Mobile
HiddenMiner Android Malware Can Cause Device Failure
A new Android malware can surreptitiously use the infected device's computing power to mine Monero. Its self-protection and persistence mechanisms include hiding itself from the unwitting user and abusing the Device Administrator feature.
We uncovered a new Android malware that can surreptitiously use the infected device's computing power to mine Monero. Trend Micro detects this as ANDROIDOS_HIDDENMINER. This Monero-mining Android app’s self-protection and persistence mechanisms include hiding itself from the unwitting user and abusing the Device Administrator feature (a technique typically seen in SLocker Android ransomware).
We further delved into HiddenMiner and found the Monero mining pools and wallets connected to the malware, and learned that one of its operators withdrew 26 XMR (or US$5,360 as of March 26, 2018) from one of the wallets. This indicates a rather active campaign of using infected devices to mine cryptocurrency. HiddenMiner uses the device’s CPU power to mine Monero. There is no switch, controller or optimizer in HiddenMiner’s code, which means it will continuously mine Monero until the device’s resources are exhausted. Given HiddenMiner’s nature, it could cause the affected device to overheat and potentially fail.
This is similar to the Loapi Monero-mining Android malware, which other security researchers observed to have caused a device’s battery to bloat. In fact, Loapi’s technique of locking the screen after revoking device administration permissions is analogous to HiddenMiner’s.
HiddenMiner is found in third-party app marketplaces. So far, it’s affecting users in India and China, but it won’t be a surprise if it spreads beyond both countries.
 Figure 1. Screenshot for one Monero wallet address’s status
Figure 1. Screenshot for one Monero wallet address’s status
Infection Chain
HiddenMiner poses as a legitimate Google Play update app, popping up as com.google.android.provider complete with Google Play’s icon. It requires users to activate it as a device administrator. It will persistently pop up until victims click the Activate button. Once granted permission, HiddenMiner will start mining Monero in the background.
Figure 2. The malicious app’s screen requiring users to activate it as device administrator
Technical Analysis
HiddenMiner uses several techniques to hide itself in devices, such as emptying the app label and using a transparent icon after installation. Once activated as device administrator, it will hide the app from the app launcher by calling setComponentEnableSetting(). Note that the malware will hide itself and automatically run with device administrator permission until the next device boot. The DoubleHidden Android adware employs similar techniques.
 Figure 3. An illustration of how HiddenMiner hides itself: an empty app label and transparent icon after installation (left), then disappearing once granted device administration permissions (right)
Figure 3. An illustration of how HiddenMiner hides itself: an empty app label and transparent icon after installation (left), then disappearing once granted device administration permissions (right)
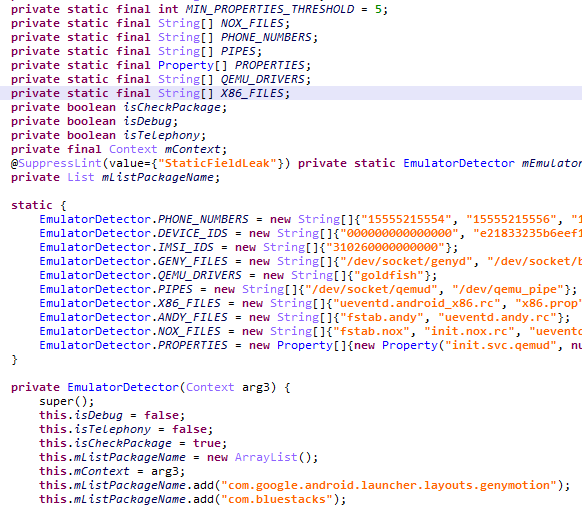
HiddenMiner also has anti-emulator capabilities to bypass detection and automated analysis. It checks if it’s running on an emulator by abusing an Android emulator detector found on Github.
Figure 4. Code snippet showing how HiddenMiner bypasses Android emulators based on our sandboxing detection and analysis
Figure 5. Code snippet showing how HiddenMiner mines Monero
Abusing Device Administration Permission
Users can't uninstall an active system admin package until device administrator privileges are removed first. In HiddenMiner’s case, victims cannot remove it from device administrator as the malware employs a trick to lock the device’s screen when a user wants to deactivate its device administrator privileges. It takes advantage of a bug found in Android operating systems except Nougat (Android 7.0) and later versions.
 Figure 6. Code snippet showing how HiddenMiner prevents removal of device administrator privileges
Figure 6. Code snippet showing how HiddenMiner prevents removal of device administrator privileges
Google resolved this security issue in Nougat and later Android OSs by reducing the privileges of device admin applications so they can no longer lock the screens (if it is part of the app’s feature). Device admin will no longer be notified via the onDisableRequested() context. These tactics aren’t new: certain Android ransomware and information stealers (i.e. Fobus) employed these to gain a foothold in the device.
Indeed, HiddenMiner is yet another example of how cybercriminals are riding the cryptocurrency mining wave. For users and businesses, this reinforces the importance of practicing mobile security hygiene: download only from official app marketplaces, regularly update the device’s OS (or ask the original equipment manufacturer for their availability), and be more prudent with the permissions you grant to applications.
Trend Micro Solutions
Trend Micro™ Mobile Security blocks malicious apps that may exploit this vulnerability. End users and enterprises can also benefit from its multilayered security capabilities that secure the device’s data and privacy, and safeguard them from ransomware, fraudulent websites, and identity theft.
For organizations, Trend Micro™ Mobile Security for Enterprise provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites.
Trend Micro’s Mobile App Reputation Service (MARS) covers Android threats using leading sandbox and machine learning technologies. It can protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
Indicators of Compromise
Related hashes (SHA-256) detected as ANDROIDOS_HIDDENMINER (package name as com.android.sesupdate):
- 7FBF758FEAF4D992B16B26AC582A4BDCFC1A36B6F29B52FC713A2B8537F54202
- E62C034516F28A01ABD1014D5D9CAA7E103AE42C4D38419C39BC9846538747FA
- 975A12756CA4F5E428704F7C553FD2B2CCC12F7965DD61C80BEC7BCBA08C1B37
- FD30B04CE4A732FB830A03C1A0AC0FBB0972C87307E515646239B0834156FA0E
- D21899BDAB5B1D786D8FC6C133385650A4CDA2B71A394B1F8DDC5C0EC39F1523
- BF9C41EE9D4A718F6B6958EC2E935395E79882B0EBEE545E2C84277DBA70A657
- B924A8EC7CFC1D5DDD9828467D7FC583FA6B35F441170D171C7A084FFD1799AD
- B40E2EEF49EDB271BBA2E5AD15C773E6EBDF4BFE5822AD93DDFE20847B8F9D67
- 419629E1644B0179F0AE837FE3F8D80C6E490A59838E485EEDA048BF8DF176D2
- 3039B2FF2E1EDB522FFADAEAED8B0CEE1519CFA56FABE7CE6F0F6A50816D026D
- 1C24C3AD27027E79ADD11D124B1366AE577F9C92CD3302BD26869825C90BF377
- 0156051E50544F9F725B75E32E0ACE888E53FBC79CAC50835B9A9EB39F0FCA84
Monero mining pools and wallets/addresses related to HiddenMiner:
- pool[.]minergate[.]com
- monero[.]hashvault[.]pro
- monero[.]hashvault[.]pro
- supportxmr[.]com
- 49Bq2bFsvJFAe11SgAZQZjZRn6rE2CXH z4tkoomgx4pZhkJVSUmUHT4ixRWdGX 8z2cgJeftiyTEK1U1DW7mEZS8E4dF5hkn
- 43QGgipcHvNLBX3nunZLwVQpF6Vbobm GcQKzXzQ5xMfJgzfRBzfXcJHX1tUHcKP m9bcjubrzKqTm69JbQSL4B3f6E3mNCbU
- 486GAqHxZnCYNcN2V1SEASSoWmifzXZ NrDVgZayZXytJFbr1hSaXGyCbLGzwyX1h eyhcLaps2ZvWFGs1AJKSjEKJNvsTq9q