Cyber Threats
How Trend Micro Helps Manage Exploited Vulnerabilities
As technological innovations evolve, protecting companies from cyber threats tomorrow secures their businesses today. Read how Trend Micro protects customers from vulnerability exploits by blocking them as early as possible.

As technological innovations evolve, protecting companies from cyber threats tomorrow secures their businesses today. Exploiting known vulnerabilities to successfully compromise an organization has long been a common tactic used by malicious actors. Whether Heartbleed, EternalBlue, or most recently Zerologon, threat actors take advantage of newly disclosed vulnerabilities in their attacks. But even with thousands of new vulnerabilities disclosed every year (18K+ in 2020 according to NIST), the reality is that only so many are weaponized into exploits and used in attacks. As such, businesses have had to rethink their patch management process due to this proliferation of known vulnerabilities as well as the shrinking time window from patch to exploit and to decide what to patch now and what can wait.
For over 30 years, Trend Micro has defended enterprises against malicious cyber activities and has blocked both zero-day exploits and n-day vulnerabilities as early as possible. Supported by the Zero Day Initiative (ZDI), the world’s largest vendor agnostic bug bounty program, and our n-day vulnerability research team, Trend Micro has one of, if not the largest, vulnerability research organization in the world and uses this to protect our customers from exploits. In 2020, our TippingPoint IPS solution was able to protect customers on average 81 days prior to a patch being disclosed for bugs submitted to the ZDI. Host-based and network-based IPS technology is used to deploy a virtual patch that can protect a system from an exploit. Even when a new vulnerability is disclosed that ZDI does not help disclose, our vulnerability research team analyzes many of the critical bugs and works to ensure a new IPS filter is made available as quickly as possible for our customers. As part of our constant collection and analysis of newly disclosed vulnerabilities, let’s dive into a recent case study to give you an example of how this works.
Case Study of How Trend Micro Protects Customers from Vulnerability Exploits
In October 2020, the National Security Agency (NSA) named 25 vulnerabilities that had been exploited by Chinese state-sponsored cyber actors to acquire sensitive intellectual property, economic, political, and military information. 13 of the 25 vulnerabilities were newly published in 2020, and the oldest vulnerability could be traced back to 2015. The threats these bugs posed were real, with 15 rated Critical according to their CVSS v3.1 score.
| CVE | Published Date | CVSS v3.1 severity | CVSS v3.1 base score | Vendor | Trend IPS Filter (Y/N) |
| CVE-2015-4852 | 11/18/15 | NA | NA | Oracle | Y |
| CVE-2017-6327 | 8/11/17 | High | 8.8 | Symantec | Y |
| CVE-2018-6789 | 2/8/18 | Critical | 9.8 | Canonical | Y |
| Debian | Y | ||||
| Exim | Y | ||||
| CVE-2018-4939 | 5/19/18 | Critical | 9.8 | Adobe | Y |
| CVE-2019-3396 | 3/25/19 | Critical | 9.8 | Atlassian | Y |
| CVE-2019-0803 | 4/9/19 | High | 7.8 | Microsoft | Y |
| CVE-2019-11510 | 5/8/19 | Critical | 10 | Pulse secure | Y |
| CVE-2019-0708 | 5/16/19 | Critical | 9.8 | Microsoft | Y |
| CVE-2019-11580 | 6/3/19 | Critical | 9.8 | Atlassian | Y |
| CVE-2019-1040 | 6/12/19 | Medium | 5.9 | Microsoft | Y |
| CVE-2019-18935 | 12/11/19 | Critical | 9.8 | Telerik | Y |
| CVE-2019-19781 | 12/27/19 | Critical | 9.8 | Citrix | Y |
| CVE-2020-0601 | 1/14/20 | High | 8.1 | Microsoft | Y |
| CVE-2020-2555 | 1/15/20 | Critical | 9.8 | Oracle | Y |
| CVE-2020-8515 | 2/1/20 | Critical | 9.8 | Draytek | Y |
| CVE-2020-3118 | 2/5/20 | High | 8.8 | Cisco | N |
| CVE-2020-0688 | 2/11/20 | High | 8.8 | Microsoft | Y |
| CVE-2020-10189 | 3/6/20 | Critical | 9.8 | Zohocorp | Y |
| CVE-2020-5902 | 7/1/20 | Critical | 9.8 | F5 | Y |
| CVE-2020-15505 | 7/7/20 | Critical | 9.8 | Mobileiron | Y |
| CVE-2020-8193 | 7/10/20 | Medium | 6.5 | Citrix | Y |
| CVE-2020-8195 | 7/10/20 | Medium | 6.5 | Citrix | Y |
| CVE-2020-8196 | 7/10/20 | Medium | 4.3 | Citrix | Y |
| CVE-2020-1350 | 7/14/20 | Critical | 10 | Microsoft | Y |
| CVE-2020-1472 | 8/17/20 | Critical | 10 | Canonical | Y |
| Fedoraproject | Y | ||||
| Microsoft | Y | ||||
| Opensuse | Y | ||||
| Samba | Y | ||||
| Synology | Y |
Source: Trend Micro
Speed matters in the battle against cyber-attacks. No matter it’s a zero-day vulnerability, or known vulnerabilities still on the long “To be patched” list, Trend Micro provides clients with quick and pain-free solutions.
Trend Micro Research tracked these vulnerabilities and helped enterprises defend against potential exploits. Our products offer virtual patching and vulnerability shielding to protect against known vulnerabilities. Specific vulnerability protections include:
- Trend Micro – Cloud One Workload Security provides comprehensive server and virtual desktop (VDI) protection for virtual, cloud, and hybrid deployments.
- TippingPoint Threat Protection System proactively detects and prevents vulnerability attacks and network exploits.
In this case study, 25 cloud-based rules and 28 TippingPoint filters cover the vulnerabilities on NSA’s list and only one CVE (CVE-2020-3118) does not have coverage. Let’s look at how vulnerabilities are covered under each scenario:
1. Virtual patching before official protection released
Zero-day vulnerabilities pose enormous cybersecurity threats. They are usually exploited long before an official patch released from vendors, making targeted companies hard to defend themselves against attacks. To protect companies against malicious activities, Trend Micro runs the world’s largest bug bounty program, Zero Day Initiative (ZDI), to capture exploits before it’s being used in the dark web, and then develop a digital vaccine to protect client companies.
CVE-2020-2555 is a perfect example of how Trend Micro covers zero-day vulnerabilities. It’s a vulnerability that exists in the Oracle Coherence product of Oracle Fusion Middleware. This easily exploitable vulnerability allows unauthenticated attackers with network access via T3 to compromise Oracle Coherence. As a critical vulnerability rated at 9.8 in CVSS3.1 base score, it was captured by Jang from VNPT ISC, who worked with Trend Micro ZDI program. TippingPoints soon developed a virtual patch to CVE-2020-2555, 57 days prior to the official patch from Oracle.
The virtual patch came in at the right time. The first attack recorded was merely 45 days after the patch published. As time went by, more cyber actors weaponized this vulnerability and the overall attacks reached a peak in August 2020. At the end of 2020, the total attacks of CVE-2020-2555 amounted to 4.23k.
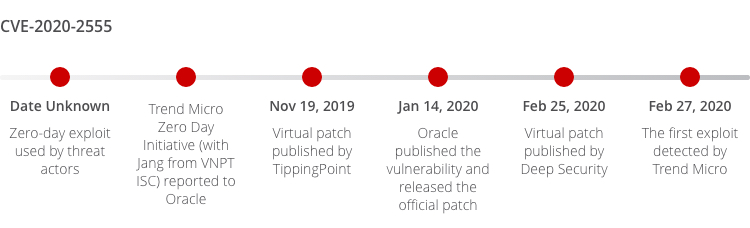
Source: https://www.oracle.com/security-alerts/cpujan2020.html
2. In-time coverage with pain-free solutions
For the vulnerabilities that are not captured through the ZDI program, Trend Micro syncs up with the vendor and offers in-time coverage.
CVE-2020-1350 is a critical vulnerability rated at 10, which has been targeted by cyber actors since August 2020. It is a Remote Code Execution (RCE) vulnerability that exists in Windows DNS servers when they fail to properly handle requests. Microsoft published this vulnerability on July 14, 2020 and offered an official patch. On the same day, Trend Micro leveraged its solid research power and released virtual patches through TippingPoint and Deep Security. Through virtual patching, Trend Micro offered clients pain-free solutions to defend their systems, avoiding the hassle of manual patching.
The protection was invaluable. By the end of 2020, our virtual patches for this CVE have blocked 2.9 million attacks from cybercriminals.
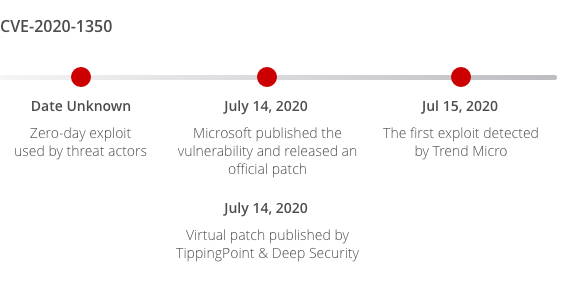
Source: https://msrc-blog.microsoft.com/2020/07/14/july-2020-security-update-cve-2020-1350-vulnerability-in-windows-domain-name-system-dns-server/
https://media.defense.gov/2020/Jul/16/2002458198/-1/-1/0/CSA_CVE20201350-V_1_0%20-%20COPY.PDF
3. Complete shield in less than 30 days of vulnerability debut
In some cases, it might take longer to form a complete shield for certain vulnerabilities. For those more complicated vulnerabilities, Trend Micro manages to launch virtual patching in less than 30 days from when they were introduced publicly.
CVE-2020-0688, for example, demonstrates how Trend Micro protects clients against potential exploits. This is a Microsoft Exchange validation key remote code execution vulnerability, which exists when the software fails to properly handle objects in memory. It was captured by an anonymous researcher who worked with Trend Micro ZDI program. ZDI later reported the vulnerability to the vendor, Microsoft, who published an official patch on Feb 11, 2020. Trend Micro soon published its virtual patches through TippingPoint and Deep Security in 13 days and 28 days respectively. Soon, Trend Micro blocked the first attack recorded on March 14 and protected clients from around 1,760 attacks in 2020.
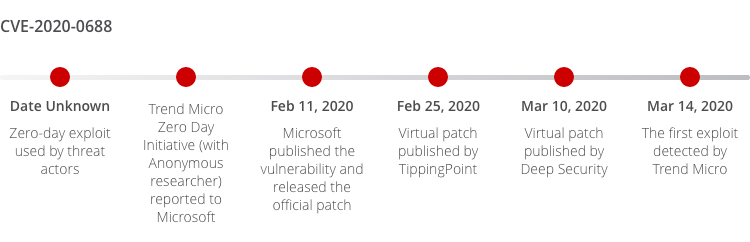
Source: https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-0688
How to Protect Your Organization from Vulnerability Exploitation
Traditional security measures should always be applied to watch for compromised accounts and networks, malicious traffic, and other Indicators of Compromise (IoCs). A good resource for identifying In-The-Wild exploits of vulnerabilities is Google Project Zero’s site: https://github.com/googleprojectzero/0days-in-the-wild Identifying what vulnerabilities need to be patched or virtually patched is a good start. Prioritization is critical:
- Continuously conduct an exposure assessment to determine what CVEs past and present are in your environment at all times
- Assess the criticality of those systems that contain those CVEs
- Conduct a continuous but simple risk assessment:
- Assess the Probability-likelihood of those identified CVEs are or will be exploited in the wild against the severity-impact of those CVEs used in an attack
- Is a POC available
- Is it In-The-Wild
- Assess the Probability-likelihood of those identified CVEs are or will be exploited in the wild against the severity-impact of those CVEs used in an attack
Preventative measures are also a good option: Intrusion prevention systems and antimalware software for the network and the host devices (all endpoints) to monitor for ransomware, viruses, and other threats are critical. Logs need to be collected, centralized, and analyzed by a SIEM (Security Information & Event Manager), which can be done automatically through the Trend Micro Vision One platform. Vision One simplifies the process of prioritizing and analyzing security event logs, allowing IT and SOC teams to spend their time on the most critical threats.
- Regularly update online infrastructures. While this may seem like a reactive strategy, applying patches to systems, servers, and networks as soon as they’re available lowers the number of flaws and the exploits that target them. Accordingly, organizations should also factor critical/high severity vulnerabilities as well as those with a public POC and/or are being actively exploited in-the-wild into their patch management policies as well as incident response and remediation strategies.
- Secure the email gateways, servers, and networks. Attacks can take the form of threats that may target different parts of an organization’s online infrastructure — either to facilitate the execution of malware, deliver payloads, or perform lateral movement — which is why it’s important to secure them equally.
- Enforce the principle of least privilege. Many threats abuse legitimate and open-source penetration testing and system administration tools to successfully exploit a vulnerability. Restricting and securing their use helps reduce the risks of attackers gaining access to the entire network or system.
- Nurture and practice cybersecurity hygiene. Fostering a culture of cybersecurity, which includes increasing user awareness on phishing attacks, helps just as much as the security solutions that are deployed by the organization.
- Employ multilayered security defenses. Additional layers of security reduce an organization’s attack surface. Firewalls and intrusion detection and prevention systems, for instance, help filter malicious traffic and network activities. Application control and behavior monitoring prevents dubious executables and malware-related routines from running, while sandboxes quarantine suspicious and malicious files.
Here’s how virtual patching augments an organization’s existing security technologies as well as vulnerability and patch management policies:
- Buys additional time so security teams can assess the vulnerability, test and apply the necessary patches. For in-house applications, virtual patching provides time for developers and programmers to fix flaws in their code.
- Avoids unnecessary downtime by providing enterprises more freedom to enforce their patch management policies on their own schedule. This mitigates the potential revenue loss caused by unplanned or superfluous disruptions in business operations.
- Improves regulatory compliance by helping organizations meet timeliness requirements, such as those imposed by the EU General Data Protection Regulation (GDPR) and Payment Card Industry (PCI).
- Provides an additional layer of security controls to components in the IT infrastructures for which patches are no longer issued (e.g., legacy systems and end-of-support OSs like Windows Server 2008) or are prohibitively costly to patch.
- Provides flexibility by reducing the need to roll out workarounds or emergency patches. It eases the task, for instance, of gauging specific points in the network that require patching (or if a patch needs to be applied to all systems).
Trend Micro provides comprehensive security solutions for businesses of all size and industries, no matter where they are in their digital transformation journey and include a virtual patch feature.
Cloud One Workload Security enhances runtime protection for cloud-based workloads. To shield users’ information from being stolen, Apex One offers automatic, insightful, all-in-one endpoint security. TippingPoint Threat Protection System with NGIPS defends the network against known, unknown, and undisclosed vulnerabilities. For small and medium businesses, Worry-Free Services Suites offers simple and complete protection for your endpoints and beyond. Each of these solutions offer a virtual patching feature that can shield an organization from exploits of vulnerabilities without the need of the vendor patch. And our TippingPoint customers had the added benefit of being shielded on average 81 days ahead of the vendor patch for vulnerabilities submitted to our Zero Day Initiative in 2020. With 15 research centers across the globe, Trend Micro Research provides customers with the latest insights on the cybersecurity landscape.
To learn more about how Trend Micro can protect your business from vulnerabilities, please visit: https://www.trendmicro.com/en_us/business/products/network/intrusion-prevention/threat-intelligence.html.

