What is SIEM?
SIEM Meaning
SIEM (Security Information and Event Management) is a solution for cyber security monitoring, detection, and investigation, SIEM collects, manages, and analyzes event logs generated by networks and systems, contributing to early detection of security incidents and prompt response. By combining security information management (SIM) and security event management (SEM), SIEM systems provide centralized visibility into security events and log data generated by endpoints, servers, applications, and network devices. This approach enables organizations to detect, analyze, and respond to potential threats in real time.
What does SIEM stand for?
SIEM stands for Security Information and Event Management. It is a cybersecurity solution that collects, analyzes, and correlates security data from various sources to detect, investigate, and respond to potential threats in real time.
SIEM Security Functions
SIEM systems operate by collecting and aggregating log data, performing correlation analysis to identify anomalies, and generating actionable alerts for security teams. They also provide detailed reports to help with compliance and auditing requirements. As a cornerstone of modern Security Operations Centers (SOCs), SIEM enhances threat detection, incident response, and overall security posture by transforming raw log data into actionable intelligence, ensuring organizations can proactively mitigate risks.
Log collection
SIEM systems gather log and alert data from various devices and applications across the IT infrastructure, including firewalls, servers, endpoints, databases, and cloud services. This aggregation ensures that all security-relevant information is stored in one place, streamlining visibility and eliminating silos. Logs can include user activity, system errors, access attempts, and application-specific events. The ability to ingest data from diverse sources enables SIEM to provide a holistic view of an organization’s security landscape.
Correlate security events
Correlating security events involves analyzing patterns and relationships between multiple logs to identify potential threats or suspicious behaviors. For example, a single failed login attempt might not trigger concern, but multiple failed attempts followed by a successful login from an unusual location could indicate a brute force attack. By applying predefined rules, machine learning algorithms, and context-aware analysis, SIEM identifies these patterns and prioritizes potential security incidents for investigation.
Alerts and Notifications
When anomalous activity or a potential security incident is detected, SIEM systems generate alerts based on pre-defined thresholds and rules. These alerts are sent to security teams via dashboards, emails, or integrated response tools. For instance, an alert might be triggered for unauthorized access to a critical database or abnormal traffic spikes indicative of a denial-of-service (DoS) attack. Alerts are prioritized to help security personnel focus on the most critical issues first, improving response efficiency.
Report Generation
SIEM platforms generate comprehensive reports that summarize security events, trends, and incident responses. These reports are essential for understanding the organization's security posture over time, meeting compliance requirements, and providing actionable insights to improve future defenses. They can also include workflows for incident management, detailing step-by-step procedures for containment, eradication, and recovery after a breach. Reports often serve as critical documentation for internal reviews and external audits.
SIEM Tools
SIEM tools collect and analyze large volumes of data from organization's endpoints in real-time and detect and block cyber threats by working alongside security teams
You need to define rules to help those teams and generate alerts
SIEM tools help as well with:
- Event logs that can help consolidate data from numerous sources
- Adding intelligence to raw data obtained from a correlation of events from different logs or sources
- Automation of security alerts. Most SIEM platforms will allow you to set up direct notifications
SIEM and SOAR tools have been instrumental in centralizing security event data and automating response workflows. Despite their utility, they face significant challenges:
- Data Overload: SIEM platforms often generate excessive alerts, overwhelming SOC teams and leading to alert fatigue.
- Integration Complexity: SOAR relies heavily on seamless integration with various tools, which can be complex and time-consuming.
- Operational Silos: Both technologies require substantial manual effort to correlate data and orchestrate responses, creating inefficiencies in incident response.
While these tools remain valuable, their fragmented approach to detection and response has created an opportunity for XDR to provide a more cohesive solution.
XDR vs SIEM
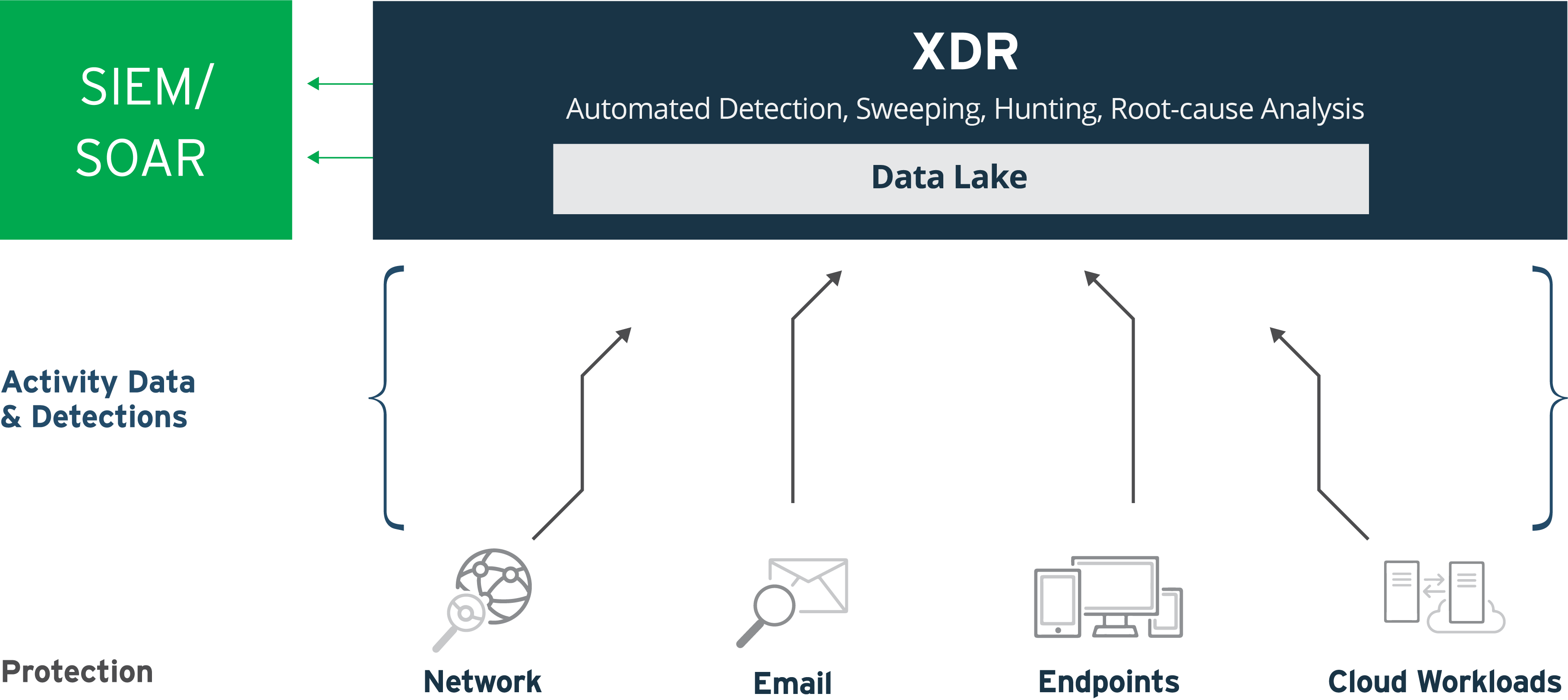
Similar to SIEM as a tool to improve security level and efficiency is XDR (Extended Detection and Response). The differences between SIEM and XDR are as follows:
Data collection targets and contextualization
- SIEM: Collects, manages, and analyzes events and logs generated within a network or system. Analysis is performed primarily on log data to detect abnormal activity and signs of attacks.
- XDR: Collects and analyzes telemetry data from multiple data sources, including endpoints, networks, and the cloud. It collects not only security events, but also endpoint file and process information, network traffic data, etc.
Analysis and detection
- SIEM: Analyzes the collected data according to predefined rules and algorithms. It detects unusual activity or signs of attacks and generates appropriate alerts and warnings. Some products have the ability to perform correlation analysis between mechanical logs. However, the judgment of whether or not an event is a possible cyber attack basically relies on the "human intuition" of the operator.
- XDR: Based on the threat intelligence (malware, malicious sites, malicious emails, attack methods used by cyber attackers, etc.) possessed by cyber security companies that provide XDR, signs of cyber attacks are determined for the collected telemetry. For example, legitimate tools provided by Microsoft, such as PsExec, Cobalt Strike, and Mimikatz, are often misused in cyber attacks.
Incident Response and Automation
- SIEM: Provides basic information and procedures for security incidents to assist in incident response; SIEM is primarily focused on alert generation and monitoring, while other products may be required for actual response procedures.
- XDR: Provides automation and orchestration capabilities to support rapid response to security incidents. Detected threats are analyzed and response guidance is provided in real time.
Dependence on the source
- The value of a SIEM solution is directly related to the sources from which it obtains its information. If there are gaps in the coverage, they are often noticed late or not at all.
- In consequence, if we compare SIEM to XDR, we should also point out that in most cases it is not an either/or decision. More often it is XDR and SIEM since SIEMs get most value from Detection & Response logs. How about this as “famous last word”:
- Due to the dependence of a SIEM solution on the quality of information generated by third-party providers, it often happens that both variants are used in parallel and XDR solutions pass the pre-correlated data on to the SIEM.
SIEM Benefits
Logs can be managed centrally
By introducing SIEM, logs can be managed centrally. This eliminates the need to manage logs for each device, and reduces management errors and omissions. In addition, SIEM has the function of normalizing collected logs and visualizes the entire IT environment, enabling efficient and comprehensive management.
Early detection of security incidents and threats
SIEM centralizes log management and performs correlation analysis in real time, enabling early detection of incidents and threats. When a threat symptom or incident is discovered, a quick response can be made, minimizing the spread of damage.
Preventing internal fraud
Security incidents are not only caused by external cyber attacks. Preventing misconduct by employees of your own organization is also an important security measure for an organization. By introducing SIEM, you can detect suspicious employee behavior and unauthorized access. SIEM is also effective in preventing internal fraud.
Eliminating the shortage of security personnel
By using SIEM, you can streamline security operations. By automating a series of tasks such as log aggregation, normalization, and analysis, you can reduce the resources required for your organization's security measures. Although a certain level of security knowledge is required to operate SIEM, introducing SIEM will enable you to implement more efficient security measures than before.
The role of SIEM in SOC
SIEM is primarily used in a Security Operations Center (SOC), an organization that monitors security within an organization and understands the occurrence of cyber attacks and incidents, SIEM is an important tool for security professionals to support efficient security operations in the following ways
Alert notification through integrated log management
SIEMs manage various logs in an integrated manner and detect signs of abnormal activity or attacks, and alert security personnel. For example, in addition to detecting malware and other unauthorized behavior, SIEM will alert you when suspicious events are detected, such as multiple login attempts to servers where critical information is stored, or use of cloud services not authorized by your company.
Incident investigation and response
Based on unauthorized or suspicious events, SIEM investigates whether or not it is a cyber attack (normal behavior, access error, etc.). If determined to be a cyber-attack, the route and scope of the attack, including whether it is an external or internal cyber-attack, can be traced to provide clues for incident response. The following measures will be taken
- If the attack is determined to be an external cyber attack: Block the IP of the access source, change the threshold to be blocked by the security product, etc.
- If the behavior is caused by an employee: If the employee is violating a policy set by the company (e.g., there is access to cloud storage even though the use of cloud storage is prohibited), issue a warning to the employee, etc.
Reporting
From a medium- to long-term perspective, visualize the status of violations of your company's security policies and the impact of cyber attacks, and create a report. By visualizing what kind of cyber-attacks the company has been subjected to over a period of one month, three months, six months, one year, etc., the company can consider what security measures it should take next.
The main use cases of SIEM are listed above, but the greatest benefit of SIEM for security personnel is the ability to quickly visualize events and log information from multiple different products and link them to the next action.
SIEM Challenges
While SIEM brings benefits to SOCs and other organizations in terms of improved security and operational efficiency, it also presents the following challenges.
Complex implementation and configuration: SIEMs are complex systems that require time and expertise to implement and configure. Security professionals must continually work to integrate device logs and data sources, configure rules, and tune alerts.
Processing large amounts of log data
A large amount of log data must be processed and analyzed. Appropriate hardware and storage resources are needed to process large amounts of data. It is also necessary to manage log data retention periods and data compression/reduction.
Ongoing response to false positives and alert overload
SIEMs generate alerts based on predefined rules and patterns. However, false positives (false positives: legitimate activity mistakenly detected as malicious) and false negatives (false negatives: malicious activity missed) can occur. Also, depending on the configuration, a large number of alerts may be received, requiring continuous tuning of alerts and improvement of rules on the user side.
Response after incident detection
When an event is detected in real time, the actual incident must be confirmed and responded to. If security personnel does not tune up alerts ahead of time, they will be required to respond to alerts of various sizes, which may in turn reduce operational efficiency.
Skill and resource requirements
Proper implementation and operation of SIEM requires security analysis and log management skills. It also requires the availability of appropriate resources (personnel, hardware, and software).
Trend Micro SIEM solution
Optimize workflows with an ecosystem that includes SIEM, SOAR, IAM, firewall, threat intelligence, IT service management, and more.
Siloed tools create security gaps. Trend Vision One serves teams with these robust capabilities for prevention, detection, and response:
- Cloud operations: Hybrid, multi-cloud security with complete cloud-native application protection
- IT Infrastructure: Endpoint, email, and network security that safeguard borderless workforces
- SOC: Threat detection and response that extends across security layers to accelerate detection and response