Mobile
Mobile Campaign ‘Bouncing Golf’ Affects Middle East
We uncovered a cyberespionage campaign targeting Middle Eastern countries. We named this campaign “Bouncing Golf” based on the malware’s code in the package named “golf.”
We uncovered a cyberespionage campaign targeting Middle Eastern countries. We named this campaign “Bouncing Golf” based on the malware’s code in the package named “golf.” The malware involved, which Trend Micro detects as AndroidOS_GolfSpy.HRX, is notable for its wide range of cyberespionage capabilities. Malicious codes are embedded in apps that the operators repackaged from legitimate applications. Monitoring the command and control (C&C) servers used by Bouncing Golf, we’ve so far observed more than 660 Android devices infected with GolfSpy. Much of the information being stolen appear to be military-related.
The campaign’s attack vector is also interesting. These repackaged, malware-laden apps are neither on Google Play nor popular third-party app marketplaces, and we only saw the website hosting the malicious apps being promoted on social media when we followed GolfSpy’s trail. We were also able to analyze some GolfSpy samples sourced from the Trend Micro mobile app reputation service.
Also of note is Bouncing Golf’s possible connection to a previously reported mobile cyberespionage campaign that researchers named Domestic Kitten. The strings of code, for one, are similarly structured. The data targeted for theft also have similar formats.
 Figure 1. GolfSpy’s infection chain
Figure 1. GolfSpy’s infection chain
GolfSpy's Potential Impact
Given GolfSpy’s information-stealing capabilities, this malware can effectively hijack an infected Android device. Here is a list of information that GolfSpy steals:
- Device accounts
- List of applications installed in the device
- Device’s current running processes
- Battery status
- Bookmarks/Histories of the device’s default browser
- Call logs and records
- Clipboard contents
- Contacts, including those in VCard format
- Mobile operator information
- Files stored on SDcard
- Device location
- List of image, audio, and video files stored on the device
- Storage and memory information
- Connection information
- Sensor information
- SMS messages
- Pictures
GolfSpy also has a function that lets it connect to a remote server to fetch and perform commands, including: searching for, listing, deleting, and renaming files as well as downloading a file into and retrieving a file from the device; taking screenshots; installing other application packages (APK); recording audio and video; and updating the malware.
Technical Analysis
The repackaged applications are embedded with malicious code, which can be found in the com.golf package. These repackaged apps pose as communication, news, lifestyle, book, and reference apps popularly used in the Middle East. The GolfSpy malware embedded in the apps is hardcoded with an internal name used by the attacker.
Figure 2. Icons of the apps that Bouncing Golf’s operators repackaged (top) and a comparison of packages between the original legitimate app (bottom left) and GolfSpy (bottom right)
 Figure 3. GolfSpy’s configurations encoded by a custom algorithm (right) and its decoded version (left)
Figure 3. GolfSpy’s configurations encoded by a custom algorithm (right) and its decoded version (left)
As shown in Figure 3, GolfSpy’s configurations (e.g., C&C server, secret keys) are encoded by a customized algorithm. After it is launched, GolfSpy will generate a unique ID for the affected device and then collect its data such as SMS, contact list, location, and accounts in this format: “%,[],time”(shown in Figure 4). The information is written into a file on the device. The attacker can choose the data types to collect, which are written in a certain format.
Figure 4. Code snippet showing GolfSpy generating UUID
The value of % is in the range of 1-9 or a-j. Each value represents a different type of data to steal from the device:
| Value | Data Type |
| 1 | Accounts |
| 2 | Installed APP list |
| 3 | Running processes list |
| 4 | Battery status |
| 5 | Browser bookmarks and histories |
| 6 | Call logs |
| 7 | Clipboard |
| 8 | Contacts |
| 9 | Mobile operator information |
| a | File list on SD card |
| b | Location |
| c | Image list |
| d | Audio list |
| e | Video list |
| f | Storage and memory information |
| g | Connection information |
| h | Sensors information |
| i | SMS messages |
| j | VCard format contacts |
Table 1. The type of data corresponding to the value coded in GolfSpy
Figure 5 shows the code snippets that are involved in monitoring and recording the device’s phone call. It will also take a photo using the device’s front camera when the user wakes the device.
Apart from collecting the above data, the spyware monitors users’ phone calls, records them, and saves the recorded file on the device. GolfSpy encrypts all the stolen data using a simple XOR operation with a pre-configured key before sending it to the C&C server using the HTTP POST method.
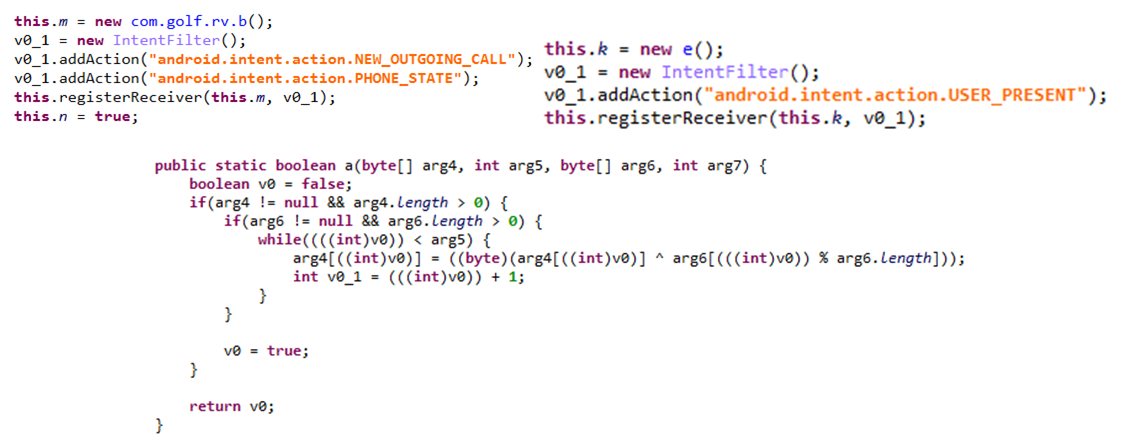 Figure 5. Code snippets showing how GolfSpy monitors phone calls via register receiver (top left), its actions when the device is woken up (top right), and how it encrypts the stolen data (bottom)
Figure 5. Code snippets showing how GolfSpy monitors phone calls via register receiver (top left), its actions when the device is woken up (top right), and how it encrypts the stolen data (bottom)
The malware retrieves commands from the C&C server via HTTP, and attackers can steal specific files on the infected device. The command is a constructed string split into three parts using "<DEL>" as a separator. The first part is the target directory, the second is a regular expression used to match specific files, while the last part is an ID.
 Figure 6. Example of a command that steals specific files from an infected device’s application (top), and GolfSpy’s parse-and-perform command (bottom)
Figure 6. Example of a command that steals specific files from an infected device’s application (top), and GolfSpy’s parse-and-perform command (bottom)
Apart from the HTTP POST method, GolfSpy also creates a socket connection to the remote C&C server in order to receive and perform additional commands. Stolen data will also be encrypted and sent to the C&C server via the socket connection. The encryption key is different from the one used for sending stolen data via HTTP.
 Figure 7. The additional commands that attackers can carry out via a socket connection (top) and the key used to encrypt the stolen data (bottom)
Figure 7. The additional commands that attackers can carry out via a socket connection (top) and the key used to encrypt the stolen data (bottom)
Correlating Bouncing Golf's Activities
We monitored Bouncing Golf’s C&C-related activities and saw that the campaign has affected more than 660 devices as of this writing. The small or limited number is understandable given the nature of this campaign, but we also expect it to increase or even diversify in terms of distribution. Most of the affected devices were located in the Middle East, and many of the stolen data we saw is military-related (e.g., images, documents).
Bouncing Golf’s operators also try to cover their tracks. The registrant contact details of the C&C domains used in the campaign, for instance, were masked. The C&C server IP addresses used also appear to be disparate, as they were located in many European countries like Russia, France, Holland, and Germany.
It’s not a definite correlation, but Bouncing Golf also seems to have a connection with Domestic Kitten due to similarities we found in their code. For example, the Android malware that both deploy share the same strings of code for their decoding algorithm. The data that Domestic Kitten steals follows a similar format with Bouncing Golf’s, with each type of data having a unique identifying character. It’s also worth noting that both campaigns repackage apps that are commonly used in their target’s countries, such as Telegram, Kik, and Plus messaging apps.
 Figure 8. Code snippets showing: the decoding algorithm shared by both Bouncing Golf and Domestic Kitten (top), the format of data that Domestic Kitten’s malware targets to steal (center), and how both Bouncing Golf (bottom left) and Domestic Kitten (bottom right) use "<DEL>" as a separator in their command strings.
Figure 8. Code snippets showing: the decoding algorithm shared by both Bouncing Golf and Domestic Kitten (top), the format of data that Domestic Kitten’s malware targets to steal (center), and how both Bouncing Golf (bottom left) and Domestic Kitten (bottom right) use "<DEL>" as a separator in their command strings.
As we’ve seen in last year’s mobile threat landscape, we expect more cyberespionage campaigns targeting the mobile platform given its ubiquity, employing tried-and-tested techniques to lure unwitting users. The extent of information that these kinds of threats can steal is also significant, as it lets attackers virtually take over a compromised device. Users should adopt best practices, while organizations should ensure that they balance the need for mobility and the importance of security.
End users and enterprises can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security™ . Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that exploit vulnerabilities, preventing unauthorized access to apps, and detecting and blocking malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies, protecting devices against malware, zero-day and known exploits, privacy leaks, and application vulnerabilities.
A list of indicators of compromise (IoCs) is in this appendix.





