Overview
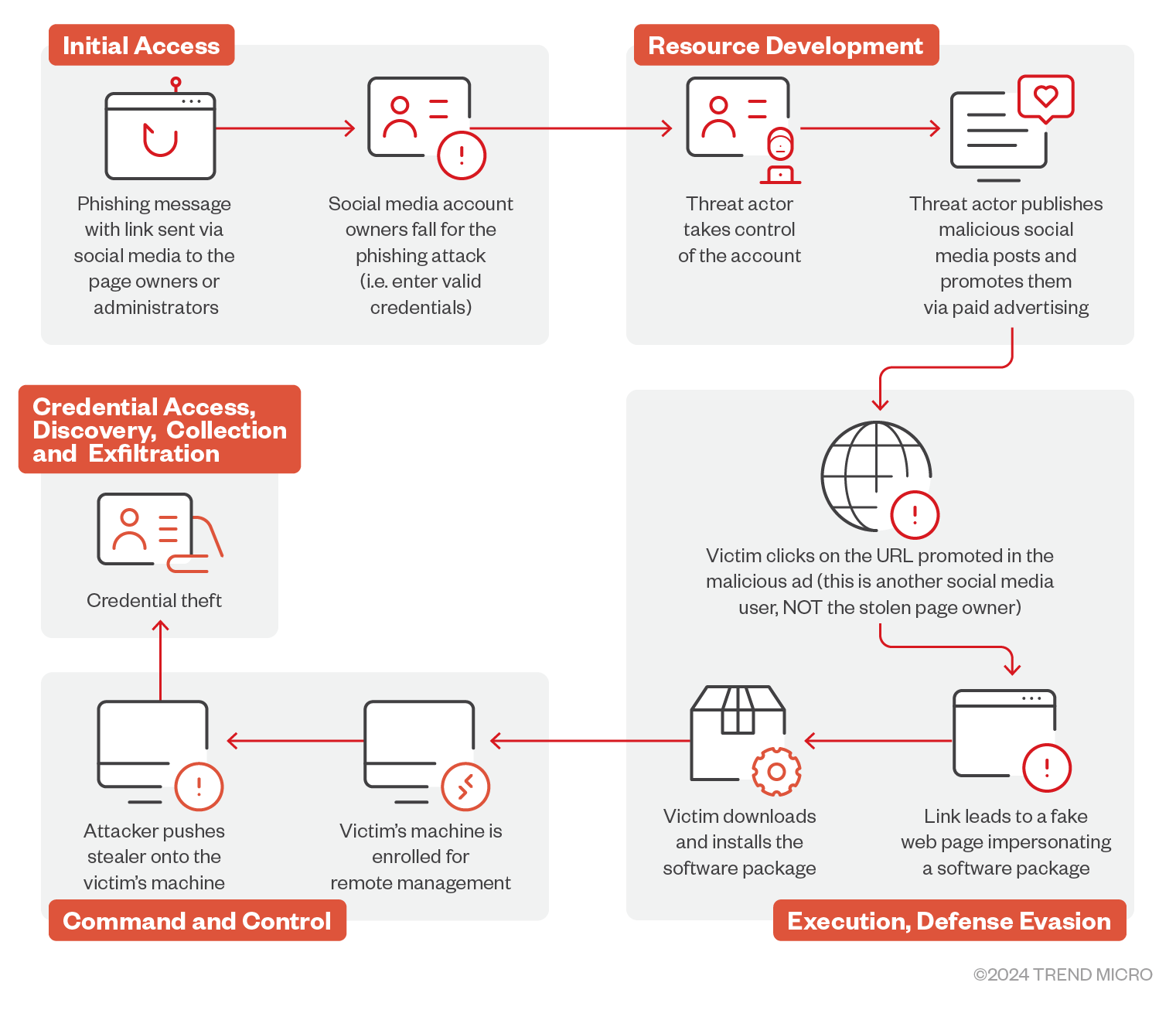
- In this blog entry, we examine how threat actors hijack social media pages, rename them to resemble a legitimate AI photo editor, then post malicious links to fake websites, which are boosted via paid ads.
- The attackers use spam messages with phishing links to steal admin credentials. These links lead to fake account protection pages that trick users into providing their login information.
- Once the attacker gains control of the page, ads are posted promoting the AI photo editor, leading victims to download an endpoint management utility disguised as the photo editor.
- The ITarian software is used to execute additional payloads like Lumma Stealer, which exfiltrates sensitive data such as cryptocurrency wallet files, browser data, and password manager databases.
- Cybercriminals are exploiting the popularity of AI tools by using them as lures for malicious activities, which includes phishing scams, deepfakes, and automated attacks.
We discovered a malvertising campaign involving a threat actor that steals social media pages (typically related to photography), changing their names to make them seem connected to popular AI photo editors. The threat actor then creates malicious posts with links to fake websites made to resemble the actual website of the legitimate photo editor. To increase traffic, the perpetrator then boosts the malicious posts via paid ads.
The abuse of paid Facebook promotions for malicious activities is not new. In 2023, we published two blog posts on profile stealers, which were implemented either as browser extensions or standalone applications.
When victims open the malicious websites, they are tricked into visiting the download section and installing the package, which is — as expected — not a photo editor, but a legitimate endpoint management utility using a malicious configuration. After successful installation, this utility allows for remote device management. The attacker can then abuse the tool’s features to download and execute credential stealers, which ultimately leads to the exfiltration of sensitive data and credentials.
Technical analysis
To gain control of the target social media page, the threat actor will first send messages to the administrator containing phishing links, which can either be direct links or personalized link pages (linkup.top, bio.link, s.id, and linkbio.co, among others). Sometimes these links abuse Facebook’s open redirect URL, >, to seem more legitimate.
The sender of the message will typically use an empty profile with randomly generated usernames followed by a few digits.
If operators of the targeted Facebook pages click on the personalized links, they are presented with a screen similar to those shown below.
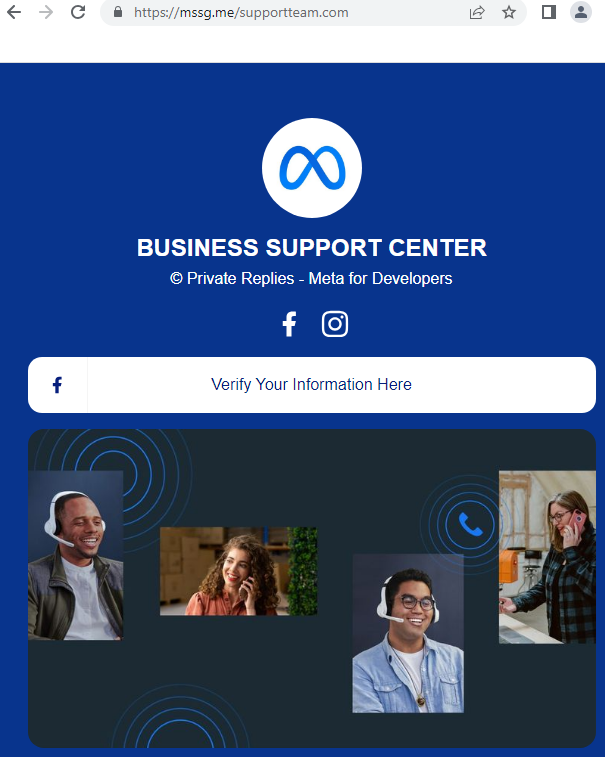
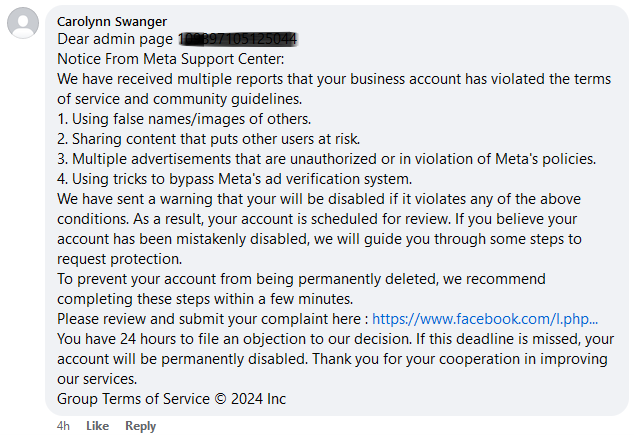
Clicking on the “Verify Your Information Here” links lead to a fake account protection page, which in several subsequent steps, asks users for the information necessary to log in and take over their account, such as their phone number, email address, birthday, and password.
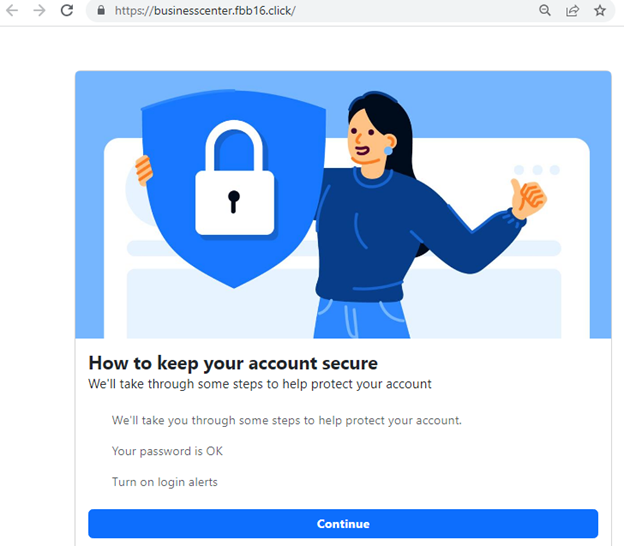
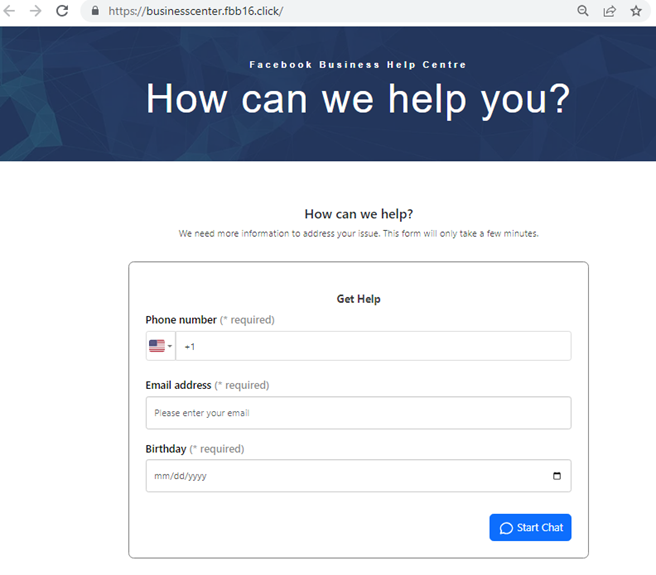
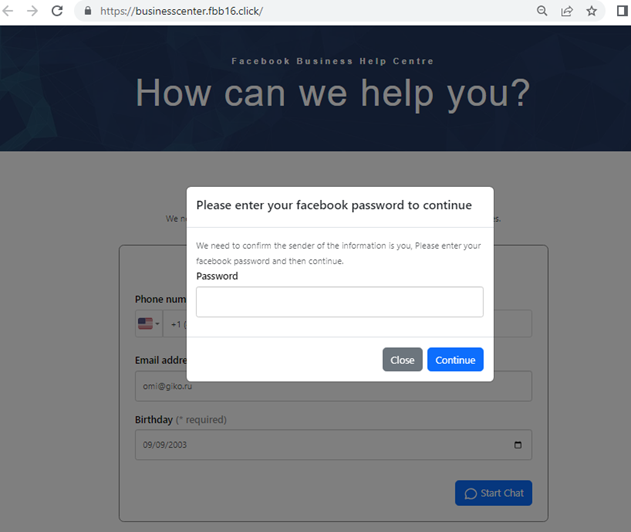
After the target provides all the needed information, the attacker then steals their profile and starts posting malicious ads.
After taking control of the Facebook pages, the threat actor will start posting advertisements that links to the fake AI photo editor domain. In this case, the name of the legitimate photo editor being abused is Evoto.
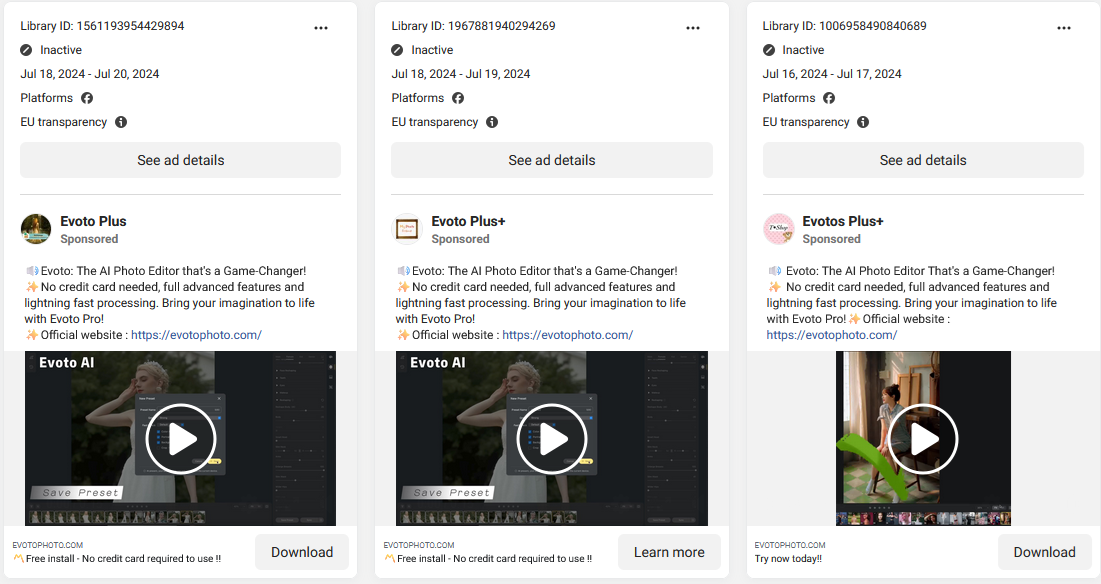
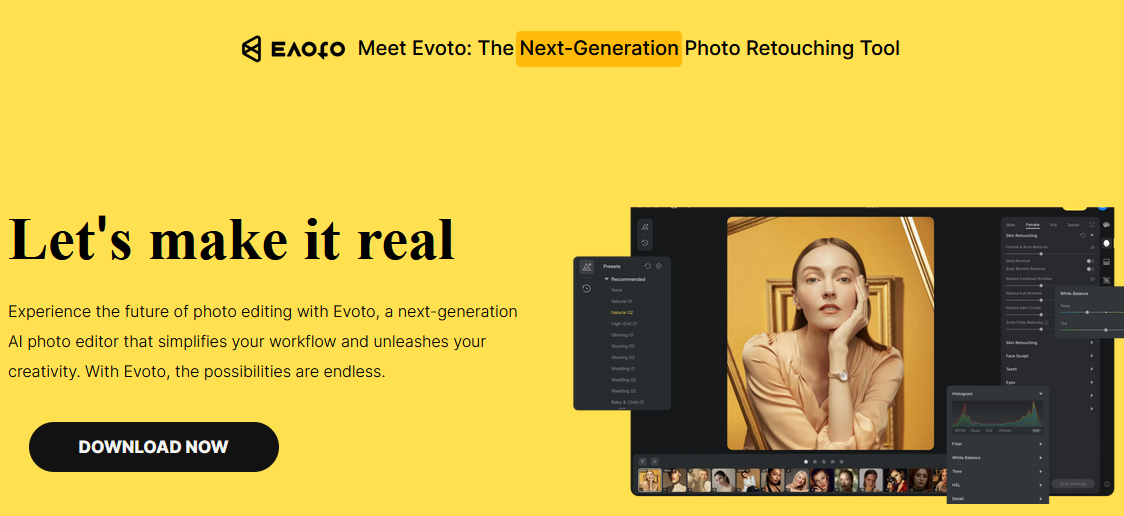
The fake photo editor web page looks very similar to the original one, which helps in tricking the victim into thinking that they are downloading a photo editor. The reality however, is that they are actually downloading and installing an endpoint management software.
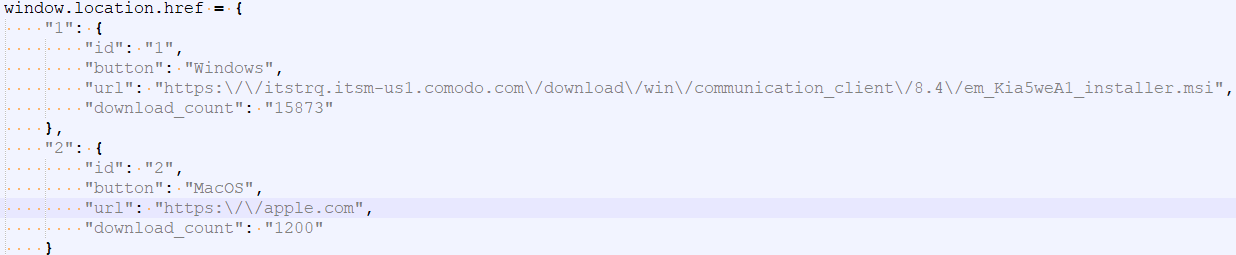
Interestingly enough, the JavaScript responsible for downloading the package contains statistics in a variable called download_count. At the time of writing this report, there are approximately 16,000 hits for Windows binary and 1,200 hits for the MacOS version (which only redirects to apple.com and does not return any binary).
When victims execute the installation MSI package (disguised as a photo editor installer), their devices are immediately enrolled for management, giving the threat actor full access to remotely control the device.
As shown in the link from Figure 9, the downloaded file is an ITarian installer. ITarian is a free endpoint management software. Threat actor signs up for a free account, registers a subdomain (seen in the subdomain itstrq in Figures 9 and 10), and creates an installation MSI package. This installation package needs to be distributed to victims for installation.
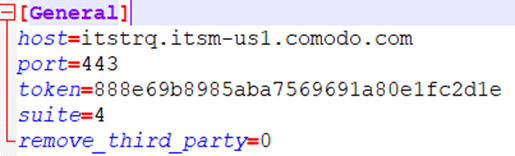
Interestingly, the MSI package itself does not contain any malicious components. It does not even contain any file with a malicious configuration. Instead, we get the installer file name format: em_<token>_installer.msi. When querying https://mdmsupport.comodo.com/enroll/resolve/token/<token>, we receive the malicious enrollment configuration.
When the device is successfully enrolled for remote management, a few scheduled tasks are executed. The scheduled tasks are of the Python_Procedure type and contain
1) A simple downloader in Python to download and execute an additional payload.
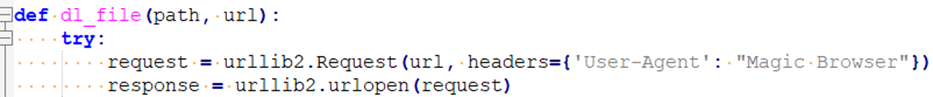
Of note is the user agent value “Magic Browser”. The additional payload is typically Lumma Stealer and its binary is usually encrypted with PackLab Crypter.
2) A simple script to exclude disk C: from being scanned with Microsoft Defender.

The script modifies Windows Defender settings by calling Add-MpPreference -ExclusionPath.
The final payload is Lumma Stealer, which has its initial C&C communication characterized by two consecutive POST requests to the /api URL path with the x-www-form-urlencoded content type. The first request content is act=life, followed by the second requests content, “act=recive_message&ver=<version>&lid=<id>&j=” (sic!), which returns a Base64 encoded stealer configuration.
The first 32 bytes of the debased buffer is a XOR key, while the remaining bytes are the encrypted configuration. The decrypted configuration is in JSON format and lists everything the stealer is supposed to steal.
Security Recommendations
The targeting of social media users for malicious activities highlights the importance of robust security measures to protect account credentials and prevent unauthorized access. This includes the following best practices:
- Users should enable multi-factor authentication (MFA) on all social media accounts to add an extra layer of protection against unauthorized access.
- Users should regularly update and use strong, unique passwords for social media accounts.
- Organizations should educate their employees on the dangers of phishing attacks and how to recognize suspicious messages and links.
- Users should always verify the legitimacy of links, especially those asking for personal information or login credentials.
- Both organizations and individual users should monitor their accounts for any unusual behavior, such as unexpected login attempts or changes to account information.
- Organizations should consider using security solutions that can detect abnormal account activities.
- Organizations should consider employing endpoint technologies such as Trend Vision One™ , which provides multilayered protection and behavior detection, helping block malicious tools before they can do any damage.
- For other types of AI tool abuse, specifically those involving deepfakes, userss can consider using Trend's Deepfake Inspector, which helps protect against scammers using AI face-swapping technology during live video calls. Users can activate the tool when joining video calls and can be alerted to the presence of AI-generated content or deepfake scams.
MITRE ATT&CK techniques
The following tactics and techniques are a subset of the MITRE ATT&CK list.