We were able to observe a series of network attacks exploiting CVE-2018-7602, a security flaw in the Drupal content management framework. For now, these attacks aim to turn affected systems into Monero-mining bots. Of note are its ways of hiding behind the Tor network to elude detection and how it checks the affected system first before infecting it with a cryptocurrency-mining malware. While these attacks currently deliver resource-stealing and system performance-slowing malware, the vulnerability can be used as a doorway to other threats.
What is CVE-2018-7602?
CVE-2018-7602 is a remote code execution (RCE) vulnerability affecting Drupal’s versions 7 and 8, which was patched on April 25, 2018. The security flaw was discovered after Drupal’s security team looked into another vulnerability, CVE-2018-7600 (also known as Drupalgeddon 2, patched on March 28, 2018). Drupal’s security team also reported that CVE-2018-7602 is being actively exploited in the wild. According to a researcher's technical analysis, successfully exploiting the vulnerability entails elevating the permission to modify or delete the content of a Drupal-run site.
How does the exploit lead to the Monero miner?
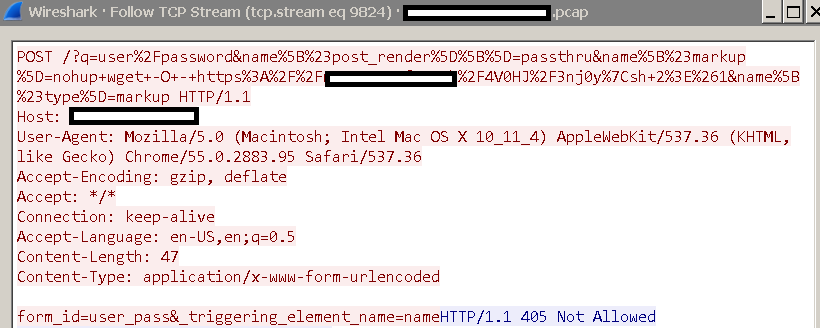
As shown in Figures 1 and 2, the attacks we’ve seen exploiting CVE-2018-7602 download a shell script, which will then retrieve an Executable and Linkable Format-based (ELF) downloader (detected by Trend Micro as ELF_DLOADR.DHG). As shown in Figure 3, the downloader will add a crontab entry (which, in Unix-based systems, contain commands to be executed) to automatically update itself. In this case, the command is to check the link from which it downloads and interprets a script named up.jpg posing as a JPEG file. The ELF-based downloader also retrieves a Monero-mining malware (COINMINER_TOOLXMR.O-ELF64) and installs it on the affected machine.
Figure 1: Code snippet showing how CVE-2018-7602 is exploited
 Figure 2: Code snippet showing how the shell script is retrieved
Figure 2: Code snippet showing how the shell script is retrieved
Figure 3: A crontab entry added by the malware to auto-update itself
What makes these attacks notable?
The downloader employs the HTTP 1.0 POST method to send data back in SEND_DATA() function. The target path for the POST method is /drupal/df.php. HTTP 1.0 traffic is quite uncommon in these kinds of attacks, as most of the HTTP traffic by many organizations is already in HTTP 1.1 or later. And given this seeming variance, we foresee this as a pattern in future attacks.
Figure 4: The assembly codes of the SEND_DATA() function of the downloader
The Monero miner installed in the machine is the open-source XMRig (version 2.6.3). It also checks if the machine is to be compromised or not. When the miner starts to run, it changes its process name to [^$I$^] and accesses the file /tmp/dvir.pid. Figure 6 shows this furtive behavior, which the attacker/operator added in their modified version of XMRig. This is a red flag that administrators or information security professionals can take into account to discern malicious activities, such as when deploying host-based intrusion detection and prevention systems or performing forensics.
Figure 5: A part of XMRig included in the cryptocurrency-mining malware
 Figure 6: The reversed pseudo codes of the Monero-miner's main() function
Figure 6: The reversed pseudo codes of the Monero-miner's main() function
Where are these attacks coming from?
The attacks are notable for the precautions they took in that they hide behind the Tor network. We were able to follow the malware’s trail to 197[.]231[.]221[.]211. Based on WhoIs information, the IP segment 197[.]231[.]221[.]0[/]24 appears to belong to a virtual private network (VPN) provider. Additionally, we found that the IP address is a Tor exit node — gateways from where encrypted Tor traffic is passed to normal internet traffic.
In fact, Trend Micro has blocked 810 attacks in the past month coming from this IP address. Given that it’s a Tor exit node, we are not certain if these attacks are related to the Monero-mining payload or are from a single threat actor. The bulk of attacks from this IP address exploit Heartbleed (CVE-2014-0160). The other attacks we observed exploited ShellShock (CVE-2014-6271), an information disclosure vulnerability in WEB GoAhead (CVE-2017-5674), and a memory leak flaw in Apache (CVE-2004-0113). Trend Micro also blocked File Transfer Protocol (FTP) and Secure Shell (SSH) brute-force logins from this IP address. Note that these attacks exploit even old Linux or Unix-based vulnerabilities, underscoring the importance of defense in depth. This is particularly true for enterprises whose web applications and sites — like those that use Drupal — manage sensitive data and transactions. Even a security flaw dating as far back as 2014 can be used as an entry point for attackers.
 Figure 7: TOR exit node information (2018/06/16) for 197[.]231[.]221[.]211
Figure 7: TOR exit node information (2018/06/16) for 197[.]231[.]221[.]211
Defending against this threat
Patching and updating the Drupal core fixes the vulnerability that this threat exploits. Drupal’s security bulletin provides guidelines on fixing the vulnerability, especially for those that still use unsupported versions of Drupal. Developers, as well as system administrators and information security professionals, should also practice security by design: securing the applications from which personal and corporate data are stored and managed while also ensuring their ease of use and functionality.
A single vulnerability in a website or application could cause a data breach or outage. Organizations can further thwart threats like this through defense in depth: enforcing the principle of least privilege and adding multiple security layers, such as virtual patching, firewalls, intrusion detection and prevention systems, as well as application control and behavior monitoring.
Trend Micro Solutions
A proactive, multilayered approach to security is key against threats that exploit vulnerabilities — from the gateway, endpoints, networks, and servers. Trend Micro Deep Security and Trend Micro™ Vulnerability Protection also provide virtual patching that protects servers and endpoints from threats that abuse vulnerabilities in critical applications or websites such as those that use Drupal. Trend Micro™ OfficeScan™ with XGen™ endpoint security has Vulnerability Protection that shields endpoints from identified and unknown vulnerability exploits even before patches are even deployed. Trend Micro™ Smart Protection Suites and Worry-Free™ Business Security protect end users and businesses from these threats by detecting and blocking malicious files and all related malicious URLs.
The Trend Micro™ Smart Home Network solution protects customers via these DPI rules:
- 1134569 – WEB Drupal Core Form Rendering Remote Code Execution -1.1 (CVE-2018-7600)
- 1134571 – WEB Drupal Core Form Rendering Remote Code Execution -1.2 (CVE-2018-7600)
- 1134572 – WEB Drupal Core Form Rendering Remote Code Execution -1.3 (CVE-2018-7600)
- 1134790 – WEB Drupal Core drupalgeddon3 Authenticated Remote Code Execution -2 (CVE-2018-7602)
The Trend Micro Deep Security and Trend Micro™ Vulnerability Protection solutions protect user systems from any threats that may target the vulnerabilities mentioned above via the following DPI rule 1009054 – Drupal Core Remote Code Execution Vulnerability (CVE-2018-7602).
Indicators of Compromise (IoCs)
Related hashes (SHA-256): Detected as ELF_DLOADR.DHG:
- a1d8bfc17bf395742e4c8a81ca0ba352b998c1590ac2fb014aa23671b2ee6302
- 01147a014378711ee299de7b37ac0a262a1ac22011a510bdf9ad0c93695827b
Detected as COINMINER_TOOLXMR.O-ELF64:
- 89cdf303dc94e56dacc4e894d44c54845e4658a0dc5b32d50b0650a67f92d5b3