Phishing
How HTML Attachments and Phishing Are Used In BEC
BEC attacks used keyloggers to steal saved account information. But using an executable file attachment usually flags a user not to click them. As a result, we’ve seen a trend wherein the attached files are no longer executable files but HTML pages.
Traditionally, BEC attacks have used keyloggers to steal saved account information from target machines. However, using an executable file for the attachment usually flags a user not to click them as there is a high chance that the file is malicious. As a result, we’ve seen a trend wherein the attached files are no longer executable files but HTML pages:

Figure 1. Phishing Email with HTML attachment
Opening the attachment will launch a browser with the following content:
Figure 2. HTML Phishing page (Click to enlarge)
The page asks the user to enter their username and password to view the document file. To lure a user to use an email account, they added images from popular email providers like Gmail, Outlook, and Yahoo Mail.
When a victim enters their username/password and submits the form, the credentials are then sent to a PHP script configured by the attacker. Usually, this script is configured to send the credentials to an email account controlled by the attacker.
Figure 3. HTML source code with POST command (Click to enlarge)
Checking the source code of the HTML attachment indicates that it was probably coded in Nigeria, as the Google link was set to a version for that country.
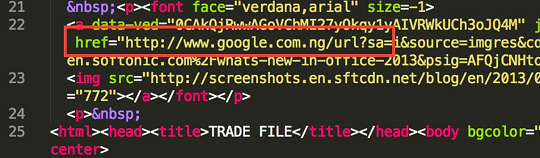
Figure 4. URL with localized Google domain
This makes even more sense if one considers what we found on Nigerian forums. Nairaland (a popular Nigerian forum) contained an advertisement for scam pages. The seller offers different scam pages for various email services like 163 Mail, Gmail, Hotmail, and Yahoo Mail.
Figure 5. Website with scam pages for email services
Keyloggers are still commonly used by BEC actors to retrieve the accounts of their victims and are very effective. However, delivering an executable file through email can be difficult nowadays as anti-spam rules will quickly flag these messages. On the other hand, an HTML file poses no immediate threat—unless the file was verified to be a phishing page.
A phishing page can be easily coded and deployed, unlike a keylogger that requires some coding knowledge. A phishing page will also run on any platform, as they only need a browser, unlike keyloggers, which will be dependent on the builder.
One disadvantage of phishing pages over keyloggers is how they recover passwords from their victims. For a phishing page, a user needs to enter their credentials into a form and send them. A keylogger only needs to be executed and will then be running in the background. In summary:
| Keyloggers | HTML Phishing Page | |
| Password recovery | No user interaction needed once keyloggers are executed | User needs to enter credentials |
| Multiple account recovery | Yes | No |
| Multi platform | No | Yes |
Table 1. Differences between HTML phishing pages and keyloggers (Click to enlarge)
HTML Attachments - Statistics
To gain more insight, we looked into feedback information from our products via the Smart Protection Network. From July 1, 2016 to June 30, 2017, we found 14,867 records and 6,664 unique hashes.
The following chart shows the number of cases seen per month:
Figure 6. Number of BEC-related phishing attacks per month
The following chart shows where the above incidents were recorded:
Figure 7. Location of BEC-related phishing attacks
The following chart indicates the keywords used in these attachments:
Figure 8. Keywords used in BEC-related phishing attacks
Other Phishing Email and Attachment Samples
The SHA256 hashes of the samples used in the original screenshots are the following:
- 1b369df9ea0f75b5d40aa60c649f12d174e28f1177a473775d2d5454e4ca131c
- ac5f29a25e918691f4949587290e9ef6ca4dae1398d3e4a1e5fe69687a67eab0
Below are several samples of other attacks that use this methodology:




Figures 9 to 13. Various phishing emails and websites used in BEC attacks
We recently talked about this topic at the RSA Conference 2017 Asia Pacific & Japan, which was held in Singapore from July 26 to 28. Our Phish Insight service tests the ability of organizations to resist online scams, allowing administrators to judge the level of risk they are currently exposed to.








