Ransomware
Albabat Ransomware Group Potentially Expands Targets to Multiple OS, Uses GitHub to Streamline Operations
Trend Research encounters new versions of the Albabat ransomware, which appears to target Windows, Linux, and macOS devices. We also reveal the group’s use of GitHub to streamline their ransomware operation.
Key takeaways
- Trend Research uncovered new versions of the Albabat ransomware. The development of these versions signifies the ransomware operators’ potential expansion of their targets from Windows to Linux and macOS. Research also reveals the group’s use of GitHub to streamline operations.
- Enterprises should remain vigilant against ransomware threats like Albabat as a successful attack can incur reputational damage, operational disruption, and financial losses once threat actors get a hold of and ransom critical data.
- To mitigate Albabat ransomware, organizations should have strong access controls for sensitive data, update and patch systems regularly and have proper backups.
Albabat ransomware evolves to target multiple OS
The group behind Albabat, a financially motivated ransomware, has recently been active and released a new version of their ransomware. Early versions were observed in late 2023 and early 2024. Our threat hunting team has recently encountered versions 2.0.0 and 2.5, which target not only Microsoft Windows but also gather system and hardware information on Linux and macOS. The team discovered multiple previously undetected variants of the Albabat ransomware. These new versions retrieve their configuration data through the GitHub REST API using a "User-Agent" string labelled "Awesome App." The configuration provides key details about the ransomware's behavior and operational parameters. Notably, it indicates that these variants belong to Albabat version 2.0.
By decoding it, we can better understand the configuration of the ransomware.
The Albabat version ignores the following folders: Searches, AppData, $RECYCLE.BIN, System Volume Information, windows.old, steamapps, perflogs, ansel, tmp, node_modules, cache, vendor, target, Mozilla, venv, env, Chrome, google-chrome, pypoetry, vimfiles, viminfo, site-packages, scoop, go, and temp.
This version also encrypts the following extensions: ~$, .src, .ico, .cur, .theme, .themepack, .bat, .com, .cmd, .cpl, .prf, .icls, .idx, .mod, .pyd, .vhdx, ._pth, .hta, .mp3, .CHK, .pickle, .pif, .url, .ogg, .tmp, .dat, .exe, .lnk, .win, .vscdb, .bin, .cab, .inf, .lib, .tcl, .cat, .so, .msi, .vpk, .vc, .cur, .ini, .bik, .sfx, .xnb, .ttf, .otf, .woff, .woff2, .vfont, .resource, .N2PK, .log, .pkg, .desktop, .dll, .pkr, .arc, .sig, .bk2, .arz, .swf, .qt, .wma, .mp2, .vdf, .pdb, .nfo, .whl, .mui, .srm, .smc, .dic, .lock, .pyc, .TAG, .locale, .store, .sdi, .library-ms, .acf, .po, and .mo.
It also skips the following files: ntuser.dat, ntuser.ini, iconcache.db, Thumbs.db, and .DS_Store.
In addition, it kills the following processes: taskmgr.exe, processhacker.exe, regedit.exe, code.exe, excel.exe, powerpnt.exe, winword.exe, msaccess.exe, mspub.exe, msedge.exe, virtualboxvm.exe, virtualbox.exe, chrome.exe, cs2.exe, steam.exe, postgres.exe, mysqlworkbench.exe, outlook.exe, mysqld.exe, windowsterminal.exe, powershell.exe, cmd.exe, sublime_text.exe, microsoft.photos.exe, and photosapp.exe.
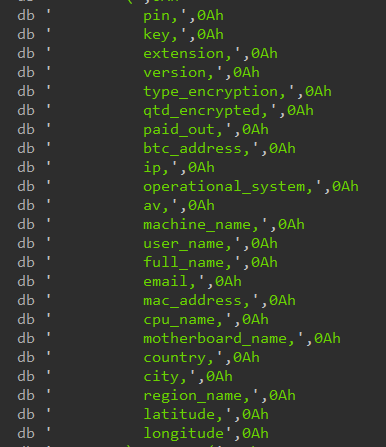
The configuration details show where the ransomware stores data collected from the victim's machine. It connects to a PostgreSQL database at the following address:
postgres://postgres.<username>:<password>@aws-0-us-west-1.pooler.supabase[.]com:5432/postgres
The ransomware uses a database to track infections and payments. This collected information helps attackers to make ransom demands, monitor infections, and sell victims' data.
The configuration also includes commands for Linux and macOS that indicate binaries have been developed to target these platforms.

GitHub account used for configuration and essential components
The GitHub repository billdev.github.io is used to store and deliver configuration files for ransomware. Although the repository used by the ransomware is currently private, it remains accessible through an authentication token observed in Fiddler during the connection.
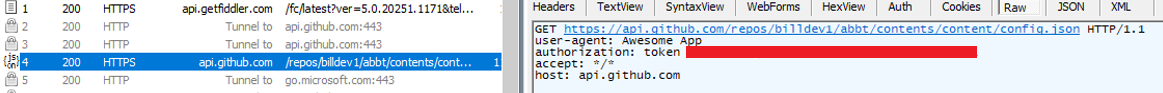

Upon further investigation of the GitHub account, we found out that the page was created on February 27, 2024, implying that it is just over a year old. The account is registered under the name "Bill Borguiann," which is likely an alias or pseudonym.

The commit history shows ongoing active development, with the user primarily modifying the configuration code. The associated commit email is billdev@morke[.]org, and the most recent commit was made on February 22, 2025.

The commit history shows a significant increase in activity during August and September 2024. There were particularly high volumes of commits at two key times: between 00:00 to 04:00 UTC, and from 12:00 to 16:00 UTC. This pattern displays a focused and consistent effort during these specific hours, as illustrated in the graph below.
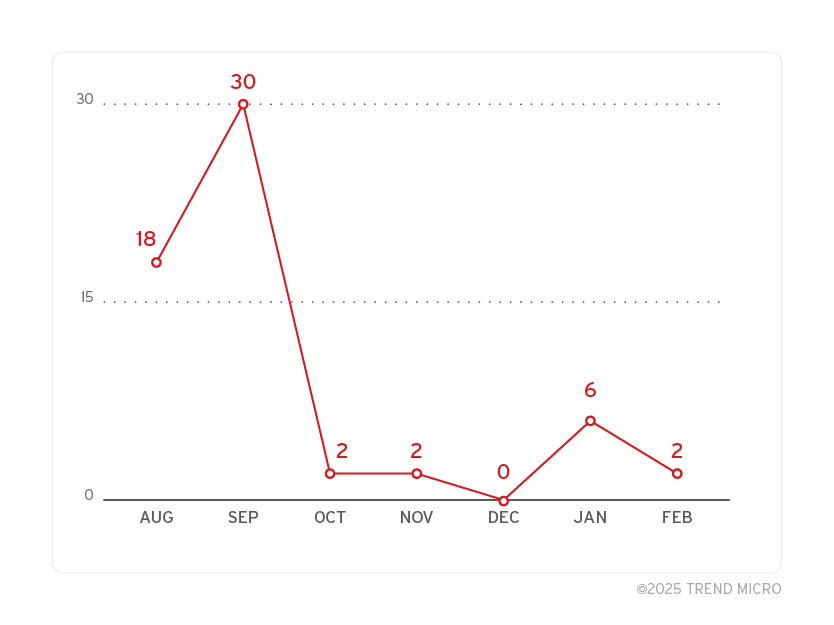
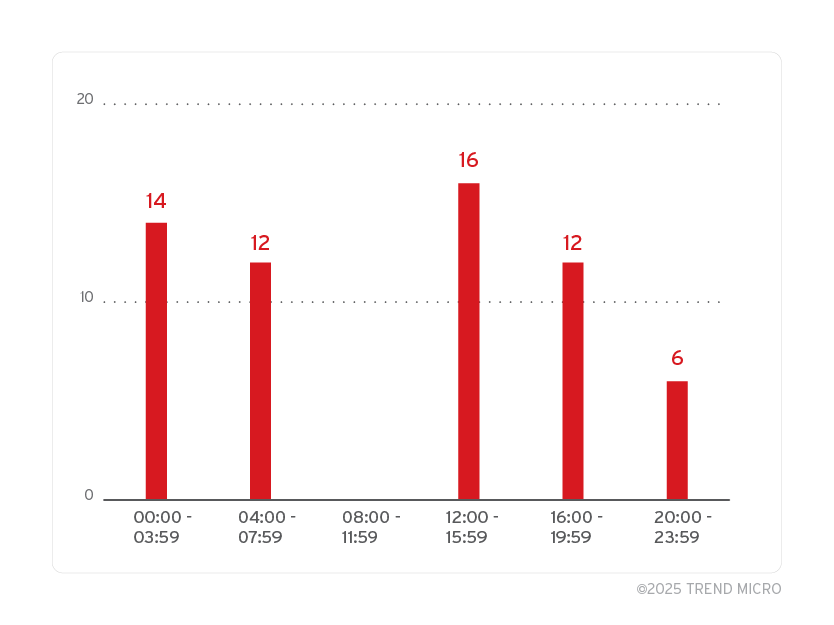
A noteworthy discovery in the private repository is a folder named 2.5.x, which likely suggests a newer version of the ransomware. Considering that the latest version found in the wild is 2.0, this strongly indicates that version 2.5 is currently in development.

No ransomware binary was found in the 2.5.x directory. Instead, it contains a config.json file for version 2.5 of the ransomware. This configuration reveals newly added cryptocurrency wallets for Bitcoin, Ethereum, Solana, and BNB. No transactions have been detected in these wallets yet.

Security recommendations
Staying ahead of ransomware threats such as Albabat and monitoring indicators of compromise (IoCs) is necessary for proactive cybersecurity defense. This approach allows for early detection of threats, enhances security measures, supports forensic investigations, and disrupts the activities of cybercriminals. For researchers, tracking IoCs offers valuable insights into attack patterns, which can help them develop more effective threat prevention strategies.
Enterprises can also implement the following security best practices:
- Regular backups: Maintain up-to-date, secure backups of all critical data. Regularly test restoration processes to ensure data can be recovered quickly in the event of an attack.
- Network segmentation: Implement network segmentation to limit the spread of ransomware across your organization. By isolating sensitive data and critical systems, you can prevent widespread damage.
- Patch and update systems: Regularly update and patch application software, operating systems, and other applications to ensure that you close vulnerabilities that attackers could exploit.
- User training and awareness: Conduct regular training sessions for employees to recognize phishing attempts and suspicious links.
Proactive security with Trend Vision One™
Trend Vision One™ is the only AI-powered enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection. This comprehensive approach helps you predict and prevent threats, accelerating proactive security outcomes across your entire digital estate. Backed by decades of cybersecurity leadership and Trend Cybertron, the industry's first proactive cybersecurity AI, it delivers proven results: a 92% reduction in ransomware risk and a 99% reduction in detection time. Security leaders can benchmark their posture and showcase continuous improvement to stakeholders. With Trend Vision One, you’re enabled to eliminate security blind spots, focus on what matters most, and elevate security into a strategic partner for innovation.
Trend Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Vision One customers can access a range of Intelligence Reports and Threat Insights. Threat Insights helps customers stay ahead of cyber threats before they happen and allows them to prepare for emerging threats by offering comprehensive information on threat actors, their malicious activities, and their techniques. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and effectively respond to threats.
Trend Vision One Intelligence Reports App [IOC Sweeping]
- Albabat: Streamlining Ransomware Operations with GitHub for Configuration and Components
Trend Vision One Threat Insights App
- Emerging Threat: Albabat: Streamlining Ransomware Operations with GitHub for Configuration and Components
Hunting Queries
Trend Vision One Search App
Trend Vision One customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Detection of Command-Line Execution for System Information Gathering
eventSubId: 2 AND processCmd: /cmd.+wmic (cpu|csproduct|os|nic).+get (name|caption|displayName|MACAddress)/
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
Indicators of Compromise (IoC)
| SHA1 | Detection |
| 1cc2d1f2a991c19b7e633a92b1629641c019cdeb | Ransom.Win64.ALBABAT.THBBEBE |
| c7c52fdaecf325dfaf6eda14e0603579feaed40a | Ransom.Win64.ALBABAT.THBBEBE |
| 8a3ea65147a156d381d8f1773e91eb8e0f6b1e40 | Ransom.Win64.ALBABAT.THBBEBE |
| 8de54cad9d6316679580c91117b484acb493ab72 | Ransom.Win64.ALBABAT.THBBEBE |
| d67dc8c4232a3943a66608d62874923e9a3fb628 | Ransom.Win64.ALBABAT.THBBEBE |

