Posts in this series
This article is the last in a series that discusses the challenges that IT departments face when they are assigned the task of overseeing cybersecurity in factories and implementing measures to overcome these challenges. As explained in the first two articles, a factory network that accounts for diverse conditions and environments requires a well-balanced consideration of security in view of the actual operational situation, namely because applying uniform security policies to such a network is difficult compared to IT. In terms of factory security, Trend Micro recommends three measures: network separation, layer-optimized measures, and integrated management of these elements. In this third article, we will explain this concrete approach to security.
Factory system from the perspective of roles
Before discussing network configuration, we will provide an overview of a factory system from the perspective of roles. When the entire system is simplified in terms of factory production activities, the following layers can be identified: the production planning layer, implementation management layer, control layers, and work layer. From top to bottom, what to produce and the production methods are planned, and instructions are provided. The lower we go, the more details and real-time properties we obtain. Conversely, from bottom to top, information on how products were made and which products were made is reported, increasing the degree of information aggregation.
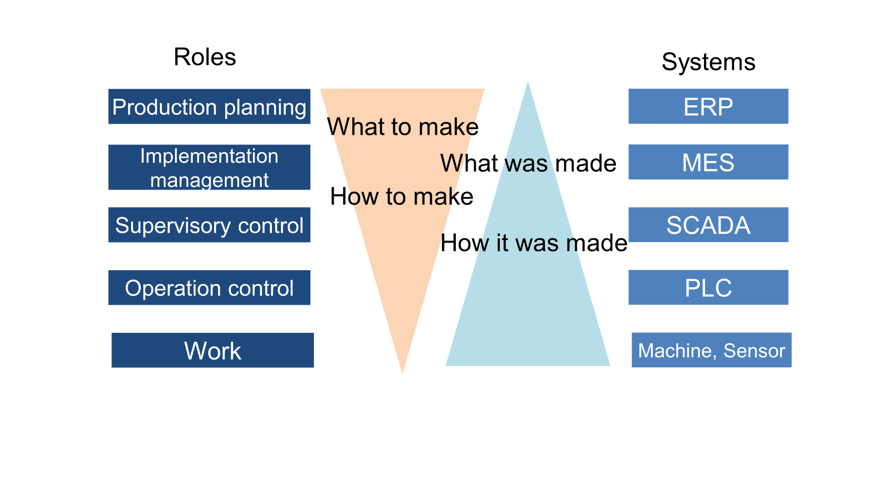
Figure 1: Image of factory system roles (Trend Micro)
* ERP: Enterprise Resource Planning, MES: Manufacturing Execution System, SCADA: Supervisory Control And Data Acquisition, PLC: Programmable Logic Controller
Network layers and attack scenarios
An entire factory network can be abstracted by referencing the Purdue Enterprise Reference Architecture, which was developed amidst the computerization of manufacturing operations. ERP is placed in the IT layer and MES, which manages overall execution, in the topmost factory layer. Under this, SCADA and HMI (for supervisory control) and EWS (for designing and programming) are placed and connected to devices that handle physical processes and to PLC, which operates those devices.
In some cyberattacks, malicious programs that target numerous devices without specific targets happen to reach factories, whereas other cyberattacks aim at specific targets and involve either an intrusion from the IT network into the OT network or an intrusion within the factory network. In the former case, malicious programs may spread within the IT network or into the factory network via the IT network. In the latter case, malicious programs may be injected mainly when a device or removable media is brought in and connected to a system for maintenance purposes, or when maintenance is carried out via a dedicated line. In the event of an intrusion, the malware may build a platform for unauthorized external communication by creating a backdoor, or it may spread in the supervisory control layer and consume network and computing resources, thereby interrupting functionality or causing deteriorated functionality. As a result, the work layer will not operate as planned, affecting production activities.
Although assets are managed in the factory as a matter of course, caution should be exercised because this perspective differs from that of IT management. It is not easy to comprehensively understand the versions and configurations of device OSs and software. The operational difficulty of applying security patches and installing security software in response to device vulnerabilities also complicates measure implementation. In addition, vulnerabilities in authentication and protocols are also problematic. In the past, there was no need to implement authentication when devices were connected by serial cable, and no need to consider the security of inter-device communications. However, as intra-factory networks are laid out, these vulnerabilities increasingly facilitate intrusions and the spread of attacks as well as slow down recovery.
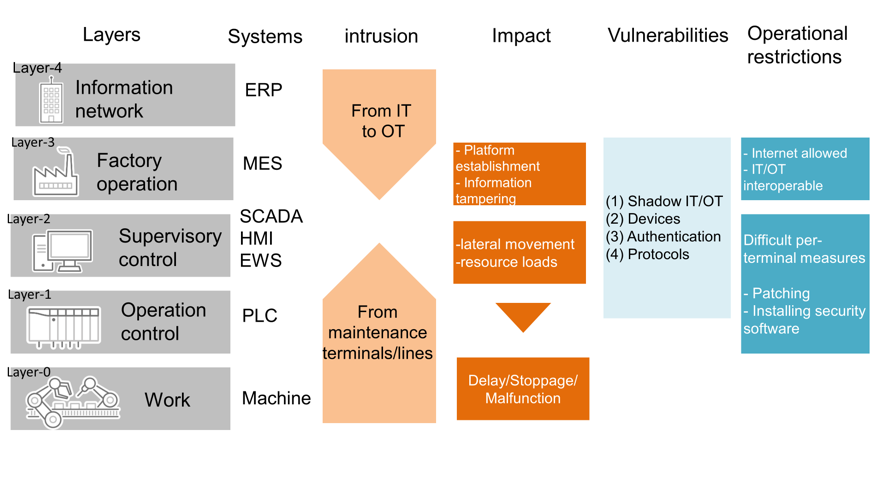
Figure 2: Attacks and vulnerabilities as seen from factory network layers (Trend Micro)
Separate IT and OT, and take measures in each layer to ensure factory security
In a factory network, damage due to the halting of a production line, shipment of defective products, or personnel accidents caused by cyberattacks must be dealt with as business risks.
The first task is to separate the IT and OT environments and to prevent intrusion from IT into OT. Set up a DMZ so that information can be shared mutually without directly connecting IT and OT. An effective approach is to incorporate mechanisms for eliminating and blocking unauthorized communication using FW, IPS, and other tools.
The next task is to reduce the risk in layer three, which contains the MES and other components that control the entire factory OT system, where threats from the outside or inside may build a platform for a prolonged silent attack, thus having a broad impact throughout the factory. In this layer, an effective approach is to implement mechanisms for monitoring internal activities and detecting infections within the network, suspicious changes made to servers, and communications to external C&C servers.
For the third task, it is effective to implement two approaches in layer two, the control layer close to physical work. One approach is network segmentation, and the other is the protection of mission-critical terminals. In an environment in which measures based on per-terminal patching and IT security software are not suitable for operational reasons, the best measure is to segment the network in order to detect intrusions at an early stage and to localize damage. In addition, locking down mission-critical system terminals such as those for SCADA and running periodic malware tests for EWS in a nearly standalone manner are effective for preventing infections.
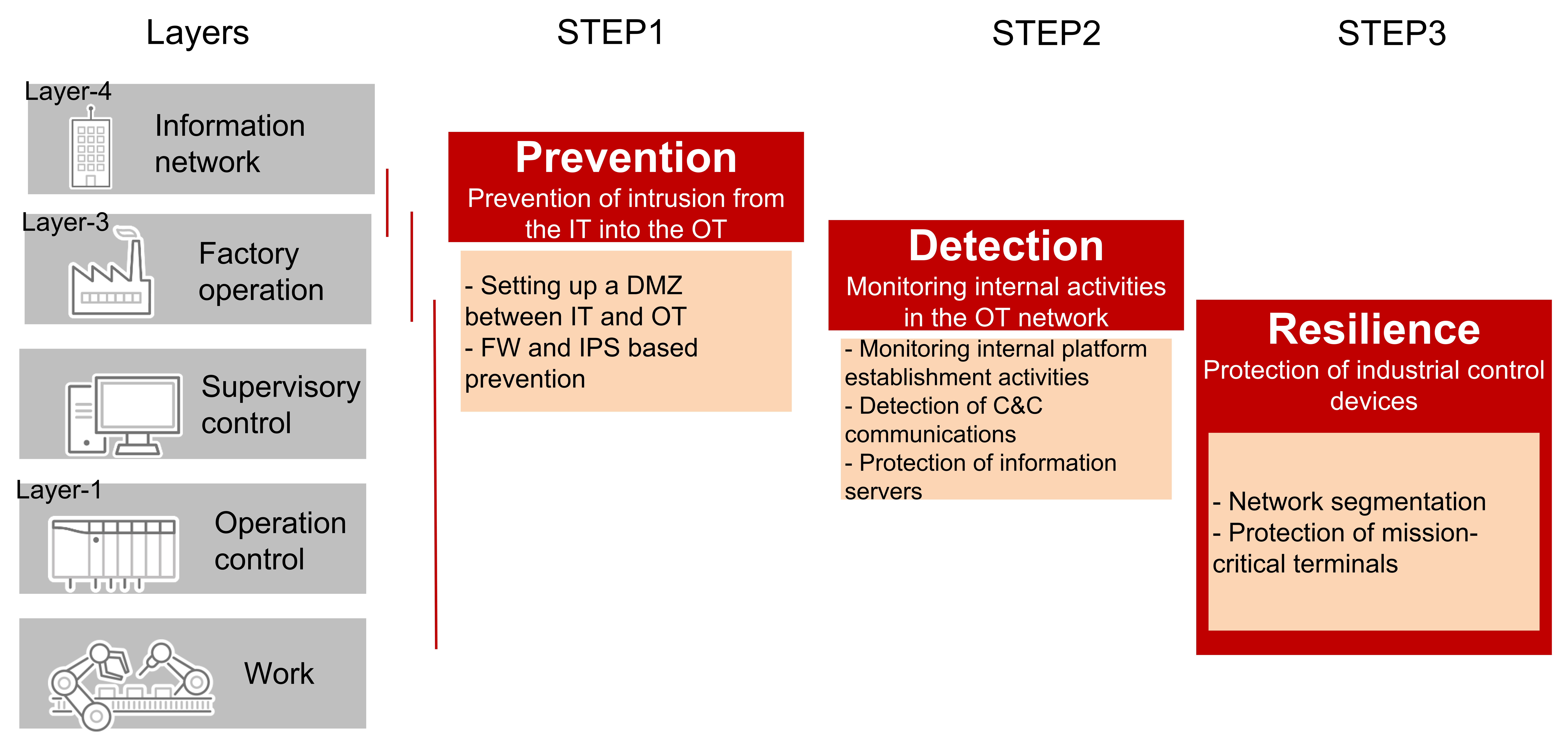
Figure 3: Per-layer measure policies (Trend Micro)
Adopting this approach, Trend Micro provides a solution to achieve continuous, stable operation based on the concept of "Keep Operation Running." To prevent cyberattacks by fortifying the factory with multiple layers, another measure worthy of note is to visualize and manage the overall security of IT and OT. Latent threats in the factory can be visualized only after implementing measures in each layer. Connecting these brings us one step closer to achieving security in an environment in which IT and OT are fused together. For the details of the specific products that constitute this solution, please refer to our solution page.
Trend Micro: Smart Factory Security
https://www.trendmicro.com/us/iot-security/iot-solutions/smart-factory
Providing support with IT and OT expertise and technologies
Trend Micro utilizes its various expertise to develop factory security solutions. We apply vulnerability-related findings made at the Zero Day Initiative, the world's largest vulnerability discovery community which we run, not only to IT but also to OT. Trend Micro Research investigates manufacturing industry-specific security risks and conducts research projects that cover both IT and OT. We disclose research reports in order to help with customers' in-house awareness-raising and education. In addition, we have been achieving positive results in assessment, planning, and operations through our experience helping many customers implement security measures and respond to incidents. We would love the opportunity to help IT departments that are working on factory cybersecurity as a partner, not only with our products but also from the perspectives of people and processes.
Trend Micro: Articles related to smart factory security

