APT & Targeted Attacks
Operation Pawn Storm: Outlook Web Access Users at Risk
In our recently released report, Operation Pawn Storm, we talked about an operation that involved three attack scenarios. For this post, we will talk about the third scenario: phishing emails that redirect victims to fake Outlook Web Access login pages.
In our recently released report, Operation Pawn Storm, we talked about an operation that involved three attack scenarios. For this post, we will talk about the third scenario: phishing emails that redirect victims to fake Outlook Web Access login pages. What's most notable about this is that it is simple, effective, and can be easily replicated. Through one line of simple Javascript code, the millions of Outlook Web Access (OWA) users are placed at risk of becoming a victim of a clever but simple phishing attack. No exploits and vulnerabilities are used here. A feature of JavaScript, the preview pane of Microsoft’s OWA and two typo-squatted domains are used. We have seen this kind of phishing attack being used against US defense companies like Academi (formerly known as Blackwater), SAIC and the OSCE.
How it works
To target defense company Academi, the attacker registered two typosquatted domain names:
- tolonevvs[dot]com (real news domain: tolonews.com (news site about Afghanistan))
- academl[dot]com (real company domain: academi.com)
A link to the typosquatted domains are then sent to Academi through spear-phishing emails -- to a very limited number of employees who might actually expect to receive email notifications from tolonews.com. When the target opens the email through the preview pane of Microsoft Outlook Web Access and clicks on the typosquatted domain, a new tab will be opened which loads the original news site. From the target's perspective, their browser will look like this:
Figure 1. The real news site opened in a new tab after clicking the typosquatted domain (Click to enlarge)
This may seem harmless, but there is more to this than just an opened tab to a news site. The typosquatted domain tolonevvs.com actually contained a mildly obfuscated JavaScript code:
Figure 2. JavaScript code in the typosquatted domain, tolonevvs.com
This JavaScript is not malicious because it simply sets the windows open property to point to a URL:
window.opener.location = "hxxps://mail[dot] academl[dot]com/owa/auth/logon.aspx?replaceCurrent=1&url=https%3a%2f%2fmail.academi.com%2fowa%2f&tids=lkdmfvlkd"
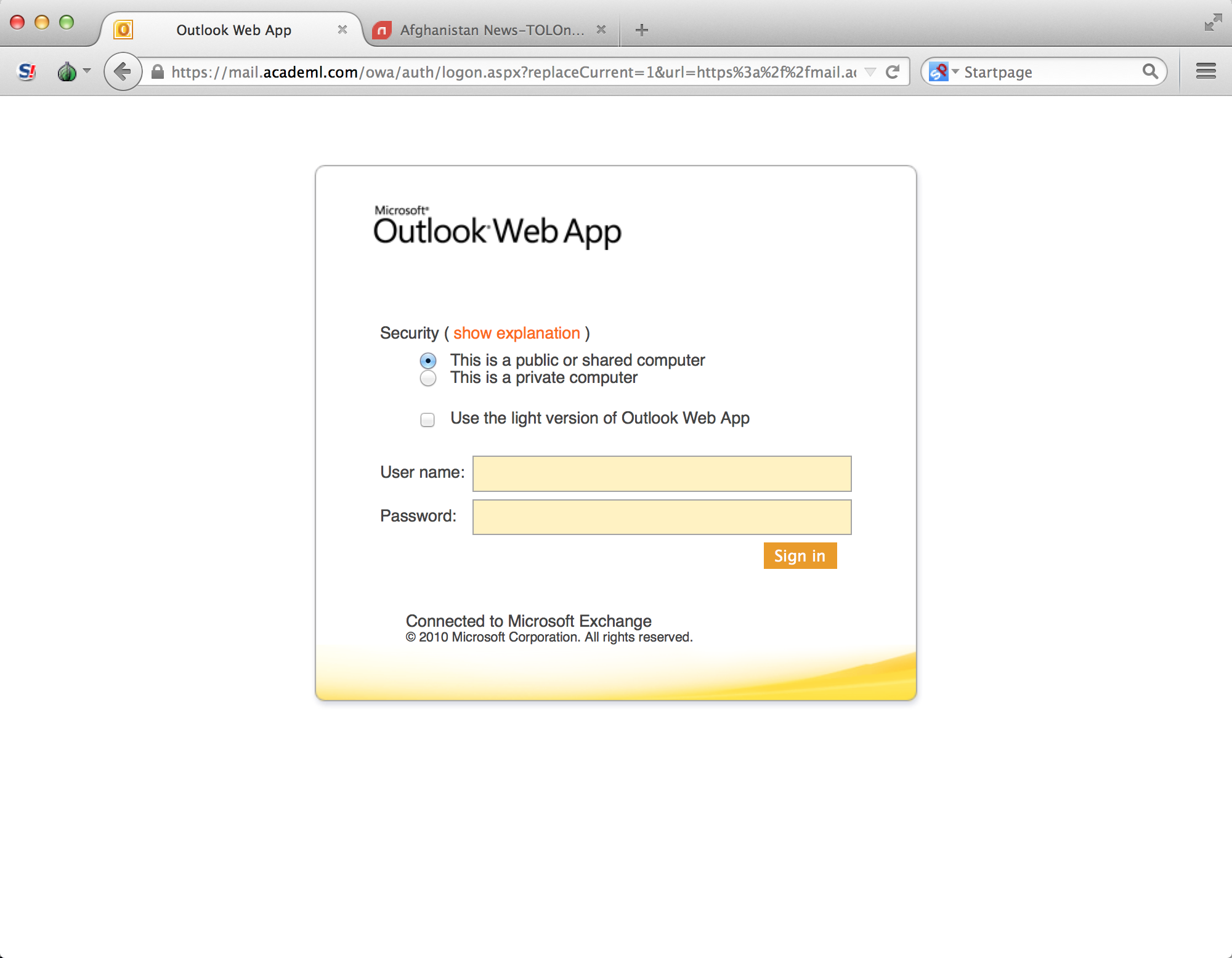
What this means is that the legitimate URL of the original OWA session in the first tab of the browser gets changed to the URL of the fake OWA server set up by the attacker, which in this case is mail[dot]academl[dot]com. When the victim is done with reading the news and he returns to his OWA session, he will see this:
Figure 3. Phishing site opened in the original OWA tab
At this point, the target is likely to believe that while reading the news on the legitimate website tolonews.com, the OWA server logged him out. The truth, however, is that if the target enters his/her credentials again, his/her information will then be captured by the attacker.
For the complete details on the attacks we saw using this technique, please check out our paper, Operation Pawn Storm.
Not Limited to Operation Pawn Storm or OWA
Although we did see this technique used in a certain operation, basically any company having an OWA web server is at risk becoming a victim of this kind of phish attack. Even two factor authentication might not prevent a one-time complete download of the mailbox of the victim. The only safe way to prevent this kind of attack is to turn off the preview pane in OWA.
Users of other web mail services than OWA are also are at risk. For example, we verified that Gmail users who read their e-mail in Safari, and Yahoo e-mail users who read their e-mail in Safari or Firefox could become victims of a similar phishing trick. Users are strongly recommended to be very careful when entering their information into login pages, and to make sure that they are logging into the correct site and not a typosquatted one.