Now, more than ever, the cloud is a relevant topic. Pandemic or not, businesses, schools, and other organizations have moved online and, consequently, many IT departments have had to deal with a move to the cloud. And even if this change had been on the roadmap of affected organizations, such a fast adoption of cloud technologies might have left organizations exposed to risks brought on by customers’ unfamiliarity with the specifics of its configurations.
Understanding the shared responsibility model — with pizzaTo understand how an unplanned move to the cloud could put organizations at risk, it’s important to first understand the shared responsibility model. The shared responsibility model has been adopted by major cloud business players to outline whether it’s the customer or the cloud service provider (CSP) that is responsible for an operational task in the cloud.
In the past, it was usual for potential customers to avoid using cloud services for fear of not knowing where their data would reside and whether it would be secure. More recently, however, many organizations believe that the cloud is completely secure and that they wouldn’t have any responsibility with regard to data security. Neither assumption is correct.
Cloud computing responsibility is akin to eating pizza: You, the pizza consumer, have multiple methods of receiving the pizza, as illustrated in Figure 1. If you don’t trust your “inner chef” or you’re just too busy, you’ll probably just go to a restaurant and eat pizza there, or simply have it delivered to your home. But if you prefer to have personalized pizza, made with your family recipe, you won’t mind going to the trouble of making and baking your own dough in order to satisfy your cravings.
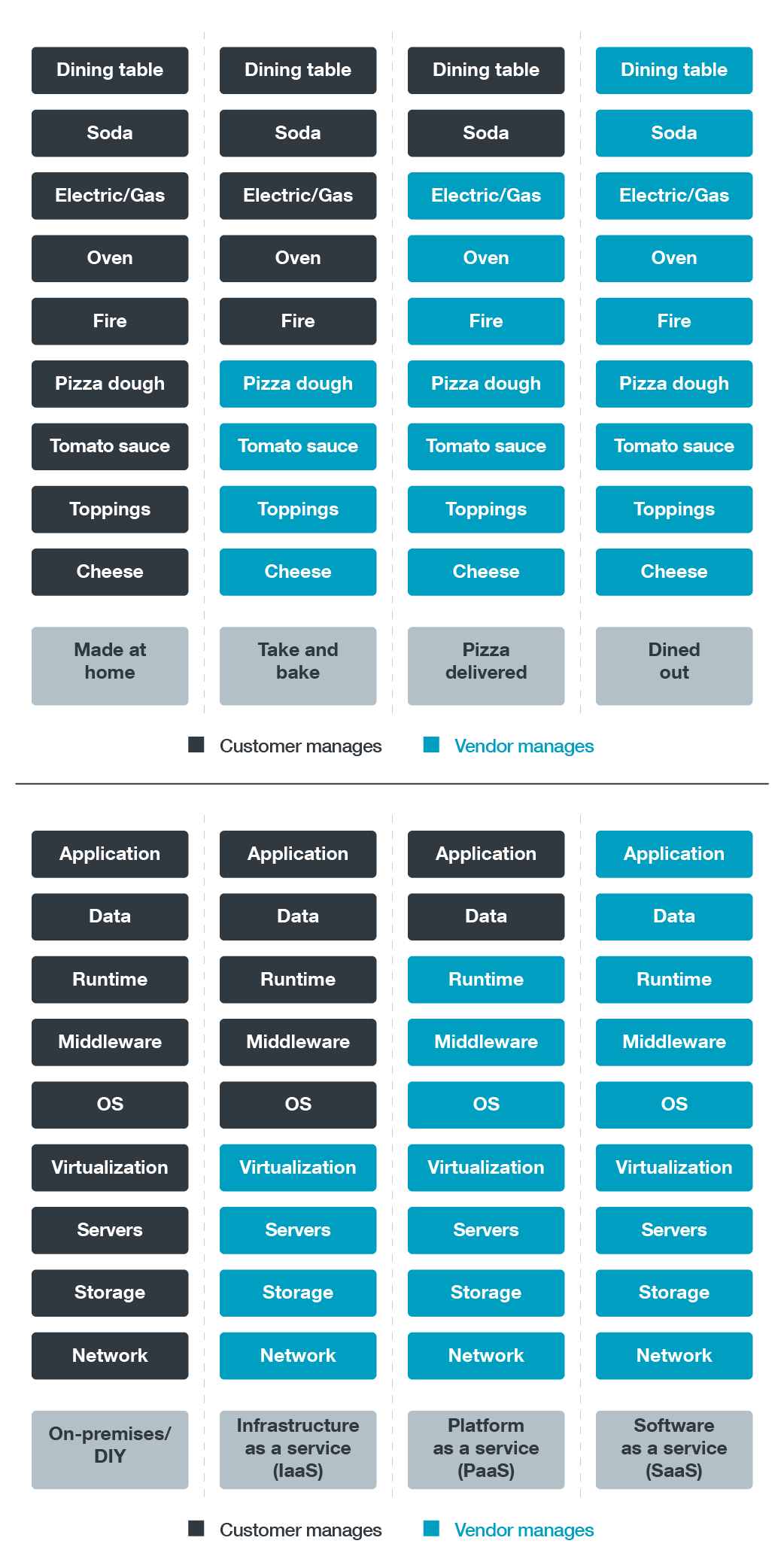
You, the cloud service customer, can have cloud computing in multiple ways as well. You can adopt off-the-shelf software-as-a-service (SaaS) technologies and depend on the default services offered (equivalent to eating pizza in a restaurant). You can also choose the platform-as-a-service (PaaS) or infrastructure-as-a-service (IaaS) model and build your own services on top of it (pizza delivery or take and bake). Or you can decide to have your services completely on-premises (homemade pizza).
CSPs such as Amazon Web Services (AWS) and other cloud providers provide documentation on how they define shared responsibility and how they cater to their customers’ needs using the model.
Understanding cloud architectures — with Lego
In addition to knowing that there are indeed responsibilities on the customer side, it’s important to know how to best build services on top of whatever flavor of cloud computing you choose to use. And this is where the topic of cloud architectures comes in.
To make it easier to understand, we now switch our analogy to Lego (which is the next best thing after pizza). If building in the cloud is like playing with Lego bricks, the frameworks of how to best build in the cloud — such as those provided by AWS and other providers — are akin to the Lego manuals that come with new boxes of bricks. You can build remarkable things following the best practices, but you can deliberately opt to not follow them and still end up creating something great. But if you do decide to build without a guide, you have to bear in mind that every brick you pick for your foundation will influence the integrity of the entire construction sooner or later, one way or another. Thus, knowing each piece and understanding its ripple effects are paramount — and the same is true for cloud architectures.
Cloud misconfigurationsWhen a customer is using one of their CSP’s services and believe that they have a certain configuration in place but in fact do not, a cloud misconfiguration arises. Customer misconfigurations, such as when a storage bucket that should have been made private and encrypted during its creation is actually public and in plain text, could result in data exposure, among other serious consequences.
The Trend Micro Cloud One™️ – Conformity solution runs over 490 million security posture checks against AWS accounts every day. This allows organizations to get an overview of commonly committed customer misconfigurations. Notably, for a considerable number of misconfigurations, the issue points to a lack of encryption, which is one of the security mechanisms recommended by AWS’ Well-Architected framework.
Amazon Elastic Block Store volume encryption
Amazon Elastic Block Store (EBS) is the block storage service of AWS. Most compliance frameworks and standards require organizations to implement full-disk encryption on their hard drives, and AWS promotes this practice as well. However, a significant percentage of the high-risk detections found by Trend Micro were related to Amazon EBS volumes that are not encrypted at rest.
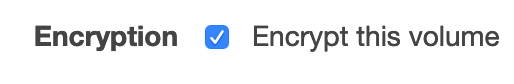
Customers might be operating on the assumption that AWS encrypts those volumes by default, but this isn’t the case. Fortunately, AWS makes it easy for customers to encrypt volumes: All they need to do is tick a checkbox, as shown in Figure 2. On top of that, AWS emphasizes that encrypted volumes have the same performance as unencrypted volumes.
Amazon Machine Image encryption
Amazon Machine Image (AMI) functions as an open virtual appliance that allows customers to spin multiple Amazon Elastic Compute Cloud (EC2) instances (“servers”) with the same operating system, configurations, and data. Having this data encrypted is also a good practice. However, a significant percentage of the high-risk detections found by Trend Micro involved unencrypted AMIs. Customers can enable AMI encryption with a simple tick of a checkbox, using an interface similar to that for enabling encryption for an Amazon EBS volume.
Amazon Simple Storage Service bucket encryption
Amazon Simple Storage Service (S3) is one of the most widely used services of AWS. As such, it is also one of the cloud storage services that are often mentioned when data leaks concerning big organizations make news. This may have resulted in the impression that Amazon S3 is an unsecure service. However, under the shared responsibility model, AWS provides the tools, but it’s the organization’s job to make sure buckets are properly configured.
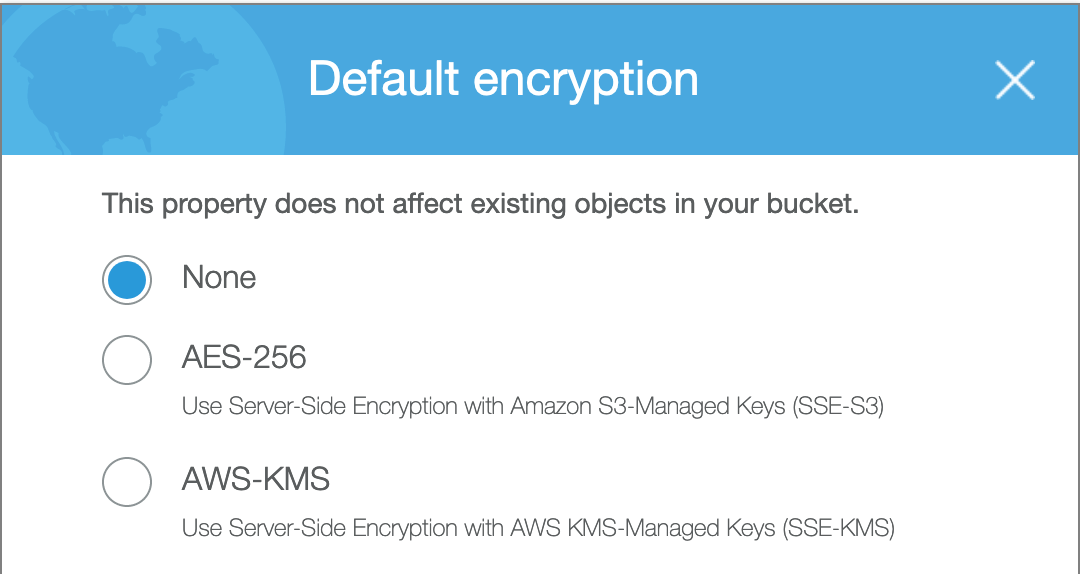
It’s important to note that while every newly created Amazon S3 bucket is private by default, it’s not encrypted. But encrypting an Amazon S3 bucket is as easy as selecting the option button corresponding to the preferred encryption method, as shown in Figure 3.
Amazon Simple Notification Service topic encryption
Amazon Simple Notification Service (SNS) is a core service for cloud-native design. This managed messaging service allows service-to-service communication, decoupling monolith applications and enabling the adoption of a microservices architecture. More often than not, sensitive data is transferred through this service. But if malicious actors gain access to the data in transit or at rest, they wouldn’t be able to make sense of it if encryption is enabled.
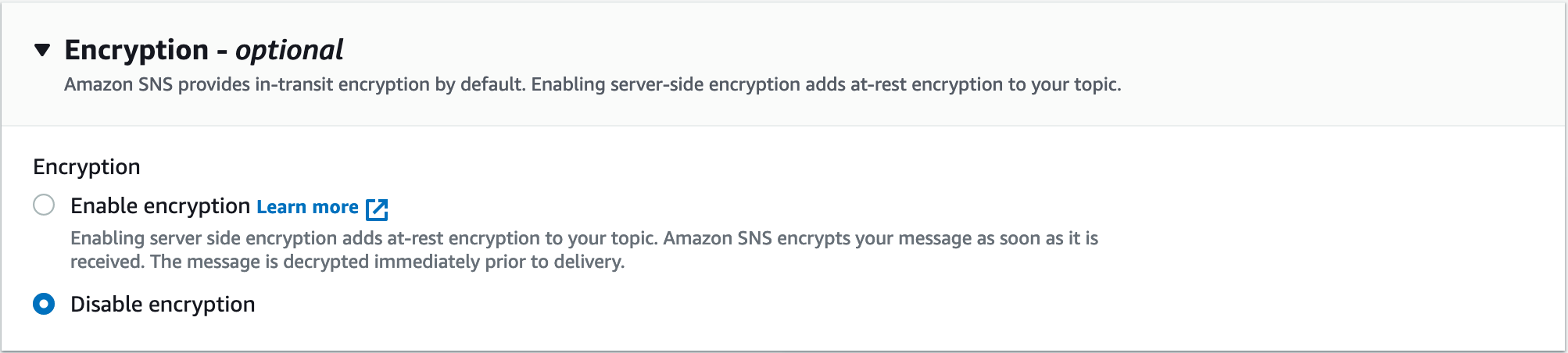
Amazon SNS provides in-transit encryption by default, but server-side at-rest encryption for a topic is optional and is disabled by default. However, enabling encryption for a topic can be easily done with a click of the corresponding option button, as shown in Figure 4.
Keeping the pie and the bricks in mindFor many organizations now, more than ever, migrating workloads to the cloud is full of promise and opportunity. However, organizations should understand what’s required of them by their slice of the shared responsibility pie, so to speak, that is adopted by their CSPs. Likewise, organizations should understand the best practices and the recommendations laid out in their CSPs’ frameworks in order to properly build on their foundational bricks. Doing both will help them avoid cloud misconfigurations and the consequences that come with these security gaps.
Trend Micro solutionsThe Trend Micro Cloud One™ – Conformity solution provides continuous security, compliance, and governance in a SaaS platform, designed to help organizations manage misconfigurations of cloud resources in a multi-cloud environment — helping cloud builders have the confidence that their cloud infrastructure is configured and compliant to grow and scale their business. Conformity is part of the Trend Micro Cloud One™ platform, a security services platform for organizations building in the cloud. It delivers flexible and scalable all-in-one security that helps DevOps engineers securely build and innovate as they migrate to and build in the cloud.

