Using a machine learning system, we analyzed 3 million software downloads, involving hundreds of thousands of internet-connected machines, and provide insights in this three-part blog series. In the first part of this series, we took a closer look at unpopular software downloads and the risks they pose to organizations. We also briefly mentioned the problem regarding code signing abuse, which we will elaborate on in this post.
Code signing is the practice of cryptographically signing software with the intent of giving the operating system (like Windows) an efficient and precise way to discriminate between a legitimate application (like an installer for Microsoft Office) and malicious software. All modern operating systems and browsers automatically verify signatures by means of the concept of a certificate chain.
Valid certificates are issued or signed by trusted certification authorities (CAs), which are backed up by parent CAs. This mechanism relies entirely and strictly on the concept of trust. We assume that malware operators are, by definition, untrustworthy entities. Supposedly, these untrustworthy entities have no access to valid certificates. However, our analysis shows that is not the case.
There is an entire market supporting the operations of malware operators that have gained access to valid certificates that are then used in signing malicious software. In our analysis, we observed a large number of malicious software that have been signed by trusted authorities — bypassing any client-side validation mechanisms built in recent OSs and browsers.
| Type | Number of software | Signed (overall downloads) | Number of software | Signed (browser-only downloads) |
|---|---|---|---|---|
| Trojan | 22,413 | 59.9% | 12,827 | 81.3% |
| Dropper | 43,423 | 85.6% | 33,820 | 95.4% |
| Ransomware | 563 | 44.4% | 313 | 68.7% |
| Bot | 1,092 | 1.5% | 268 | 2.2% |
| Worm | 201 | 5.5% | 57 | 12.3% |
| Spyware | 80 | 21.2% | 40 | 25.0% |
| Banker | 1,719 | 1.2% | 272 | 1.8% |
| FakeAV | 987 | 2.8% | 446 | 4.5% |
| Adware | 29,345 | 43.1% | 8,792 | 91.8% |
| PUP | 31,018 | 76.0% | 21,792 | 79.6% |
| Undefined | 60,609 | 65.1% | 42,614 | 71.3% |
| Benign (total) | 43,601 | 30.7% | 30,346 | 32.1% |
| Unknown (total) | 1,626,901 | 38.4% | 1,227,241 | 42.1% |
| Malicious (total) | 191,450 | 66% | 121,241 | 81% |
Table 1. Percentage of signed benign, unknown, and malicious software (with types)
Looking at Table 1, more malicious software appear to be signed than legitimate or benign apps (66% versus 30.7%). This is also true for malware made available via a direct link such as browsers (81% versus 32.1%). This shows that cybercriminals commonly provide software that are signed correctly, therefore running and bypassing code signing validations.
With Table 1 offering a breakdown by malware type, the distribution suggests that malware operators tend to invest more efforts in signing malware that get executed first on a target machine (like droppers and adware, as highlighted in the first part of this series) rather than in more aggressive types of malware, which may take on an already compromised environment. This makes sense from a business standpoint because access to valid code signing is expensive, therefore challenging cybercriminals to strategically use their budget.
| Type | Major signers | Major common signers with benign software |
|---|---|---|
| Trojan | Somoto Ltd., Somoto Israel, RAPIDDOWN | Open Source Developer, Binstall, Rspark LLC |
| Dropper | Somoto Israel, Sevas-S LLC, SecureInstall | Softonic International, RBMF Technologies LLC, Open Source Developer |
| Ransomware | ISBRInstaller, Trusted Software Aps, The Nielsen Company | WorldSetup, UpdateStar GmbH, AppWork GmbH |
| Bot | Benjamin Delpy, Supersoft, Flores Corporation | Nir Sofer |
| Worm | 70166A21-2F6A-4CC0-822C-607696D8F4B7, JumpyApps, Xi’an Xinli Software Technology Co. | None |
| Spyware | R-DATA Sp. z o.o., Mipko OOO, Ts Security System - Seguranca em Sistemas Ltda | Refog Inc., Video Technology, Valery Kuzniatsou |
| Banker | WEBPIC DESENVOLVIMENTO DE SOFTWARE LTDA, JDI BACKUP LIMITED, Wallinson | Open Source Developer, TLAPIA |
| FakeAV | Webcellence Ltd., ISBRInstaller, William Richard John | UpdateStar GmbH, The Phone Support Pvt. Ltd., 2345[.]com |
| Adware | Apps Installer SL, Tuto4PC[.]com, ClientConnect LTD | SITE ON SPOT Ltd., Open Source Developer, Binstall |
| PUP | Somoto Ltd., Amonetize ltd., Firseria | Binstall, SITE ON SPOT Ltd., Perion Network Ltd. |
| Others | ISBRInstaller, JumpyApps, Somoto Israel | Binstall, UpdateStar GmbH, BoomeranGO Inc. |
| Malicious (total) | Somoto Ltd., ISBRInstaller, Somoto Israel | Softonic International, Binstall, SITE ON SPOT Ltd. |
Table 2. Major signers for malicious software
| Benign software | Number |
|---|---|
| TeamViewer | 209 |
| Blizzard Entertainment | 77 |
| Lespeed Technology Ltd. | 71 |
| Hamrick Software | 66 |
| Dell Inc. | 59 |
| Google Inc. | 59 |
| NVIDIA Corporation | 58 |
| Softland S.R.L. | 52 |
| Adobe Systems Incorporated | 48 |
| Recovery Toolbox | 43 |
| Malicious software | Number |
|---|---|
| Somoto Ltd. | 5,652 |
| ISBRInstaller | 5,127 |
| Somoto Israel | 5,062 |
| Apps Installer SL | 5,049 |
| SecureInstall | 2,694 |
| Firseria | 2,474 |
| Amonetize ltd. | 1,932 |
| JumpyApps | 1,896 |
| ClientConnect LTD | 1,761 |
| Media Ingea SL | 1,671 |
Table 3. Major exclusive signers for both benign and malicious software downloads
Table 3 gives a general list of names for both benign and malicious applications, while Table 2 provides a more detailed view on the types of malware. While some signers like Somoto Ltd., ISBRInstaller, and Somoto Israel were generally found as signers in different types of malware, others were found used in more specific types. SecureInstall was found being used by droppers, while Benjamin Delpy was found being used by bots.
While it’s crucial to scrutinize major signers of malicious software, we must also point to the more serious concern of issuers that both sign benign and unwanted/malicious software.
Note: There are reasons why signed certificates exist for both benign and unwanted/malicious software. Either they are stolen or re-sold in the underground, or legitimate organizations offer both benign and questionable applications like PUPs.
Figure 1. Common signers between benign and unwanted/malicious applications
How code signing abuse reflects in the underground
In recent years, notorious cases of code signing abuses have been reported in the wild.
In 2010, StuxNet received huge media attention when it was found using a stolen digital signature from Realtek Semiconductor Corp. to target WinCC supervisory control and data acquisition (SCADA) systems. Realtek is a legitimate global manufacturer of microchips based in Taiwan. When the certificate was revoked, StuxNet started using signatures from JMicron Technology Corp., another Taiwan-based firm specialized in microchip design. Post-mortem analyses suggested that cybercriminals compromised these organizations to steal their development certificates, including the private keys used to sign the executables.
In 2014, following a massive hack against Sony Pictures, samples from a malware campaign called Destover were found signed with valid certificates from Sony. This malware was reportedly used against Sony in attacks that led to the leak of corporate and personal data and the destruction of data on corporate PCs.
CopyKittens, Suckfly, Turla, and Regin were other well-known campaigns that have also successfully used signed certificates for malicious ends.
Problems in validating certificate requests
A general problem that we observed is that CAs — to different extents — fail in properly validating the certificate requests they receive. We don’t know if this is, somehow, voluntary and where the line of responsibility terminates.
While a public key infrastructure (PKI) offers three classes of certificates, with two of them (classes 2 and 3) requiring an extended verification process of the actual organization or business requesting the certificate, we encountered certificates issued to organizations that were easily traceable to cybercrime like malware distribution.
During our investigation, we observed that some of the major CAs involved in this phenomenon are Comodo and Certum. Out of thousands of binaries that were signed with certificates issued by these CAs, roughly 14% (Comodo) and 12% (Certum) of binaries were malicious. These values topped 36% for periods of extensive malware campaigns. There were also a few cases wherein Digicert, Symantec, and Verisign certificates were issued to entities that later used them to sign malware.
Origins of fraudulent certificates
The two most common causes of fraudulent certificates are as follows:
- Stolen certificates: Certificates are stolen from a legitimate organization where there’s been a system compromise from a malware infection.
- Faked certificates: CAs issue certificates to cybercriminals that mimic a legitimate organization. Social engineering techniques are usually employed by the attacker.
Let’s look at some cases that we observed in the wild. One of the biggest Russian financial brokers became the target of cybercriminals using fraudulent certificates for the Razy ransomware. After we contacted the organization, they confirmed that they did not request such a certificate.
Figure 2. Fraudulent certificate used to sign variants of the Razy ransomware
In another case, attackers mimicked an Oracle vendor to acquire two certificates – one was issued as “Oracle America, Inc.” in 2014, while the other was issued as “Oracle Industries” in 2017. The cybercriminals behind these operations signed malicious files like spyware, adware, unwanted browser toolbars, and other PUPs. These binaries were concealed as legitimate Oracle applications. One of the files was named after a Java program.
Figure 3. Malware concealed as a Java application, signed with a certificate from "Oracle America, Inc."
We also found malicious files signed with a certificate from “Handan City Congtai District LiKang Daily Goods Department.” However, the certificate was already revoked, probably because the issuer had taken action in response to a likely data breach or theft.
Figure 4. Example of a revoked certificate that was supposedly used for a malware
Organizations that distribute signed unwanted/malicious software
There are also organizations that have legitimate products, but further examination revealed some other aspects to them. In a way, these organizations seem to be in the gray zone of PUPs and other unwanted software like adware such as BrowseFox. To a certain extent, they produce and commercialize licit software such as toolbars, downloaders, and archivers, but they have also been found embedding PUPs in their “Free Edition” versions. Their software are digitally signed with certificates issued by appropriate CAs. Some examples:
- Mindspark Interactive Network — a company that develops and markets entertainment and personal computing software
- Inbox — a vendor providing free communication platforms like email
- Auslogics — a vendor advertising software (like Booster) for PC performance improvement
Figure 5. Thousands of malicious files signed by seemingly legitimate organizations
Figure 6. Example of an unwanted toolbar from Inbox
Figure 7. Auslogics’ advertisement page
Fraudulent certificates sold in the underground
We found advertisements in the underground, such as ones in forums and marketplaces in the Deep Web, that sell counterfeit certificates.
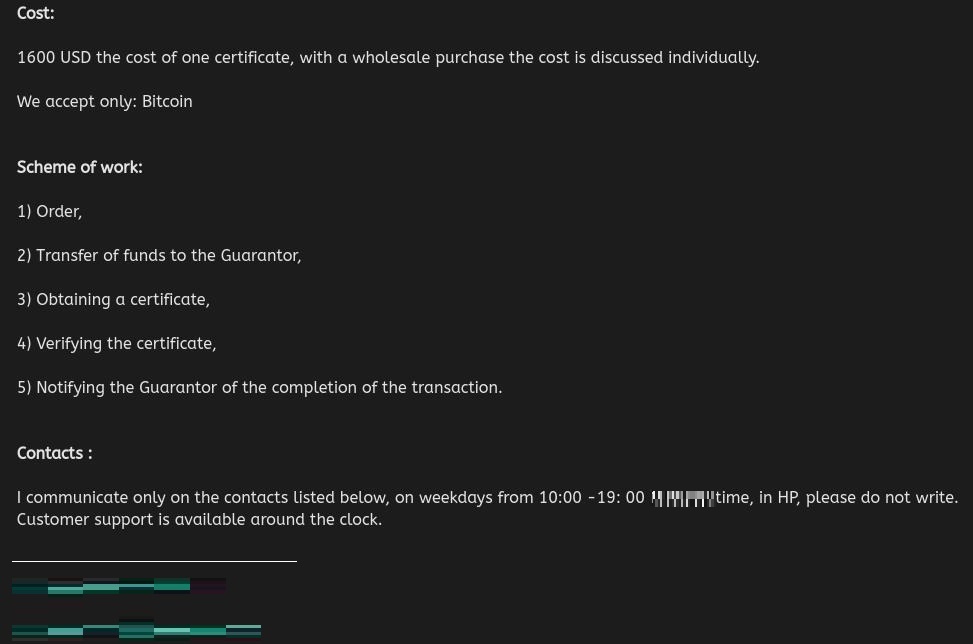
Figure 8. Sample of extended validation (EV) certificate being sold for US$1,600 in the underground
Figure 9. Advertisement selling standard and EV certificates
The advertisements for fraudulent certificates in the underground show that cybercriminals see how useful the mechanism of code signing is in malware campaigns.
Code signing is a very efficient technique in defending against malware, but as revealed in our research, it is not foolproof and can be abused. Users and businesses should carefully evaluate any software installed on their system, on top of standard precautions like updating the operating systems and implementing cybersecurity solutions.
Malware detection systems need labeled files to be able to defend internet-connected machines from infection. Yet a huge number of software files hailing from unpopular websites are still unlabeled and there remain unknown or undefined threats. Our research regarding the abuse of code signing is made possible by a system of classification that uses machine learning technology to analyze files. We made use of such a human-readable machine learning system and explored other key findings on large-scale global download events in our research paper titled Exploring the Long Tail of (Malicious) Software Downloads.