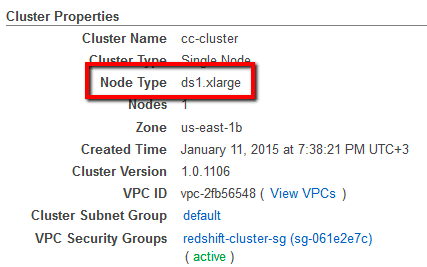
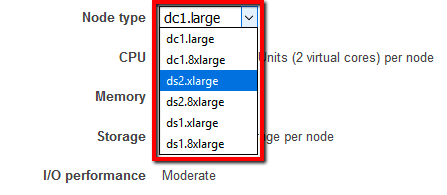
Ensure that all your AWS Redshift Reserved Nodes (RN) have corresponding database nodes running within the same account or within any AWS accounts members of an AWS Organization (if there is one created). A corresponding database node is a running Redshift node that matches the reservation parameters such as Region and Node Type.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
optimisation
When an AWS Redshift Reserved Node is not being used, the investment made is not valorized. For example, if you reserve a ds2.xlarge Redshift node within US East (N. Virginia) region and you don't launch a node with the same type, in the same region of the same AWS account or in any other member AWS accounts available within your AWS Organization, the specified Redshift RN is considered unused and you end up paying for resources that you don't use.
Audit
To determine if you have any unused Redshift Reserved Nodes within your AWS account or your AWS Organization (if there is one created), perform the following:
Remediation / Resolution
Once purchased, AWS Redshift Reserved Nodes cannot be modified, canceled or sold on Amazon Reserved Instance Marketplace and you will be billed for these resources regardless of whether you use them or not. To make use of your investment, you can provision and utilize a corresponding Redshift cluster node for each unused Reserved Node purchased within the current AWS account or within any other member accounts available in your AWS Organization (if you are using one). To provision new Redshift clusters using nodes that match the RNs purchase criteria, perform the following:
References
- AWS Documentation
- What Is Amazon Redshift?
- Paying Bills for Multiple Accounts Using Consolidated Billing
- Creating and Editing Consolidated Billing Account Families
- AWS Command Line Interface (CLI) Documentation
- redshift
- describe-reserved-nodes
- describe-clusters
- create-cluster