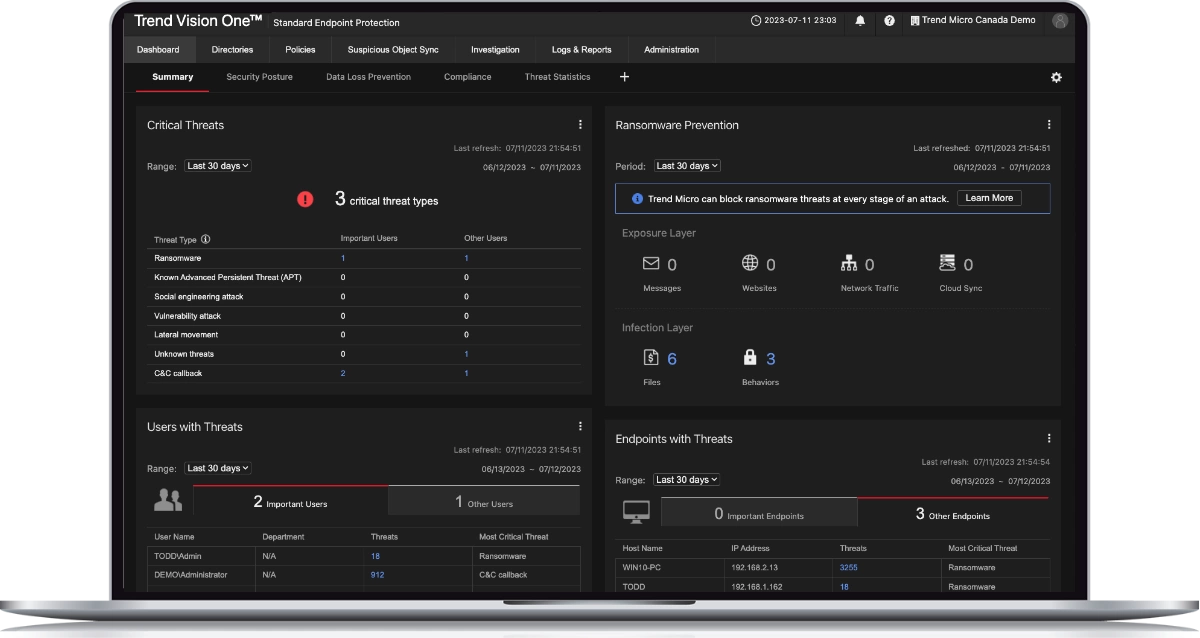
Consolidate endpoint, server, and workload security
Uncovering events and the attack path across endpoints, servers, and cloud workloads requires a single solution with a single view.
Respond faster, increase operational efficiency, and improve your overall security posture with centralized visibility, response, and management.

Detect and respond faster with EDR and XDR
Stop adversaries with a broader perspective and better context to hunt, detect, investigate, and respond to threats with EDR.
Extend your defenses to email, network, cloud, mobile, identity, IoT, and OT with purpose-built native XDR, included in Trend Vision One™.

Streamline IT security operations
Trend Vision One – Endpoint Security is unrivaled in platform support.
See inventory, check detections, take risk mitigation actions, and manage policies and licenses, all in one place. Achieve optimal security outcomes across on-premises, cloud, multi-cloud, and hybrid environments.
Trend Vision One™ Ranked #1 out of 59 Enterprise Solutions
The extended detection and response platform customers are raving about.




WHY TREND VISION ONE – ENDPOINT SECURITY
The broadest threat protection available
Layered protection for all stages of an attack
Multiple layers of security provide you with prevention and protection capabilities across every stage of the attack chain. Industry-leading intrusion prevention empowers you to mitigate known but unpatched threats.
Predict if files are malicious and detect indicators of attack before they get a chance to execute.
Stay ahead of threats
Get timely protection against an ever-growing variety of threats and vulnerabilities ahead of other security vendors. Block newly discovered vulnerabilities on arrival and powered by vulnerability research teams, including Trend Micro™ Zero Day Initiative.
Stop threats before execution with web reputation service, exploit prevention, and application control.
Broad platform support
Infrastructure transformation presents a mix of technologies that can be complex for your teams to secure as risks are uncovered.
Support a broad range of operating systems, including comprehensive Linux platform protection
Managed detection and response (MDR)
Augment your existing security operations with 24/7 monitoring. Rapidly detect, investigate, and respond to threats across all security layers.
Trend Micro™ Managed XDR analysts free up your security analyst teams so they can focus on mitigating the most sophisticated attacks and improving strategies and processes.

“Trend Micro is a good fit for customers who want a consistently strong endpoint protection platform that can support evolving to XDR.”

Market-leading performance
JOIN 500K+ GLOBAL CUSTOMERS
Consolidate visibility, analysis, and controls across security layers and workflows