Cyber Threats
Using Writing Style Checks to Stop CEO Impersonations
If an employees receives an email that looks like it’s from the CEO asking for sensitive data, could they spot it as a fake based on how it is written? Writing Style DNA technology is now available to prevent Business Email Compromise Attacks (BEC).
If one of your employees receives an email that looks like it’s from the CEO asking to send sensitive data or to make a wire transfer, could that employee spot it as a fake based on how it is written? He or she may be so concerned with pleasing the CEO that they may urgently respond without a second thought. What if artificial intelligence could recognise that the writing style of suspect email doesn’t match the style of your CEO to spot fraud? It can.
Writing Style DNA technology is now available to prevent Business Email Compromise Attacks (BEC) which according to the FBI has cost organisations $12.5 billion with some companies losing as much as $56 million dollars.
Unique Writing Style
Some of us write long sentences with a variety of words while others are more direct with short words and small paragraphs. If we look at the email of three Enron executives (based on a dataset of 500,000 emails released publicly during the Federal Energy Regulatory Commission’s investigation) we can see the differences in how they write. Looking at the emails from Jeffrey Skilling, Sally Beck, and David Delainey, we can compare writing style elements such as sentence length, word length, repeated words, paragraph length, pronoun usage, and adjective usage.

Graph of writing style elements of 3 Enron executives
We see that the three executives style vary across the 16 elements in the chart above. As humans, we can perhaps come up with 50 or maybe 100 different writing style elements to measure. A computer AI though can see many more differences between users writing. The AI powering Writing Style DNA can exam an email for 7000 writing style elements in less than a quarter of a second. If we know what an executive’s writing style looks like, then the AI can compare the expected style to the writing in an email suspected of impersonating that executive.
Training an AI model of a User’s Writing Style
Based on previous Business Email Compromise attacks, we see that the CEO and Director are most likely to be impersonated and can define these individuals as “high-profile users” within the admin console for Trend Micro Cloud App Security or ScanMail for Exchange.

Titles of impersonated senders in 1H 2018 Business Email Compromise attempts
To create a well-defined model of a high-profile user’s writing style, the AI examines 300-500 previously sent emails. Executive’s email is highly sensitive and to protect privacy, the AI extracts metadata describing the writing style but not the actual text.
Your executives style of writing isn’t static but rather evolves over time just like this infographic shows JK Rowling’s style changing over the course of writing the Harry Potter books. As such, the AI model for a high-profile user can be regularly updated at a select interval.
Process Flow
When an external email from a name similar to a high-profile user, the writing style of the email content is examined after other anti-fraud checks. The volume of BEC attacks is small to start with (compared to other types of phishing) and other AI based technologies catch most attacks which leaves only a small number of the stealthiest attacks for writing style examination. For these attacks, if the style doesn’t match, the recipient is warned not to act on the email unless he/she verifies the sender’s identity using a phone number or email from the company directory. Optionally, the impersonated executive can also be warned of the fraud attempt on their behalf.
Internal and Beta Results
Internally, Trend Micro has been testing this since January of 2018. Writing style models are in place for our executive team and some other high-profile users. During this time, Writing Style DNA detected 15 additional BEC attacks which were attempting to impersonate our CEO, Eva Chen. This works out to an average of 1 additional attack detected every other week. To date, there have been no false positives.
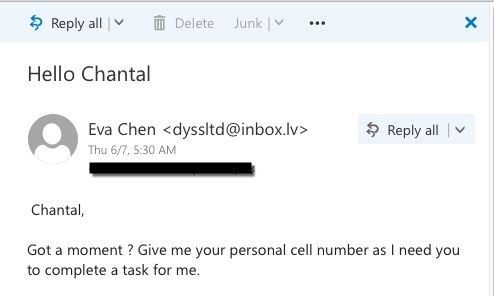
Sample BEC attempt detected with Writing Style DNA
We have also had more than 60 beta customers try the technology over the past few months. Many initially found their executives were using their personal email accounts occasionally to email others at the organisation and these personal accounts can be whitelisted by the admin. Writing Style DNA detected 15 additional BEC attacks at 7 organisations.
Available now and included with your license
Writing Style DNA is now available with Cloud App Security for Office 365 and ScanMail for Microsoft Exchange at no additional charge.
The Cloud App Security service has been updated already to include this functionality and ScanMail customers can upgrade to SMEX 12.5 SP1 to start using this technology. ScanMail customers can learn more about upgrading to v12.5 SP1 at this webinar September 6.

