What is SOAR Security?
Trend Micro stops threats faster with deeper insights to hunt, detect, investigate, and respond.
What is SOAR in cyber security?
SOAR, also known as Security Orchestration, Automation, and Response, is a function or solution in cyber security that automates cyber-attack incident response and security operations. It reduces the workload of operators by automatically processing workflows when certain conditions are met, based on rules predefined by the vendor or playbooks defined by the user.
SOAR performs processing based on vendor-defined rules or user-defined playbooks (a list of flows that perform a series of actions specified in a script when certain conditions are met). It supports security operators by automatically performing actions in response to pre-assumed situations. For example, communication is blocked when an unspecified number of communications occur within a certain period of time to a server where important information is stored. It also automatically takes actions such as blocking terminals that are infected with malware or accessing command and control (C&C) servers to a quarantine network.
How does SOAR work?
Security Orchestration
SOAR integrates various security tools and platforms, enabling seamless communication and collaboration between cybersecurity and IT teams. For instance, firewalls, endpoint protection systems, and SIEM solutions can work together within a unified SOAR ecosystem. This interconnectedness eliminates silos, ensuring that security operations are cohesive and comprehensive.
Security Automation
Repetitive tasks like threat detection, alert triaging, and log analysis can consume significant time and resources. SOAR automates these processes, reducing the manual workload and minimizing the risk of human error. For example, SOAR can automatically investigate phishing emails by analyzing headers, extracting URLs, and checking them against threat intelligence databases.
Security Response
SOAR platforms facilitate faster and more coordinated incident responses by utilizing pre-defined playbooks. These playbooks outline specific actions to be taken for various types of incidents, ensuring consistency and efficiency. For example, in the event of a malware infection, a playbook might include isolating the affected system, initiating a forensic investigation, and notifying stakeholders.
Benefits of SOAR Security
Streamlined Operations
SOAR automates repetitive and time-intensive tasks, such as log analysis and threat correlation, significantly reducing the workload for security teams. By automating these processes, teams can redirect their focus toward higher-priority tasks, such as incident investigation and strategic planning.
Faster Incident Response
With pre-defined playbooks and automated workflows, SOAR enables organizations to detect, analyze, and mitigate security incidents in real time. By reducing the time it takes to respond, SOAR minimizes the potential impact of cyber threats on critical systems and data.
Improved Accuracy and Consistency
Automation through SOAR eliminates the variability and errors that can arise from manual processes. By standardizing responses to common threats, organizations can ensure a consistent and reliable approach to incident handling across their entire security infrastructure.
Enhanced Threat Detection
SOAR platforms integrate with diverse threat intelligence feeds and monitoring tools, providing a unified view of potential risks. This holistic perspective allows security teams to identify threats more effectively and act on data-driven insights to bolster their defenses.
Scalability
As organizations grow and adopt more complex IT environments, SOAR platforms adapt seamlessly to evolving needs. Whether managing on-premises systems, cloud environments, or hybrid setups, SOAR provides scalable solutions that accommodate expansion without compromising security.
Resource Optimization
For organizations facing resource constraints, SOAR maximizes the value of existing personnel and tools. By automating repetitive tasks and reducing alert fatigue, security teams can achieve greater efficiency without the need for significant staffing increases.
Enhanced Collaboration
SOAR fosters better communication and coordination among security teams by providing centralized dashboards and unified workflows. This collaboration improves incident management and ensures that responses are swift and well-coordinated.
Increased Compliance
By automating data collection and reporting, SOAR simplifies compliance with regulations like GDPR, HIPAA, and PCI DSS. Organizations can generate accurate reports and maintain an audit trail, demonstrating their commitment to security best practices and regulatory adherence.
SOAR vs SIEM
While both SOAR and SIEM have similarities such as the detection of security risks and data collection and analysis but their roles within an organization differ significantly. Both tools gather and analyze data to identify threats and notify security teams, but the scope of their functionality sets them apart.
SIEM technologies focus on correlating and analyzing logs from multiple data sources to identify suspicious activities. It then alerts security analysts to investigate further. SOAR, on the other hand, takes a more hands-on approach to security operations by automating workflows and executing responses based on predefined workflows. This includes leveraging AI to recognize behavioral patterns and proactively mitigate potential risks.
One of SOAR’s unique strengths is its ability to process alerts from sources that traditional SIEM systems may not cover, such as cloud environments, IoT devices, and vulnerability scans. This expanded scope allows SOAR to filter and consolidate alerts, reducing redundancy and improving efficiency. Integrating SOAR with SIEM combines the analytical power of the latter with the automation and orchestration of the former, creating a more streamlined and effective security strategy.
By utilizing these tools together, organizations can strike a balance between thorough threat detection and swift, automated response, empowering security teams to stay ahead of evolving cyber threats
Relationship between SOAR and XDR
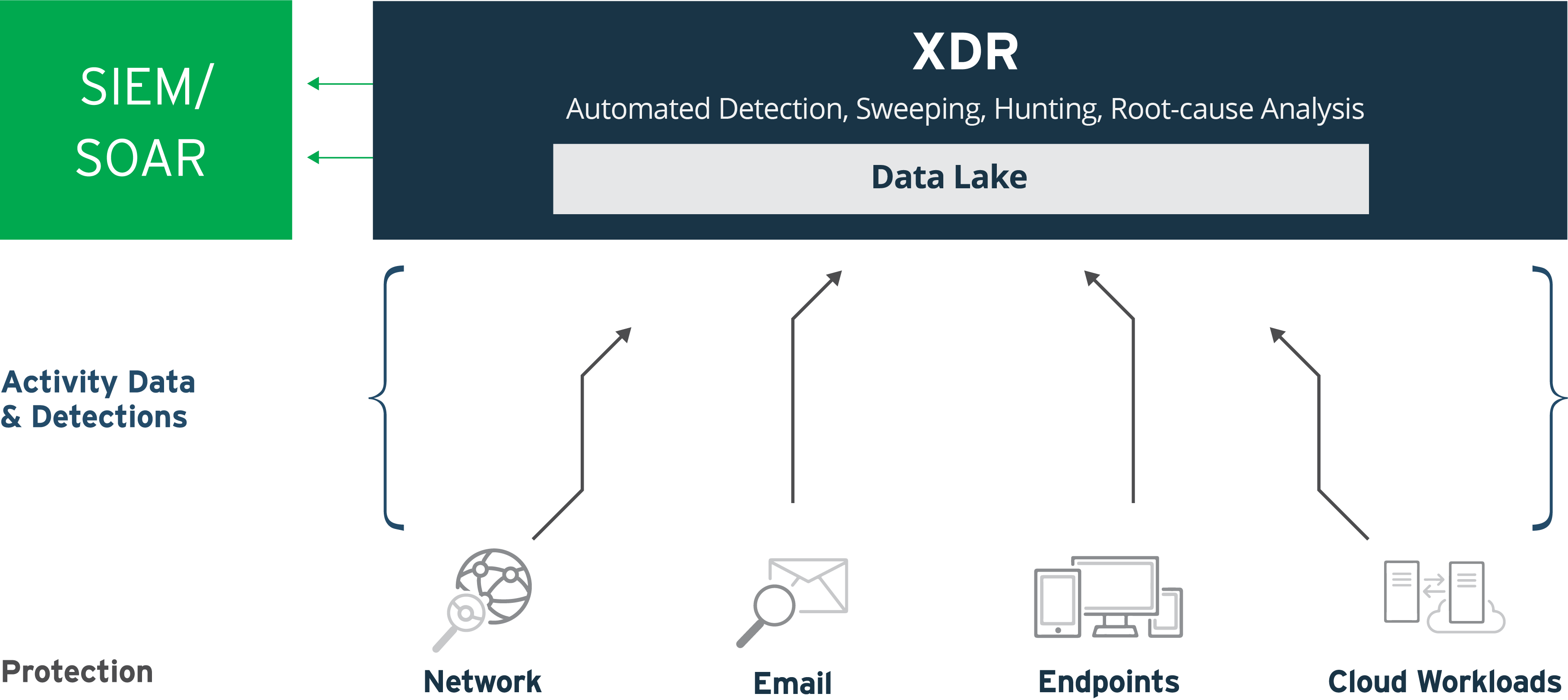
SIEM is a product that aggregates logs and events from PCs, servers, proxies, firewalls, security products, etc., and visualizes them in a meaningful way; SOAR is a product that automatically acts when certain actions (such as many accesses to a specific server within a certain time) occur based on predefined rules, using information gathered by SIEM. XDR is a product that detects and visualizes traces of attacks to investigate, identify the cause, and respond to incidents as a post-response to cyber-attacks, if a threat enters a user's environment. SOAR has been attracting attention in recent years for its ability to mechanically process massive amounts of log information to remove noise and extract only those alerts that truly require action.
SOAR can be effective in cases where there are a wide range of products and services that can be used in conjunction with APIs and detailed conditions for script settings, and where experienced security operators can continuously maintain settings. Some XDRs can also be integrated with SOAR, so that XDRs can be used to supplement expertise in cyber-attack detection, while SOAR can be used to integrate with a wide range of products and automate responses.
XDR is reshaping cybersecurity by unifying and enhancing SIEM and SOAR capabilities into a single platform. It addresses alert fatigue, improves incident correlation, simplifies operations, and enhances efficiency for SOC teams.
Trend Micro XDR Platform with SOAR
Optimize workflows with an ecosystem that includes SIEM, SOAR, IAM, firewall, threat intelligence, IT service management, and more.