A newly emerged information-stealing malware named Bandit Stealer is gaining traction as it targets numerous browsers and cryptocurrency wallets while evading detection. Currently, there is a growing interest and promotional activity within the malware community to increase awareness and use of the malware. While the focus of targeting is limited to the Windows platform as of this writing, it has the potential to expand to other platforms as Bandit Stealer was developed using the Go programming language, possibly allowing cross-platform compatibility.
For this analysis, we used the sample hash (SHA256) 050dbd816c222d3c012ba9f2b1308db8e160e7d891f231272f1eacf19d0a0a06, a 64-bit binary executable written in Go. In the next sections, we provide insights into the functions and capabilities of this recently discovered information-stealing malware.
Escalation
The malware tries to use runas.exe, a command-line utility program in Windows operating systems (OS) that allows users to run specific programs or commands with user credentials or permissions other than those from the current user's account. This elevates the user’s privileges and executes itself with administrative access, allowing the user of the utility to execute malicious activities without being detected or blocked by the security measures in place.
Microsoft has implemented various measures to prevent the unauthorized use of the runas.exe function, including the implementation of security restrictions. This limits the privileges and actions that can be performed using runas.exe. Microsoft has also strengthened user access controls, ensuring that only authorized individuals with the necessary permissions can execute privileged operations. In this case, the malware is trying to run itself as an administrator. However, due to the existing mitigation or security improvements of Microsoft, it was prevented because using runas with administrator rights requires a password.
By using the runas.exe command, users can run programs as an administrator or any other user account with appropriate privileges, provide a more secure environment for running critical applications, or perform system-level tasks. This utility is particularly useful in situations where the current user account does not have sufficient privileges to execute a specific command or program. In the case of Bandit Stealer, this is done with the following command line:
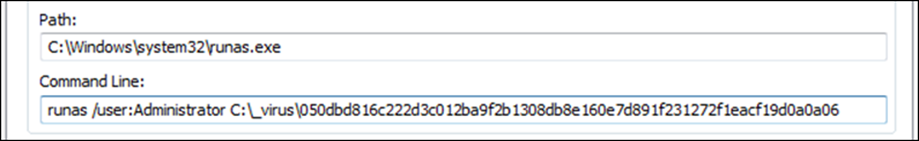
Despite this, Bandit Stealer is not successful in utilizing it because they need to provide the appropriate credentials.
Evasion
Bandit Stealer checks for the following to determine if it's running in a sandbox environment and alters its behavior accordingly to avoid detection or analysis:
- container
- jail
- KVM
- QEMU
- sandbox
- Virtual Machine
- VirtualBox
- VMware
- Xen
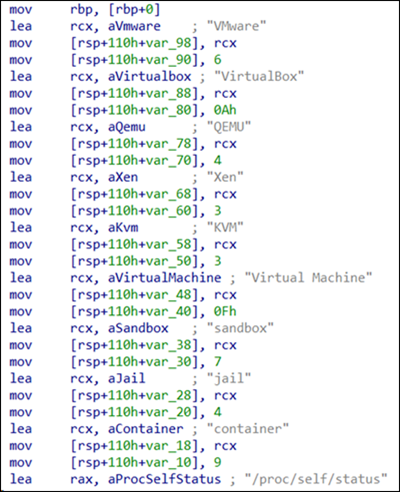
However, reading /proc/self/status is specific to Linux OS, and attempting to access this file path on a Windows system will result in an error. It's possible that the malware is being tested and includes a feature that can infect Linux machines, hence the presence of tshe Linux-specific command.
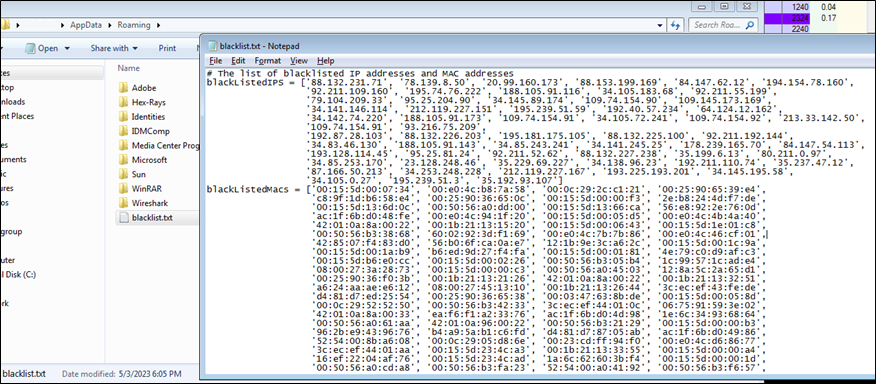
The malware downloads the content of the Pastebin link hxxps[:]//pastebin[.]com/raw/3fS0MSjN and saves it to a file named “blacklist.txt” in the AppData folder. This list contains hardware IDs, IP addresses, MAC addresses, usernames, hostnames, and process names typically used to detect whether the malware is running in a sandbox or testing environment. This technique was previously used by other information stealers such as Creal Stealer, Luna Grabber, Kyoku Cookie token stealer and Pegasus Stealer. The similarities were based on the blacklist content, IPs, and MAC addresses used. This suggests that it is either based on or using a port of the original Python-based stealer. It is likely that with Bandit Stealer, the Go programming language was employed to avoid detection and ensure cross-platform functionality similar to Python-based stealers.
After downloading, the blacklist.txt file will be stored in path <C:\Users\<Username>\AppData\Roaming\blacklist.txt>. The malware will then use the function bandits.utils.CompareWithBlacklist to compare the network interface addresses, hardware (HWID), and host name with the entries in the blacklist.
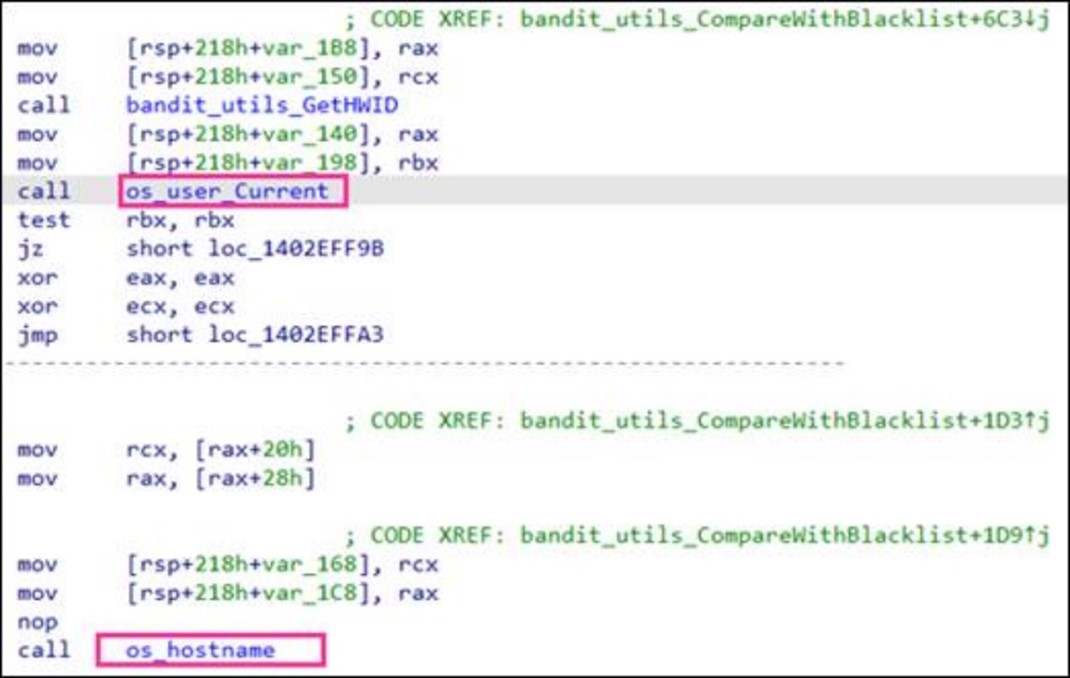
The first half of a MAC addresses (24 bits) is called the Organizationally Unique Identifier (OUI), which identifies the manufacturer or vendor of the network interface. One of the MAC addresses given from the blacklist, "00:0c:29" corresponds to the OUI for VMware products such as virtual machines, which is commonly used for sandbox and malware analysis. The malware leverages the command "wmic csproduct get uuid", a Windows Management Instrumentation Command-line (WMIC) utility used to retrieve the unique hardware identifier (UUID) of the infected device.
The malware will retrieve the current username using os_user_Current and device name using os_hostname. Once the malware checks for blacklisted IP addresses, MAC addresses, HWIDs, and users, it will proceed to terminate blacklisted processes related to malware analysis tools.
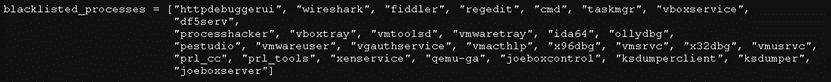
The malware employs the Linux-specific pgrep and pkill commands to terminate the blacklisted processes. These commands are commonly used in Linux and Unix-like OS to search for and terminate processes based on their names or attributes, such as the process owner's username or command-line arguments. The pgrep command is used to find the Process ID (PID) of a running process based on its attributes. Conversely, the pkill command sends a signal to one or more running processes that leads to their termination. However, since these commands are Linux-specific, they cannot be used in Windows. It is likely that the malware is still under development or being adapted to the Windows platform.
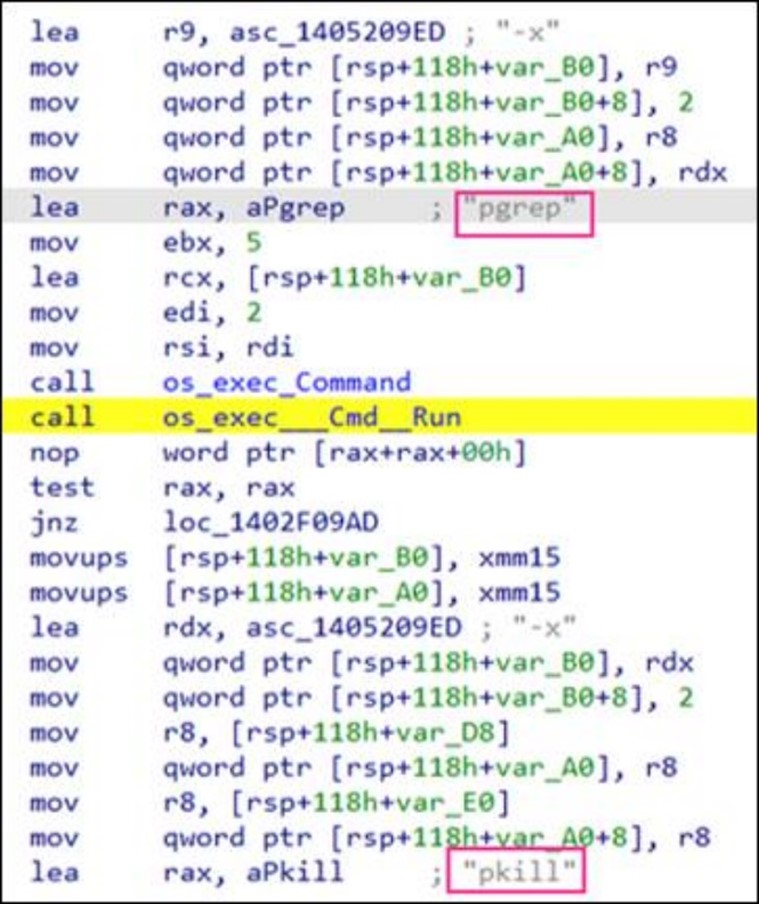
Persistence
In order to persistently run and carry out its malicious activities, Bandit Stealer creates a registry entry for autorun. It will create an autorun registry entry <HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run> with a value name “BANDIT STEALER” to ensure that the malware is executed every time the infected system starts up or restarts. This way, even after a system shutdown or reboot, the malware can still operate and steal data from the victim's system.
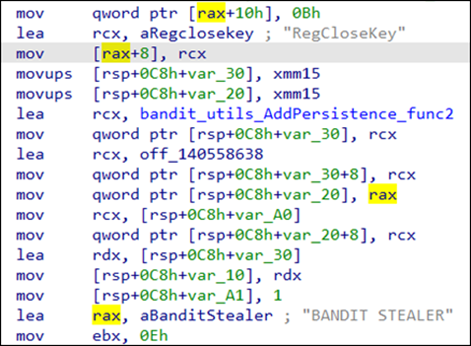
Collection of the victim's data
Once the persistence is established, Bandit Stealer collects the victim's stolen information and stores it in the “vicinfo” folder in <C:\Users\<Username>\AppData\Local\>.
We break down the specific information obtained from the victim and its corresponding details:
| Stolen Information | Details |
|---|---|
| Username, computer name, and current IP | The malware uses the functions os.Getenv and os.hostname, and the command line utility curl to get the username, computer name and public IP of the victim. |
| Obtains the victim's hard drive information | The malware retrieves the disk information in drive C using win32 API GetDiskFreeSpaceExW. Bandit Stealer gets the following information:
|
| Retrieves the detailed information of the victim machine | The malware gathers the following:
|
| Program runtime of the malware | The malware uses "time_now" function, a programming function that retrieves or generates the current time. It provides the current date and time information based on the system clock or a specified time zone. |
| Screen size of the victim’s machine | The malware executes the following command to retrieve the screen size: |
| UAC Information | UAC (User Account Control) is a security feature in Windows OS. The malware runs the command below to determine if “UAC Enabled” in the victim machine: |
| IP location of the victim | The process involves making an HTTP request to the specified URL using the GET method. In this case, the URL https://ipapi.com/json/, which is a web service that provides IP geolocation data in JSON format, is used. |
| Country code | The malware executes the command to retrieve the country code associated with an IP address: |
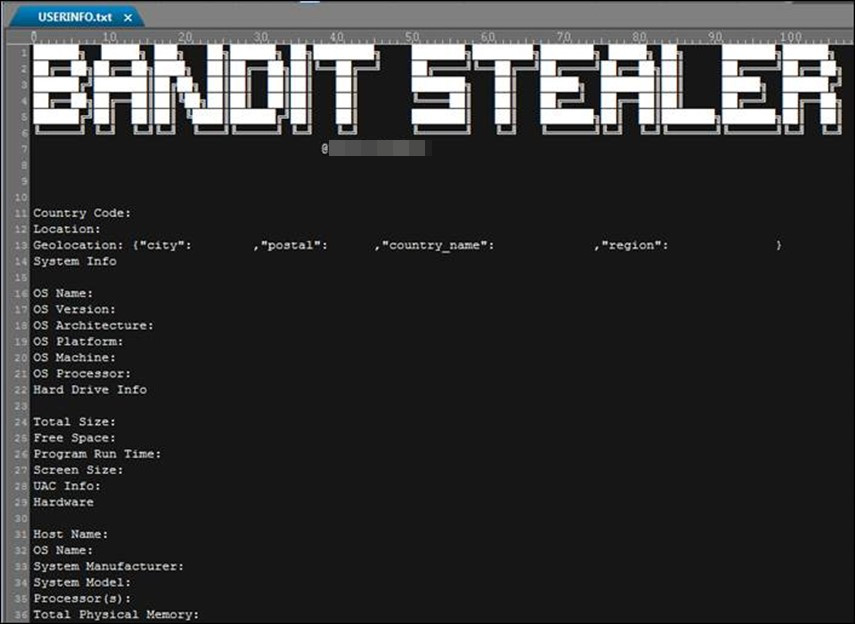
After gathering all the information, the malware saves these in a file named "userinfo.txt" within the <C:\Users\<Username>\AppData\Local\vicinfo> folder.
Bandit Stealer collects Telegram sessions to gain unauthorized access, allowing impersonation and malicious actions such as accessing private messages and data associated with the compromised account.

The malware checks the folder paths of the browser and cryptocurrencies to gain unauthorized access to personal or confidential information in order to exploit it for financial gain. Table 2 shows the list of the browsers scanned and their corresponding paths:
| Browser | Path |
|---|---|
| 7Star | %appdata%\7Star\7Star\User Data\Local State |
| YandexBrowser | %appdata%\Yandex\YandexBrowser\User Data\Local State |
| Brave-Browser | %localappdata%\BraveSoftware\Brave-Browser\User Data\Local State |
| Amigo | %appdata%\Amigo\User Data\Local State |
| Torch | %appdata%\Torch\User Data\Local State |
| Google Chrome Canary | %appdata%\Google\Chrome SxS\User Data\Local State |
| Google Chrome | %localappdata%\Google\Chrome\User Data\Local State |
| Cent Browser | %appdata%\CentBrowser\User Data\Local State |
| Sputnik | %appdata%\Sputnik\Sputnik\User Data\Local State |
| Iridium | %localappdata%\Iridium\User Data\Local State |
| Orbitum | %appdata%\Orbitum\User Data\Local State |
| UCozMedia | %appdata%\uCozMedia\Uran\User Data\Local State |
| Epic Privacy Browser | %appdata%\Epic Privacy Browser\User Data\Local State |
| Microsoft Edge | %localappdata%\Microsoft\Edge\User Data\Local State |
| Kometa | %appdata%\Kometa\User Data\Local State |
The following sensitive information will be stolen from the victim’s browser:
- Login data
- Cookies
- Web history
- Credit card details
Table 3 shows the list of cryptocurrencies collected and their corresponding paths:
| Cryptourrency | Path |
|---|---|
| Bitcoin | %appdata%\Bitcoin |
| Litecoin | %appdata%\Litecoin |
| Dash | %appdata%\Dash |
| Ethereum | %appdata%\Ethereum |
| Electrum | %appdata%\Electrum |
| Exodus | %appdata%\Exodus |
| Atomic | %localappdata%\atomic |
Additionally, the malware scans for specific browser extensions associated with cryptocurrency wallets by checking the path of the browser extensions. Table 4 shows the wallets that the malware searches for and their respective paths:
| Extension Name | Path |
|---|---|
| Clover Wallet | %localappdata%Google\Chrome\User Data\Default\Local Extension Settings\nhnkbkgjikgcigadomkphalanndcapjk |
| Jaxx Liberty | %localappdata%Google\Chrome\User Data\Default\IndexedDB\chromeextension_cjelfplplebdjjenllpjcblmjkfcffne_0.indexeddb.leveldb |
| Wombat | %localappdata%Google\Chrome\User Data\Default\Local Extension Settings\amkmjjmmflddogmhpjloimipbofnfjih |
| TronLink | %localappdata%Google\Chrome\User Data\Default\Local Extension Settings\ibnejdfjmmkpcnlpebklmnkoeoihofec |
| Trust Wallet | %localappdata%Google\Chrome\User Data\Default\Local Extension Settings\egjidjbpglichdcondbcbdnbeeppgdph |
| Crypto.com | %localappdata%Microsoft\Edge\User Data\Default\Local Extension Settings\gpbdhlngfkgihnfeekcmkbbalpdflgmg |
| BitKeep: Crypto & NFT Wallet | %localappdata%Microsoft\Edge\User Data\Default\Local Extension Settings\jiidiaalihmmhddjgbnbgdfflelocpak |
Sending the victim’s information
Bandit Stealer tries to execute isof -t <path of zip file>, a utility in the Linux environment to list down all the processes that are actively using a file. It is possible that the author tries to terminate the processes that accesses the Zip file to use it and send it to the server or Telegram.
Delivery
The malware file might have been unwittingly downloaded by users while visiting malicious websites or through phishing emails. In this section, we break down the different ways the malware was installed and executed.
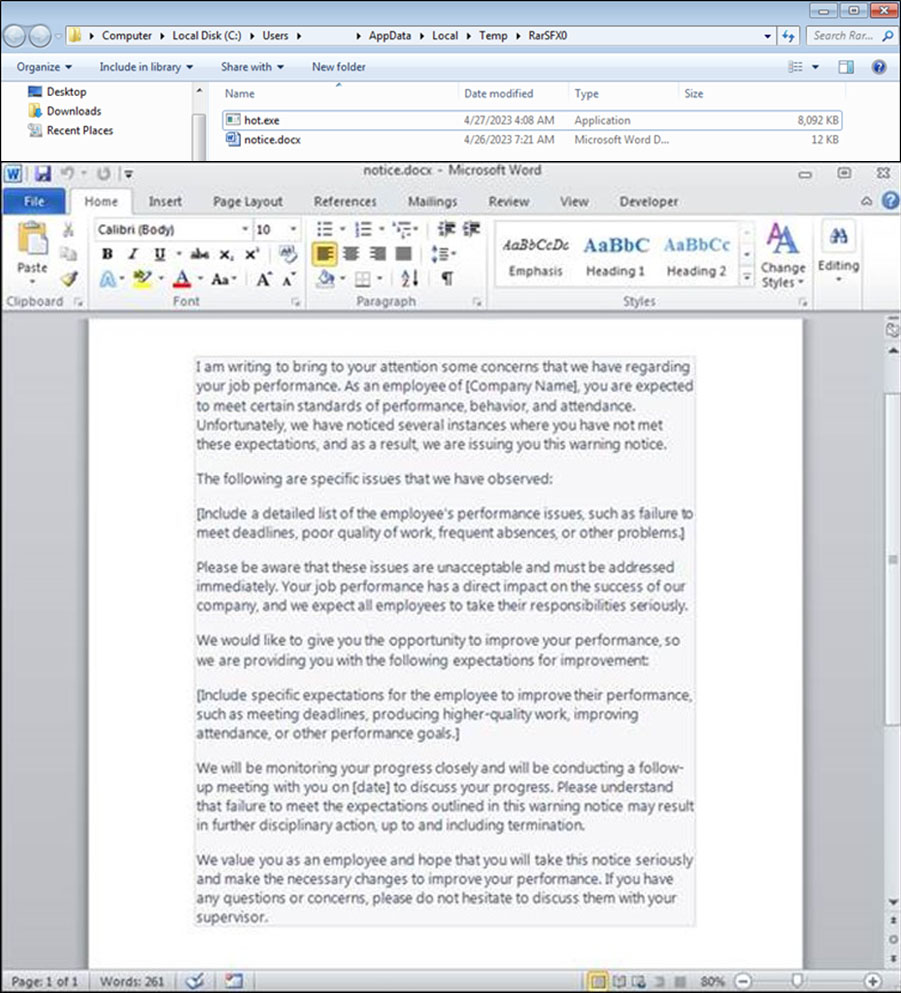
1. The dropper, a self-extracting archive, executes the hot.exe file. Once the malware has carried out all its intended actions, it opens a Word document and deceives the user to open a seemingly harmless document and creating the illusion of a non-malicious file being accessed.
Execution parent: NewWarningNotice.exe (SHA256: 106a184d39858af7b0264f26fe0fc657a84ccfd87df3a4f55e7060b3c3c1d92d) drops the following files:
- %temp%\RarSFX0\notice.docx (opens this document)
- %temp%\RarSFX0\hot.exe (Bandit Stealer)
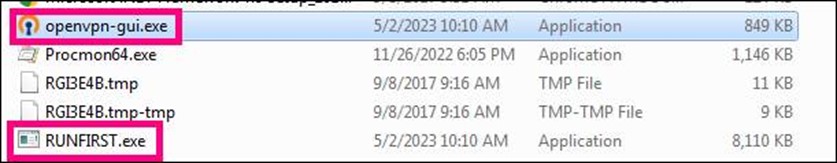
2. The dropper, also a self-extracting archive, executes the RUNFIRST.exe file. After the malware has completed all its intended actions, it will open a non-malicious file named openvpn-gui.exe.
Execution Parent: OpenVpnGUI_unlimited.exe (SHA256: 064338e9b9075b48890d9db21fec27a3c7ce10e80abc954ba3777b660eceeacb) drops the following file:
- %TEMP%\RUNFIRST.exe (Bandit Stealer)
- %TEMP%\openvpn-gui.exe
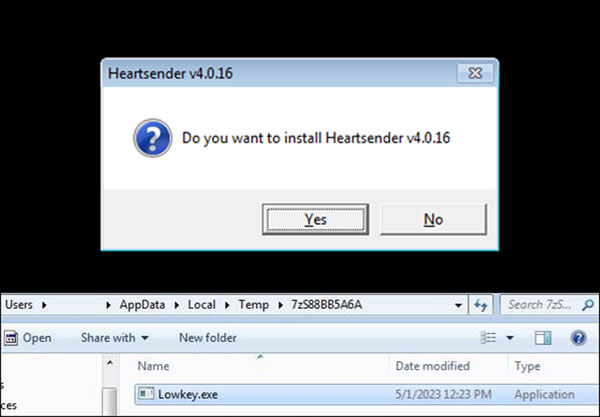
3. Once the self-extracting archive is executed, it will prompt the image shown in Figure 16, which acts as an installer of a Heartsender application. Heartsender is a spam distribution tool that automates the process of sending large volumes of emails to numerous recipients. While they can be utilized for advertising and marketing purposes, it is uncommon for regular users to use this app due to the potential for abuse in phishing, scams, and the distribution of malware. In this sample, the author appears to have created a fake installer of Heartsender, which can be purchased online, to trick users into installing it with the embedded malware.
Once the victim chooses the Yes button, the malware will drop and execute the Lowkey.exe file, which is Bandit Stealer.
Execution Parent: HeartSender.exe (SHA256: 64fe4148c74e0603c198459fd46b3ed3bece8066498f91782b6d98d5c3fc2d01) drops the file %TEMP%\Lowkey.exe (Bandit Stealer)
Conclusion
While Bandit Stealer was specifically developed to operate on Windows systems, we have observed the presence of Linux commands. As the binary sample of Bandit Stealer is designed to run in Windows, some Linux commands used by the malware include:
- pgrep and pkill commands to terminate the blacklisted processes
- isof -t <path of zip file>, a utility used in Linux environments to list down all processes that are actively using a file
- /proc/self/status, a file path specific to the Linux operating system
It is possible that these commands will be used in future cross-platform developments of the malware following the advertisement in the malware community stating developers are continuously updating the malware's features and security patches.
We also observed Bandit Stealer bearing similarities with other info stealers, primarily based on the use of blacklisted items such as IPs and MAC addresses. It is worth noting that the blacklist appears to be publicly accessible, rendering it available for use by anyone and making it challenging to attribute to specific threat actors. Based on our investigation, the malware is considerably original as there are no known malware families associated with it, and its emergence aligns with the anticipated advertisement.
As of this writing, we have not identified any active threat groups associated with this particular malware because of its recent emergence and limited data on its operation. We have not observed traces of what the group might have been doing with the information it has stolen as the malware is in its early stages. However, the malware actor can potentially exploit them for purposes such as identity theft, financial gain, data breaches, credential stuffing attacks, and account takeovers.
Moreover, while we still don’t know why Heartsender was used as a decoy, we noticed cracked versions of this application available on other websites, which could potentially be the source of the sample. As it is, legitimate advertising and marketing companies opt to use other applications that allow them more functions such as analytics and multiple, real-time collaboration capabilities. This is one indicator for companies and security teams to double check before proceeding to install any application.
Indicators of Compromise (IOCs)
| SHA256 | Detections |
|---|---|
| 782ec01fa989886571a72b77dc662640a9df7a5fbdc8a863a256820c7faf8e3b | TrojanSpy.Win64.BANDITSTEAL.THEOBBC |
| 050dbd816c222d3c012ba9f2b1308db8e160e7d891f231272f1eacf19d0a0a06 | TrojanSpy.Win64.BANDITSTEAL.THDBGBC |
| c4776e3d50d53cb0cad3f6b4e685bbb8e0b6efe0b3e761db2b64a4232f21996e | TrojanSpy.Win64.BANDITSTEAL.THEOBBC |
| ecc311fcf3884ead2e5614baedfe412e6d797d044df005dff2fae86f9c80d63a | TrojanSpy.Win64.BANDITSTEAL.THEOIBC |
| 191ce844c2381564bfc289789e364d1330ddc05bd97c9a8c13139e5f240c2527 | TrojanSpy.Win64.BANDITSTEAL.THEAFBC |
| 70a577151ba8b726808ad4bda7a4caf31eb2f4ab7e70045247b145d5feda5440 | TrojanSpy.Win64.BANDITSTEAL.THEAHBC |
| da3c3df0712fffd047e3b7326852d96def7584f5070c3c7803e47593899b4d0a | TrojanSpy.Win64.BANDITSTEAL.THEBCBC |
| 1cd60650fa3e560d8f7c80d4d059e669e64486bd3ca6daed52d8fdce14d0455b | |
| d934a1bde6bb75936d223426e64497e92526b8bc75a4f8a59a87f1d25ed1a0d2 | |
| 106a184d39858af7b0264f26fe0fc657a84ccfd87df3a4f55e7060b3c3c1d92d | Trojan.Win32.BANDITSTEAL.THEOBBC |
| 064338e9b9075b48890d9db21fec27a3c7ce10e80abc954ba3777b660eceeacb | |
| 64fe4148c74e0603c198459fd46b3ed3bece8066498f91782b6d98d5c3fc2d01 | |
| 69088f95523d2199e5a277a67a2f70a42e653bf58fb0f3790aa1436bd101eeb1 | Trojan.Win32.BANDITSTEAL.THEOIBC |
| 191ce844c2381564bfc289789e364d1330ddc05bd97c9a8c13139e5f240c2527 | TrojanSpy.Win64.BANDITSTEAL.THEAFBC |
| ecc311fcf3884ead2e5614baedfe412e6d797d044df005dff2fae86f9c80d63a | blacklist.txt |
App details
- 5144443087 Telegram CHAT ID
- 5943289606:AAGNEW2B3zDRhGDxY7E1tg7_m2BJcVkUJDw Telegram BOT ID
URLs
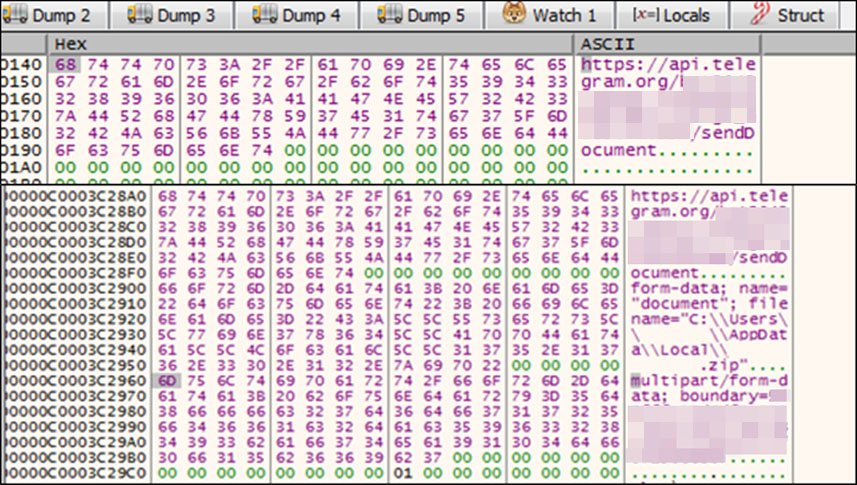
- https[:]//api[.]telegram[.]org/bot5943289606:AAGNEW2B3zDRhGDxY7E1tg7_m2BJcVkUJDw/sendDocument URL where the malware sends data
- https[:]//pastebin[.]com/raw/3fS0MSjN URL where the malware downloads the blacklist.txt file

