What is Cyber Security Compliance?
Cyber Security Compliance
Compliance in cyber security refers to the practice of adhering to established frameworks, standards, and regulations that are designed to protect sensitive data and information systems within organizations. Cyber security compliance ensures that organizations follow best practices to mitigate cyber risks, safeguard assets, and by achieving compliance, it can help maintain trust among customers and stakeholders.
A well-structured compliance program reinforces both legal and ethical accountability, ensuring businesses build trust while maintaining strong security controls. Without it, organizations risk not only cyberattacks and operational failures but also long-term reputational and financial damage.
Why is Cyber Security Compliance Important?
With cyber threats increasing in frequency and sophistication, ensuring compliance with cybersecurity regulations is no longer optional, it is a business necessity. Failure to comply with security compliance requirements can lead to severe consequences, including:
Legal and Financial Penalties: Organizations found in violation of cybersecurity laws and regulations may face hefty fines, lawsuits, or even loss of business licenses.
Reputation Damage: A data breach resulting from non-compliance can erode consumer trust, causing customers to lose confidence in a business.
Operational Disruptions: Non-compliance may leave security vulnerabilities unaddressed, leading to system downtime, operational losses, and potential data loss.
By aligning with compliance standards, organizations can reduce their exposure to cyber risks, improve their security posture, and demonstrate their commitment to data protection.
Key Cyber Security Compliance Frameworks and Regulations
There are numerous cybersecurity laws and regulations that govern how businesses handle data and protect their IT systems. Below are some of the most recognized compliance frameworks:
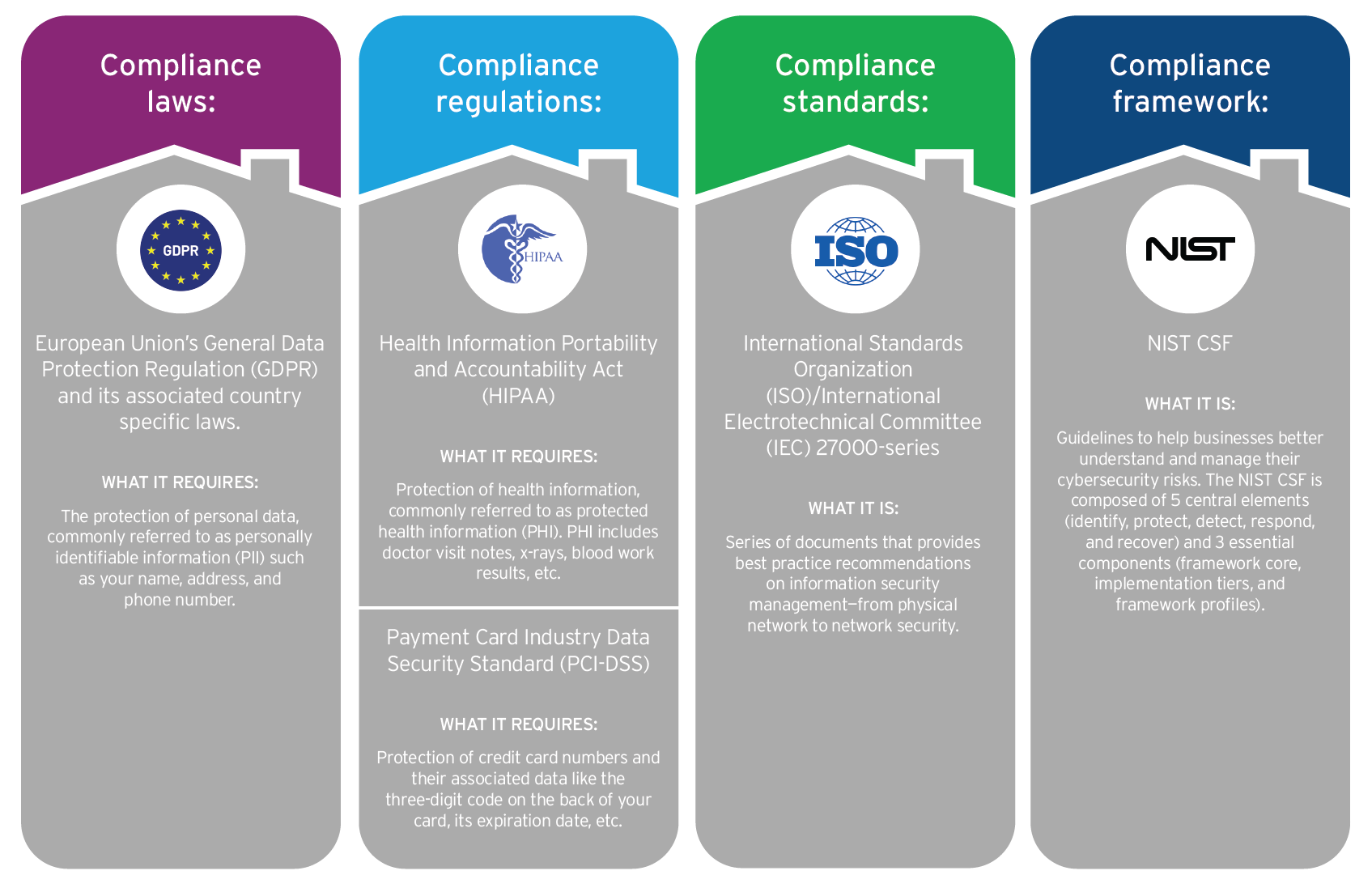
General Data Protection Regulation (GDPR)
GDPR is focused on data privacy and protection for EU residents and mandates organizations to secure personal data and maintain transparency in data usage. Organizations that are non-compliant can face fines of up to €20 million or 4% of their annual global revenue, whichever is higher.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is a U.S. regulation that governs the secure handling of protected health information (PHI). Healthcare organizations have to apply strict measures to protect their patients' data, such as data encryption, strict access controls, and security risk assessments.
Payment Card Industry Data Security Standard (PCI-DSS)
PCI DSS is a set of policies and procedures designed to protect cardholder data and reduce card payment fraud for organizations that process, store, and transmit credit card information. Although PCI DSS is a standard and not a law, non-compliant organizations can risk losing partnerships with major card payment providers, such as Visa, Mastercard, or American Express.
National Institute of Standards and Technology (NIST) Cybersecurity Framework 2.0
The NIST framework provides a structured approach for managing cybersecurity risks, which focuses on five key functions:
- Govern - Establishes and monitors the organization's cybersecurity risk management strategy, expectations, and policy..
- Identify - Assists in understanding the organization's assets, data, and associated cybersecurity risks.
- Protect - Focuses on implementing safeguards to ensure the delivery of critical services.
- Detect - Involves continuous monitoring and detection processes to identify anomalies and potential incidents.
- Respond - Outlines appropriate actions to take once a cybersecurity incident is detected.
- Recover - Supports the restoration of capabilities or services impaired due to a cybersecurity incident.
ISO 27001 Compliance
ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a framework for information security teams to help organizations identify and manage their information security risks.
Organizations operating in multiple jurisdictions may also need to comply with frameworks like SOC 2, FISMA, and CMMC, depending on their industry and regulatory requirements.
We briefly mentioned a few of the well-known compliance standards—let’s take a deeper look to 4 for of them:
Best Practices for Cyber Security Compliance
A strong cybersecurity compliance program helps organizations meet regulatory requirements, protect sensitive data, and mitigate security risks.
Establish Clear Compliance Policies and Documentation
Organizations must define security policies that align with industry regulations and these policies should specify:
Data access controls: Who can access sensitive data and under what conditions?
Risk management protocols: How will the organization identify, assess, and mitigate cyber risks?
Incident response procedures: What actions should an organization take in the event of a breach?
Compliance monitoring guidelines: How will the organization track and ensure continuous adherence to cybersecurity standards?
Conduct Regular Security Audits and Risk Assessments
Organizations should conduct routine security audits and risk assessments as they can help to:
Identify security gaps and vulnerabilities.
Verify adherence to regulatory compliance cybersecurity standards.
Detect outdated security controls that need enhancements.
Ensure third-party vendors comply with security requirements.
Implement Strong Data Protection and Access Control Measures
Organizations must implement strong data protection policies to ensure network security compliance by incorporating:
Encryption: Protect sensitive data at rest and in transit to prevent unauthorized access.
Multi-Factor Authentication (MFA): Strengthen authentication protocols to minimize the risk of credential theft.
The Principle of Least Privilege (PoLP): Restrict access rights to only those necessary for an employee’s role.
- Secure data disposal: Ensure obsolete data is destroyed in accordance with compliance regulations like ISO 27001 compliance and GDPR security compliance.
Develop a Dedicated Compliance and Security Team
A successful compliance program requires leadership and accountability. Organizations should appoint:
A Chief Information Security Officer (CISO) or compliance officer to oversee compliance efforts.
A cross-functional security team that collaborates with IT, legal, and operational teams to ensure company-wide compliance.
Third-party compliance consultants if internal expertise is insufficient.
Employee Training and Cyber Security Awareness
A well-informed workforce is a critical defense against cyber threats. Businesses should:
Implement regular cybersecurity awareness training to help employees recognize phishing attacks, social engineering tactics, and malware threats.
Educate staff on security compliance best practices and the consequences of non-compliance.
Maintain an Incident Response and Breach Reporting Plan
Organizations must have a clear incident response plan to contain, mitigate, and report security breaches quickly. A compliant incident response framework should include:
Incident detection and analysis: Identifying potential security threats in real-time.
Containment and mitigation strategies: To minimize damage and prevent further compromise.
Regulatory breach reporting: Ensuring timely notification to relevant authorities, stakeholders, and affected individuals (as required under GDPR, HIPAA cybersecurity regulations, and PCI-DSS requirements).
Leverage Cybersecurity Compliance Tools and Automation
Compliance management can be complex, but organizations can streamline processes using security tools such as:
Security Information and Event Management (SIEM) systems: Centralized monitoring of security events and compliance violations.
Compliance management platforms: Automate policy tracking, audit logs, and security assessments.
- Automated vulnerability scanners: Identify system weaknesses before cybercriminals exploit them.
Benefits of Cyber Security Compliance
Aside from avoiding legal consequences, cybersecurity compliance offers numerous advantages, including:
Enhanced Data Protection
Compliance mandates strong security controls and regular audits, which help protect sensitive information from breaches and unauthorized access. This minimizes the risk of data loss and maintains customer privacy.
Risk Mitigation
Adhering to compliance standards means identifying vulnerabilities before they become critical. This proactive approach significantly reduces the likelihood of cyberattacks and other security incidents.
Legal and Regulatory Assurance
With clear guidelines and benchmarks in place, compliance ensures that organizations meet the necessary legal and regulatory obligations. This reduces the risk of incurring fines, penalties, and costly legal disputes.
Improved Operational Efficiency
A structured compliance program streamlines security processes and policies, reducing redundancies and improving overall operational efficiency. This often results in faster response times and a more agile IT infrastructure.
Challenges in Cyber Security Compliance
Managing cyber security compliance is complex for organizations and has a variety of challenges, such as:
Evolving Regulations and Security Standards
Cybersecurity regulations, such as GDPR, HIPAA, PCI-DSS, and ISO 27001, are frequently updated to address emerging threats. Organizations must continuously revise policies, implement new security measures, and ensure compliance with jurisdiction-specific requirements to avoid legal penalties and data breaches.
Balancing Security Controls with Business Operations
Strict security measures can sometimes disrupt business processes if not carefully integrated. Companies must find a balance between enforcing compliance and maintaining productivity by aligning cybersecurity initiatives with operational objectives and leveraging automation to streamline security enforcement.
Third-Party Vendor and Supply Chain Risks
Many organizations face challenges in managing third-party compliance, especially when relying on cloud services, contractors, and external partners. To reduce supply chain vulnerabilities, businesses should regularly assess vendor risks, enforce security requirements through contracts, and implement continuous monitoring to ensure adherence to cybersecurity standards.
Complexity and Cost of Compliance Management
Many organizations struggle with compliance silos, redundant security controls, and resource-heavy assessments and without a centralized approach, it becomes complex to maintain compliance across multiple frameworks. Organizations can automate security processes, improving visibility, and streamlining workflows that can help to reduce administrative workload, reduce assessment fatigue, and lower audit costs.
Demonstrating Compliance and Security Control Effectiveness
Regulators and stakeholders require clear evidence of security control efficacy. Organizations need real-time monitoring, security analytics, and comprehensive reporting to provide visibility into risk mitigation efforts and ensure that cybersecurity measures align with compliance mandates.