Malware
SocGholish’s Intrusion Techniques Facilitate Distribution of RansomHub Ransomware
Trend Research analyzed SocGholish’s MaaS framework and its role in deploying RansomHub ransomware through compromised websites, using highly obfuscated JavaScript loaders to evade detection and execute various malicious tasks.
Summary
- The complex intrusion set Water Scylla is composed of multiple stages that involves compromised websites, collaboration with threat actors operating malicious Keitaro TDS instances, SocGholish payload delivery, and post-compromise activity that leads to RansomHub. As of the start of 2025, SocGholish detections have been highest in the United States, with government organizations among the most affected.
- SocGholish is characterized by its obfuscated JavaScript loader, which uses various evasion techniques to bypass traditional detection methods, primarily propagating through compromised legitimate websites.
- By infecting legitimate websites with malicious scripts, threat actors redirect visitors to fake browser update notifications, convincing them to download and execute a malicious file.
- Water Scylla collaborates with threat actors operating rogue Keitaro Traffic Distribution System (TDS) instances to distribute SocGholish Payloads.
- The SocGholish loader can download and execute malicious payloads, exfiltrate sensitive data, and execute arbitrary commands, providing persistent access for further exploitation and payload deployment.
- Deploying extended detection and response solutions, hardening endpoints, enhancing logging and network monitoring, using web reputation services, securing CMS and web applications, and retiring or isolating end-of-life systems are essential to protecting enterprises from SocGholish intrusions and subsequent ransomware attacks on businesses.
First observed in 2018, Trend Research has been closely monitoring the activities of the SocGholish – also known as FakeUpdates – malware-as-a-service (MaaS) framework. This particular intrusion set is tracked by Trend Micro under the name Water Scylla, whose activities lead to RansomHub ransomware deployment.
SocGholish is characterised by its highly obfuscated JavaScript loader, which employs a range of evasion techniques that enable it to bypass traditional signature-based detection methods effectively.
The primary method of propagation for SocGholish involves the compromise of legitimate websites. Threat actors inject malicious scripts into these sites to hijack user traffic. When users visit these compromised sites, they are redirected to deceptive webpages that masquerade as legitimate browser update notifications. Through social engineering tactics, users are convinced to download a malicious ZIP file. This file contains a JavaScript file, which is the SocGholish loader.
This blog entry focuses on a cluster that deploys backdoor components to enable initial access for RansomHub ransomware-as-a-service (RaaS) affiliates. Ransomhub is a top ransomware player in terms of the number of organisations impacted by data breaches, just behind Akira in second place and CL0P in first, and SocGholish a key enabler of these attacks.
SocGholish’s key role in enabling initial access for ransomware warrants the attention of defenders to thwart attacks. The primary objective of SocGholish is to drop second-stage payloads, which include backdoor components. These backdoors provide threat actors with persistent access to infected systems, facilitating further exploitation and payload deployment.
SocGholish's loader is highly versatile and capable of executing arbitrary tasks as directed by its operators. It can:
- Download and execute malicious payloads: including backdoor components, and stealer routines.
- Exfiltrate sensitive information: It collects and sends data from infected systems back to its command-and-control (C&C) infrastructure.
Execute arbitrary commands: This allows threat actors to perform a wide range of malicious activities on the compromised system.
Since the start of the year, SocGholish detections have been highest in the US, followed by Japan, then Taiwan. Government entities top the list of most affected organizations, with those in the banking and consulting industries coming in second and third, respectively. The persistent and evasive nature of SocGholish highlights its critical role in the initial stages of ransomware attacks. This underscores the need for heightened awareness and robust cybersecurity measures to identify and mitigate such threats effectively.
Initial access and execution
The primary mechanism for SocGholish distribution involves several components.
- A compromised website injected with a malicious script. (T1608.004 - Drive-by Target)
- A rogue Keitaro TDS instance (a commercial traffic distribution system) delivers SocGholish and filters unwanted traffic from sandboxes and researchers
- A fake update page to lure victims and serve the payload
- The ZIP file containing the SocGholish JavaScript payload



Threat actor-operated Keitaro TDS instances
Water Scylla collaborates with threat actors who operate rogue Keitaro Traffic Direction System (TDS) servers (Figure 4) for the purpose of delivering FakeUpdate pages with the SocGholish payload.

Trend Micro telemetry from 2025 alone has identified thousands of compromised websites injected with scripts pointing to these malicious TDS domains, which may lead to SocGholish infections depending on the geolocation of the visitor. Figure 5 below highlights the scale of these compromises, which hijack users and facilitate malware delivery.

Among the most frequently used TDS domains, “blackshelter[.]org” has at least 1,297 compromised websites redirecting to it, followed by “rednosehorse[.]com” with 932 and “newgoodfoodmarket[.]com” with 550.
Initial execution
When the user opens the JavaScript file (Figure 7) (T1204.002: User Execution: Malicious File), Windows Scripting Host (wscript.exe) (T1059.007: Command and Scripting Interpreter: JavaScript) executes the loader, which proceeds to collect several pieces of information about the endpoint, as shown in Table 1. This information is sent to the C&C server to profile the environment (Figure 6).

| Artefact | Description |
| ScriptFullName | The full path of the script being executed |
| ComputerName | The name of the computer |
| UserName | The currently logged-in user |
| UserDomain | The domain of the user |
| '%userdnsdomain% | The DNS domain of the user via the Environment Variable UserDnsDomain |
| Win32_ComputerSystem.Manufacturer | The manufacturer of the computer |
| Win32_ComputerSystem.Model | The model of the computer |
| Win32_BIOS.Version and Win32_BIOS. SerialNumber | A concatenation of BIOS version and serial number |
| AntiSpywareProduct.displayName | The name of the installed antispyware products |
| AntiVirusProduct.displayName | The name of the installed antivirus products |
| MACAddress | The MAC address of the network adapter |
| Win32_Process.Name | The names of the running processes |
| Win32_OperatingSystem.BuildNumber | The build number of the operating system |
Table 1. Information collected by the SocGholish loader during environment profiling

Command and control, defense evasion
Our investigation identified dozens of tasks sent by the C&C server to be executed by the loader. They range from reconnaissance commands to the deployment of backdoor components, to data exfiltration.
Task execution is supported by helper functions. Such functions include:
- A deobfuscation function to extract every third character from a string (Figure 8)
- Two strings related to the MSXML2.XMLHTTP ActiveXObject are deobfuscated by this function, likely to evade scanning of content by the Anti Malware Scanning Interface (AMSI) (T1027.013: Encrypted/Encoded File)
- odkpjpehwnww = open
- swneqhnuedjy = send
- Two strings related to the MSXML2.XMLHTTP ActiveXObject are deobfuscated by this function, likely to evade scanning of content by the Anti Malware Scanning Interface (AMSI) (T1027.013: Encrypted/Encoded File)

- Function to send data to the C&C server (Figure 9)
- Contains obfuscated function names belonging to ActiveXObject('MSXML2.XMLHTTP'), which are deobfuscated by the preceding ‘alfh’ function

- Function to read a file from disk and then delete it (Figure 10) (T1070.004: Indicator Removal on Host: File Deletion)
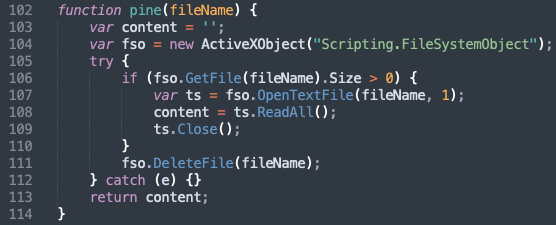
- A function to generate a temporary file path (Figure 11) (T1074.001: Data Staged: Local Data Staging)

- A function to execute a command and capture the output from it (Figure 12) (T1059.003: Command and Scripting Interpreter: Windows Command Shell)

Task execution
While SocGholish is running, it beacons to the C&C server. Tasks are subsequently sent to SocGholish, which are then executed by the loader. Each time the task is executed, the resulting output is piped to a temporary file and sent back to the C&C server.
The malicious tasks are executed in this order:
- Discovery and reconnaissance tasks
- Credential access followed exfiltration tasks
- Backdoor deployment and persistence tasks
- Reverse shell deployment tasks
- Follow on reconnaissance tasks and tasks to download and execute NIRCMD to collect a screenshot
Discovery tasks
- The discovery tasks (Figure 13) are as follow:
- Execute PowerShell command to list the contents of the APPDATA Microsoft Signatures directory (T1059.001: Command and Scripting Interpreter: PowerShell)
- Execute the net command to list domain users (T1087.002: Account Discovery: Domain Account)
- Execute the nltest command to list domain trusts (T1482: Domain Trust Discovery)
- Execute Active Directory Service Interfaces (ADSI) query via PowerShell command to retrieve AD information and interact with objects. The ADSI command will retrieve: (T1069.002: Permission Groups Discovery: Domain)
- Usernames
- User emails
- List Windows 2003 servers
- List all servers
- Get the DNS hostnames of computers

Command and control - backdoor deployment tasks
The following tasks were executed to deploy a Python-based backdoor in the compromised environment to gain persistent access and relay connections from the attacker-controlled server to machines inside of the compromised environment. We attribute this activity to RansomHub affiliates, where it is used by threat actors for command and control, data exfiltration and ransomware deployment.
The tasks (Figure 14) are as follow:
- Download and install Python 3.12 (T1059.006: Command and Scripting Interpreter: Python)
- Install Python PIP
- Install dependencies and list the directory contents
- Create a scheduled task to achieve persistence (T1053.005: Scheduled Task/Job: Scheduled Task)

The file pypa.py is a Python proxy client obfuscated with pyobfuscate (Figure 15).

It contains a hardcoded IP address and port for the RansomHub associated with the C&C server (T1095 Non-Application Layer Protocol) (Figure 16). This is a change from previous versions of this malicious script, which accepted the IP address and port as command line arguments.

The purpose of the backdoor is the create a connection to the hardcoded C&C server and listen for commands from the attackers. Commands are connection commands, with supported targets in the format of an IP address or a domain.
The start_transferring function, shown in Figure 17, unpacks the connection commands sent from the attacker server and creates connections to the target inside of the compromised environment – effectively allowing threat actors to connect to any host (internal or on the internet) with a route from the compromised host.
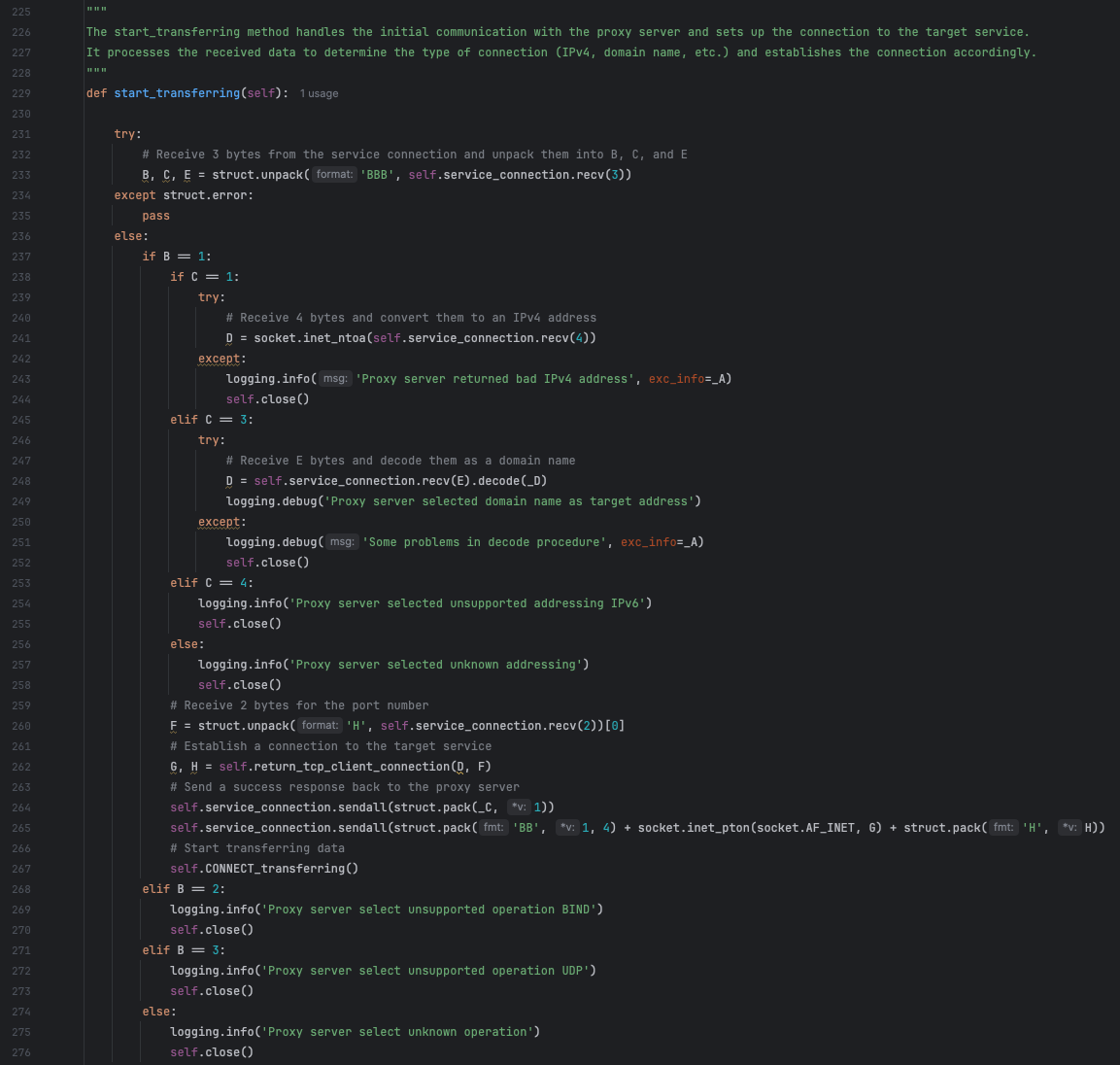
Credential access and exfiltration tasks
In order to gather as much sensitive browser data as possible, the threat actors search for both default and additional browser profiles - where the contents of browser stores are exfiltrated. Notably, app bound encryption keys are extracted from browsers – in a likely effort to access encrypted at rest credentials located in browser stores. The impact of these tasks is the theft of sensitive credentials, leading to a potential broader compromise of business and personal accounts.
The following tasks (Figures 18-21) were observed carrying out this behavior:
- Copy Microsoft Edge login data to a specified location (T1555.003 Credentials from Password Stores: Credentials from Web Browsers)
- Copy Google Chrome login data to a specified location (T1555.003 Credentials from Password Stores: Credentials from Web Browsers)
- Upload binary file <redacted>edg.bin, which contains sensitive information including credentials, to server (T1041: Exfiltration Over C2 Channel)
- Upload binary file <redacted>chr.bin, which contains sensitive information including credentials, to server

- Extract app_bound_encrypted_key from Edge Local State
- Extract app_bound_encrypted_key encrypted key from Chrome Local State

- List contents of Chrome user folder (to identify other browser profiles)
- List contents of Chrome User Data folder

- Exfiltrate the extracted data from additional user profile data to SocGholish C&C server

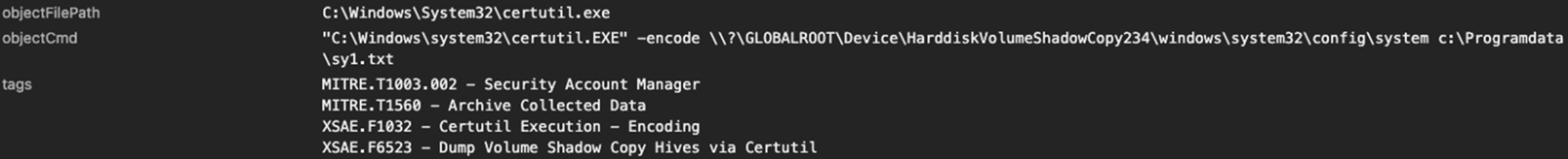
Additionally, it was observed that the attacker utilized the certutil utility to extract the registry hives (SAM, SECURITY, SYSTEM) from a Volume Shadow Copy, saving the content to the %PROGRAMDATA% folder into files named s*1.txt, where * represents the identifier for the specific hive dumped (Figures 22-24). (T1003.002 OS Credential Dumping: Security Account Manager, S0160 : certutil, T1006 : Direct Volume Access)


SSH reverse shell with port forwarding deployment
Multiple tasks were executed to deploy a reverse shell that’s likely related to RansomHub for the purpose of command and control (T1572 Protocol Tunneling), and data exfiltration (T1041: Exfiltration Over C2 Channel) (Figure 25).
The tasks are as follow:
- List the contents of OpenSSH in the System32 directory
- Deploy a scheduled task to create the SSH reverse shell with remote port forwarding (-R) (T1021.004: Remote Services: SSH)
- A one-time execution of the scheduled task was performed to launch the reverse shell

Hands-on keyboard interaction
The timing of these commands (Figures 26-30), along with the duplication of task execution and execution of a command with a syntax error, suggests that this phase involved manual hands-on keyboard interaction.
- Execute systeminfo command to collect detailed information about the host (T1082: System Information Discovery).
- Execute ipconfing /all command to collect detailed network information about the host (T1016: System Network Configuration Discovery)
- Get members of local administrators group (T1069.001: Permission Groups Discovery: Local Groups)
- List network shares (T1135: Network Share Discovery).
- Get account policies (T1201: Password Policy Discovery).
- List user directories on the machine (T1083: File and Directory Discovery).

- Entered an erroneous command – net use <username> /domain(T1087.002 Account Discovery: Domain Account)
- Retrieve domain user information (T1069.002: Permission Groups Discovery: Domain Groups).
- Search for files containing the string ‘pass’ (looking for files containing credentials) (T1083: File and Directory Discovery, T1552.001 Unsecured Credentials: Credentials In Files).

- Extract Wi-Fi profiles (SSID and key) (T1602.002: Data from Local System: Passwords from Wireless Networks).

- Download and execute NIRCMD (T1105: Ingress Tool Transfer)
- Send screenshot to C&C server


The attacker also utilized the SMB protocol (T1021.002: Application Layer Protocol: SMB/Windows Admin Shares) to connect to multiple hosts in the network using compromised credentials (T1078: Valid Accounts). Subsequently, a BAT file was transferred into the %PROGRAMDATA% folder of the remote hosts. Additionally, a scheduled task was created to execute the BAT file every two hours on the remote hosts (Figure 31). However, the task and the file were deleted a few seconds later after being forcibly executed by the adversary.

Although, the file being unavailable, the telemetry available on the host indicates the batch file appears to be attempting to extract encrypted keys from local state files associated with Microsoft Edge and Google Chrome browsers and save the results in the %PROGRAMDATA% folder as a *.log file.
The attacker manually searched for image files saved on the host and targeted files with names that potentially indicated they contained credentials related to cloud management services.
| Tactic | Technique | Reference |
| TA0042 Resource Development | T1608.004 Drive-By Target | In preparation for SocGholish delivery, threat actors compromise websites and inject malicious code to Hijack Visitor Traffic to redirect users to FakeUpdates pages serving SocGholish |
| TA0002 Execution | T1204.002 Malicious File | Actors rely on users to launch a malicious JavaScript file to gain execution |
| T1059.007 Command and Scripting Interpreter: JavaScript | SocGholish uses JavaScript to execute malicious code with wscript.exe | |
| T1059.003 Windows Command Shell Command and Scripting Interpreter: Windows Command Shell | SocGholish Tasks are executed via Windows Command Shell (cmd.exe) | |
| T1059.001 Command and Scripting Interpreter: PowerShell | SocGholish uses PowerShell run Reconnaissance commands and deploy Backdoors | |
| T1059.006 Command and Scripting Interpreter: Python | Threat Actors deploy a Python based Backdoor to proxy external connections to internal information assets | |
| TA0005 Defense Evasion | T1027.013 Obfuscated Files or Information: Encrypted/Encoded File | SocGholish uses heavy code obfuscation to make static file detection more challenging for defenders |
| T1070.004 Indicator Removal: File Deletion | SocGholish contains code to delete evidence of malicious C&C Server Task execution from disk | |
| T1006 Direct Volume Access | Threat actors abuse certutil.exe to read from Volume Shadow Copies to access sensitive data stored by the Security Accounts Manager (SAM) | |
| TA0009 Collection | T1074.001 Data Staged: Local Data Staging | SocGholish Tasks output data to a temporary directory generated by a function in the loader prior to exfiltration |
| TA0007 Discovery | T1069.001 Permission Groups Discovery: Local Groups | SocGholish Tasks were executed to determine the local administrators group membership |
| T1087.002 Account Discovery: Domain Account | SocGholish Tasks are used to gather Information about Domain Accounts | |
| T1082 System Information Discovery | SocGholish Tasks obtain detailed information about the environment during the initial loader execution and through the execution of systeminfo command | |
| T1482 Domain Trust Discovery | SocGholish Tasks execute nltest to gather information about domain trust relationships | |
| T1069.002 Permission Groups Discovery: Domain Groups | SocGholish Tasks are executed to discover level groups and permissions | |
| T1016 System Network Configuration Discovery | SocGholish Tasks executed ipconfig /all command to network configuration and settings | |
| T1135 Network Share Discovery | SocGholish Tasks were executed to identify shared drives | |
| T1083 File and Directory Discovery | Adversaries executed the dir command to discover sensitive files and explore user directories | |
| TA0003 Persistence | T1053.005 Scheduled Task/Job: Scheduled Task | A Scheduled Task is used to achieve persistence with the Python Based Backdoor |
| TA0011 Command and Control | T1095 Non-Application Layer Protocol | The Python Based backdoor establishes a TCP connection towards an external host for the purpose of relaying connections to internal assets in the compromised environment |
| T1572 Protocol Tunneling | Threat actors use SSH to proxy communications from an External C&C Server | |
| T1105 Ingress Tool Transfer | Adversaries executed SocGholish Tasks to download tools such as NIRCMD.exe to collect screenshots from the compromised environment | |
| TA0006 Credential Access | T1555 Credentials from Password Stores | Adversaries abuse netsh wlan show profiles to extract sensitive information about Wireless Network Configurations |
| T1555.003 Credentials from Password Stores: Credentials from Web Browsers | SocGholish Tasks are executed to copy and exfiltrate credentials from Web Browser Password Stores | |
| T1003.002 Security Account Manager | Threat actors abuse certutil.exe to read from Volume Shadow Copies to access sensitive data stored by the Security Accounts Manager (SAM) | |
| T1552 Unsecured Credentials: Credentials In Files | Adversaries searched for files with the string ‘pass’ in the name | |
| TA0010 Exfiltration | T1041 Exfiltration Over C2 Channel | SocGholish Exfiltrates stolen data including Credentials, Screenshots and outputs from Reconnaissance commands to its C&C Server |
| TA0008 Lateral Movement | T1021.002 Remote Services: SMB/Windows Admin Shares | Adversaries used Valid Accounts to access SMB protocol to compromise hosts in the network |
SocGholish infrastructure
Our most recent tracking of SocGholish C&C infrastructure shows 18 active C&C servers, whose domains are rotated at least once per week – with some fluctuations in the frequency of domain rotation (Figure 32). Fresh domains may lead to a higher infection success rate.
SocGholish operators use compromised domains for C&C infrastructure, where a new subdomain is specifically created by the threat actors for use with SocGholish. This technique, known as domain shadowing, is desirable from a threat actor perspective, because it enables them to leverage the reputation of more mature domains which are less likely be blocked by automated detection systems.

RansomHub infrastructure
As the objective of this cluster is to enable initial access for RansomHub, our intelligence teams have continuously tracked the malicious infrastructure as it is deployed for use in the post-SocGholish infection phase (Figure 33). We identified 22 IP addresses across a diverse range of Autonomous Systems (ASNs), predominantly located in the US, with just two located in the Netherlands and Germany, respectively.
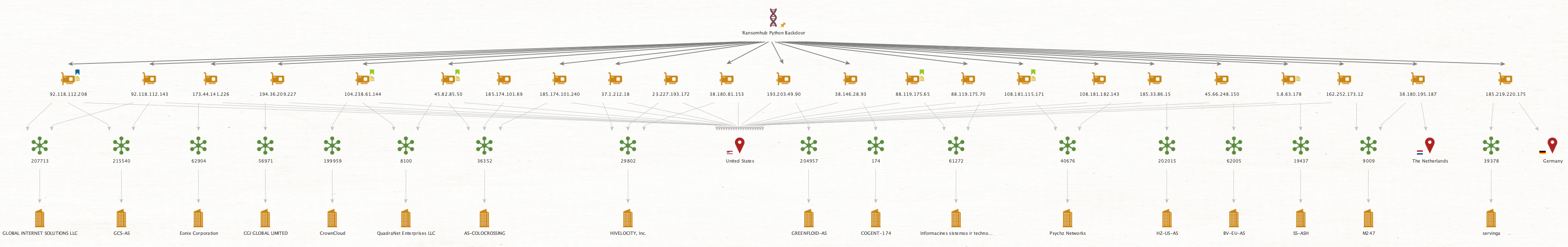
Security recommendations
Security and incident response teams must urgently address SocGholish infections as critical events and invoke incident response procedures to rapidly mitigate the impact of its malicious activity like backdoor deployment, unauthorized access to sensitive data, lateral movement, data exfiltration, and ransomware-driven data destruction. Defenders should also apply the following best practices:
- Deploying security operations solutions to rapidly identify, disrupt and correlate malicious activities such as those used in attacks with SocGholish
- Reducing the attack surface for script-based malware like SocGholish by:
- Hardening endpoints and servers by blocking suspicious Windows Scripting Host (wscript.exe) and PowerShell execution through policy-based controls like group policy objects
- Trend Vision One customers can apply “Attack Surface Reduction” by ensuring that “Behavior Monitoring and Predictive Machine Learning” are enabled in Endpoint and Server Policies
- Enabling logging of anti-malware scan interface events to support investigations
- Trend Vision One customers can investigate “TELEMETRY_AMSI_EXECUTE” events to recreate script executions for incident response activities
- Deploying web reputation services (WRS) on endpoints, cloud workloads and proxy servers to detect and block malicious and anomalous traffic
- Using network intrusion detection and prevention solutions, and network detection and response (NDR), to gain visibility into network traffic
- Retiring or significantly hardening, segment or isolate end-of-life operating systems, as these are targeted by adversaries through reconnaissance and lateral movement tactics
For their part, website administrators and owners should be aware that vulnerable content management systems (CMS) and their plugin systems are frequently targeted by threat actors. This is because they enable cybercriminals to abuse websites to hijack visitor traffic, as is the case with SocGholish, and distribute malware.
Compromised websites can have a significant impact on a business’ operations if their websites are being tagged as malicious by security solutions and web browser block lists. Website administrators can mitigate this by:
- Monitoring security announcements for Content Management Systems and applying mitigations and/or patching vulnerabilities
- Monitoring security announcements for content management system plugins and applying mitigations and/or patching vulnerabilities, which are exploited to gain initial access to webservers
- Deploying web application firewall to filter exploit traffic
- Restricting access to administration portals
- Using multi-factor authentication (MFA) and complex passwords for administration panels
- Using SSH keys for administration interfaces and avoiding exposing administration interfaces such as web host management interfaces, control panels, and SSH interfaces to the internet
- Isolating and rebuilding compromised web servers to eradicate threat actors in the aftermath of a compromise
Proactive security with Trend Vision One™
Trend Vision One™ is an enterprise cybersecurity platform that simplifies security and helps enterprises detect and stop threats faster by consolidating multiple security capabilities, enabling greater command of the enterprise’s attack surface, and providing complete visibility into its cyber risk posture. The cloud-based platform leverages AI and threat intelligence from 250 million sensors and 16 threat research centers around the globe to provide comprehensive risk insights, earlier threat detection, and automated risk and threat response options in a single solution.
As we noted earlier, Trend Vision One customers can reduce their potential attack surface by ensuring that “Behavior Monitoring and Predictive Machine Learning” are enabled in Endpoint and Server Policies.
Trend Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Vision One customers can access a range of Intelligence Reports and Threat Insights. Threat Insights helps customers stay ahead of cyber threats before they happen and allows them to prepare for emerging threats by offering comprehensive information on threat actors, their malicious activities, and their techniques. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and effectively respond to threats.
Trend Vision One Intelligence Reports App [IOC Sweeping]
- [AIM/MDR/IR][Spot Report] Ghoulish Tactics: Unmasking the SocGholish to Ransomhub Attack Chain
Trend Vision One Threat Insights App
- Threat Actors: Water Scylla
- Emerging Threats: Ghoulish Tactics: Unmasking the SocGholish to Ransomhub Attack Chain
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Searching for the initial dropper:
tags: (“XSAE.F11697” OR “XSAE.F11689” OR “XSAE. F8637” OR “XSAE. F8636” OR “XSAE. F7176”)
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Conclusion
SocGholish is a prevalent and evasive threat. The use of heavy obfuscation in the loader poses a challenge for static file detection technologies. The fileless execution of commands may pose a challenge for certain detection technologies.
The sheer volume of compromised websites leading to SocGholish, coupled with the use of a commercial TDS for sandbox and crawler evasion and the use of Anti-Sandbox routines may pose a challenge for certain automated detection solutions like sandboxes, which may enable SocGholish to run in environments, leading to highly impactful attacks.
Its collaboration with prevalent and dangerous RaaS operations like RansomHub means that SocGholish poses a significant threat to enterprises. However, there are several detection opportunities, from suspect execution with suspicious process chains that perform discovery, lateral movement, credential access and data exfiltration, to outbound connections to low reputation infrastructure, and anomalous internal connections from compromised hosts.
Indicators of compromise (IOCs)
Download the list of IOCs here.

