Posts in this series
This article is the second in a series that discusses the challenges that IT departments face when they are assigned the task of overseeing cybersecurity in factories and implementing measures to overcome these challenges. Before beginning to consider countermeasures, in the first article we explained the source of the challenges while focusing on the differences between the objectives of IT and OT systems and on tasks to support these systems. In this second article, we will carry out an analysis to uncover the challenges that lie in the way of promoting factory security from an IT perspective and seek solutions. We will consider the challenges in terms of people, processes, and technology, which are the elements of IT service management at ITIL.
People: Cross-organizational projects at a standstillMany smart factory and IoT projects are promoted as cross-functional efforts under Digital Transformation (DX) within a business strategy. Although in some companies DX promotion and IoT promotion teams may be formed to lead such projects, personnel from other departments, such as manufacturing departments and information system departments, engage in planning and implementation alongside their main jobs. The Japan Users Association of Information Systems (JUAS), one of Japan's largest user communities, reported that collaboration between IT departments and business departments accounted for 41.7% of bodies that play major roles in planning process digitization (the highest percentage), IT departments for 35.2%, and departments specializing in digitization for 5.1%, the lowest percentage.*1 Regarding organizational involvement in security, a survey conducted by Trend Micro*2 revealed that approximately 80% of companies that have started to work on IIoT-related initiatives involve their IT departments, whereas only approximately 40% involve their security-related decision-makers.

Figure 1: Trend Micro, "IoT Security Survey of Corporations"*2
Alongside the trend toward promotion of IoT, there have been an increasing number of cyberattack incidents in Japan and abroad as well as a rise in demand for management-level measures to address various guidelines. In this context, some companies have formed independent teams that are responsible for overseeing security on a company-wide basis. Generally, information system departments provide back-office services as part of head offices, whereas manufacturing departments are located in factories or spun off as different companies as a result of separating manufacturing and sales. In many cross-organizational projects, time and effort are required to account for differences in interest due to the many stakeholders; it is unclear where responsibility lies; and organizational barriers and abilities tend to affect progress, though of course this is not limited to projects related to IoT and security,.
In terms of talent, a recent survey*3 noted that there will be a shortage of approximately 193,000 information security professionals in Japan, and the development of security talent is increasingly being discussed and initiatives undertaken. For example, the Plan for General Development of Security Talent devised by the National Center of Incident Readiness and Strategy for Cybersecurity (NISC)*4 defines the (1) management layer (CSO, CISO), (2) strategic management layer (bridging talent), and (3) practitioner layer, and NISC reports that design and implementation of the skills required for these layers as well as education and training for acquiring such skills are underway. In addition, in the manufacturing industry, there is rising demand for talent that understands both IT and OT, despite the fact that demand was low in the previous environment in which IT and OT were separated.
To solve organizational and talent-related challenges, managerial leadership is crucial. Security awareness raising and education as well as cross-departmental interactions will have more significance when objectives are shared across organizations.
*1 Japan Users Association of Information Systems: "2019 Corporate IT Trends Survey Report," April 2019.
https://juas.or.jp/cms/media/2017/02/it19_ppt.pdf
*2 Trend Micro: "IoT Security Survey of Corporations," May 2019.
https://resources.trendmicro.com/jp-docdownload-form-m120-web-iot-security-report.html
*3 Ministry of Internal Affairs and Communications: "Present State of Cybersecurity Talent in Japan," December 2018.
https://www.soumu.go.jp/main_content/000591470.pdf
*4 Cyber Security Strategy Headquarters (NISC): "Plan for General Development of Security Talent," March 2016.
https://www.nisc.go.jp/active/kihon/pdf/jinzai_kyoka_hoshin.pdf
Processes: Operations to avoid stoppagesSome claim that stocktaking of information assets, installation of security software, and application of patches, which are common IT security practices, are unacceptable in OT system operations. The manufacturing department strikes a balance among output QCD (Quality, Cost, and Delivery) and S (Safety), and controls the input 4M (Man, Material, Machine, and Method) in order to improve production. As described in the first article, the principal purpose of OT system operations is to eliminate all factors that may impair the safety and availability of the Machine, or system.
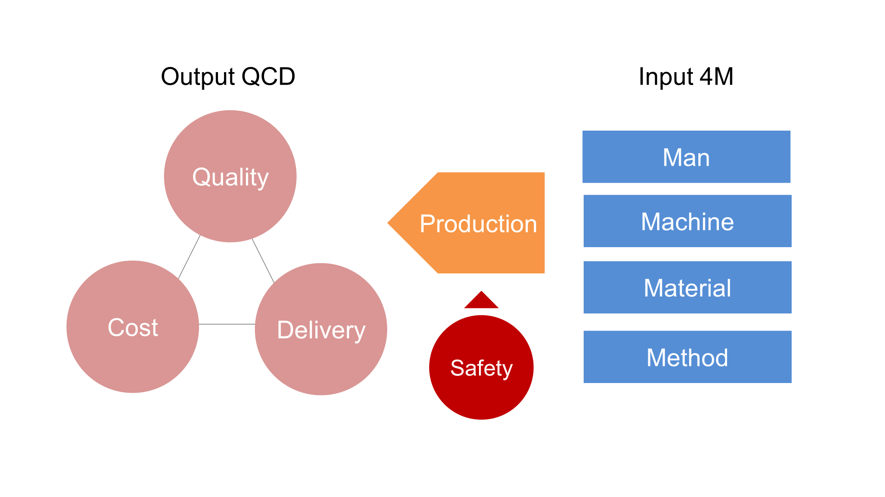
Figure 2: Input and output of production activities (Trend Micro)
OT system operations emphasize equipment maintenance service. This aims to prevent equipment from failing, to extend the service life, and to reduce downtime, thereby securing safety and availability. Measures against failures that have already occurred are referred to as breakdown maintenance, whereas measures against failures that have yet to occur are referred to as preventive maintenance. In some cases, preventive maintenance includes periodic or scheduled shutdowns; in other cases, it includes condition monitoring for on-demand shutdowns. With regard to the latter cases, predictive maintenance, which is an approach to implementing measures by using IoT to predict the future based on present conditions, is attracting attention.
Although the claims that OT systems cannot be stopped or changed may stand out from the perspective of IT security, OT systems must be stopped and changed based on their purposes; thus, it is important to work collaboratively with a practical understanding of operational approaches and methods.
Technology: OT systems that cannot be standardizedManufacturing factories have diverse OT systems for different products and purposes. Compared to IT systems, these are difficult to standardize among companies, factories, and systems. There are a wide range of general-purpose and industry-specific OSs and protocols used for industrial control devices, including MES, HMI, EWS, and PLC, and individual devices may each provide a single function and have limited computing resources.
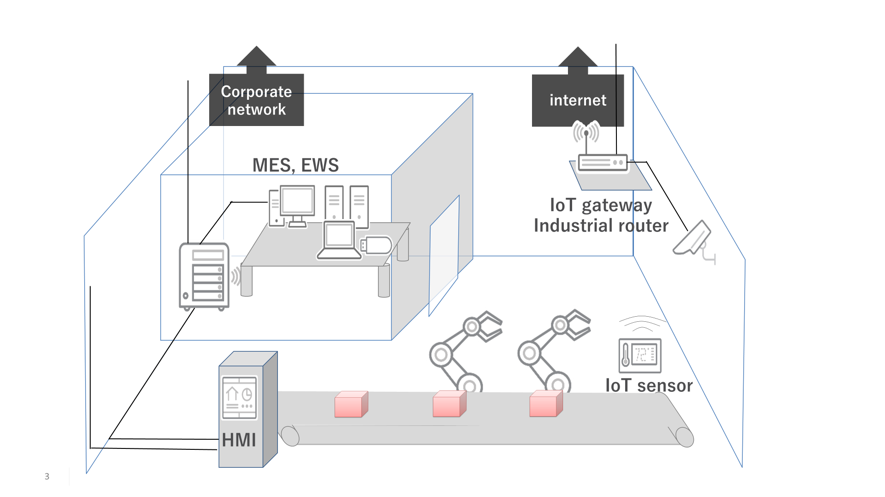
Figure 3: Image of a factory OT system (Trend Micro)
Speaking of the useful life of the machinery and equipment that these devices control, the useful life of PCs in IT is generally four to five years, and that of manufacturing equipment is generally ten to twenty years or more. For reference, the tax laws define the useful life of depreciable assets as follows: four years for PCs, ten years for automotive manufacturing equipment, and fifteen years for internal-combustion and gas-turbine power generators.*5 Note that these numbers often differ from the actual duration of service. One factor that makes it difficult to apply common IT security practices is that devices that run on common desktop OSs are operated along with machinery as a single system that is used over a period several times longer than that of the devices running on desktop OSs. In addition, it is often the case that there are many standalone terminals and devices not connected to the network even when implementation of a factory-wide LAN and integration into an information system network are partially underway. In many situations, diverse terminals, equipment, and environments exist alongside one another.
Thus, instead of promoting security measures uniformly, it is necessary to consider policies by comparing individual on-site tasks, systems, and operations with potential security risk scenarios.
*5 Tokyo Metropolitan Government Bureau of Taxation: "Ministerial Ordinance on the Useful Life of Depreciable Assets."
https://www.tax.metro.tokyo.lg.jp/shisan/info/hyo02.pdf
This second article considered what challenges lie in the way of promoting factory IT security with regard to people, processes, and technology. Since security measures for smart factories require collaboration among departments that play different roles, management must exercise leadership to promote interdepartmental understanding and consider security that is appropriate for on-site tasks and operations.
The third article, the last in this series, describes a specific approach to overcoming such challenges.

