To secure your Amazon Web Services account and adhere to security best practices, ensure that your AWS root user is not using X.509 certificates to perform SOAP-protocol requests to AWS services. An X.509 certificate is a signing certificate utilized for API request validation purposes. Some AWS services use X.509 certificates to approve requests that are signed with a corresponding private key. Cloud Conformity strongly recommends disabling any active X.509 certificates deployed for your root account because using the root user to perform daily operations and develop AWS applications is not a best practice.
This rule can help you with the following compliance standards:
- APRA
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
Disabling X.509 signing certificates created for your AWS root account eliminates the risk of unauthorized access to certain AWS services and resources, in case the private certificate keys are stolen or shared accidentally.
Audit
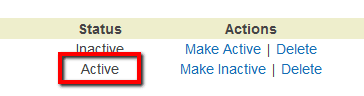
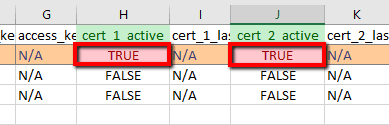
To determine if your AWS root account has any active X.509 certificates, perform the following:
Remediation / Resolution
To disable any active X.509 signing certificates created for your AWS root account, perform the following actions:
Note: Disabling X.509 certificates deployed for your AWS root user via Command Line Interface (CLI) is not currently supported.References
- AWS Documentation
- AWS IAM FAQs
- IAM Best Practices
- Getting Credential Reports for Your AWS Account
- X.509 client certificates
- AWS Command Line Interface (CLI) Documentation
- iam
- get-credential-report