task | When executed with the argument -S, it will create a scheduled task named Rhsd that will execute the ransomware |
| Defence Evasion | T1070.004 Indicator Removal: File Deletion | Rhysida ransomware deletes itself after execution. The scheduled task (Rhsd) created would also be deleted after execution. |
| T1070.001 Indicator Removal: Clear Windows Event Logs | It uses wevtutil.exe to clear Windows event logs. | |
| Discovery | T1083 File and Directory Discovery | It enumerates and looks for files to encrypt in all local drives. |
| T1082 System Information Discovery | Obtains the following information:
|
|
| Impact | T1490 Inhibit System Recovery | It executes uses vssadmin to remove volume shadow copies |
| T1486 Data Encrypted for Impact | It uses a 4096-bit RSA key and Cha-cha20 for file encryption. It avoids encrypting files with the following strings in their file name:
It avoids encrypting files found in the following folders:
It appends the following extension to the file name of the encrypted files: .rhysida It encrypts all system drives from A to Z. It drops the following ransom note: {Encrypted Directory}\CriticalBreachDetected.pdf |
|
| T1491.001 Defacement: Internal Defacement | It changes the desktop wallpaper after encryption and prevents the user from changing it back by modifying the NoChangingWallpaper registry value. |
Trend Micro Solutions
Trend solutions such as Apex One, Deep Security, Cloud One Workload Security, Worry-Free Business Security, Deep Discovery Web Inspector, Titanium Internet Security, and Cloud Edge can help protect against attacks employed by the Rhysida ransomware.
The following solutions protect Trend customers from Rhysida attacks:
| Trend Micro solutions | Detection Patterns / Policies / Rules |
|
|
|
|
|
|
|
|
Trend Micro XDR uses the following workbench alerts to protect customers from Rhysida-related attacks:
| Workbench Alert | ID |
| Anomalous Regsvr32 Execution Leading to Cobalt Strike | 63758d9f-4405-4aec5-b421-64aef7c85dca |
| COBALT C2 Connection | afd1fa1f-b8fc-4979-8bf7-136db80aa264 |
| Early Indicator of Attack via Cobalt Strike | 0ddda3c1-dd25-4975-a4ab-b1fa9065568d |
| Lateral Movement of Cobalt Strike Beacon | 5c7cdb1d-c9fb-4b1d-b71f-9a916b10b513 |
| Possible Cobalt Strike Beacon | 45ca58cc-671b-42ab-a388-d972ff571d68 |
| Possible Cobalt Strike Beacon Active Directory Database Dumping | 1f103cab-9517-455d-ad08-70eaa05b8f8d |
| Possible Cobalt Strike Connection | 85c752b8-93c2-4450-81eb-52aec6161088e |
| Possible Cobalt Strike Privilege Escalation Behaviour | 2c997bac-4fc0-43b4-8279-6f2e7cf723ae |
| Possible Fileless Cobalt Strike | cf1051ba-5360-4226-8ffb-955fae849db53 |
| Workbench Alert | ID |
| Possible Credential Access via PSEXESVC Command Execution | 0b870a13-e371-4bad-9221-be7ad98f16d7 |
| Possible Powershell Process Injection via PSEXEC | 7fae83eb8-f40f-43be-8edd-f6cbc1399ac0 |
| Possible Remote Ransomware Execution via PsExec | 47fbd8f3-9fb5-4595-9582-eb82566ead7a |
| PSEXEC Execution By Process | e011b6b9-bdef-47b7-b823-c29492cab414 |
| Remote Execution of Windows Command Shell via PsExec | b21f4b3e-c692-4eaf-bee0-ece272b69ed0 |
| Suspicious Execution of PowerShell Parameters and PSEXEC | 26371284-526b-4028-810d-9ac71aad2536 |
| Suspicious Mimikatz Credential Dumping via PsExec | 8004d0ac-ea48-40dd-aabf-f96c24906acf |
| Workbench Alert | ID |
| Possible Disabling of Antivirus Software | 64a633e4-e1e3-443a-8a56-7574c022d23f |
| Suspicious Deletion of Volume Shadow Copy | 5707562c-e4bf-4714-90b8-becd19bce8e5 |
| Workbench Alert | ID |
| Ransom Note Detection (Real-time Scan) | 16423703-6226-4564-91f2-3c03f2409843 |
| Ransomware Behaviour Detection | 6afc8c15-a075-4412-98c1-bb2b25d6e05e |
| Ransomware Detection (Real-time Scan) | 2c5e7584-b88e-4bed-b80c-dfb7ede8626d |
| Scheduled Task Creation via Command Line | 05989746-dc16-4589-8261-6b604cd2e186 |
| System-Defined Event Logs Clearing via Wevtutil | 639bd61d-8aee-4538-bc37-c630dd63d80f |
Trend Vision One customers can use the following hunting query to search for Rhysida within their system:
processcmd:"powershell.exe*\\*$\?.ps1" OR (objectFilePath:"?:*\\??\\psexec.exe" AND processcmd:"*cmd.exe*\\??\\??.bat")