Mobile
Fake Apps Read SMS Codes to Trigger WAP, Carrier Bill
We found an app named “Yellow Camera” disguised as a photo editing app. It reads SMS codes to activate a Wireless Application Protocol (WAP), targeting users in Southeast Asia but may expand as it also targets Chinese-speaking users.
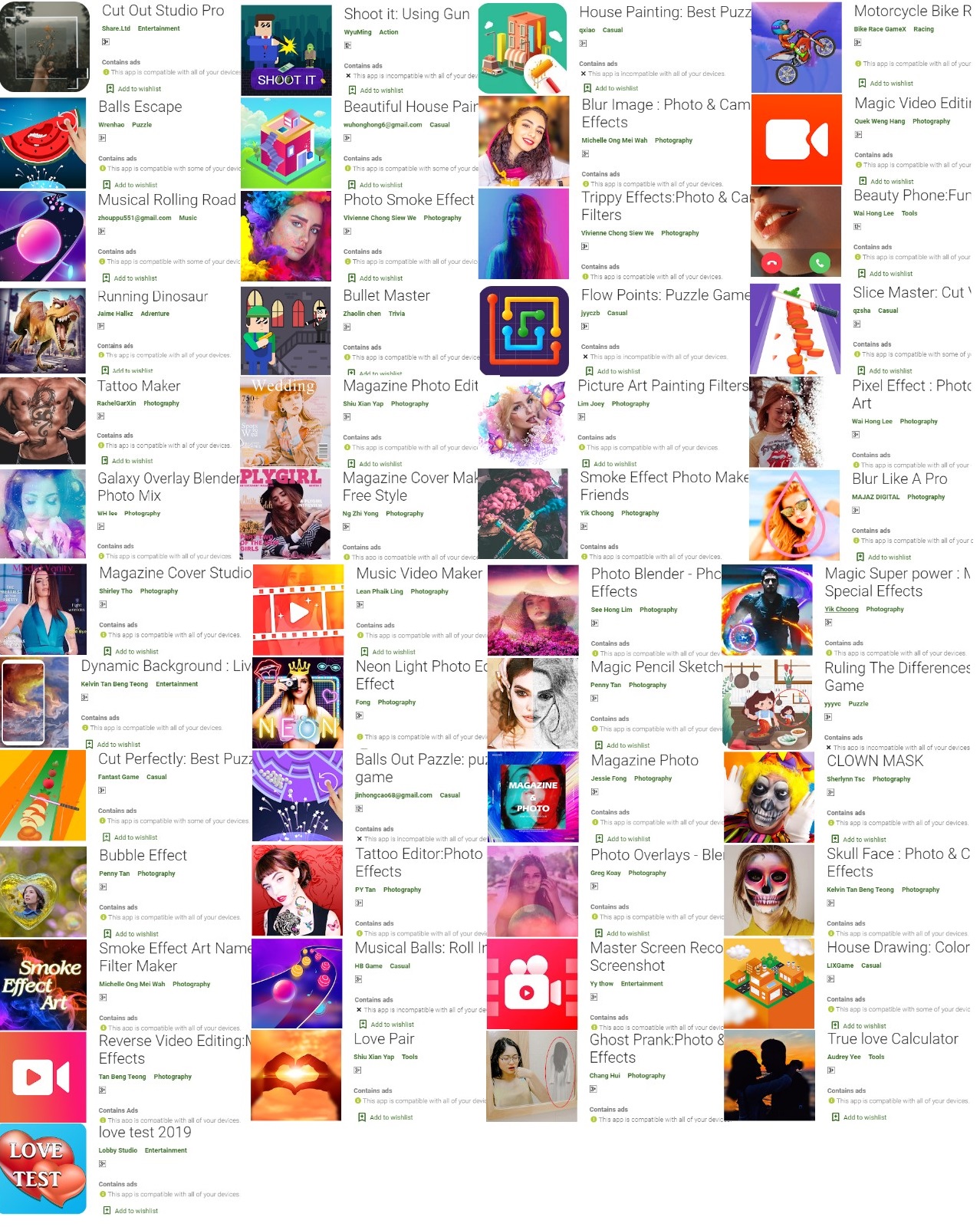
We recently found 49 new adware apps on Google Play, disguised as games and stylized cameras. These apps are typical adware, hiding themselves within mobile devices to show ads and deploying anti-uninstall and evasion functions. These apps are no longer live but before they were taken down by Google, the total number of downloads was more than 3 million.
This recent incident continues an ongoing trend of mobile adware surges — just last August we discovered 85 fake photography and gaming adware apps that also employed unique techniques to evade detection. These adware apps have been a long-running issue for mobile companies. Google needs to remove wave after wave — before the August batch of adware apps, there had also been over 100 adware apps found in July and adware that affected over 9 million users in January. We have been closely following mobile adware fraud for years and found these types of apps also quite prevalent in 2018. New versions are still constantly being uploaded, and we continue to monitor their progress.
Figure 1. Adware apps on Google Play
Behavior analysis
Similar to our previous disclosures, these latest apps disguise their icons and push full-screen ads onto a victim’s device. The user cannot use the usual methods to exit the ad — it can only be closed by clicking the back or home key.
Figure 2. Screen captures of codes showing how the malicious app’s icon is hidden or removed
Figure 3. Screenshots showing the full-screen advertisements
It is clear that these apps are equipped with several effective evasion tactics. They try to dodge the static and dynamic analysis of security solutions via these techniques:
- Code is heavily obfuscated. (Figure 4)
- Strings are not only encoded by base64 but also encrypted with custom algorithms with the package name as key. (Figure 5)
- The adware shortcut is disguised as a popular default browser and uses the same icon as the default browser. However, when clicked, it actually opens an ad page and creates many shortcuts to pollute the home screen. (Figures 6, 7, 8)
- It takes a different action with higher and lower OS versions, particularly in creating shortcuts. (Figure 10) This is probably because after the release of Android OS 8.0, Google tightened the permissions of shortcuts. The user has to give consent, otherwise the app can’t create a shortcut. (Figure 11)
- The adware is kept alive with the StartForgroundService function (deployed after Android OS 8.0). It registers itself as a foreground service, meaning it can run even if the user is not interacting with it. This also lowers its chances of being killed when memory is low. Based on this action, we can say that the adware evolves all the time, always adapting to new OS features and updates.
- There is an extended delay time to trigger malicious actions.
Figure 4. Code obfuscation
Figure 5. Screen captures of code showing encryption with custom algorithms with the package name as key (left) and no encryption in lower version (right)
Figure 6. Screen captures of code showing the list of common default browsers
Figure 7. Screenshot showing the app can create duplicate shortcuts
As mentioned, the adware app will create many duplicate shortcuts of the browser icon. For example, it opens a blank web page when the fake Chrome icon is clicked, and then the page gets refreshed into a full-screen ad.
After seeing the full-screen ad, the user may try to click ‘Recent Screen’ button to check where it came from or close the ad. But there is no information displayed and no clue about where the ad came from. This tactic can help the adware disguise itself. Also, the adware icon itself has been hidden from the user, making it difficult to locate and uninstall the app.
Figure 8. Screenshots showing duplicate shortcuts disguised as Chrome browsers (left), a full-screen ad that opens up after clicking a fake icon (center), and the ‘Recent Screen’ section where there is simply a blank display (right)
The adware makers use the new setTaskDescription(...) method in the Activity class. It can be used to set the display of the title of the task and the icon of the task in the ‘Recent Screen’ section. For this particular adware, it set the title and icon to invisible. As shown in Figure 8 (right), when the ‘Recent Screen’ button is clicked, there is simply a black bar with no page shown.
Figure 9. Screenshot showing how the title is set to empty and the icon to invisible
Figure 10. Code showing different actions for higher and lower OS versions
Figure 11. A request to the user to create a shortcut on Android OS 8.0
The adware’s code also provides a maximum show count and also sets an interval time for when ads appear on a user’s phone.
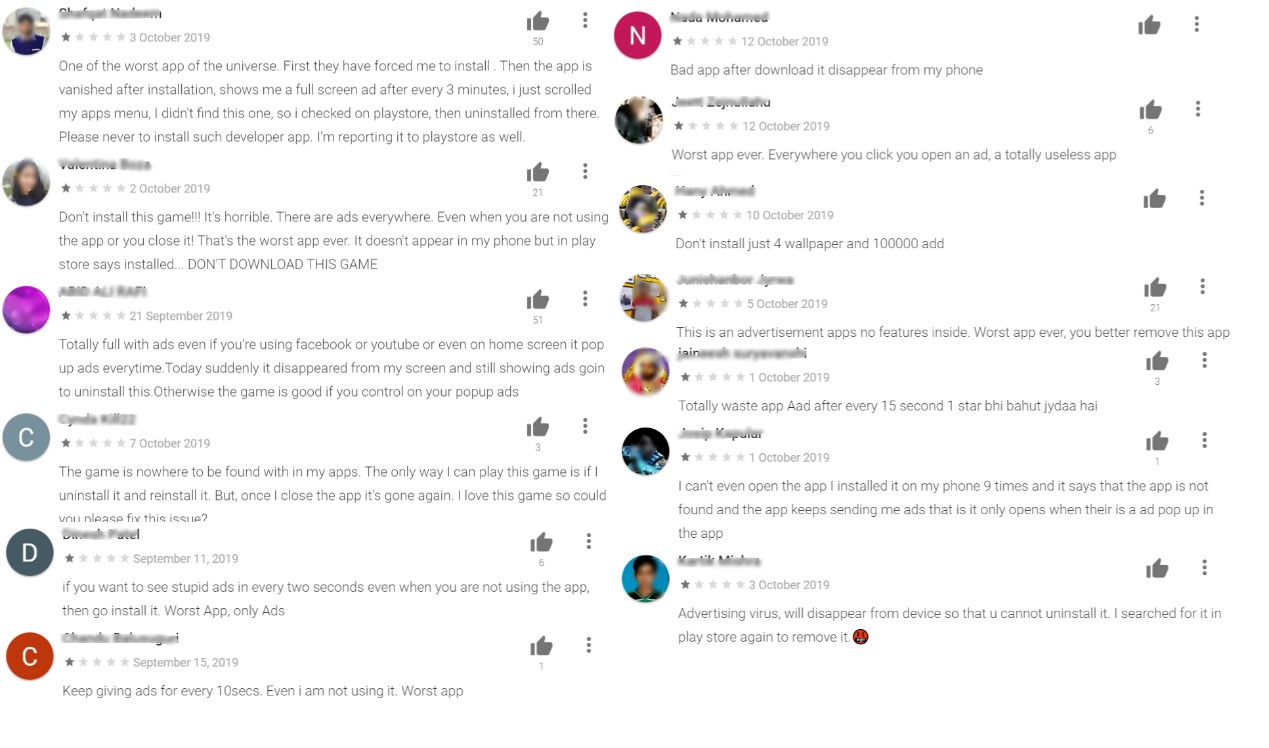
From the many Google Play reviews, we found different behaviors reported: full-screen ads pop up every several minutes; ads pop up when users click anywhere on the screen; ads show whenever the user unlocks an infected phone's screen (the OS will send the notification “android.intent.action.USER_PRESENT” to the app and it will show the ad).
Figure 12. Screen capture of Google Play reviews describing the behavior of the adware-loaded apps
This kind of behavior is not simply an annoyance to users. The continuous display of ads popping up will consume the battery of the phone, which is an issue that has been around for years. And it will also affect the memory: Since the running process is considered a foreground service, the system sees it as something the user is actively aware of and will not terminate it even if the device is low on memory. It is also problematic because the app is difficult to uninstall, using evasive techniques to hide itself from users. Deleting the fake browser shortcuts seen on the screen will not delete the app; instead, the user has to go to the phone settings and find the app in the applications section to uninstall it.
Solutions and security recommendations
Luckily, manufacturers are well aware of the adware nuisance and are constantly installing new fixes to help users avoid these apps. As noted above, Android OS 8.0 and later versions require user consent before installing shortcuts. Users should always keep their software and OS updated so that they can benefit from the latest security solutions from software companies; and they should also adopt best practices when securing mobile devices. App reviews are also a good indicator of quality — they can help raise red flags for suspicious behaviors.
Users can also benefit from security solutions that can thwart stealthy adware, such as the Trend Micro™ Mobile Security™ solution, which blocks malicious apps. End users can also benefit from its multilayered security capabilities that secure the device owner’s data and privacy and safeguards them from ransomware, fraudulent websites, and identity theft.
For organizations, the Trend Micro Mobile Security for Enterprise suite provides device, compliance, and application management, data protection, and configuration provisioning. It also protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps, and detects and blocks malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
The indicators of compromise (IoCs) are in this appendix.
MITRE ATT&CK techniques
| Tactic | Technique | ID | Description |
| Initial Access | Deliver Malicious App via Authorized App Store | T1475 | Used to upload malware to Google Play store |
| Persistence | App Auto-Start at Device Boot | T1402 | Used to listen for the BOOT_COMPLETED broadcast |
| Defense Evasion | Obfuscated Files or Information | T1406 | Used to evade many app vetting techniques, then deobfuscate or decrypt the code at runtime |
| Defense Evasion | Suppress Application Icon | T1508 | Used to suppress its icon from being displayed to the user in the application launcher to hide the fact that it is installed |
| Impact | Generate Fraudulent Advertising Revenue | T1472 | Used to generate revenue by showing non-closeable ads |
| Command and Control | Standard Application Layer Protocol | T1437 | Used to communicate with remote C2 server |