Orphaned EC2 Instances to make sure every instance is launched within an AWS Auto Scaling Group in order to help improve the availability and scalability of your web applications during instance failures or denial-of-service attacks (DoS, DDoS).
This rule can help you with the following compliance standards:
- MAS
- NIST4
For further details on compliance standards supported by Conformity, see here.
This rule can help you work with the AWS Well-Architected Framework.
This rule resolution is part of the Conformity Security & Compliance tool for AWS.
As good practice, every EC2 instance should be launched inside an AWS Auto Scaling Group. To achieve zero downtime, Cloud Conformity recommends attaching an Elastic Load Balancer (ELB) to the Auto Scaling Group (ASG) in order to use ELB health checks in combination with the ASG to identify unhealthy instances and cycle them out automatically. This auto-scaling configuration can also help to maintain optimal the resiliency and availability of your applications during DDoS attacks by scaling and absorbing the attacks.
Audit
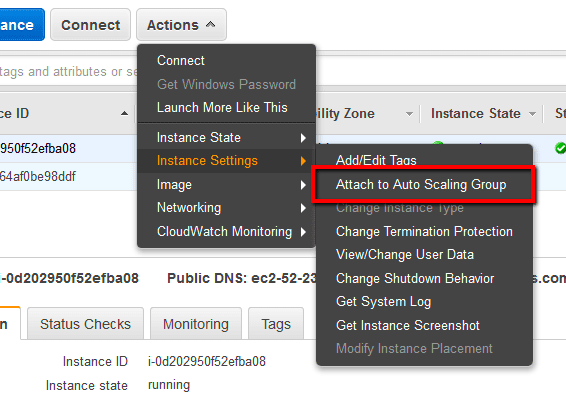
To identify any orphaned EC2 Instances (i.e. instances that don't belong to any ASG), perform the following:
Remediation / Resolution
To deploy a running EC2 instance into an AWS auto-scaling configuration using Auto Scaling Groups (ASGs) and Elastic Load Balancers (ELBs) for high reliability and security, perform the following:
References
- AWS Documentation
- What Is Auto Scaling?
- Getting Started with Elastic Load Balancing
- Creating a Launch Configuration Using an EC2 Instance
- Using a Load Balancer With an Auto Scaling Group
- Attaching a Load Balancer to Your Auto Scaling Group
- Adding Health Checks to Your Auto Scaling Group
- AWS Command Line Interface (CLI) Documentation
- ec2
- describe-instances
- autoscaling
- create-auto-scaling-group
- describe-auto-scaling-instances
- elb
- create-load-balancer
- configure-health-check

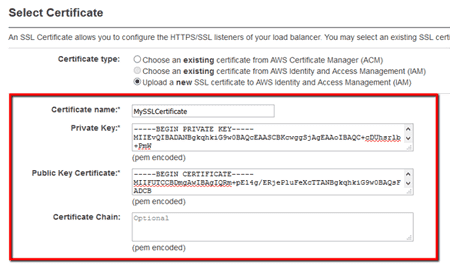 granted by the SSL provider from which you bought the certificate.
granted by the SSL provider from which you bought the certificate.