Social media influencers build and expand their business or brand through credibility and authenticity to their audience. For hackers, however, they could be seen as trophies. That’s what happened to a photographer with more than 15,000 followers on Instagram, when she had her account stolen.
A closer look into the incident revealed that the hacker got into her account through phishing. While it seemed straightforward enough, we also found that targeting popular Instagram profiles has become a modus for a certain group of Turkish-speaking hackers. And by abusing Instagram’s account recovery process, they were able to keep the stolen account even if the victim squarely followed the process. We’ve seen cases where owners of Instagram profiles with followers between 15,000 and 70,000 were hacked and were never retrieved. The victims ranged from famous actors and singers to owners of startup businesses like photoshoot equipment rentals.
The group also engages in digital extortion. Once a victim tries to reach out to the hacker, they would be wringed to fork over a ransom or nude photos and videos to get the account back. Of course, the hackers never give it back. Indeed, this kind of attack — targeting high-profile accounts or social media influencers — highlights our predictions for this year’s threat landscape.
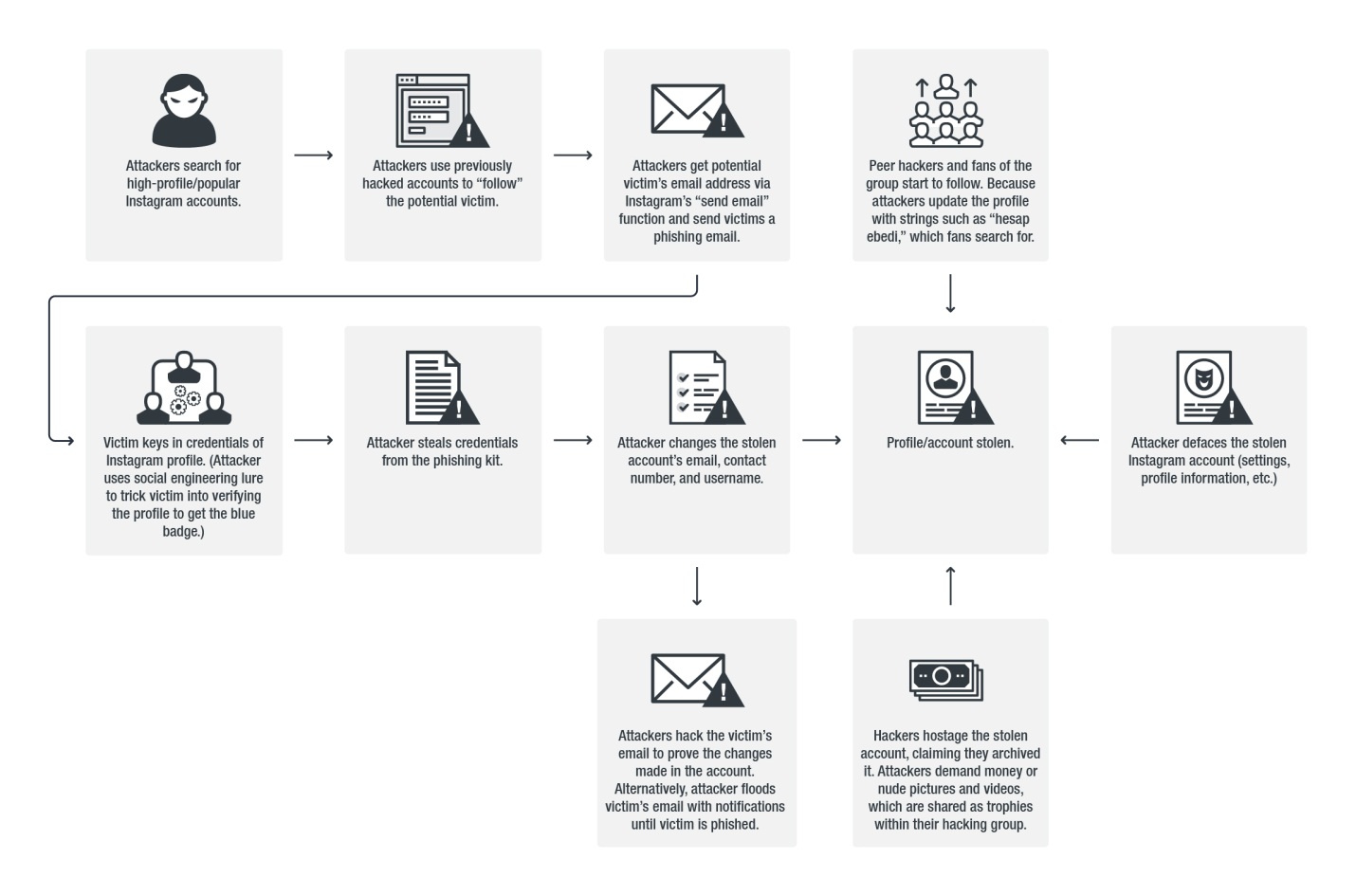 Figure 1: A visualization of how the hackers are stealing the Instagram profiles
Figure 1: A visualization of how the hackers are stealing the Instagram profiles
Attack chain
Analysis of the phishing kit revealed that the hosting system blocks requests from wget. We managed to obtain the phishing kit by spoofing a user agent.
The compromise starts with a phishing email pretending to be from Instagram. The email prods the potential victim to verify the account to get the Verified badge for the user’s Instagram profile. Note that Instagram has specific requirements and the verification process happens only after a user requests for it. Instagram doesn’t ask for credentials either.
 Figure 2: Screenshot of the phishing email asking the user to verify his Instagram account
Figure 2: Screenshot of the phishing email asking the user to verify his Instagram account
 Figure 3: The phishing page the user gets redirected to (left) and another that asks for the user’s email credentials (center); after credentials are keyed in and submitted, the user will be redirected to a page that notifies the profile has been verified (right)
Figure 3: The phishing page the user gets redirected to (left) and another that asks for the user’s email credentials (center); after credentials are keyed in and submitted, the user will be redirected to a page that notifies the profile has been verified (right)
Once the user clicks the “Verify Account” button, he will be redirected to a phishing page that asks for the user’s date of birth, email, and credentials. When we first saw these pages, they didn't have any data validation on the input and returned the same screen even after submitting an empty form. However, they’ve since added basic data validation by not letting the user submit an empty form.
Once the attacker has access to both the victim’s Instagram profile and the email related to the account, the hacker can then modify the information needed to recover the stolen account. The victim will also be prompted to enter his email’s credentials. Once submitted, a badge notification appears, but for only four seconds. This is a trick to give users the impression that their profile has been verified.
After some time, the phishing page will be diverted to Instagram’s website. This is a common tactic in phishing. It’s likely that the victim would already be logged in with cookies, so the victim may just be diverted to his Instagram profile. Since we tested the phishing kit in a clean environment, we only got Instagram’s login page.
The hacker’s modus
We looked further into these cases to learn about the hackers’ motives and how they operate. In an Instagram profile they’ve hacked, they changed its username to “natron_raze”, probably to indicate it was hacked. The email associated with the profile was also immediately modified. After some time, the account’s email was changed again. The trick here is to flood the victim with Instagram’s security emails asking if the changes were legitimate. The hacker would also try to draw the user’s attention by defacing the profile.
Figure 4: A defaced Instagram profile aiming to get attention from its owner
After the profile was compromised, other accounts immediately followed it. Some were fake profiles, while the others were either previously stolen profiles or the hackers themselves. After some time, we saw the hacker removing the hacked accounts from his follower lists, although some returned. This could probably be because the hacker realized that his modus was being monitored.
In one instance, we saw the hacker threatening to delete the account or never return the stolen profile unless the victim pays a ransom or sends nude photos or videos. The hacker also let others know he stole another account, as shown in Figure 4.
Figure 5: Screenshots of the hacked and defaced Instagram profiles
Searching for more information on “Hesap Ebedi,”(Turkish words for “account” and “eternal”) we found a forum from a hacking group discussing how to manage stolen accounts so their owners cannot get it back, even with the help of Instagram’s account retrieval process.
Figure 6: Forum post on turkhackteam mentioning the attack dynamics of stealing Instagram accounts
We reached out and disclosed our findings to Facebook and Instagram but have yet to receive a response as of this writing.
Defending against phishing
The hackers in these instances lure victims into handing out personal information to get an incentive (such as a blue badge in their profile). Their mimicry of Instagram’s emails also made their malicious emails appear legitimate. Here are some of the red flags users and businesses can watch out for:
- Use of domains other than the social network’s own
- Dubious font styles (i.e., usage of screenshots instead of actual images)
- Incorrect grammar and punctuation
- Emails that ask for credentials; social networks never ask for them outside of their actual, secure login pages
Trend Micro Smart Protection Suites and Worry-Free™ Business Security protect users and businesses from these phishing attacks by detecting malicious files and spammed messages and blocking related malicious URLs.
Indicators of Compromise (IOCs)
IP address related to the phishing attack:
- 185[.]27[.]134[.]212
- 104[.]24[.]119[.]10
- 2606[:]4700[:]30[::]6818[:]760a
- 2607[:]f8b0[:]4864[:]20[::]243
URLs related to the phishing attack:
- hxxps://2no[.]co/2WPr35
- hxxps://confirm[-]service[.]tk
- hxxp://instagrambluetick[.]ml/?i=1
- hxxp://instagrambluetick[.]ml/mailconfirmation[.]php
- hxxp://instagrambluetick[.]ml/confirmed[.]php
- hxxps://Instagram[.]derainbow[.]es
- hxxp://urlkisaltma[.]com/27rjN
- hxxp://urlkisaltma[.]com/farES





