15 Examples of recent Ransomware Attacks
Trend Micro: Cutting Ransomware risk with proactive Attack Surface Management
15 Ransomware Examples
Ransomware is malware that encrypts important files on local and network storage and demands a ransom to decrypt the files. Hackers develop this malware to make money through digital extortion.
Ransomware is encrypted, so the key cannot be forced and the only way to recover the information is from a backup.
The way ransomware works makes it especially damaging. Other types of malware destroy or steal data but leave other recovery options open. With ransomware, if there are no backups, you must pay the ransom to recover the data. Sometimes businesses pay the ransom, and the attacker does not send the decryption key.
RansomHub
RansomHub is a young Ransomware-as-a-Service (RaaS) group first detected in February 2024 and tracked by Trend Micro as Water Bakunawa. It quickly gained notoriety for their “big game hunting” tactic. They prey on victims who are more likely to pay large ransoms to mitigate the downtime on business operations caused by a ransomware attack. They target cloud storage backups and misconfigured Amazon S3 instances to threaten backup providers with data leaks, taking advantage of the trust between providers and their clients.
Rhysida
Motivated by financial gain, Rhysida’s operators have been known to use phishing attacks as a means of gaining initial access, after which Cobalt Strike is used for lateral movement in infected machines. In July 2023, our telemetry found that the Rhysida ransomware was using PsExec to deliver a script, detected as SILENTKILL, to terminate antivirus programs.
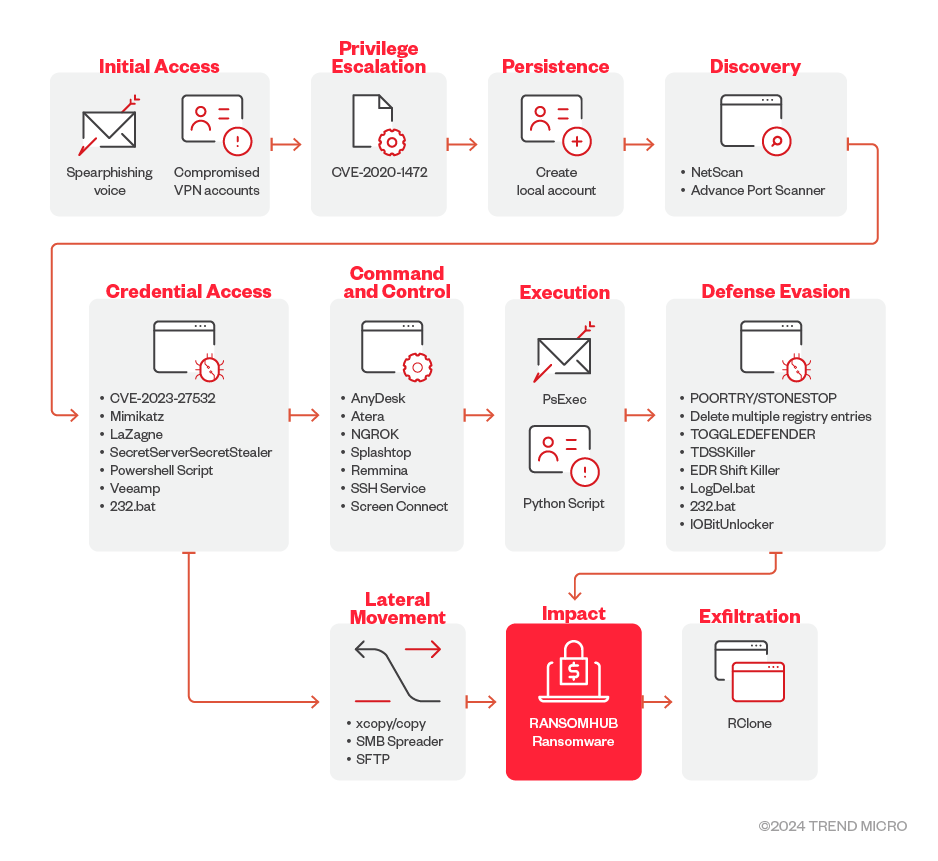
Figure 1: The RansomHub ransomware observed infection chain
Akira
Akira ransomware emerged in March 2023 and has been known to target companies based in the US and Canada.
Its Tor leak site has a unique retro look that, according to a report from Sophos, is reminiscent of “1980s green-screen consoles” that can be navigated by typing specific commands.
WannaCry
WannaCry was first detected back in April, where it was discovered using file hosting service Dropbox as part of its propagation method.
The "WannaCry" outbreaks rank as the most damaging global cyber security incidents during the first half of 2017. These massive ransomware attacks impacted the networks of hospitals, factories, and railroads in many different countries with serious consequences.
WannaCry reportedly paralyzed over 200,000 computers, including those running Germany's national railway and the hospital network of the United Kingdom.
The ransomware’s infection flow is shown in this diagram:

Figure 2: Infection diagram
Clop
Clop (sometimes stylized as “Cl0p”) was one of the most prolific ransomware families in between 2020 and 2023. It gained infamy for compromising high-profile organizations in various industries worldwide using multilevel extortion techniques that resulted in huge payouts estimated at US$500 million as of November 2021.
8Base
First detected in March 2022, 8Base is an active ransomware group that positions itself as “simple penetration testers” to justify its double-extortion strategy, which involves encrypting data and threatening to expose sensitive information. The gang adopts a name-and-shame tactic, claiming in its leak site to exclusively target organizations that “have neglected the privacy and importance of the data of their employees and customers” and revealing confidential data to potentially cause harm to its victim’s brand and reputation.
Trigona
The Trigona ransomware, first tracked by Trend Micro as Water Ungaw, emerged in October 2022. However, binaries of the ransomware were first seen as early as June of the same year. While it was active, the group positioned itself as running a lucrative scheme, launching global attacks and advertising revenues up to 20% to 50% for each successful attack. The group was also reported as communicating with network access brokers who provide compromised credentials via the Russian Anonymous Marketplace (RAMP) forum’s internal chats and using the sourced information to obtain initial access to targets.
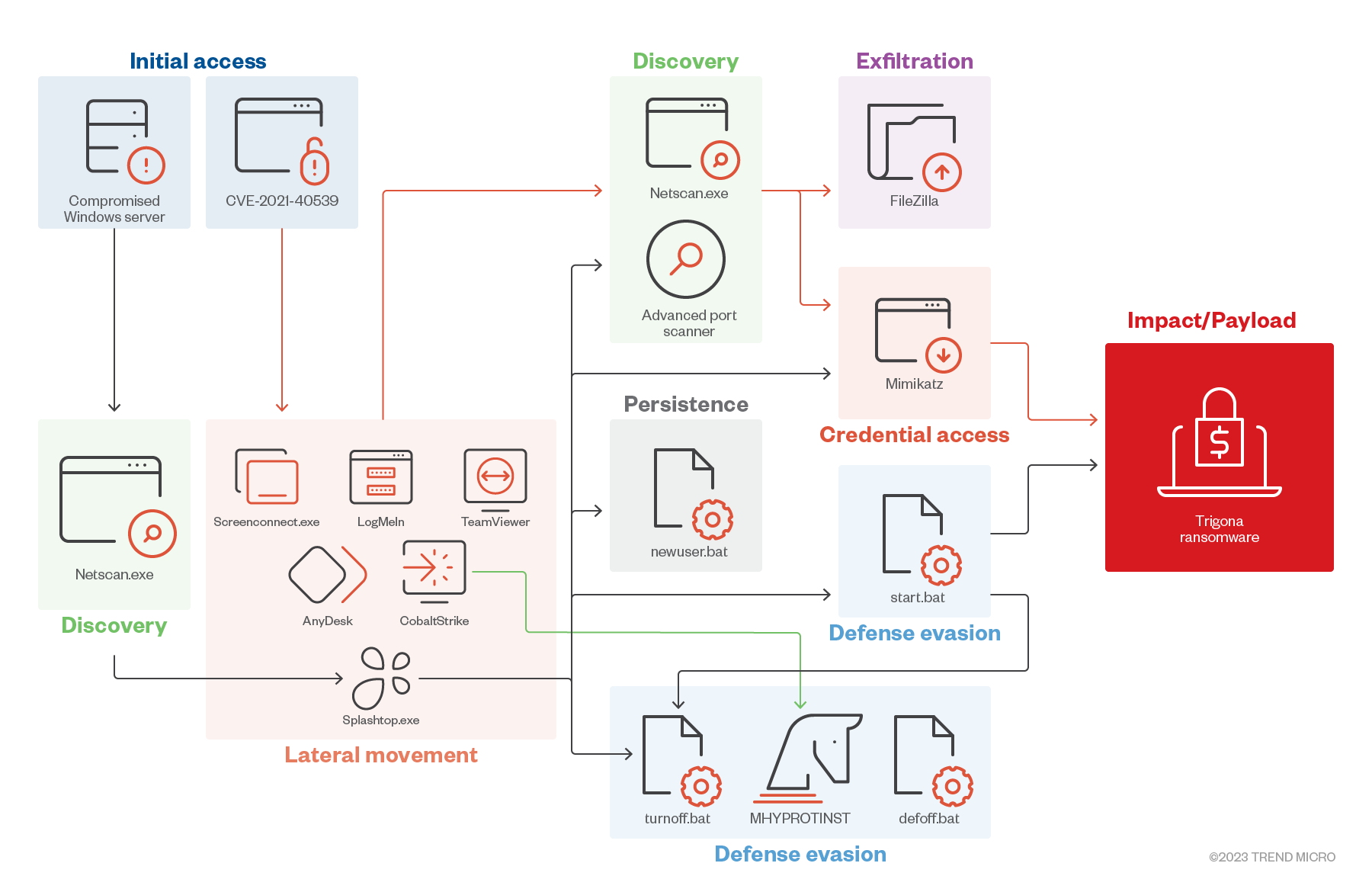
Figure 3: Trigona ransomware’s infection chain
LockBit
LockBit first emerged as the ABCD ransomware on September 2019, which was improved to become one of the most prolific ransomware families today.
Through their professional operations and strong affiliate program, LockBit operators proved that they were in it for the long haul. Thus, being acquainted with their tactics will help organizations fortify their defenses for current and future ransomware attacks.
On Feb. 19, 2024, Operation Cronos, a targeted law enforcement action, caused outages on LockBit-affiliated platforms, disrupting the notorious ransomware group's operations.
BlackCat
First observed in mid-November 2021 by researchers from the MalwareHunterTeam, BlackCat (aka AlphaVM, AlphaV, or ALPHV) swiftly gained notoriety for being the first major professional ransomware family to be written in Rust, a cross-platform language that enables malicious actors to customize malware with ease for different operating systems like Windows and Linux, thus affording a wide range of enterprise environments.
Ryuk Ransomware
Ransomware Ryuk, pronounced ree-yook, is a family of ransomware that first appeared in mid-to-late 2018. In December 2018, the New York Times reported that Tribune Publishing had been infected by Ryuk, disrupting printing in San Diego and Florida. The New York Times and the Wall Street Journal shared a printing facility in Los Angeles. They were also impacted by the attack, which caused distribution issues for the Saturday editions of the newspapers.
A variant of the older Hermes ransomware, Ryuk tops the list of the most dangerous ransomware attacks. In the CrowdStrike 2020 Global Threat Report, Ryuk accounts for three of the top 10 largest ransom demands of the year: USD $5.3 million, $9.9 million, and $12.5 million. Ryuk has successfully attacked industries and companies around the globe. Hackers call the practice of targeting large companies “big game hunting” (BGH).
The hackers leave ransom notes in the system as RyukReadMe.txt and UNIQUE_ID_DO_NOT_REMOVE.txt that read something like the following screenshot.
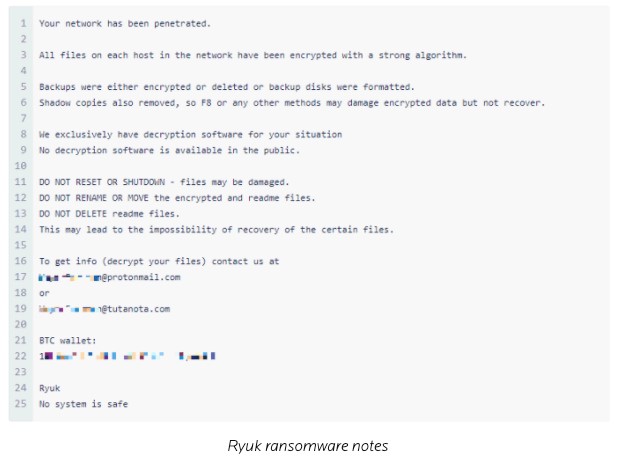
Source: Malwarebytes
Black Basta
Black Basta is a ransomware group operating as ransomware-as-a-service (RaaS) that was initially spotted in April 2022. It has since proven itself to be a formidable threat, as evidenced by its use of double-extortion tactics and expansion of its attack arsenal to include tools like the Qakbot trojan and PrintNightmare exploit.
Royal
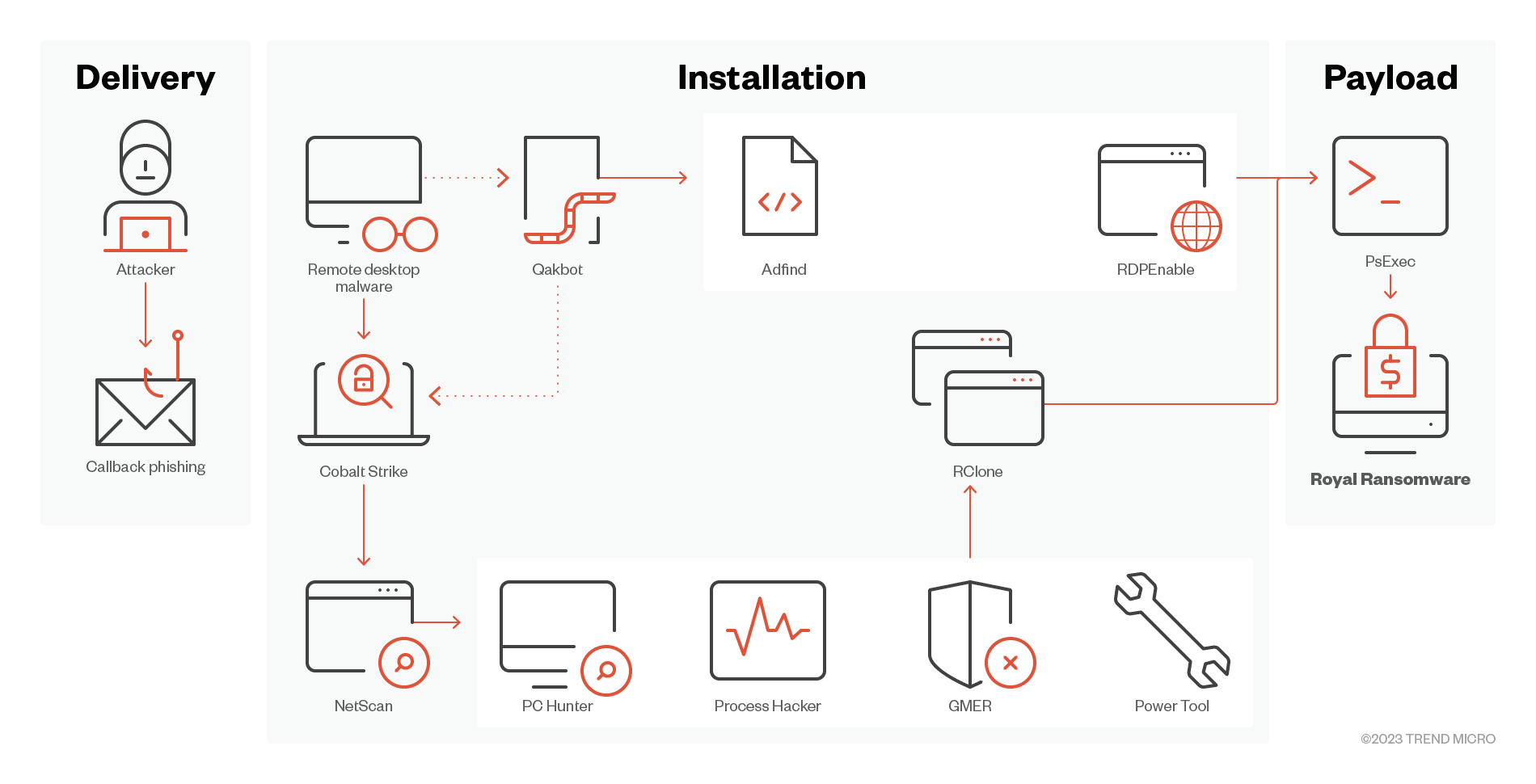
Figure 5: Royal ransomware’s attack flow
Water Ouroboros
Water Ouroboros (aka Hunters International) is a Ransomware-as-a-Service (RaaS) group that first emerged in October 2023. It is suspected to be a possible spin-off of Hive Ransomware, which had its activities disrupted by the Federal Bureau of Investigation (FBI) in January 2023.
The group behind Water Ouroboros was initially suspected to be the same group behind Hive due to the many similarities in tools, tactics, and procedures (TTPs). However, Water Ouroboros denied the connection, claiming instead that they had acquired Hive’s infrastructure and ransom binary.
Hive
On August 15, 2021, Hive’s ransomware attacks against a non-profit integrated health system severely disrupted the clinical and financial operations of three hospitals in Ohio and West Virginia. The attack resulted in emergency room diversions and cancelation of urgent surgical cases and radiology examinations. The encryption of files forced the hospital staff to use paper charts. Aside from the three hospitals, the affected non-profit also runs several outpatient service sites and clinics with a combined workforce of 3,000 employees.
Trend Micro Ransomware Protection
Last year, 83% of organizations faced multiple breaches costing $4.4 million each, while reducing risk exposure led to average savings of $1.3 million.
Cyber Risk Exposure Management, part of our Trend Vision One™ enterprise cybersecurity platform, dramatically reduces cyber risk with continuous discovery, real-time assessments, and automated mitigation across cloud, hybrid, or on-premises environments.
Related Research
Related Article