Mobile Safety
 Google has provided an update stating that 80% of Android apps have adopted the HTTPS standard by default. HTTPS encrypts network traffic, preventing third parties from intercepting data from apps.
Google has provided an update stating that 80% of Android apps have adopted the HTTPS standard by default. HTTPS encrypts network traffic, preventing third parties from intercepting data from apps. Click fraud apps pushed a 100 percent year-over-year increase in malware installed from Google Play in 2018.
Click fraud apps pushed a 100 percent year-over-year increase in malware installed from Google Play in 2018. Sextortion operations aren't new, but a new modus operandi that makes use of malware and mobile devices is emerging in East Asia. This research paper offers an in-depth look at the operation, its perpetrators, as well as their tools and methods.
Sextortion operations aren't new, but a new modus operandi that makes use of malware and mobile devices is emerging in East Asia. This research paper offers an in-depth look at the operation, its perpetrators, as well as their tools and methods.  This research paper provides in-depth information on the operation and structure of a cybercriminal group found using fake banking apps to steal mobile banking credentials from South Korean users.
This research paper provides in-depth information on the operation and structure of a cybercriminal group found using fake banking apps to steal mobile banking credentials from South Korean users.  If you gotta catch 'em all, make sure that you do so safely. Here are some best practice tips to make sure you don't get poké-hacked.
If you gotta catch 'em all, make sure that you do so safely. Here are some best practice tips to make sure you don't get poké-hacked.  There are privacy and security risks involved in connecting to public or 'free' Wi-fi hotspots. Here's a 4-step guide to setting up a virtual private network (VPN) for the times when you have to connect to unfamiliar networks.
There are privacy and security risks involved in connecting to public or 'free' Wi-fi hotspots. Here's a 4-step guide to setting up a virtual private network (VPN) for the times when you have to connect to unfamiliar networks. 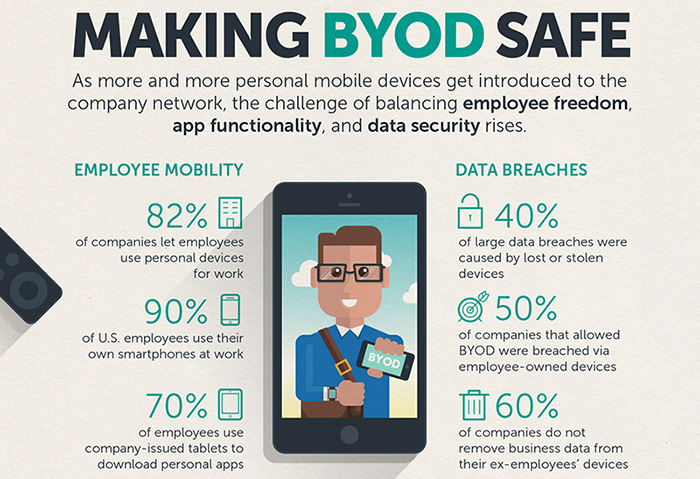 BYOD networks can benefit both the workers and the company, but it also presents a number of potential risks. This infographic details the challenges of balancing employee freedom, functionality, and security on BYOD.
BYOD networks can benefit both the workers and the company, but it also presents a number of potential risks. This infographic details the challenges of balancing employee freedom, functionality, and security on BYOD. 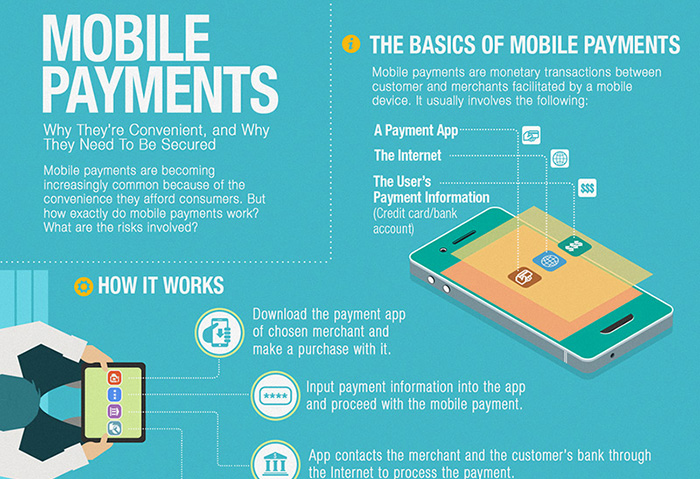 Mobile payment systems are becoming a more popular method of payment for people on the go. This shopping season, learn how mobile payments work, the threats that come with it, and what you can do to stay secure.
Mobile payment systems are becoming a more popular method of payment for people on the go. This shopping season, learn how mobile payments work, the threats that come with it, and what you can do to stay secure.