Ransomware
qkG Filecoder: Document-Encrypting Ransomware
We encountered a few interesting samples of a file-encoding ransomware variant implemented entirely in VBA macros called qkG. It’s a classic macro malware infecting Microsoft Word’s Normal template upon which all new, blank Word documents are based.
We encountered a few interesting samples of a file-encoding ransomware variant implemented entirely in VBA macros called qkG (detected by Trend Micro as RANSOM_CRYPTOQKG.A). It’s a classic macro malware infecting Microsoft Word’s Normal template (normal.dot template) upon which all new, blank Word documents are based.
Further scrutiny into qkG also shows it to be more of an experimental project or a proof of concept (PoC) rather than a malware actively used in the wild. This, however, doesn’t make qkG less of a threat. As the qkG samples demonstrated, its behaviors and techniques can be fine-tuned by its developer or other threat actors. When we first saw samples of it in VirusTotal last November 12, for instance, it didn’t have a Bitcoin address yet. It had one only two days later, along with a routine that encrypts a document on a specific day and time. The next day, we saw a qkG sample with a different behavior (viz., not encrypting documents with a specific file name format).
Notable Behaviors
qkG filecoder stands out as the first ransomware to scramble one file (and file type), and one of the few file-encrypting malware written entirely in Visual Basic for Applications (VBA) macros. It’s also one of the few that uncommonly employs malicious macro codes, unlike the usual families that use macros mainly to download the ransomware.
qkG’s unusual use of malicious macros resembles one of the techniques employed by a .lukitus variant of Locky ransomware that uses the Auto Close VBA macro. In both cases, the malicious macro is executed when the user closes the document. But unlike qkG that only scrambles the document, .lukitus Locky’s macro codes retrieve and help execute the ransomware, which will then encrypt the targeted files stored on the infected machine.
Some of the notable behaviors we’ve seen in qkG include encrypting the document's contents but leaving the file structure intact and the filename unchanged. No ransom note is added to the system as it’s prepended to the document’s content. It affects ActiveDocument, which means only the opened documents will be encrypted.
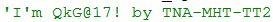
Figure 1. String within qkG’s body revealing its name and author
These samples were uploaded to VirusTotal from Vietnam and contain some comments in Vietnamese. A look into the macro malware’s body reveals its developer naming it “qkG”. There’s also the string TNA-MHT-TT2, which we construe to be the author’s moniker.
Infection Chain
When a would-be victim enables the macros, the normal.dot template gets infected (viz., malicious macro is added to it). In turn, whenever an instance of Word is started, the modified normal.dot template with the malicious code gets loaded and executed.
The malicious macros lower Word’s security settings first so it doesn't ask the user to enable macros. How the security settings are reduced depends on the Office version, and entails:
- Deactivating Protected View (PV) by modifying a few registry keys: DisableAttachmentsInPV, DisableInternetFilesInPV, DisableUnsafeLocationsInPV
- Disabling the feature that blocks Excel files marked as from the web from executing macros (Blockcontentexecutionfrominternet)
- Enabling programmatical access to VBA object model (AccessVBOM)
- Setting the security level to Low (from three possibilities: High, Medium, Low)
After the aforementioned modifications are carried out, qkG infects the normal.dot template. It adds a Document_Close() autostart macro and copies itself into it.

Figure 2. Malicious macro added to the normal.dot template
How qkG Works
When a user opens an uninfected document, nothing happens at first. qkG will, however, encrypt the file's contents once the user closes the document. It will also display a message with an email and Bitcoin address, along with the encrypted content. The qkG filecoder also adds Document_Open() autostart macro to the encrypted document and copies its body. This means if this document is opened on a clean machine, the infection chain will repeat.

Figure 3. The ransom note displayed to the victim after the document is encrypted
The encryption used is a very simple XOR cipher. The encryption key is always the same, and is included in each encrypted document.
Suppose we create a document containing the text “1234567890”. After closing the document on an infected machine, the odd characters get XORed with a corresponding character in the hardcoded password “I'm QkG@PTM17! by TNA@MHT-TT2”, while each even character is left intact. The resulting encrypted document containing text “1234567890” is in the screenshot above.
Here’s an example:
1 2 3 4 5 6 7 8 9 0
31 00 32 00 33 00 34 00 35 00 36 00 37 00 38 00 39 00 30 00
31 XOR 49 (I) = 78
32 remains
33 XOR 27 (') = 14
34 remains
The sample 2d20d5751ffbac9290271969860106fdd34309878a1e06f9dbcac23a7f50b571 contains a decryption routine. However, it’s not used within the malware body and accordingly doesn’t work. This can also be construed as malware still in development, as the other samples showed.

Figure 4. The decryption routine in one the samples of qkG
The sample 2e1136a2bfddb108cd3b3a60761113797265b281085ae35e185a4233d2e75d8e does not have the encryption routine implemented yet. It only has comments in the form of a to-do list. Note that the clipboard is never used in the finished variants of the filecoder.

Figure 5. Another qkG sample listing the supposed routines
The sample e6b15419059e833424e9c726e9b0b085d9f0fcb2cccbfe1025b0d0f8a1735a66 does not infect all files once they are closed. However, it adds a condition that the day of the week (e.g., 1 = Sunday, 2 = Monday, and so forth) must be equal to the current time’s minutes in modulo 10. For example: if the document is closed on Sunday (1) and time xx hours x1 minutes (with x being any number), the file will be encrypted.
 Figure 6. Code snapshot showing the condition set by a qkG variant in order to encrypt the file
Figure 6. Code snapshot showing the condition set by a qkG variant in order to encrypt the file
We looked into its Bitcoin address and found that it didn't have any transactions yet:
 Figure 7. Screenshot showing qkG’s Bitcoin transactions as of November 17, 2017
Figure 7. Screenshot showing qkG’s Bitcoin transactions as of November 17, 2017
Mitigation
While not particularly pervasive in terms of impact, qkG’s unique use of malicious macros is still notable. And like other ransomware families, we expect this technique to be rehashed, broadened, and repurposed for other cyberattacks.
Disabling macros significantly reduces the risk of macro-based malware such as qkG. Follow cybersecurity hygiene and apply best practices against ransomware: keep the system and its applications updated, regularly back up data, and restrict the use of tools, utilities, and features that can be misused as attack vectors. And more importantly, be more cybersecurity-aware. Macro-based malware are often employed alongside files/documents with socially-engineered hooks—ultimately, technologies that deter threats are only as good as the people who use them.
Trend Micro Solutions
Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. It features high-fidelity machine learning to secure the gateway and endpoint data and applications, and protects physical, virtual, and cloud workloads. With capabilities like web/URL filtering, behavioral analysis, and custom sandboxing, XGen™ protects against today’s purpose-built threats that bypass traditional controls, exploit known, unknown, or undisclosed vulnerabilities, and either steal or encrypt personally-identifiable data. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise:
Hashes detected as RANSOM_CRYPTOQKG.A (SHA-256):
- · 2d20d5751ffbac9290271969860106fdd34309878a1e06f9dbcac23a7f50b571
- · 2e1136a2bfddb108cd3b3a60761113797265b281085ae35e185a4233d2e75d8e
- · e6b15419059e833424e9c726e9b0b085d9f0fcb2cccbfe1025b0d0f8a1735a66.doc

