What Are the Different Types of Phishing?
Stop more threats with Trend Micro Email Security—advanced protection for your inbox!
What are the different types of phishing attacks?
Phishing attacks are social engineering attacks, and they can have a great range of targets depending on the attacker. There are a lot of phishing examples that can go from generic scam emails to more sophisticated targeted ones.
Phishing can also be a targeted attack focused on a specific individual. The attacker often tailors an email to speak directly to you, and includes information only an acquaintance would know. An attacker usually gets this information after gaining access to your personal data. If the email is this type, it is very difficult for even the most cautious of recipients not to become a victim. PhishMe Research determined that ransomware accounts for over 97% of all phishing emails.
Types of phishing attacks range from classic email phishing schemes to more inventive approaches such as spear phishing and smishing. All have the same purpose – to steal your personal details.
Email Phishing
Email phishing is another example of phishing and the most common one, and it has been in use since the 1990s. Hackers send these emails to any email address they can obtain. The email usually informs you that there has been a compromise to your account and that you need to respond immediately by clicking on a provided link. These attacks are usually easy to spot as language in the email often contains spelling and/or grammatical errors.

Example of Email Phishing
In February 2024, Pepco Group, the owner of brands like Pepco, Dealz, and Poundland, experienced a phishing attack targeting its Hungarian branch. Attackers sent sophisticated phishing emails that resulted in fraudulent money transfers amounting to approximately €15.5 million.
Spear Phishing
Spear phishing targets a specific group or type of individual such as a company’s system administrator. Below is an example of a spear phishing email. Note the attention paid to the industry in which the recipient works, the download link the victim is asked to click, and the immediate response the request requires.
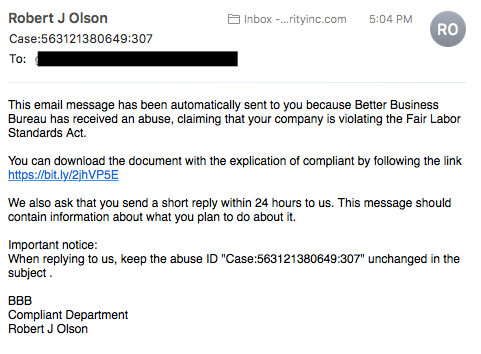
Example of Spear Phishing
In October 2024, the cybercriminal group Water Makara launched a spear-phishing campaign targeting Brazilian enterprises. They sent emails with malicious ZIP attachments disguised as personal income tax documents. When opened, these attachments executed obfuscated JavaScript via mshta.exe, leading to the deployment of the Astaroth banking malware.
Whaling
Whaling is an even more targeted type of phishing that goes after the whales – a marine animal even bigger than a fish. These attacks typically target a CEO, CFO, or any CXX within an industry or a specific business. A whaling email might state that the company is facing legal consequences and that you need to click on the link to get more information.
Example of Whaling
In 2016, Austrian aeronautics firm FACC fell victim to a Business Email Compromise (BEC) scam, losing over €42 million. Attackers impersonated the CEO, sending fraudulent emails to the finance department requesting a wire transfer for a fictitious acquisition. This whaling phishing attack targeted high-level executives to deceive employees into authorizing substantial fund transfers.
Vishing
Vishing has the same purpose as other types of phishing attacks. The attackers are still after your sensitive personal or corporate information. This attack is accomplished through a voice call. Hence the “v” rather than the “ph” in the name Vishing.
Example of Vishing
In December 2024, Trend Micro analyzed a vishing attack where an attacker impersonated a client via Microsoft Teams to deceive a victim into installing the AnyDesk remote desktop application. This granted the attacker unauthorized access, leading to the deployment of DarkGate malware, which enabled remote control over the compromised system and attempted to connect to a command-and-control server.
Search Engine Phishing
Search engine phishing, also known as SEO poisoning or SEO Trojans, is where hackers work to become the top result on a search using a search engine. Clicking on their link displayed within the search engine directs you to the hacker’s website. From there, threat actors can steal your information when you interact with the site and/or enter sensitive data. Hacker sites can pose as any type of website, but the prime candidates are banks, money transfer, social media, and shopping sites.
Example of Search Engine Phishing
In 2024, Trend Micro, in collaboration with Japanese authorities, analyzed the relationships among multiple SEO malware families used in SEO poisoning attacks that lead users to fake shopping sites. Their research identified three groups of threat actors, each using unique malware families, with one group utilizing multiple families.
Smishing
Smishing is a cyber attack that uses short message service or SMS, more commonly known as text messages to target individuals. This has become a popular attack method amongst cybercriminals as people are more likely to trust a message that comes in via their messaging app on their phone, compared to receiving an email in their inbox.
Example of Smishing
At the end of 2024, the IRS announced that they were planning to send out payments of up to $1400 to people that did not previously receive Covid-19 stimulus payments. This presented an opportunity for scammers to run a Smishing campaign posing as the IRS, with the goal of stealing personal information, such as home addresses, date of birth and Individual Tax ID Number (ITIN).
Pharming
Pharming is a type of cyberattack that silently redirects users from legitimate websites to malicious, spoofed websites without their knowledge. Unlike traditional phishing, which relies on tricking the user into clicking a malicious link, pharming can operate in the background after a system or router has already been compromised. Typically, this starts with a phishing email that delivers malicious code to the victim’s device. Once executed, the code can alter DNS settings or manipulate routing tables, causing the user’s browser to visit a fake website, even when the correct URL is typed.
Example of Pharming
In 2018, Trend Micro identified the Novidade exploit kit, that targets home and small office routers through cross-site request forgery (CSRF) attacks to alter DNS settings. By redirecting users to malicious websites, attackers could execute pharming attacks, compromising all devices connected to the affected routers.
Quishing
Quishing, which is short for "QR code phishing," is a type of cyberattack in which cybercriminals use malicious QR codes to trick people into visiting fake websites or downloading malware onto their devices. These malicious QR codes can be embedded in emails, advertisements, flyers, or simply placed on top of existing QR codes to target an unsuspecting user. The goal of this attack is to steal sensitive information such as passwords and financial data, or to infect a user's device with malware, which can lead to future exploitation.
Example of Quishing
In August 2024, UK motorists were cautioned about 'quishing' scams involving counterfeit QR codes on parking meters. Scammers placed fraudulent QR codes over legitimate ones, directing drivers to fake websites to steal personal and payment information. The RAC advised using cash, cards, or official apps for parking payments and emphasized verifying QR codes for authenticity.
Social Media Phishing
Social media phishing refers to an attack executed through platforms like Instagram, LinkedIn, Facebook, or X to impersonate trusted individuals, brands or organizations. Attackers may create fake profiles, send malicious links through direct messages, or post deceptive content that lures users into clicking harmful links. The purpose of such an attack is to steal personal data, spread malware or even gain control of your social media account.
Example of Social Media Phishing
In August 2024, Trend Micro reported a malvertising campaign where attackers hijacked social media pages, rebranded them to mimic popular AI photo editors, and posted malicious links to counterfeit websites. These deceptive sites prompted users to download software that installed credential-stealing malware, leading to the exfiltration of sensitive data such as cryptocurrency wallets and browser information.
Clone Phishing
Clone phishing involves attackers creating a near-identical replica of a legitimate email previously received by the victim. The cloned email appears to come from the original sender but contains malicious links or attachments. The goal is to deceive the recipient into believing the email is authentic, prompting them to click on harmful links or download malware-laden attachments.
Example of Clone Phishing
In 2017, a Lithuanian man impersonated an Asian-based hardware manufacturer to defraud two major U.S. technology firms of over $100 million. By sending fraudulent emails from fake accounts, he convinced employees to wire payments into his control.
Https Phishing
HTTPS phishing exploits the trust associated with the HTTPS protocol, which indicates a secure connection. Attackers create fake websites with HTTPS certificates so that seem legitimate. Victims are lured to these sites through phishing emails or messages, where they are prompted to enter sensitive information like usernames, passwords, or credit card details.
Example of Https Phishing
In March 2025, a sophisticated HTTPS phishing scam targeting Netflix users emerged, employing AI-generated emails that closely mimicked official communications. These emails, featuring subject lines like "Let's tackle your payment details," informed recipients of account holds due to billing issues and urged them to update payment information via a "update account now" button. Clicking the button led to a counterfeit Netflix login page, prompting users for sensitive data, including usernames, passwords, addresses, and credit card details.
Deceptive Phishing
Deceptive phishing is one of the most common forms of phishing. In this attack, fraudsters impersonate a legitimate company or individual to steal personal data or login credentials. These emails often create a sense of urgency, prompting recipients to act quickly by clicking on malicious links or providing confidential information.
Example of Deceptive Phishing
In November 2024, Trend Micro reported a surge in phishing scams targeting Meta users, including Facebook and Instagram. Attackers sent emails mimicking Meta's branding, falsely claiming security issues like "suspicious activity" or "account suspension." These messages urged recipients to click malicious links leading to counterfeit login pages, where entering credentials allowed scammers to hijack accounts and steal personal information.
Trend Micro Email Security Solution
Trend Micro™ Email Security screens out malicious senders and analyzes content to filter out spam. It examines sender authenticity and reputation and defends against malicious URLs.
Cross-generational threat defense techniques bolster protection against threats, establishing visibility and control across evolving threat landscapes.