Spam
New File Types Emerge in Malware Spam Attachments
Cybercriminals make use of old file types in brand-new ways in spam attachments, proving that they are regularly experimenting to evade spam filters.
As cybersecurity defenses continue to improve, cybercriminals have learned to become more creative with malware. We recently encountered threats being packaged inside old yet rarely used file types in spam campaigns. Spam continues to be a cybercriminal favorite – this old-school infection vector makes up more than 48 percent of all email traffic worldwide.
In our annual roundup report for 2017, we found that the most common file types used in malware-related spam campaigns are .XLS, .PDF, .JS, .VBS, .DOCX, .DOC, .WSF, .XLSX, .EXE, and .HTML. In August, we also reported about .EGG files delivering GandCrab v4.3 ransomware. But cybercriminals are expanding the file types they abuse. The following details how cybercriminals make use of old file types in brand-new ways, proving that they are regularly experimenting to evade spam filters.
.ARJ and .Z files
ARJ, which stands for “Archived by Robert Jung,” is a file archiver that emerged in the ‘90s just like the .ZIP, but did not receive the same level of popularity as the latter. Though the .ARJ file extension has been used to send malicious files via spam in 2014, we saw a recent spike in the use of .ARJ files to deliver malicious files to users. Recently, we saw close to 7,000 hits of malicious files compressed in ARJ detected in the Trend Micro™ Smart Protection Network™.
Figure 1. Infection chain of a spam campaign with a malicious .ARJ file attachment

Figure 2. A screen capture of a spam email with an .ARJ file attachment
We recently found a small spam campaign that distributes malicious .ARJ files. Several of these spam emails have email subjects pertaining to statements or purchase orders, such as “STATEMENT OF OUTSTANDING BALANCE AS YOUR REFERENCE,” “New Order-Snam Thai Son Group//PO//Ref 456789,” and “SUBJECT:Advice from Standard Chartered Bank,” to name a few.
After the malicious .ARJ file has been downloaded to a device, it may drop and execute a plain executable file or an executable screensaver file.

Figure 3. A screen capture of the contents of a .Z file
Back in 2014, once successfully unpacked in a system, a spam campaign with an .ARJ file attachment will turn an infected computer as part of a botnet that can be used for spam or denial-of-service attacks. This year, the payload is a spyware (detected by Trend Micro as TROJANSPY.WIN32.GOLROTED.THAOOEAH) that steals system information as well as usernames and passwords from browsers. This malware also attempts to steal stored email credentials from several email service platforms.
Cybercriminals also use .Z files maliciously. .Z file extensions are compressed Unix-based machine files, though it has been outshined by the GNU Gzip compression in terms of popularity among users. Because it appears to have a double file extension (such as .PDF.z), users may be tricked into thinking that they're opening a PDF instead of a .Z file.

Figure 4. A screen capture of a fake purchase order with a .Z file extension as an attachment
Like the .ARJ file, the archive file may contain a plain .exe file and an executable screensaver file.
We saw a spam campaign with a .Z file attachment that bears a backdoor payload (detected by Trend Micro as BACKDOOR.WIN32.REMCOS.TICOGBZ) that can open, rename, upload and delete files in an affected computer, log keystrokes, and even capture images and voice using the computer’s camera and mic. Security researchers have also found a spam campaign that sends the DarkComet RAT via a .Z file attachment to potential victims earlier this year.
.PDF Files
The use of .PDF files to distribute malware is not something new. In fact, we saw a malicious spam campaign that used .PDF files to distribute a downloader and a backdoor, targeting financial institutions early this year. With recent innovations in campaigns, cybercriminals seem eager to use known successful techniques in their code. Recently, we saw cybercriminals embedding .IQY files and .PUB files inside .PDF attachments.
Upon download, the malicious .IQY and .PUB files will be executed using a JavaScript code:


Figure 5. Screen captures of .IQY and .PUB file extensions being executed in JavaScript
This JavaScript code makes use of the exportDataObject function to export and launch the malware, specified by “nLaunch” in this case, while the exported object or file is specified by “cName.” The “nLaunch = 2” function means that the malicious file will be saved in %TEMP% prior to being launched.
Figure 6. Infection chain of malicious campaign using a .PDF file with .PUB embedded inside it
.IQY Files
The use of Internet Query Files (IQY) as an infection vector was made popular by the Necurs spam campaign that abused MS Excel’s Dynamic Data Exchange (DDE) feature to distribute the FlawedAmmyy RAT. Its recent popularity has made the method (.IQY files being used as an infection vector) more common. In this case, the .IQY file was embedded in a .PDF file.
On August 15, 2018, we saw a spam campaign distributing a .PDF with an embedded .IQY file. The Trend Micro™ Smart Protection Network™ (SPN) detected more than 58,000 hits in India alone, while other countries include Vietnam, the United States, China and Germany.
Figure 7. Infection chain of a malicious spam campaign that distributes the Marap trojan by abusing .IQY files embedded inside a .PDF file

Fig. 8. A screen capture of an .IQY file attached to a .PDF used in a spam campaign
We also recently saw .IQY files being abused to deliver BEBLOH or URSNIF malware in Japan.
.PUB
Today’s spam campaigns no longer revolve around the use of malicious macro files inside typical documents, and so cybercriminals continue to raise the ante by using rarely used documents to distribute malware. The wave of malicious spam seen at the end of August used a peculiar Microsoft office application, MS Publisher. Just like in the case of an embedded .IQY file, opening the publisher file causes a malicious macro file inside it to run.
Fig. 9. A screen capture of a code showing a .PUB file with malicious macro inside
On August 21, 2018, we received SPN feedback pertaining to a spam campaign that distributes a .PDF attachment embedded with a malicious .PUB file. Majority of our detections were seen to hit India, comprising more than 73% of detections, followed by United Kingdom at 11%. A few spam emails from this campaign were also found in Vietnam, Taiwan, China, Turkey and the United States.
SettingContent-ms
The release of the new file type called SettingContent-ms came with the release of Windows 10. This file normally contains setting content for Windows functions and mostly used to create shortcuts to the old Windows Control Panel. Cybercriminals did not take too long to exploit this function and embedded it to Microsoft office applications. Spam campaigns in early July showed that cybercriminals distributed the FlawedAmmyy remote access Trojan (RAT) inside a malicious SettingContent-ms file embedded in a PDF document.
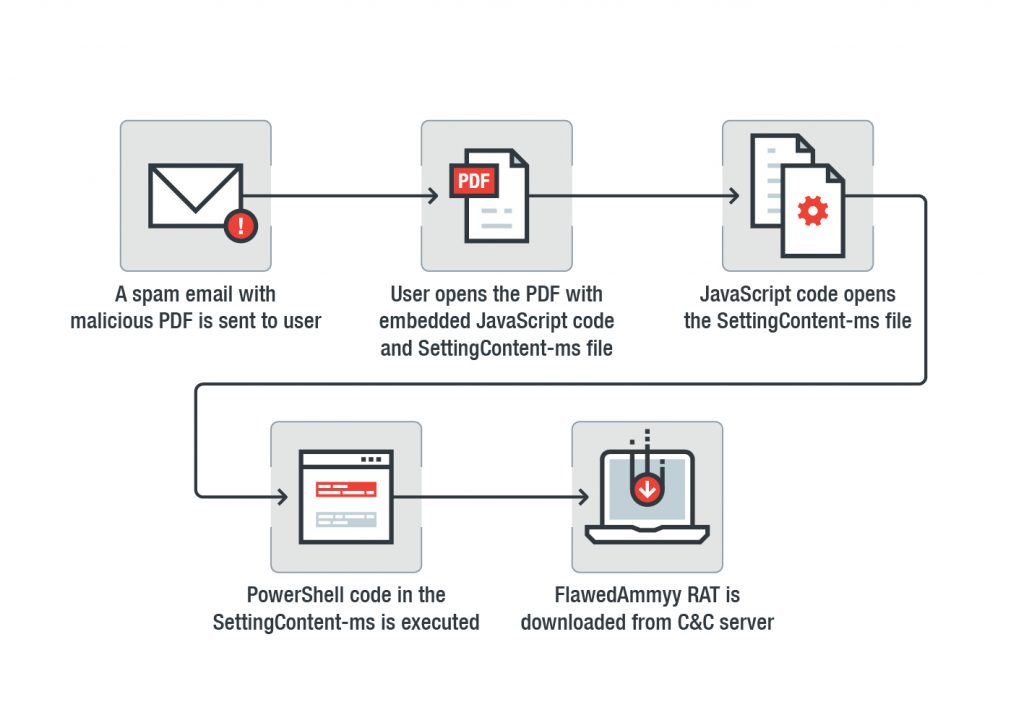 Figure 10. Infection chain of a malicious spam campaign that distributes the FlawedAmmyy RAT using a malicious .PDF embedded with JavaScript code and SettingContent-ms file
Figure 10. Infection chain of a malicious spam campaign that distributes the FlawedAmmyy RAT using a malicious .PDF embedded with JavaScript code and SettingContent-ms file
Recently, a spam campaign and a proof of concept research has shown how SettingContent-ms files can be abused by replacing the command line under the DeepLink tag with a malicious file.
Defending against ever-evolving malware in spam campaigns
The threat landscape is evolving and cyber foes are becoming more inventive, using previously or rarely seen file types to distribute malware to unsuspecting users. While certain cybersecurity solutions may not always be able to provide prompt protection, a multilayered approach to threat defense can more effectively detect and defend endpoints and systems from malware at different levels of each spam campaign.
Trend Micro’s holistic approach to cybersecurity is evidenced by its use of strong traditional and forward-facing technologies in its products. The Trend Micro™ Anti-Spam Engine (TMASE) ™ and Email Security™, which have integrated machine learning as well as defensive traditional cybersecurity technologies, block all email-based threats on the network-level. As spam email numbers continue to rise by the day, security solutions that are able to block them off swiftly and accurately are essential to keeping businesses running.
Meanwhile, the Trend Micro™ Web Reputation Service (WRS)™ protects customers from visiting compromised websites that are running possibly malicious code. Hence, executables that would need to communicate to a C&C server to download malicious files will not have the chance to get downloaded.
Cybercriminals put their time and resources to try and defeat cybersecurity defenses by changing the game – and the face of spam campaigns. And cybersecurity defenses need to always be ahead of the game, guarding against threats on various stages, to keep users safe from online dangers and allow businesses to function smoothly and efficiently.
Indicators of Compromise
- a22ede52f14be480dd478fa0ec955b807e4b91a14fbe1b5d46c07bbb5cacccbb - .Z file attachment
- d5f4d2def36c54cd404742fe40583fa5805e55aa687063f9cd92bfd7378f7dc4 - .ARJ file attachment
- dd45ab22c16b843a8755f859103f4509fcbbd2da5d837e622cb37a16e53c8cc3 - .PDF with PUB attachment
- 38066350f0ad3edfa2ccf534f51ad528b8bac6e8f1a2a5450556a33fdf345109 - .PUB
- eeae4955354e07e0df2c5ca3bdc830f6758c11ba185511ef4b3d82a9c1253e63 - Payload (BKDR_FLAWEDAMMYY.EB)
- b2b2ec71154a551b1af2cfc1611a6ed59821917c0c930ea6f737c586ecdfa147 - .PDF with IQY attachment
- 3fd386172636a5c5b471d89c23e4d24cc36d42c90975245ab1a6525e7895fc57 - IQY
- 996053ee305ee730f4095d9ee71447dd72815083c8cdf98e048f41185cf2b1d1 - payload

