Updated as of March 18, 2019, 10:48PM PDT to update Figure 1 (number of incidents/cases where unique samples of Powload were analyzed).
Powload’s staying power in the threat landscape shows how far it has come. In fact, the uptick of macro malware in the first half of 2018 was due to Powload, which was distributed via spam emails. Powload was also one of the most pervasive threats in the North American region in 2018, using various techniques to deliver payloads such as the information-stealing Emotet, Bebloh, and Ursnif. Our Powload detections and the number of related cases/incidents and unique samples we analyzed in 2018 also markedly increased compared to 2017. Powload’s evolving techniques, on the other hand, show how far it’ll go. While its use of spam email as a distribution method could be its constant, it has employed different ways of delivering payloads, from bypassing mitigations like a document’s preview mode to using fileless techniques and hijacking email accounts.
 Figure 1. Detections for Powload based on data from Trend Micro™ Smart Protection Network™ (left) and number of incidents/cases where unique samples of Powload were analyzed (right; the numbers are based on the top threats analyzed)
Figure 1. Detections for Powload based on data from Trend Micro™ Smart Protection Network™ (left) and number of incidents/cases where unique samples of Powload were analyzed (right; the numbers are based on the top threats analyzed)
In some of the recent Powload-related incidents we saw, we noticed significant changes to some of the attachments in the spam emails: the use of steganography and targeting of specific countries. Figure 2 shows the difference. For example, the samples we analyzed in early 2018 had more straightforward infection chains. These updates added another stage to the execution of malicious routines as a way to evade detection.
The Powload variants that use these techniques drop and execute the Ursnif and Bebloh data stealers. We did not see any notable differences in the payloads’ routines. The distribution tactics also resemble a spam campaign we uncovered last year, which delivered the same information stealers but distributed via the Cutwail botnet.


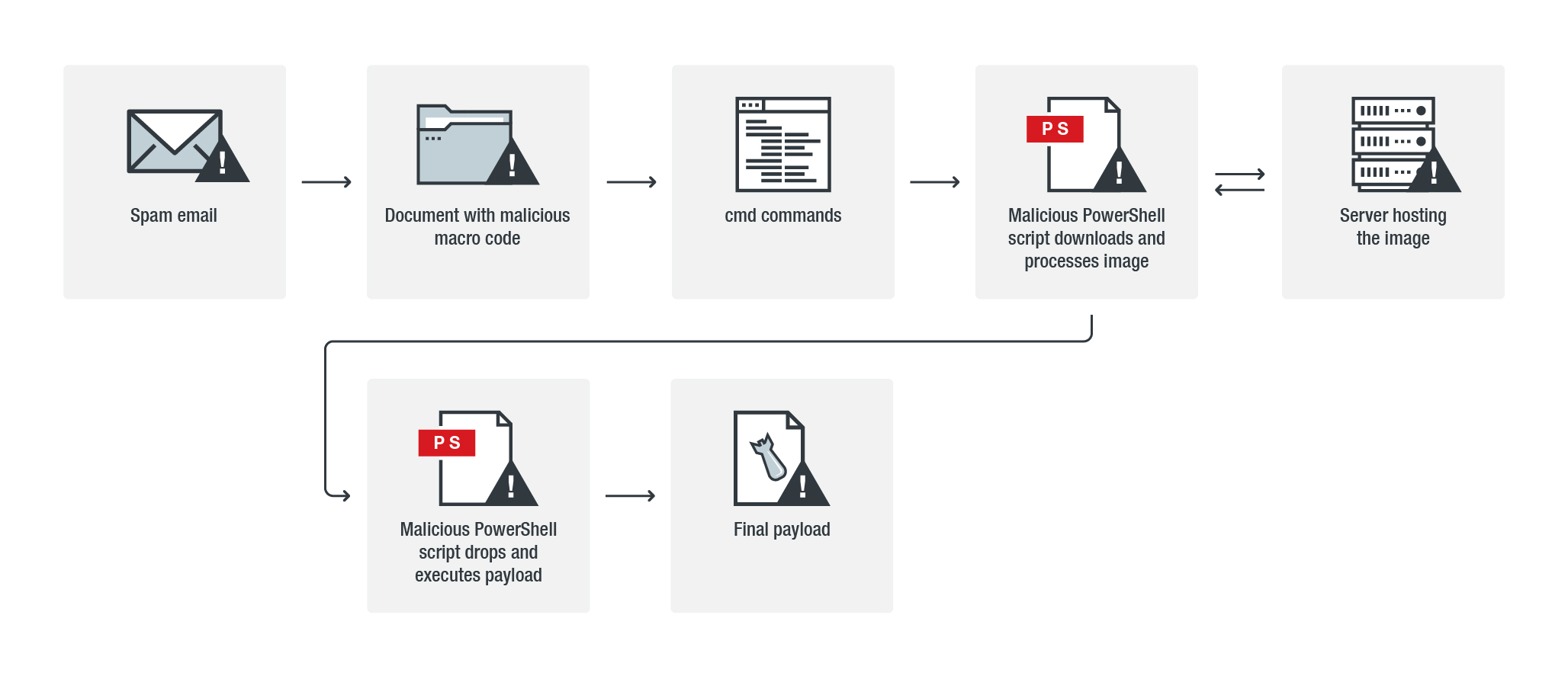 Figure 2. Powload’s typical execution flows (top, center) and its attack chain using steganography (bottom)
Figure 2. Powload’s typical execution flows (top, center) and its attack chain using steganography (bottom)
How Powload uses steganography
The use of steganography — hiding code within an image — isn’t new. Hacking groups, for instance, are known to use steganography for retrieving their backdoors. Exploit kits employ it to hide their malvertising traffic, while other threats use it to hide their command-and-control (C&C) communication.
In Powload’s case, it uses steganography to retrieve an image containing malicious code. Based on the code-extraction routines of the Powload variants we analyzed, they abuse a publicly available script (Invoke-PSImage) to create the images containing their malicious codes.
The attachments in the spam emails have malicious macro code embedded inside the document that executes a PowerShell script, which downloads an image hosted online. It then processes the downloaded image to acquire the code hidden inside the image.
Figure 3. Snapshot of code showing a PowerShell script downloading an image and acquiring the hidden code using GetPixel (highlighted)
Figure 4. Screenshot of an image containing the malicious code
 Figure 5. Examples of spam email sent to recipients, using purchase order/invoice- (left) and reference material/“signboard”-related social engineering lures to urge users to download and click the attachments
Figure 5. Examples of spam email sent to recipients, using purchase order/invoice- (left) and reference material/“signboard”-related social engineering lures to urge users to download and click the attachments
Targeted campaigns?
Another trend we observed in Powload-embedded spam emails is the specificity in their targets. By singling out a country — using region-specific brands and vocabulary — to send their spam to, the email content and its attachment can be more convincing to unwitting recipients.
Another drawback is that automated and traditional sandbox solutions whose regional settings aren’t set to the spam email’s targeted country won’t be able to properly analyze the malware.
The methods for region detection vary from the samples we analyzed. Some use the PowerShell command “Get-Culture” to obtain the computer’s regional settings. Others get the value of the xlCountrySetting property (which returns information about the current regional settings) in Excel to determine the affected machine’s location. Some samples, on the other hand, determine the location by accessing a URL (hxxp://ipinfo.io/country), a free tool that returns an IP address’ country.
Figure 6. Snapshot of PowerShell script that checks whether the machine’s regional settings is set to Japan (highlighted)
Figure 7. Snapshot showing how the macro code will only execute its main routine if the xlCountrySetting is equal to 81 (Japan) or 82 (Korea)
 Figure 8. PowerShell command that connects to ipinfo[.]io
Figure 8. PowerShell command that connects to ipinfo[.]io
Addressing Powload’s persistence
Powload’s persistence as one of 2018's most prevalent threats highlights the effectiveness of its latest techniques — despite being relatively old. We expect Powload’s developers to continue to add more malicious routines to their malware, and given how it serves as a catalyst for other threats, we also expect Powload to deliver payloads other than information stealers. Users must always practice cybersecurity hygiene and be more prudent against dubious, unsolicited emails, while businesses should enforce proactive countermeasures to secure their online perimeters.
The following Trend Micro solutions protect users and businesses by blocking the malicious documents and scripts and preventing access to attacker-specified domains: Trend Micro™ Security, Smart Protection Suites, and Worry-Free™ Business Security.
Indicators of Compromise (IoCs)
Related hashes (SHA-256):
- 23e85ee19a2f46f4f462e72995b6a91616ea2f315908c1566c36cd0afc3aa200 — detected by Trend Micro as Trojan.X97M.DLOADR.JHKK
- 667e30b20e0986c7def59f66d871a579a32f150b61f64aefd431864b33dced12 — Trojan.X97M.DLOADR.JHKH
- 75a46329eed0e0a2948f4c5e35a3fda1e0f3a23d059ba019de33c654ff0e84fa — Trojan.X97M.POWLOAD.NSFGAIDM
- 81e10dc5acf7b150591d147c1101fed72d90648f1ec40a20798836d07258b804 — Trojan.X97M.POWLOAD.NSFGAIBQ






