While the pandemic pushed enterprises and users to adapt to different changes, we continued to monitor the cybersecurity threats that take advantage of the Covid-19 pandemic. Following the recent developments with regard to the Covid-19 vaccine, we noticed cybercriminals’ growing interest in the inoculation process, from alarming the public with misinformation to riding on the trend of using the vaccines for malicious activities online. Toward the end of 2020, cybercriminals began targeting companies and consumers by using developments in vaccine awareness, production, and distribution as a lure.
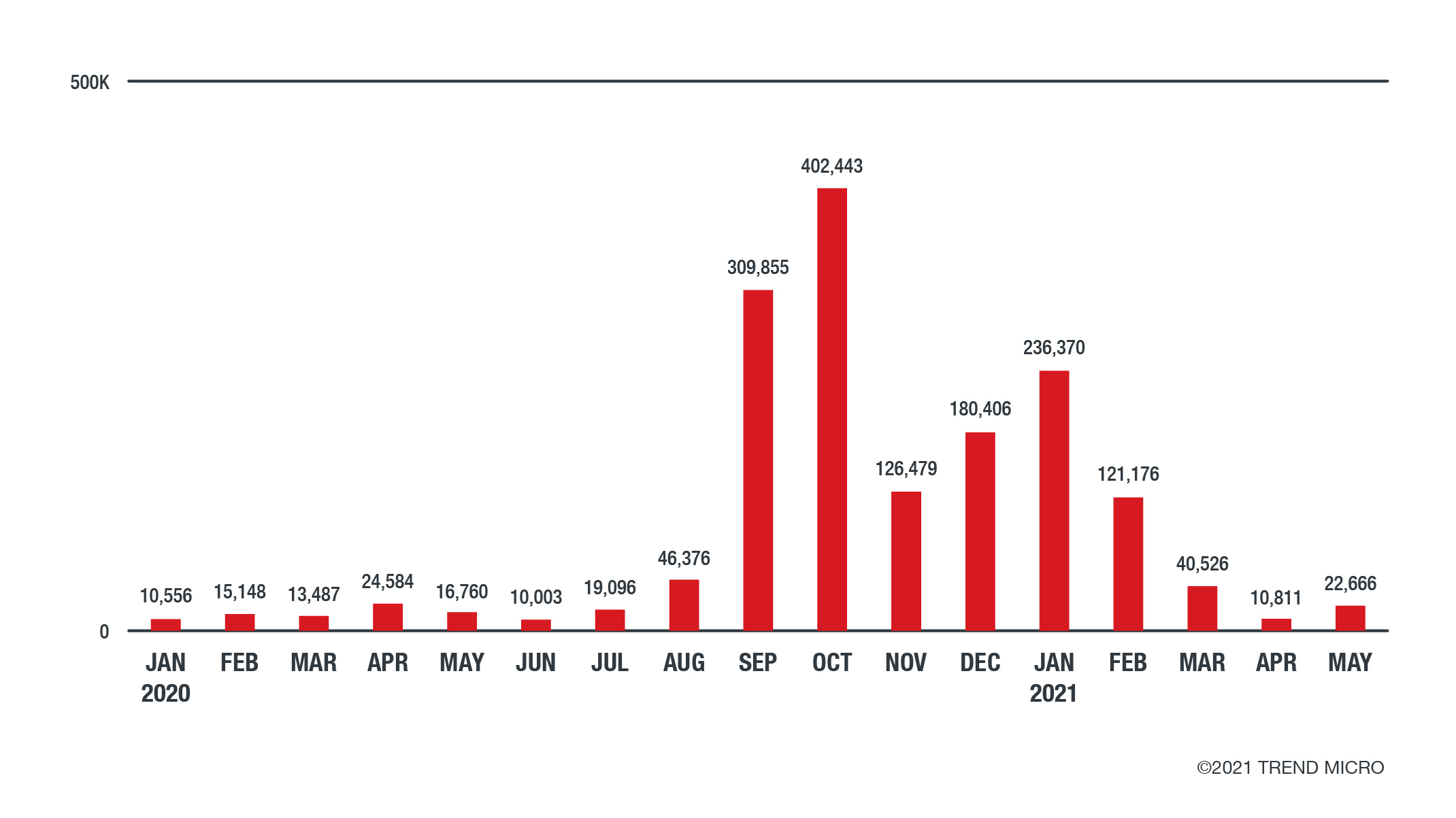
Our sensors followed the routines surrounding this theme and found detected attempts significantly increasing in the third quarter of the previous year and then reaching a peak in the last quarter of 2020. These activities include but were not limited to phishing, scams, backdoors, fake apps, and malware (such as ransomware) along with their variants for mobile, to name a few. Aside from reusing previous techniques for baiting users with information on the vaccine, it is possible that cybercriminals anticipated the general public’s growing interest in any news about the final phases of vaccine testing, as well as news about any ongoing plans for distribution.
Techniques, targets, and routines
Following our data, we found some new and dated social engineering techniques accompanying different malware deployment routines, scams, and attacks following the theme of vaccination distribution worldwide. We discuss some of their techniques and targets in the following sections.
Targeting the cold chain
The cold chain refers to the continuous logistics and management of services ensuring that temperature-controlled products are produced, stored, transported, and distributed within refrigerated environments to maintain their integrity and quality. Especially in the vaccine cold chain, each component requires personnel with specific training in handling, storing, and transporting these goods, as overseen and managed by trained professionals and guided by management procedures, specialised protocols, and legal mandates.
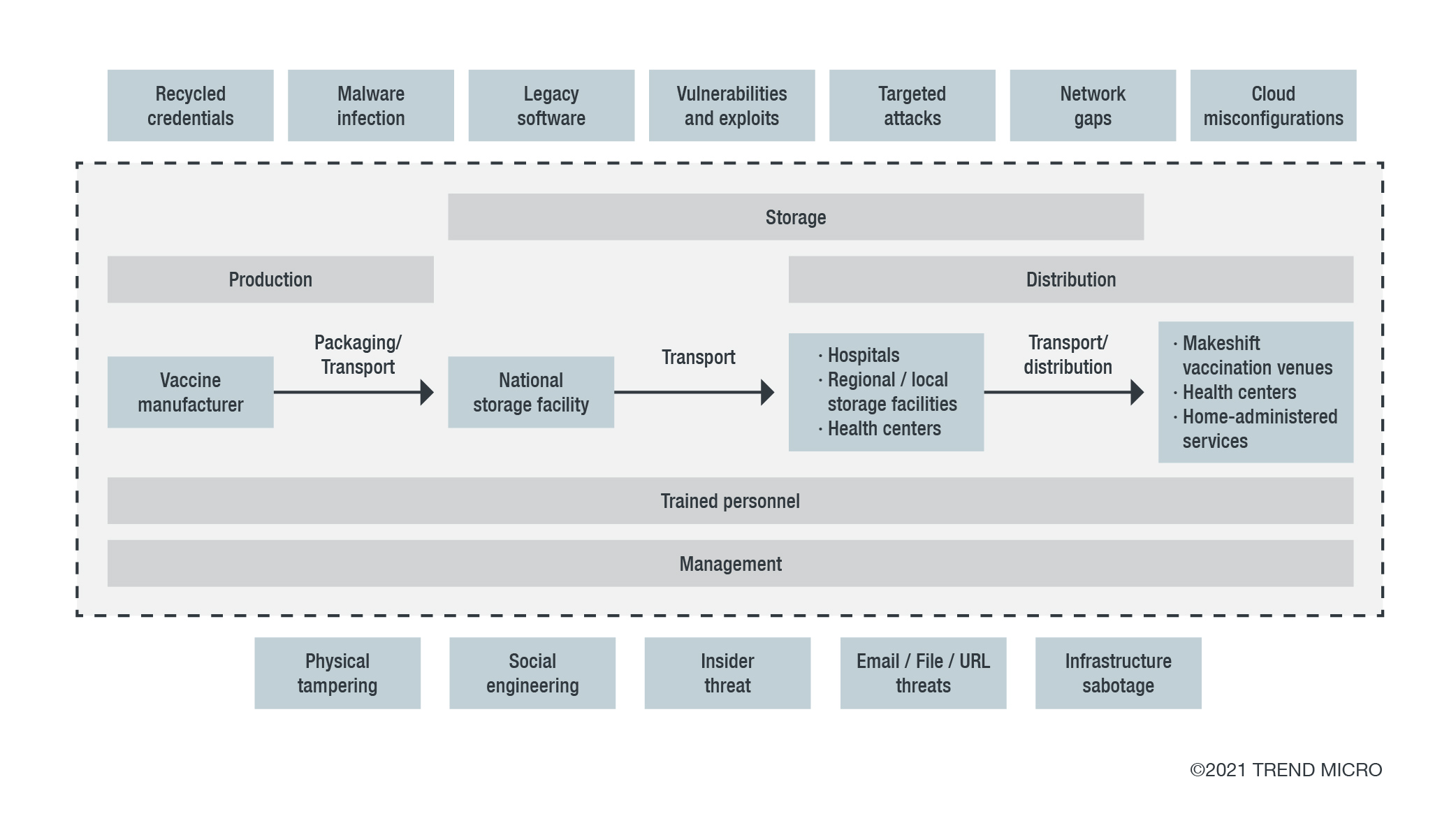
Considering the importance of this supply chain, we noticed the gradual increase of phishing schemes targeting major players who are involved in the vaccine cold chain, such as manufacturers and logistics companies, as well as their organisational customers. We tracked these malicious files, emails, and pages as stealing sensitive information. Primary target companies were in the telecommunications, banking, retail, government, and finance sectors, who were selected likely because of their heavy involvement in the vaccination processes.
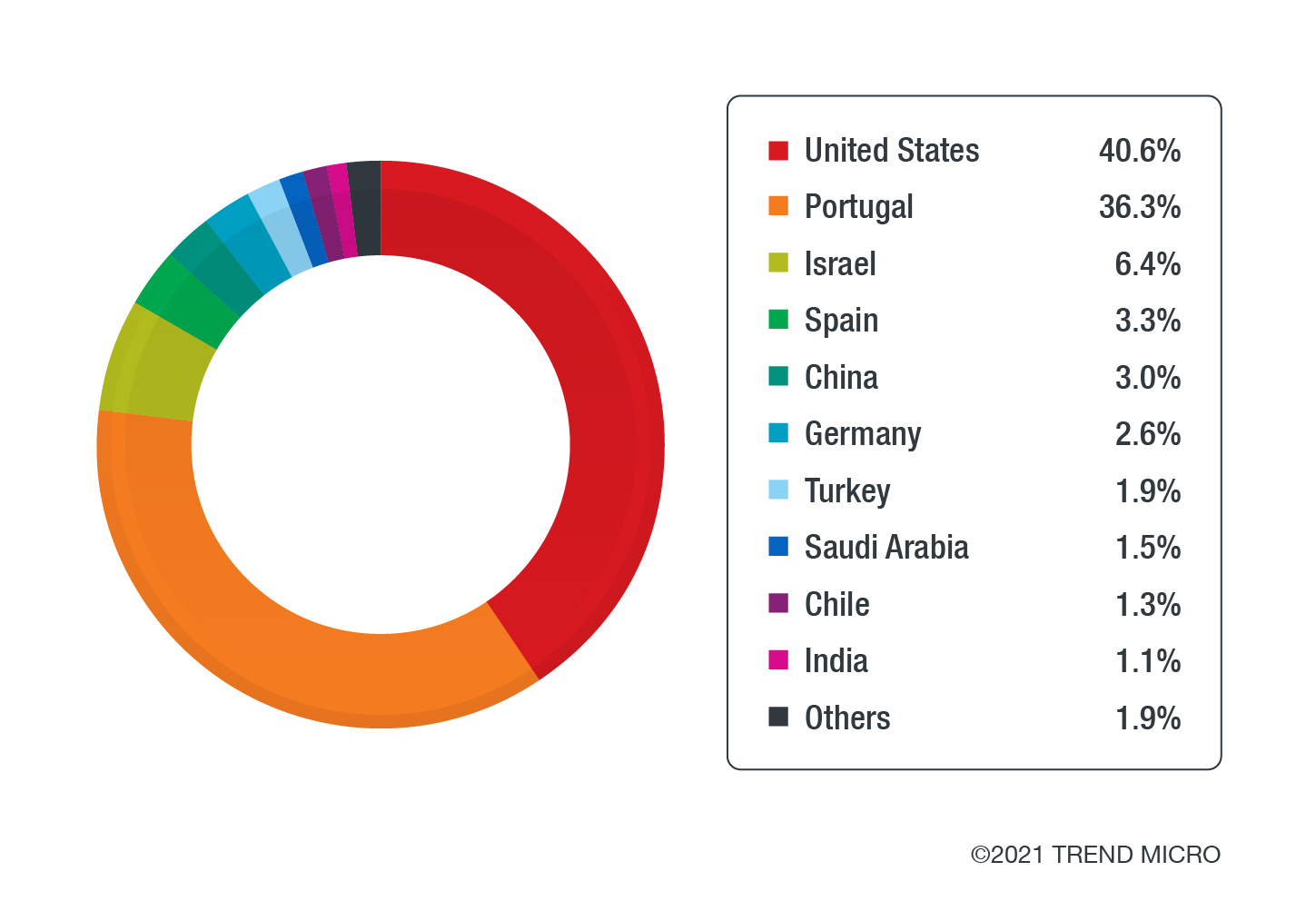
Malware operators have also been using the cold chain to attack partners down the supply line, target other countries or companies interested in purchasing in bulk, or even target users who might be looking for jobs. Despite the global takedown of the group responsible for Emotet, our sensors continue to observe a significant number of detections from different countries that use Covid-19 vaccines, medical reports, or information updates, as email lures. This suggests the presence of previously Emotet-infected units that are yet to be cleaned completely, although we expect to see a gradual elimination of the threat as residual infections are dealt with. We also observed variants of Lokibot deployed from Bangladesh and the US embedded in spam samples that impersonate vaccine suppliers and offer updates on the vaccine and release schedules. Much like others’ reports, our sensors’ ransomware detections also include Vaggen ransomware predominantly traced from the US and Germany, while majority of cold chain phishing deployments were tracked back to servers from the Netherlands and Austria.
[Read: Modern ransomware’s double extortion tactics and how to protect enterprises against them]
Scams and malware abound
Scams also continued to proliferate, targeting individuals looking for more information on the vaccine, searching for ways to acquire it, or applying for jobs and aid. While authorities have taken down a number of fake websites impersonating non-government organisations (NGOs) and companies involved in vaccine distribution, we still found more websites phishing for visitors’ personal information.


Malicious actors have also used SMS to scam people into sending them their personal information using lures such as the distribution of vaccines and stimulus packages for the elderly, the unemployed, and even struggling businesses. For example, an SMS worm was tweeted spreading in India via text messages. As victims tapped on the link in the text, the worm used the victims’ contacts to propagate. A comment on a Twitter post that disclosed this scam cited that this could be one of the first mobile malware capable of supporting dual SIMs. Notably, the malware sends the malicious worm using the first operator that the code recognises.
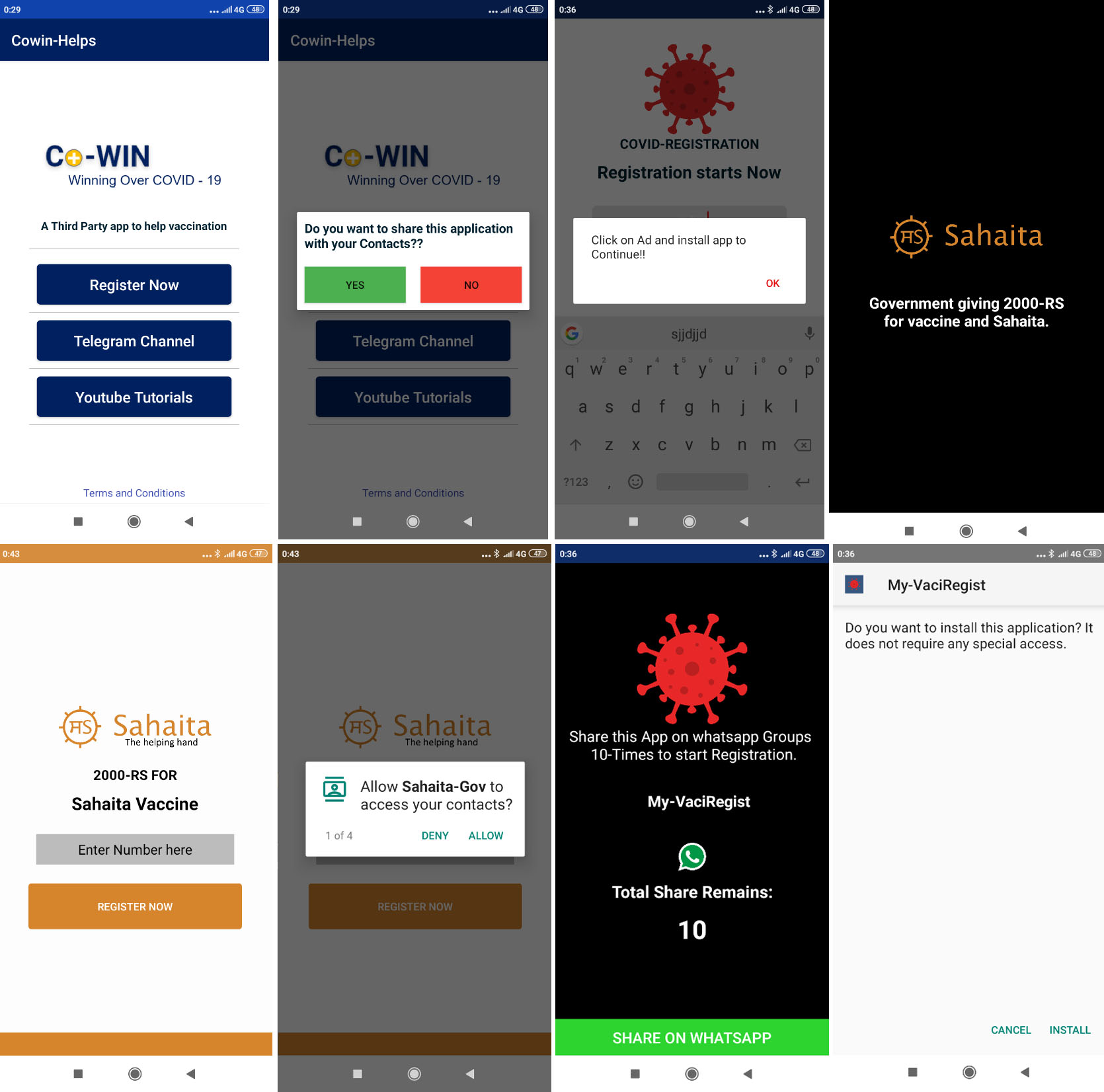
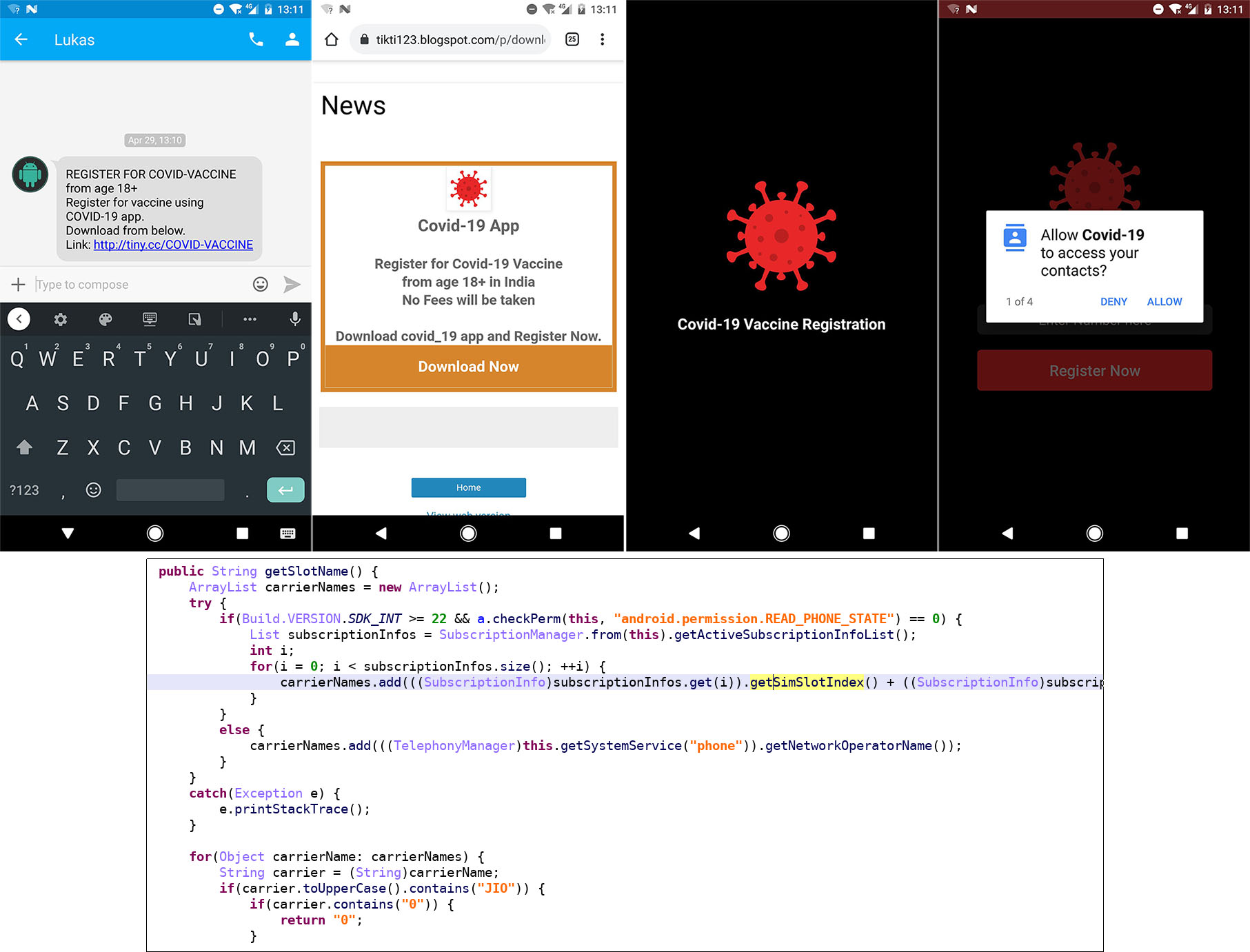
Among a number of malicious applications, we found that several of them were related to each other and simply had different lures, likely deployed to target users in India. We also found fake apps for Covid-19 testing registration. These were named “V-Alert COVID-19” (detected by Trend Micro as AndroidOS_Cerberus.HRXC) and “Covid-19 Test” (detected by Trend Micro as AndroidOS_Anubis.GCL). Both spread banking malware Anubis and Cerberus using similar command-and-control (C&C) servers as those malware that we previously tweeted about. Looking further into the deployment of Cerberus, we also found the same variants of Cerberus under the label “Google Update” targeting Japan and Germany.
Apps impersonating the government of India’s CoWIN page have also emerged with the aim to install the FakeApp malware (detected by Trend Micro as AndroidOS_FakeApp.NGPF) and steal sensitive information from vaccine registrants. In addition, our analysis of fake TikTok and “register laptop” apps also showed the apps spreading FakeApp beginning July 2020, similar to the latest fake CoWIN registry pages that started appearing toward the end of April 2021. Using the fake CoWIN platform, the cybercriminals behind FakeApp take advantage of both an ongoing initiative to get as many citizens vaccinated as possible and the increasing number of infections in India. Unfortunately, these malicious activities come along as the government tries to lessen barriers to accommodate more people for the vaccine.
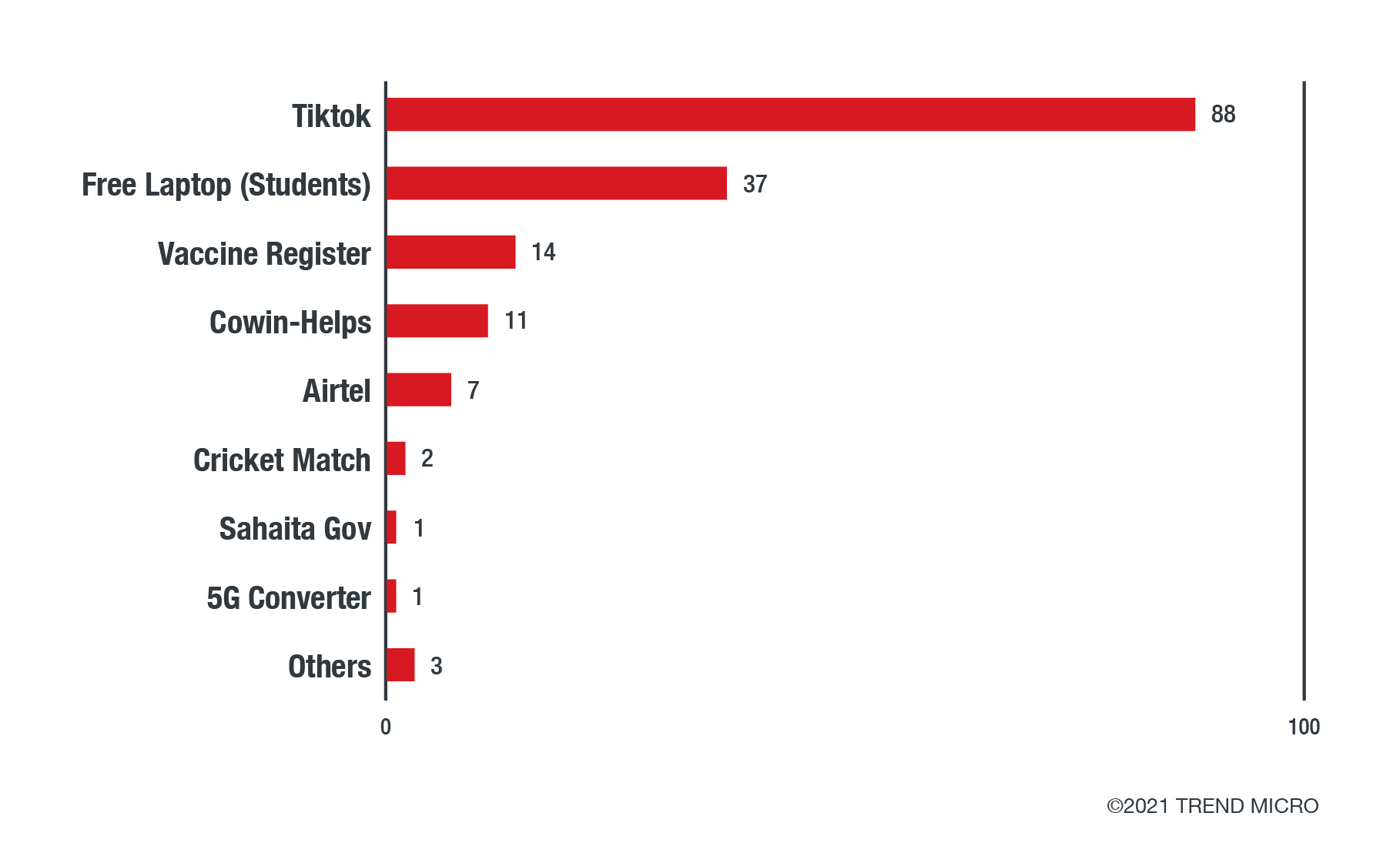
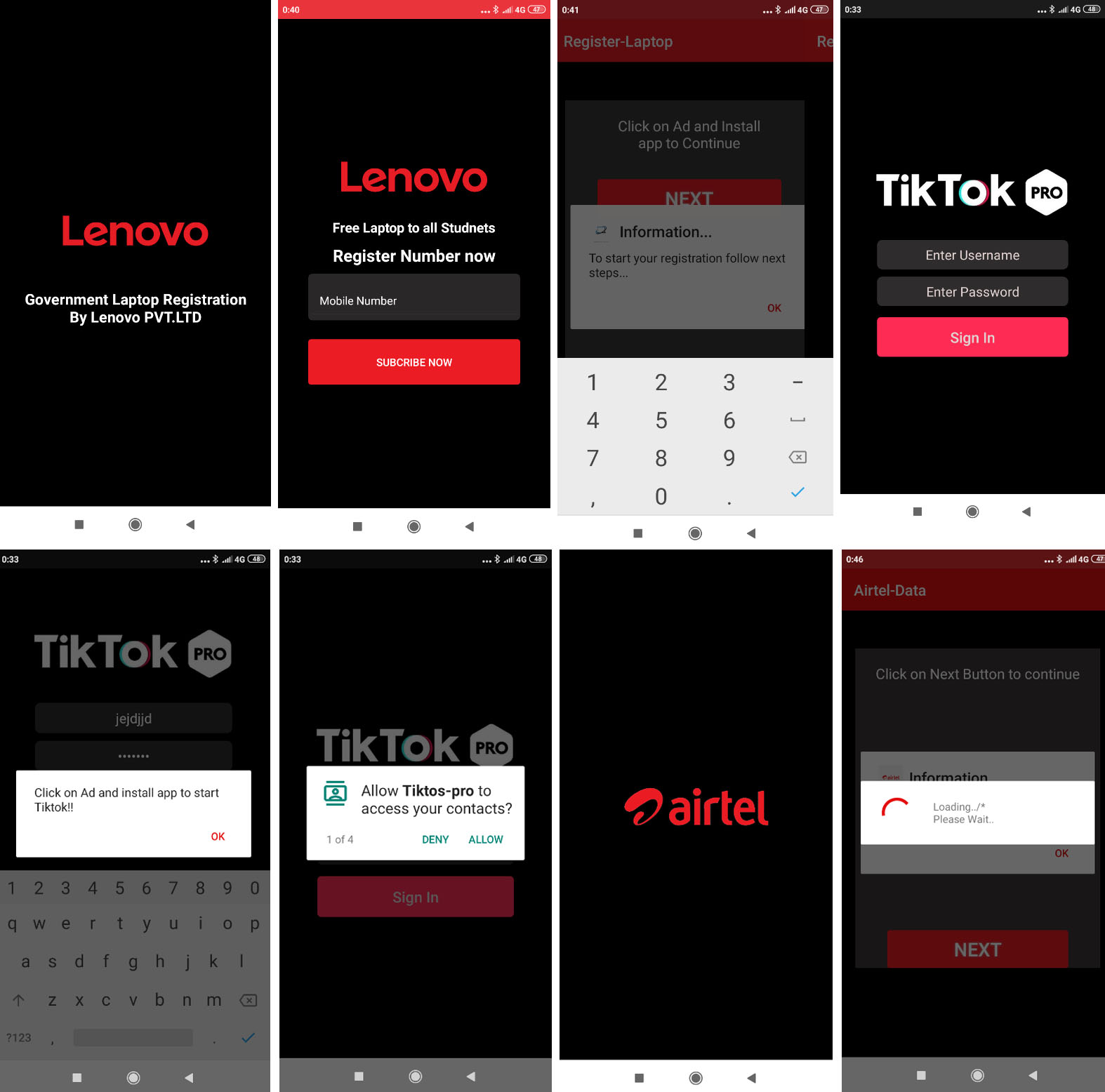
The illicit market and fake vaccination cards
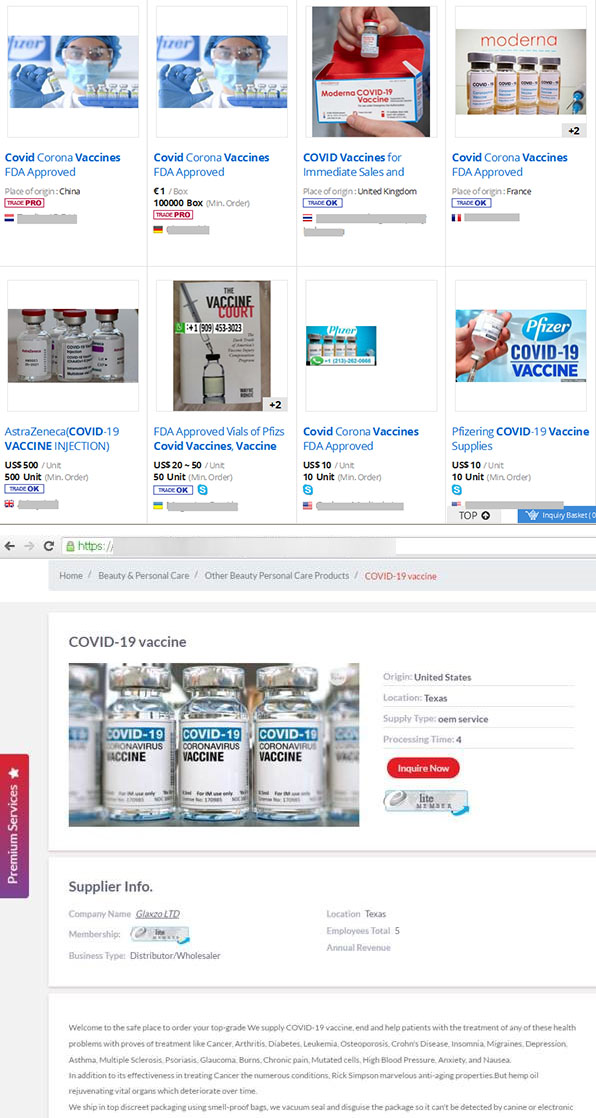
Since Q4 of 2020, authorities have been on a continuous drive to arrest groups and take down websites selling fake vaccines and cures. Additionally, while we’ve reported on the spread of pages selling fake vaccines on social media websites such as Facebook and messaging platforms like Telegram, more seller pages have been observed offering fake vaccines. Furthermore, investigators are also looking into legitimate e-commerce sites allegedly selling fake vaccines worldwide. Authorities have warned that these malicious entities might only be after users’ banking and credit card information and personal details for impersonation. It is also possible that these malicious entities are looking to sell unsuspecting victims something that might cause them more harm than good.
In the gradual return to normalcy, more people are expressing their varied interests in acquiring fake vaccination cards, likely with the aim of misrepresenting their vaccination status. Sellers have reportedly been looking to social media to create these fake cards. Authorities have been repeatedly asking legitimately vaccinated users not to post their cards on social media for two reasons: one is to prevent identity theft and another is to prevent scammers from gaining ideas on how to forge such cards. It’s important to emphasise that the forgery of these cards can be damaging and deadlier in the long run as, being counterfeit, their use for misrepresentation by individuals who have not been fully vaccinated would increase the likelihood of a prolonged pandemic and lengthier quarantine periods around the world.
Targeting users using events and aid
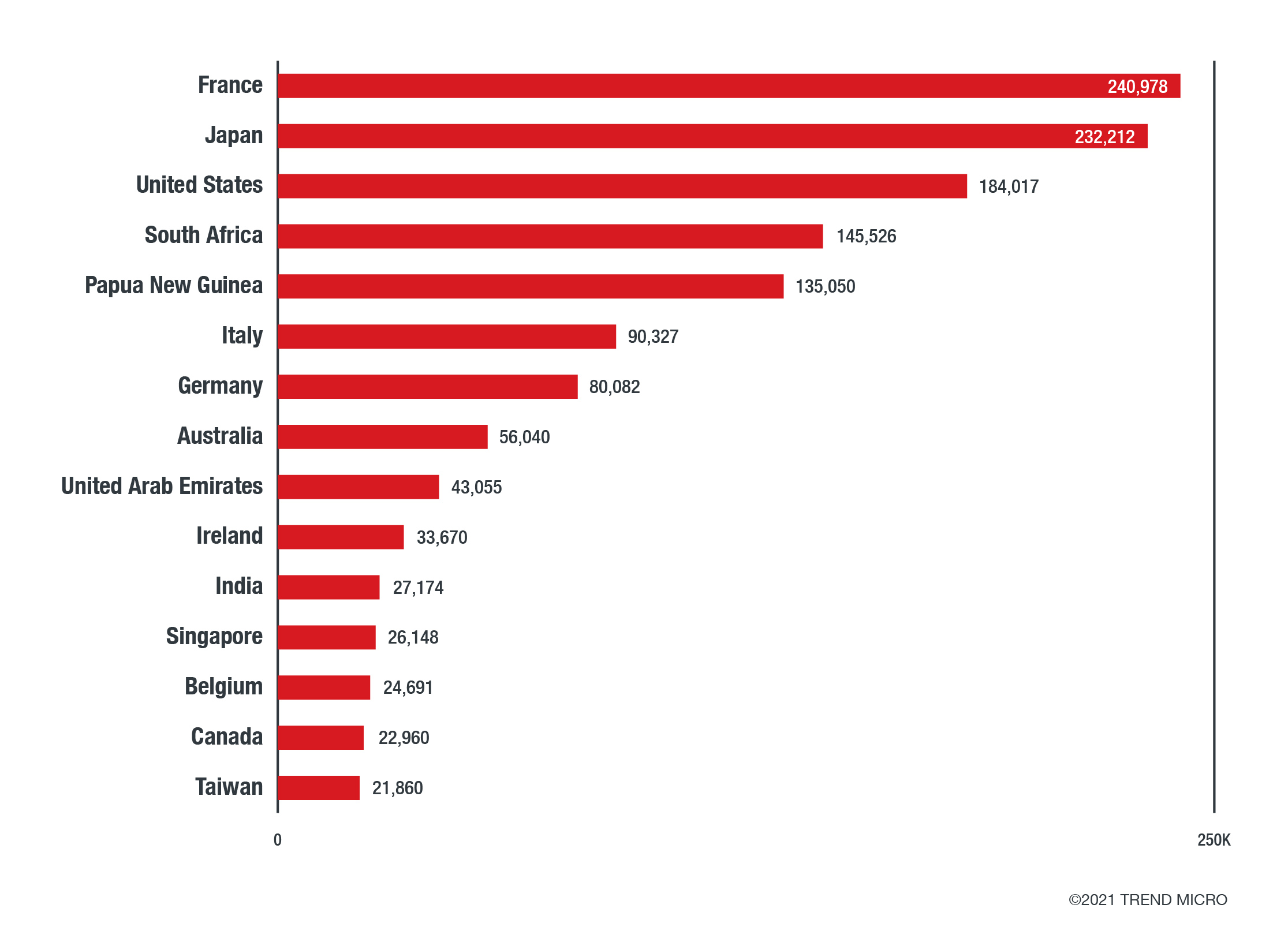
The surge in numbers for specific countries are also noticeable, which begs the question, why are these countries being targeted? The US, for example, remains a top target with regard to using the vaccine as a lure. In this case, it is likely that the US is a target given its part in the cold chain, as two of the major vaccine manufacturers have headquarters there.
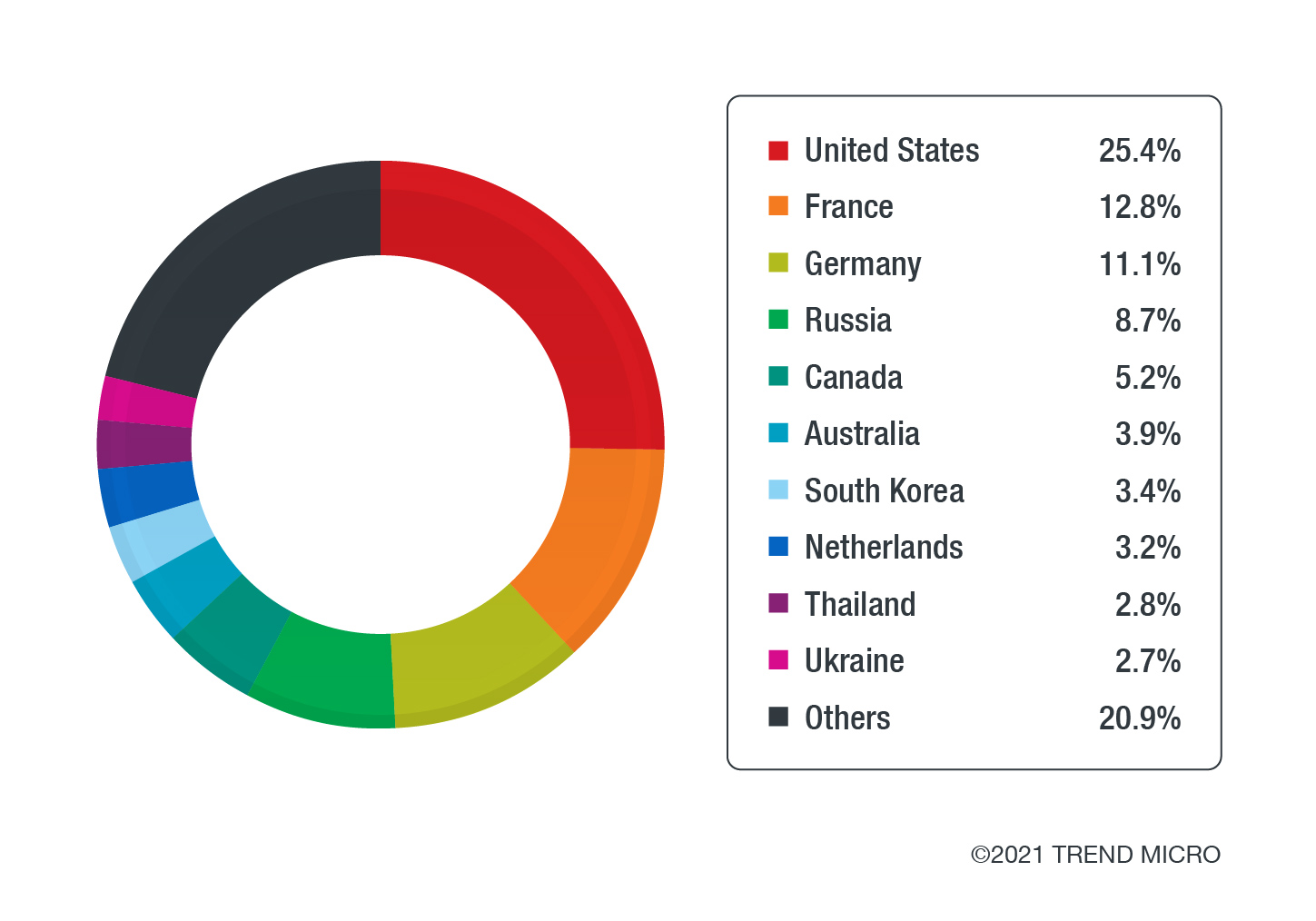
In Europe and Asia, France and Japan were the most heavily targeted with regard to malware threats and attacks. Looking at the number of attempts and targets, we think that highly anticipated events that are being advertised to proceed this year could be driving the focus of cybercriminals. Namely, these events are the French Open, Tour de France, Rugby World Cup, and the Olympics. Both countries have announced that spectators of and participants in these events are required to have proof of vaccination, such as vaccine passports. Moreover, as countries try to welcome tourists to push economies into recovery, both France and Japan have been the first to announce that all foreign visitors will be checked by new technologies that lessen contact with airport immigration officers, such as facial recognition and biometrics.
There is also a noticeable increase in targets located in Asia and Africa. It is possible that cybercriminals have moved to impersonate legitimate entities that request for or distribute aid as a result of new record surges in infections between Q1 and Q2 within these two regions. One other possible reason for the shift in their modi operandi is the fact that vaccines have yet to reach some of the countries with higher populations in these two continents.
[Read: Know the symptoms: Protect your devices while working from home]
Conclusion
Since the number of malicious routines decreased during the first quarter of the year, this could imply that cybercriminals are waiting for the next development or more news about the pandemic that they can take advantage of for abuse. In the meantime, we continue monitoring these routines and techniques, as given the ongoing vaccinations worldwide, these schemes are unlikely to subside anytime soon. Cybercriminals’ attention and targets, after all, could simply shift to other countries and events. Moreover, given the Covid-19 mutations spreading in various parts of the world, cybercriminals will continue abusing this theme as a lure for more months to come.
As a result, countries that have yet to vaccinate their citizens will likely be the next targets for malicious activities following this theme. Malicious groups and cybercriminals will take advantage of these developing localised situations. They might also use any further developments to spread more false information on available “cures” and medications online.
Documentations and technologies related to the pandemic will also be a likely target. As more people look forward to travelling for business and leisure, sales and services for falsified documents will likely be rampant in the online and offline underground market, while technologies that check the health and vaccination records of people will be targets for attacks online.
Indeed, cybercriminals will continue abusing people’s need and desire for more information, especially pieces of information that suggest a “return to normalcy” in countries where infection rates are already at a decline. It is therefore likely that misinformation and fake news will still run rampant post-vaccination, including false information that could appeal to individuals who are not yet inoculated or choose not to be.
How to protect yourself from Covid-19 scams and routines
Cybercriminal groups will continue finding the most effective techniques that they can use to infect and attack systems, as well as to target unwitting individuals for profit at others’ expense. Here are some of the best practices to mitigate risks and protect yourself from these threats and scams:
- Download apps, software, and/or media only from official platforms or websites. Applications or software from unofficial platforms might have embedded malicious components in them, or might impersonate other popular apps as a lure. They might also have functions that are unrelated to their stated purposes.
- Avoid selecting embedded links in emails and text messages that prompt urgency or are from unknown senders. These links could be phishing and/or SMShing URLs that were embedded in order to gain access to devices, steal sensitive or financial information, or spread malware. These might also lead to malicious websites that intentionally infect devices for subsequent stealthy communication.
- Avoid selecting and spreading fake news, ads, or unverified information, especially on social media. Fake news headlines are structured to be clickbait: They are alarmist to capture the interest of readers and to evoke strong emotions for manipulation. These pages might redirect you to malicious websites that steal information or spread malware. Before sharing, search for other reliable and known media agencies who publish the same content to verify the accuracy of information.
Trend Micro solutions
Trend Micro continues to monitor all attacks and malicious routines related to Covid-19 that can compromise your businesses and devices. Multilayered protection is also recommended for protecting all fronts and preventing users from accessing malicious domains that could deliver malware. Trend Micro endpoint solutions such as the Smart Protection Suites and Worry-Free™ Business Security detect and block malware as well as the malicious domains they use.
As an added layer of defence, Trend Micro™ Email Security thwarts spam and other email attacks. The protection it provides is constantly updated, protecting the system from both old and new attacks. Trend Micro™ InterScan™ Messaging Security provides comprehensive protection that stops inbound threats and secures outbound data, as well as blocks spam and other email threats.
Trend Micro Phish Insight can help empower employees and users to enhance security awareness and information in recognising threats against the organisation and themselves. These simulations on the latest threats and techniques can help increase cyber awareness and change behaviours using real-world phishing campaign samples for customised training on an easy-to-use platform. Trend Micro Check can also help detect misinformation, scams, and similar online threats. A free multiplatform tool powered by artificial intelligence (AI), Trend Micro Check offers scam link detection, email security review, fact-checking of text, audio, and visuals to identify misinformation and news outlet credibility verification. Since its launch, it has identified more than two million scams and three million instances of misinformation.
Users can also benefit from security solutions that can thwart stealthy adware, such as the Trend Micro™ Mobile Security solution, which blocks malicious apps. End users can also benefit from its multilayered security capabilities that secure the device owner’s data and privacy and safeguards them from ransomware, fraudulent websites, and identity theft.
For organisations, the Trend Micro™ Mobile Security for Enterprise suite provides device, compliance, and application management, data protection, and configuration provisioning. It also protects devices from attacks that exploit vulnerabilities, prevents unauthorised access to apps, and detects and blocks malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and ML technologies to protect users from malware, zero-day and known exploits, privacy leaks, and application vulnerability.
[Read: Looking ahead: The post-pandemic security landscape]
Indicators of Compromise (IOCs)
You can access the link here for the full list of IOCs.

