What does the pandemic spell out for the digital domain and the threats surrounding it?
We witnessed how the Covid-19 outbreak ushered heavier reliance on online systems. While such dependence was present even before, the need to reduce physical contact heightened it. More legitimate services such as those of the government and healthcare (telehealth) went online. There has also been an increase in online-only systems, including digital-only neobanks. Physical stores were also closed as efforts to expand their online counterparts increased.
As online transactions gradually become the default means to avail of services, various threats also went on the prowl.
Increased dependence on online systems could cause users to trust these platforms more readily without verifying their authenticity. Cybercriminals usually impersonate known entities and create convincing replicas of email, website, or apps from legitimate sources. Due to this, users might have a harder time identifying legitimate platforms from malicious ones. This might be especially true for those who are using online systems heavily for the first time, such as many of the elderly.
Another concern is the spread of misinformation. A problem even before the pandemic, misinformation has since been exacerbated as threat actors took advantage of the increased use of online systems by using Covid-19 and related topics, such as vaccines as bait.
Now that vaccines are in the spotlight, with over 319 million doses administered to over 118 countries, we can only expect this topic to be used more as a social engineering lure. Late last year, the INTERPOL issued a global alert regarding organized crime networks that target Covid-19 vaccines. This includes potential online or offline criminal activities for illegally advertising, selling, administering, and stealing the said vaccines. The group has also recently dismantled a fake vaccine distribution network.
This blog post shares some of our findings on malware, spam, phishing schemes, malicious websites, and illicit markets related to Covid-19 vaccines.
The spread of malware through spam
Beginning the first quarter of 2020, we saw a wave of attacks that were associated with the Covid-19 vaccine. These attacks included but are not limited to the following malware: Emotet, Fareit, Agent Tesla, and Remcos. Countries with affected users include the United States, Italy and Germany.
Emotet
Before authorities’ recent takedown of Emotet C&C servers, we detected a spam campaign that spreads the malware and uses supposed information on Covid-19 vaccine as a lure. We observed that this Emotet spam campaign ran from the start of January until the 24th of the same month. Some of the sample file names of the email attachments are listed here:
- Daily COVID reporting.doc
- DAILY COVID-19 Information.doc
- NQ29526013I_COVID-19_SARS-CoV-2.doc
- GJ-5679 Medical report Covid-19.doc
Countries affected by Emotet include the United States, Italy, and Canada, while the most affected industries are healthcare, manufacturing, banking, and transportation. We were able to identify more than 80 samples of documents with the detection of Trojan.W97M.EMOTET.SMTH. It also turns out that there were similarities in the document files. The following are some of the email subjects that we saw:
- COVID-19 Vaccine Survey
- RE: RE: COVID-19 Vaccine Clinic with Walgreens To Do Now
- Re: #TuOficinaSegura. Pfizer anuncia Vacuna contra el Covid . Novedades Oficinas YA! 10 de Noviembre de 2020
This Emotet campaign used around a hundred command-and-control (C&C) servers; these are IP addresses that can be traced to 33 countries. A majority of the addresses are from the United States, Canada, and France. Days after this massive spam campaign, certain infections of this trojan stealer cannot contact their C&C servers anymore, an event that can be attributed to law enforcement’s aforementioned crackdown on the malware’s servers.
Fareit
Cybercriminals deployed a spam campaign that spreads Fareit malware through emails that baited targets with the mention of the supposed Covid-19 vaccine. Fareit is capable of stealing personal information such as credentials in applications like browser, email, and FTP client. The email subjects used were the following:
- Corona-virus(COVID-19),Common vaccine
- Corona-Virus Disease (COVID-19) Pandemic Vaccine Released
- Latest vaccine release for Corona-virus(COVID-19)
The common attachment files were the following:
- Corona-virus vaccine.arj
- COVID-19 VACCINE SAMPLES.arj
- COVID-19 Vaccine.arj
- vaccine release for Corona-virus(COVID-19)_pdf.rar
The email senders pretended to be from the World Health Organization (WHO) and used doctors' names. The countries most affected were Germany, United States, Italy, China, Spain, and Israel.

Other malware
Aside from Emotet and Fareit, other malware types were used to propagate Covid-19 vaccine-related threats. This includes trojan stealers, namely Lokibot, Agent Tesla, and Formbook. Remote access trojans (RATs) like Remcos, Nanocore, and Android malware like Anubis were also used.
In October 2020, a ransomware variant was reportedly spread through a fake Covid-19 survey. The phishing mail contained an attachment of a purported survey for students and faculty in a university in Canada. We detected this as Ransom.Win32.VAGGEN.A and Ransom.Win32.GOCRYPT.A. Our telemetry still shows detections of this malware, with over a thousand detections mainly in Portugal, the United States, and Israel.
In November 2020, Zebocry reportedly impersonated a pharmaceutical company Sinopharm, which produces Covid-19 vaccines. Here, the attackers involved used a virtual hard drive (VHD) file that stored two files: a PDF for Sinopharm’s presentation slides and an executable that posed as a Microsoft Word document. We detected this as Backdoor.Win32.ZEBROCY.AD and the domain support-cloud[.]life as its C&C server.
The backdoor Remcos was disguised through a file that reportedly had details about the Covid-19 vaccine. Agent Tesla was disguised in a file discussing a Covid-19 vaccine or cure, either for a sample or test results.
Phishing and scams
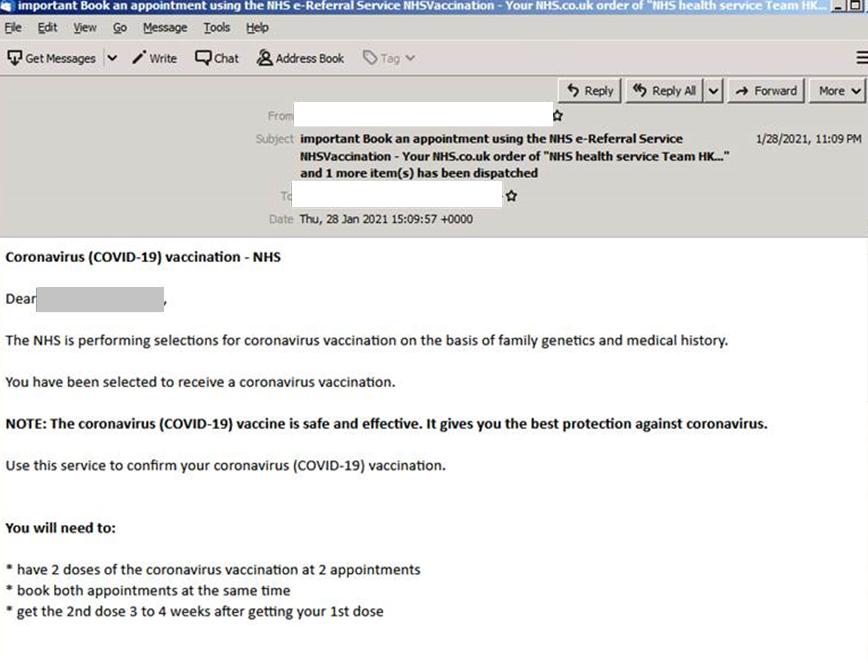
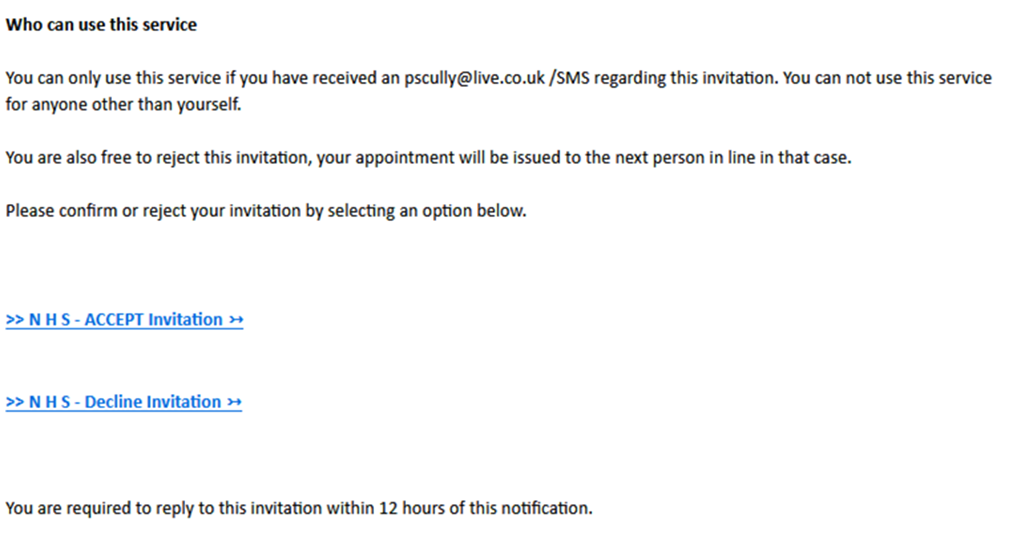
Recently, a phishing campaign that used the name of the UK’s National Health Service (NHS) circulated. The email entices a user to confirm that they accept the invitation for vaccination. Whether the “accept” or “disregard” button of the invitation is clicked, the email redirects to a landing page. This page displays a form requesting the user’s full name, birth date, address, and mobile number. We detected this campaign in the United Kingdom, Germany, United States, and the Netherlands.
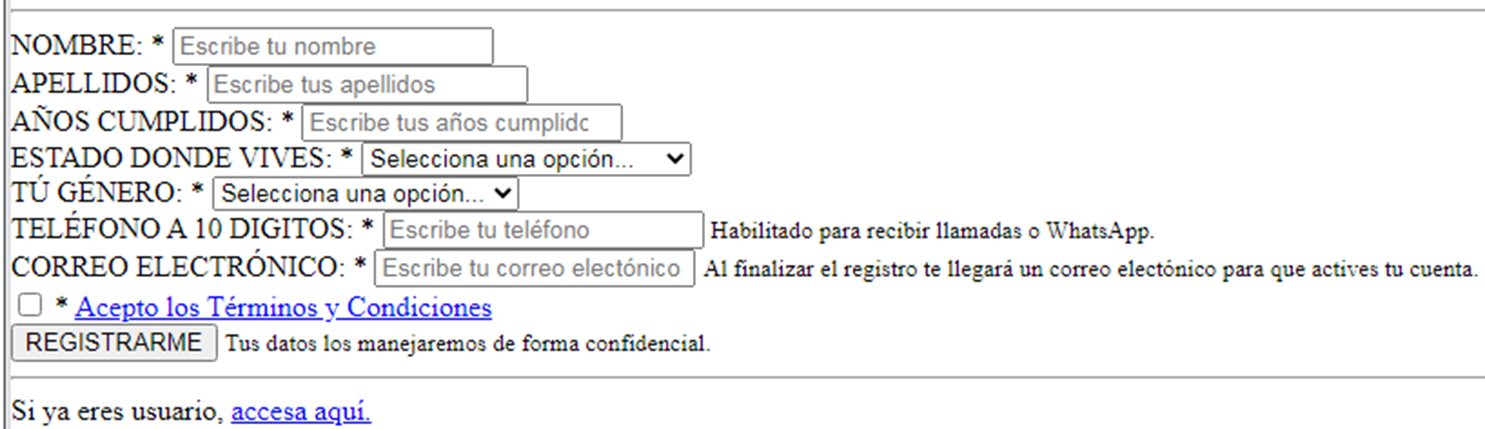
Another recent phishing campaign, which circulated in Mexico, used a website that was disguised as that of the medical laboratory “El Chopo,” which looks identical to the legitimate lab. It required details such as name, age, address, gender, mobile number, and email address. After the users register, they will supposedly receive a digital certificate for the National Vaccination Card and will be requested to wait for the cards’ activation. Through the site, users can reportedly schedule an appointment for the vaccine, and after paying MXN 2,700 (approximately USD 130), they will receive a supposed confirmation. The site even provided bogus contacts such as email addresses and Facebook and WhatsApp pages for any inquiries. We detect the phishing sites such as vacunacion.elchopo[.]mx, dinero-vacunacion.elchopo[.]mx, xn--vacunacin-d7a.elchopo[.]mx and infra-medica[.]com which are hosted in IP 64.22.104[.]14.
.png)
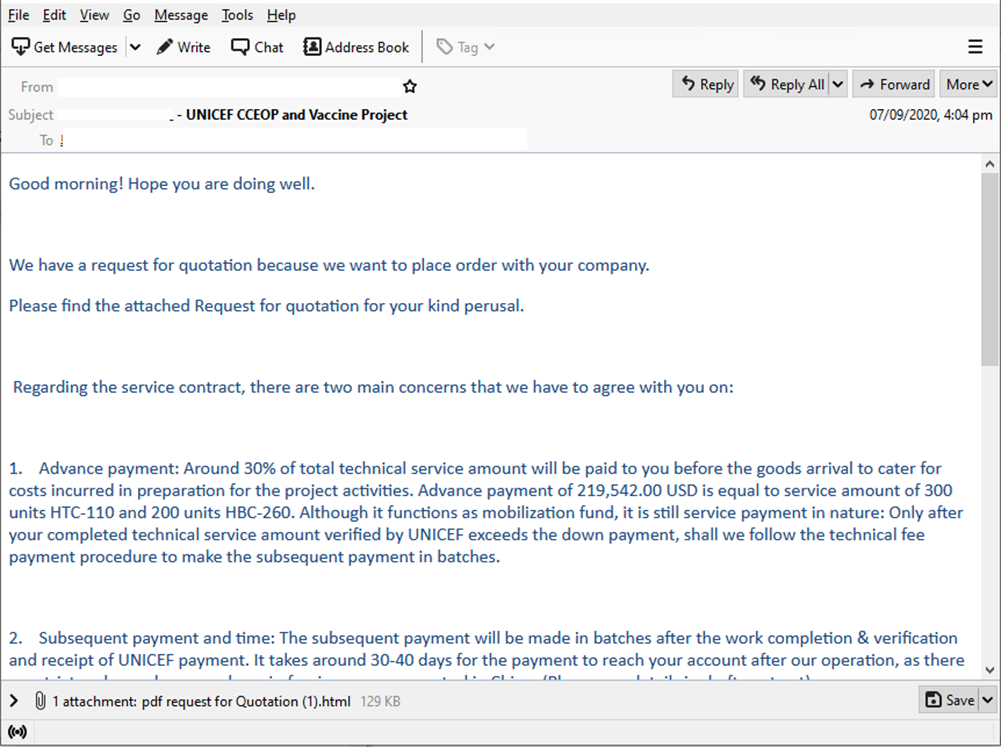
In September 2020, we observed a phishing campaign with the theme of equipment used for secure and safe transportation of vaccines. It was disguised as Unicef’s procurement for Gavi’s Cold Chain Equipment Optimization Platform (CCEOP) with a quotation request as an attachment. The attachment is an HTML file that displays a phishing page. The campaign had 20 domains and used hosting IP addresses located in the Netherlands. Trend Micro blocked the phishing domains, and the HTML files were detected as Trojan.HTML.PHISH.TIAOOHWY.
Malicious actors are still circulating several Covid-19 vaccine-related scams. These range from the distribution of vaccination cards, selling of vaccines, appointments for vaccination, and others. DomainTools has reported on illegitimate CDC vaccination record cards that are allegedly exclusive in the US for an individual’s proof of vaccination. Each card costs US$20, or US$60 for a pack of four.
Some scammers also use SMS in their campaigns. One such example is a scammer who pretended to be from a pharmaceutical company. The message used by this scammer states the receiver’s eligibility to get vaccinated, and then provides a contact number for registration. The scammer will likely ask for money once contacted via the number.
The government and law enforcement agencies of different countries continuously advise the community to be wary of such scams. The US government even took down scam sites of entities assuming the names of biotechnology companies purportedly developing treatments for Covid-19.
Malicious domains
Last year, DomainTools started providing a free, curated list of high-risk COVID-19-related domains to support the community during the global health crisis. Using this list of domains (mostly bearing the keyword “covid”) and feedback from the Trend Micro™ Smart Protection Network™, we came up with a list of 75,000 malicious domains. The categories of domains include malware, phishing, scam, and low reputation.
This year, we have seen an uptick in the creation of malicious domains bearing the keyword “vaccine.” Based on the report by DomainTools, starting November of 2020, there was a spike in the creation of domains bearing the word “vaccine.” On the other hand, the number of domains with the word “covid” has subsided since June 2020. We identified around 1,000 malicious domains bearing the keyword “vaccine” during our analysis. In November 2020, 100 domains were registered to mimic pharmaceutical brand names for the Covid-19 vaccine, such as the following:
- Gam-COVID-Vac
- BioNTech’s BNT162 vaccine (COVID-19 mRNA vaccine)
- EPI - VAK - KORONA
- PiCoVacc
- Sputnik V
Illicit markets
Cybercriminals also created sites using the Covid-19 vaccine as a lure. In 2020, the domain vaccine-coronavirus[.]com was active. Currently inactive as of writing, this site was previously disguised as the website of a medical university. From this site, users could supposedly buy vaccines using bitcoin as a mode of payment. More importantly, there is no guarantee about the vaccine’s authenticity or if the operators behind this scheme would send anything after receiving payment.
.png)
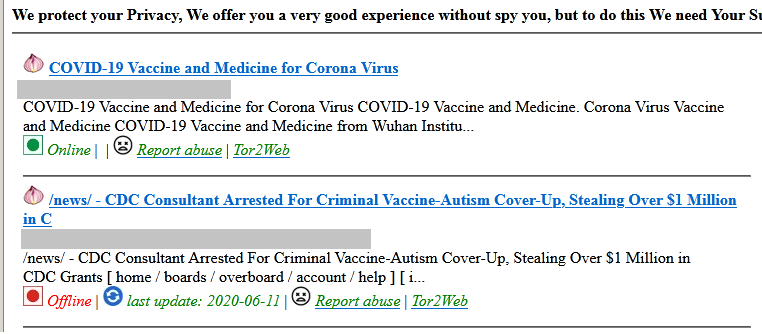
The hidden service and anonymity afforded by the dark web have made it an ideal place for cybercriminals to sell illegal vaccines. A recent report talks about an underground site where operators claim to have developed a vaccine that is not only ready for purchase but also available for shipping worldwide.
Another darknet site required buyers to send their personal details and even their Covid-19 infection status and known diseases to an email address. These details must also be submitted with payment in the form of bitcoin. We believe this is a scam site.
Meanwhile, another report discusses the sale of alleged vaccines for US$250 on underground forums.
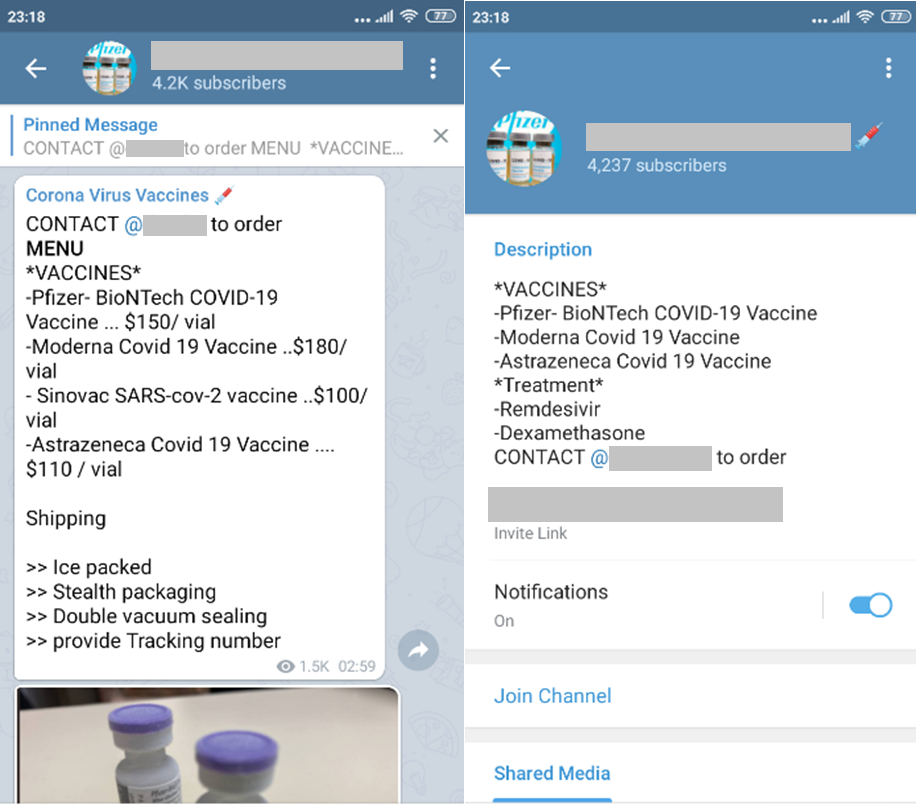
Recently, Covid-19 vaccine scams are reportedly spreading through Facebook and Telegram. This is alarming since one of the Telegram channels associated with this already has more than 4,000 subscribers. In particular, this channel supposedly offers vaccines from known brands. According to the article, a researcher tried to bait the scammer and ended up in a scam site disguised as the website of a popular courier. We were able to identify the scam site and noted that the closest domain based on the available description is the domain deltaexpressairline[.]com. A search for more scam sites using Delta Express revealed 31 more domains.
Solutions
With the ongoing health crisis, it is understandable that people are searching for ways to buy a vaccine. However, the public should be careful as many entities take advantage of this trend. More importantly, it is worth emphasizing that fake vaccines could have health repercussions — if scammers actually deliver anything after receiving payment.
Users can prevent the cybersecurity risks from these scams by not clicking on links or downloading attachments in emails from unknown sources. Users should also regularly patch and update their systems.
These systems can also be secured by a multilayered security approach for protecting endpoints, emails, web, and networks.
Online scams highlight the need to be vigilant with the information circulating online. Here are some tips on spotting misinformation:
- Get information from trusted sources. For COVID vaccine information, contact either the local health authorities or health care providers.
- Think before you click. Avoid forwarding or sharing messages and posts without verifying them first (for example, by fact-checking them through reputable search engines and news sites). By doing this, you can help contain the spread of scams and wrong information.
- Identify fake or malicious emails, websites, and apps. Some telltale signs include misspellings, grammatical errors, and incorrect names and logos of known institutions. However, some scams use convincing replicas of legitimate emails, websites, apps, and other platforms used by the organizations they’re impersonating. If unsure, it’s best to double-check with other sources such as the company’s official social media sites and contact information.
- Attend and/or conduct cybersecurity training. Increased awareness and knowledge of online scams and other types of misinformation can help identify these schemes.
Trend Micro Check can also help detect misinformation, scams, and similar online threats. A free multiplatform tool powered by artificial intelligence (AI), Trend Micro Check offers scam link detection, email security review, fact-checking of text, audio, and visuals to identify misinformation, and news outlet credibility verification. Since its launch, it has identified more than 2 million scams and 3 million instances of misinformation. Trend Micro check is available via Facebook Messenger, WhatsApp, and Google Chrome (as an extension).
Phish Insight provides the most effective phishing simulations and cybersecurity awareness training modules on the market. Powered by Trend Micro, the Phish Insight team creates a simulation template library based on billions of real phishing samples as well as a fully automated and staggered delivery system that makes the simulation emails even more convincing. Not only integrating the best and the most prevalent training modules from around the world, Phish Insight also allows users to customize their own training programs. Phish Insight enhances information security awareness for organizations by empowering people to recognize and protect themselves against the latest cyber threats.
Indicators of compromise
SHA256 |
Trend Micro Pattern Detection |
File Name |
56d85a979245364288d1814d5c45a8acf653c5da47d2eefe8f60f7b7de194e9c |
Mal_GENISO-4 (Agent Tesla) |
NEW COVID-19 VACCINE- CURE- UPDATE.Xlxs.iso |
69ae4cd1cbb84c2144408975682f1f24229d8d5a1988b12fff18fd0472cffffb |
HEUR_VBA.E2 |
Covid vaccine access - confidential.docm |
64f61dd41ec3a411e647f6371b8500666db3c96cc57a8cb0c16d47cceaf12aa9 |
TrojanSpy.AutoIt.NEGASTEAL.SMB.hp |
COVID-19 VACCINE.exe |
041320839c8485e8dcbdf8ad7f2363f71a9609ce10a7212c52b6ada033c82bc5 |
TrojanSpy.Win32.FORMBOOK.L |
vaccine_release_for_Corona-virus(COVID-19)_pdf.exe |
cbf5be2bd3f2d0d5bc495228c034d303d728c11b6bbf58cdcf313c6bf7321321 |
TrojanSpy.Win32.NEGASTEAL.THEAEBO |
COVID-19 Update Treatment Vaccine.pdf.exe |
8a020281d5b475372fcf518c8f4a6b913b3a855c458996a9d7b525062ad736ec |
TrojanSpy.Win32.NEGASTEAL.THEAEBO |
NEW COVID-19 VACCINE- CURE- UPDATE.Xlxs.exe |
56a4523b72aef34982a90a480c17386862d4788c0501b9982d798d43c860cc6c |
TrojanSpy.Win32.NEGASTEAL.THEAEBO |
Download_Covid.19_New Cases_and_New_Vaccine.doc.exe |
eecb7b15a90df049ba18e11ebe23ca8fa83900d11f6154807da5bb07314f255d |
Backdoor.MSIL.REMCOS.SM |
Covid-19 vaccine Brief summary.exe |
43c222eea7f1e367757e587b13bf17019f29bd61c07d20cbee14c4d66d43a71f |
Ransom.Win32.VAGGEN.A |
|
a88612acfb81cf09772f6bc9d0dccca8c8d5569ea73148e1e6d1fe0381fe5aec |
TrojanSpy.AutoIt.NEGASTEAL.SMB.hp |
COVID-19 Vaccine Sample.exe |
e17f4fc412f2d30169c6da41687bebbbdb390969a38458143c11474a08afec50 |
AndroidOS_FakeApp.NGPF |
Vaccine-register.apk |
b6087bb0059e7e8d33e2d34a48e3f1db439e01fcd8856e7159428e9562df7067 |
Trojan.Win64.WOREFLINT.A |
PAPER-COVID-19-Vaccine-Strategy.pdf |
76888b745714b1d0db8cd883eaac756c560b052462cae240c3917c441c07d611 |
TrojanSpy.Win32.NEGASTEAL.THEAEBO |
Download_Covid.19_New Cases_and_New_Vaccine.doc.exe |
6d0e370da27f452ed7b21d468d607eb3b938cc798ec563209ce6f67e752963b7 |
TrojanSpy.Win32.NEGASTEAL.THEAEBO |
COVID-19 VACCINE- TEST-RESULT.exe |
158af91147262440a1f8356d1f8f9cba48b168b97924bea50440d67c679c6c6d |
BKDR_SWRORT.SM |
vacuna-covid.exe |
b6162314e5f6edda9b033494a8dc5116cf831456815825949d1f59a5651d40f3 |
BKDR_NOANCOOE.SM |
COVID-19 VACCINE.EXE |
e6be29fa3a68946d8e2239ad60d37b900ddf58cb2c63245dda916f560c081679 |
Mal_GENISO-4 (Agent Tesla) |
COVID-19 VACCINE- TEST-RESULT.exe |
a08c6a65851bfe6b9c33d42c54d64869293f6119f9dd94cc060c8233e647568a |
BKDR_NANOCORE.SMD |
COVID-19 VACCINE.exe |
00c60593dfdc9bbb8b345404586dcf7197c06c7a92dad72dde2808c8cc66c6fe |
Ransom.Win32.GOCRYPT.A |
|
bfbada8b0ecc1f711dd4869c7fc97f658b88dc497a415a2e912eff9245fe9c9b |
TrojanSpy.Win32.NEGASTEAL.THEAEBO |
Download_Covid.19_New Cases_and_New_Vaccine.doc.exe |
b9bff597e8376ad448c493f4b7eb3e3c500c60528834b3b4a46a1493e3a56694 |
AndroidOS_Anubis.GCL |
Vacuna_COVID19_Chile.apk |
2b4d07dc6df290801e6dec29d4cd0649d52f0c001a171604cf374c84f57c63a2 |
TROJ_CVE20171182.SM |
COVID-19 VACCINE SAMPLES.xlsx |
052e19392c73c979c31554983a4aed5589c4ece553083dddfb4fe14ee55c440a |
TrojanSpy.Win32.LOKI.SMDF.hp |
Corona-virus(COVID-19)vaccine.exe |
2cf2568dad46a638b8e4d86aa46f4cd279511dba9900286e22aeaefc39189a88 |
Backdoor.MSIL.NANOCORE.TIAOODFN |
Covid-19 Vaccine.gz |
76299e863b71caed1b9950d904d1b52a8174b9077c9d4bc896276881caa46fad |
BKDR_NOANCOOE.SM |
COVID-19VACCINE_.exe |
bbb0f2855d1444cae835700f58acb51b6a6fd2f48046e94850982753cb4a7268 |
TrojanSpy.Win32.NEGASTEAL.THEAEBO |
Download_Covid.19_New Cases_and_New_Vaccine.doc.exe |
7e765af2d1bf7c139df8fb2bb5eef1268b3cf356f7192f4f221c42104fad2a89 |
TrojanSpy.Win32.LOKI.SMDF.hp |
Corona-virus_28C_arj.bin |
f36a0ee7f4ec23765bb28fbfa734e402042278864e246a54b8c4db6f58275662 |
Backdoor.Win32.ZEBROCY.AD |
|
fc2cc8b7cf51f41d40121d63c21c9ae1af4f8f6126b582ace5ed4a5c702b31c3 |
TrojanSpy.Win32.FORMBOOK.L |
vaccine release for Corona-virus(COVID-19)_pdf.rar |
URLs
- ip-160-153-254-152[.]ip.secureserver[.]net/nfz
- ip-160-153-254-254[.]ip.secureserver[.]net/nhs
- ip-160-153-254-152[.]ip.secureserver[.]net/CVD19
- ip-160-153-246-67[.]ip.secureserver[.]net/NHSonline
- ip-107-180-73-44[.]ip.secureserver[.]net/WEB/parcel.php
- IP 64.22.104[.]14
- support-cloud[.]life
- hxxp[:]//t[.]me/Darkwebvendor
- hxxp[:]//t[.]me/Buy_COVID_19_Vaccines
- covidsgaonvjnd6z[.]onion
- vaccine-coronavirus[.]com
- vacunacion[.]elchopo[.]mx
- dinero-vacunacion[.]elchopo[.]mx
- xn--vacunacin-d7a[.]elchopo[.]mx
- infra-medica[.]com
Emails
- darknetmarket1@protonmail[.]com
- cvdntdrs@protonmail[.]com
- orders@vaccine-coronavirus[.]com

